

D3’s integration with ThreatWorx shortens the detection and remediation cycle for everything from minor vulnerabilities to major zero-day threats. When companies receive vulnerability alerts, they don’t always have the resources to take action as fast as they need to. D3 ingests alerts from ThreatWorx and orchestrates response steps. So, when the next Log4j hits, you don’t need to panic.
ThreatWorx scans its customers’ assets for vulnerabilities and generates alerts. The challenge for customers is to free up the resources to determine the necessary steps to remediate the vulnerability and to execute those steps. Without a frictionless workflow for acting on ThreatWorx alerts, vulnerabilities are likely to remain in place longer than they should.
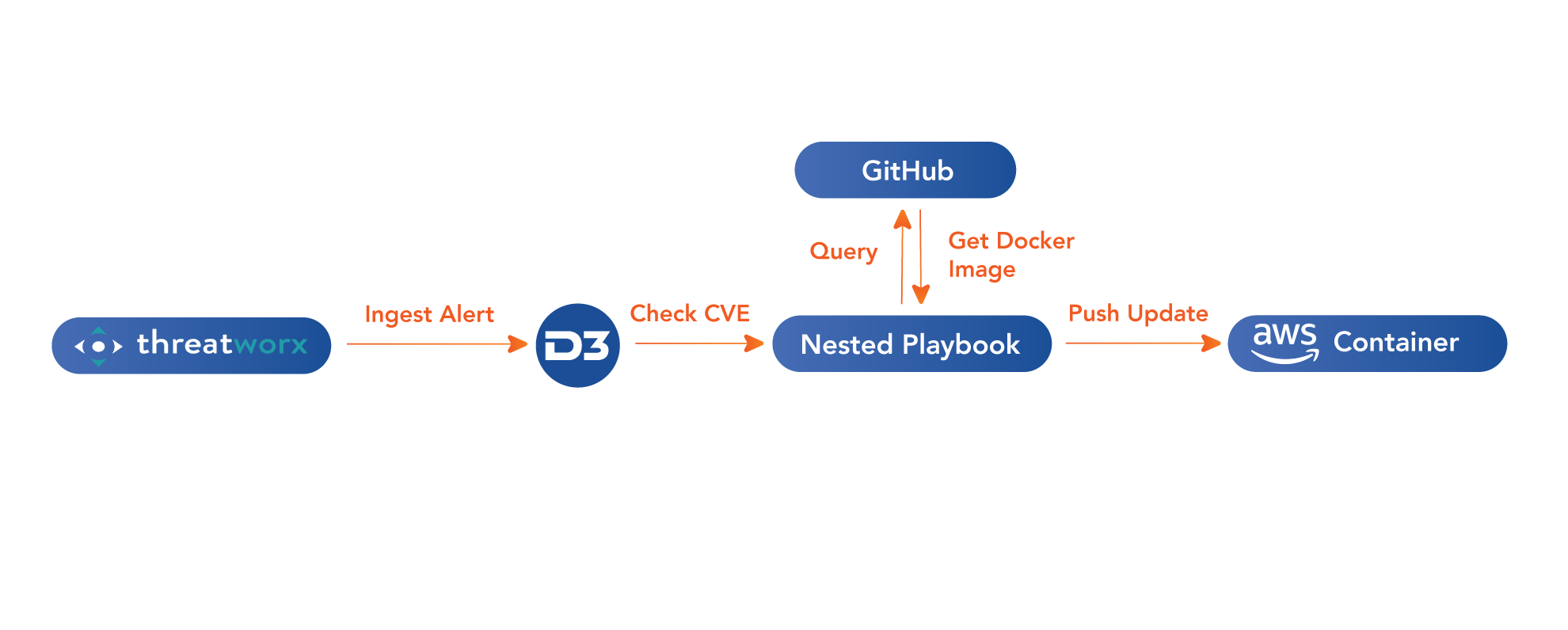
D3 ingests ThreatWorx vulnerability alerts into a vulnerability remediation playbook. The alerts are cross-referenced against the CVE glossary and tagged with the appropriate CVE number. The user can set criteria in D3 for which alerts are escalated to incidents and which are dismissed. For example, CVEs with a score of 7.0 or higher could be automatically escalated, triggering a playbook and notifications to analysts.
D3 comes with out-of-the-box sub-playbooks for many common CVEs, such as Log4j and PrintNightmare, and new downloadable playbooks are regularly published when solutions for new exploits are released. When a ThreatWorx vulnerability alert is ingested, D3 parses the CVE number and triggers the appropriate playbook. In the example of Log4j, the playbook would orchestrate actions such as retrieving the AWS Docker image file from GitHub, building the Docker image, and pushing the update to the vulnerable AWS container—resulting in an automated update of the Log4j patch to remediate the vulnerability.
Integrating ThreatWorx and D3 provides users with a workflow for detecting, assessing, and remediating vulnerabilities. By applying D3 automation rules to alerts, users can stay focused on the most important vulnerabilities and orchestrate immediate action when a CVE has a known solution. The automated process eliminates dwell time and the coordination between multiple teams that would normally be necessary.
