

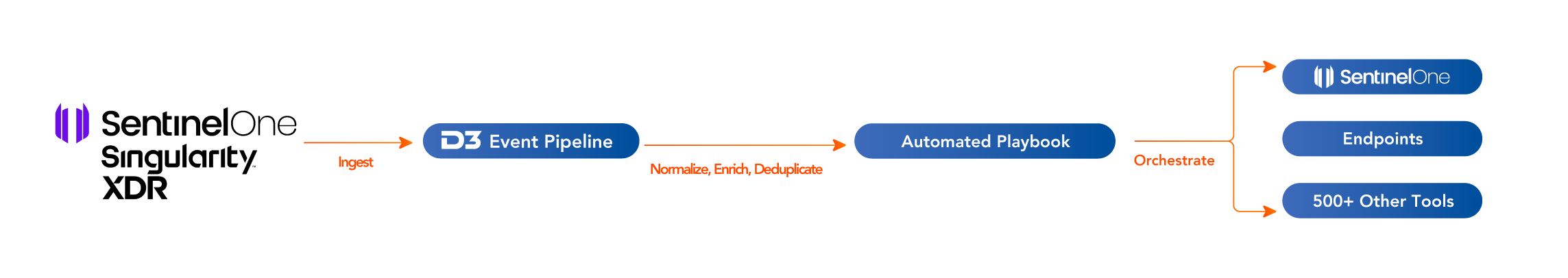
D3’s integration with SentinelOne Singularity XDR automates and orchestrates workflows for endpoint protection, threat hunting and incident response. Supporting a full range of automated actions, the joint solution reduces MTTR, triages endpoint threats through D3’s Event Pipeline, and increases the quality of investigations.
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.