ThreatWorx provides highly valuable intelligence in the form of threat alerts. Where many security teams struggle, is figuring out how to act on threat intelligence in a timely fashion. In a SOC that is ingesting dozens of alerts and threat reports from ThreatWorx and other sources, it would require a lot of dedicated resources to manually parse incoming threat intelligence, hunt for threats in the environment, and block any malicious IOCs.
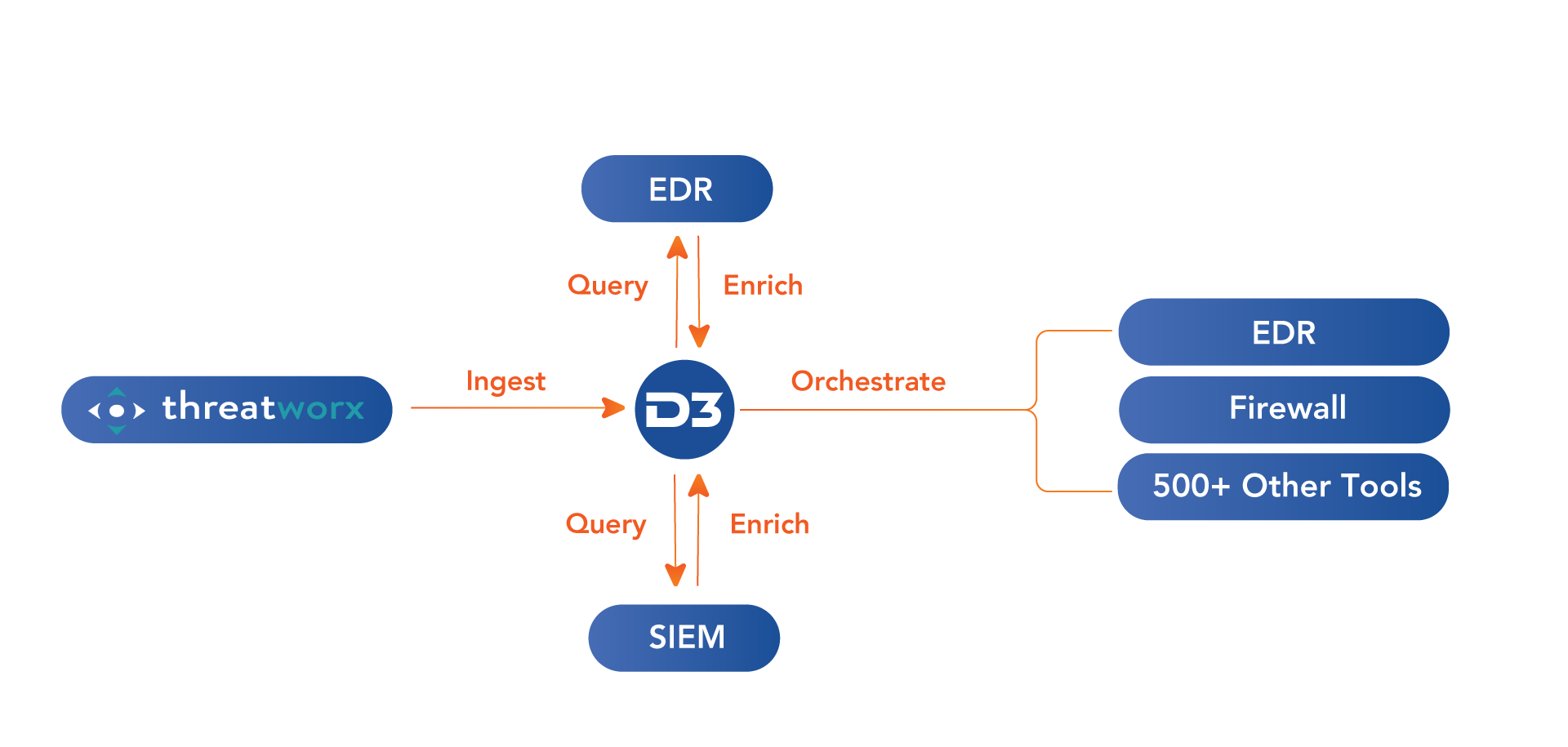
By adding D3’s automation and orchestration, users can consistently act on ThreatWorx’s alerts without committing additional resources. D3 ingests ThreatWorx intelligence and parses out the IOCs, such as file hashes, URLs, IP addresses, and domains. Then, D3 can hunt for those IOCs in the environment. In the case of a file hash, D3 can query an integrated EDR tool to find out if the hash is present on any company endpoints. If the hash is found, D3 can orchestrate the EDR tool to quarantine the endpoint, once approval is given by the appropriate person. In the case of IPs and URLs, D3 can add them to the blocklist on any integrated firewalls.
In this fully automatable process, you can consistently take action against potential threats before they do significant damage. ThreatWorx’s detailed threat intelligence provides D3 with the data it needs to run threat hunting and incident response playbooks that remediate threats and proactively defend against future risks.
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.