SMART TRIAGE
Automated Security Alert Triage Across Your SOC
Turn the Noise Down and Confidence Up
Unlock the wisdom of your security alert data and automate the entirety of your tier-one work with D3’s Event Pipeline. Ingest alerts from anywhere and identify real incidents, without any of the noise. Connect your preferred tools in a cohesive pipeline that generates cost savings through automation.
Reduce Alert-Handling Costs by 90% or More
Turn Low-Fidelity Alerts into High-Fidelity Incidents
Build the Perfect Pipeline for Your Needs
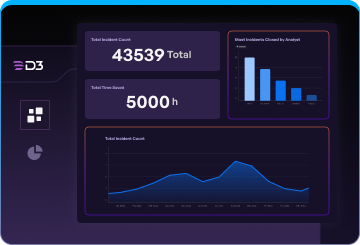

the smart soar approach
A Pipeline to Help SecOps Teams Triage Alerts Faster
Create a Single Source of Truth
Enrich and consolidate alerts to create high-fidelity incident records.
Leave no Stone Unturned
Correlate across dimensions so you don’t miss anything. Search across tools, past and present timeframes, adversary TTPs, and more.
Find the Value in your Security Data
Use rich data to inform conclusive, automated, incident response.
Entirely Automated Alert-Handling
Lets you focus on the higher-tier tasks that improve your security posture.
how it works
One Security Alert Pipeline for Your Entire Stack
Hundreds of Premium Integrations
Fully featured and vendor-agnostic, Smart SOAR’s integrations can be launched and operating in seconds, with minimal time or effort required for setup and maintenance.
Process every alert
Achieve full coverage of your alerts through automation that filters out the noise.
Activate Your Data
Break down silos and turn your security data into valuable intelligence.
Develop High-Fidelity Incidents
Automated enrichment, correlation, and grouping puts everything you need on one screen.
Scale Your Operations
Automatically process hundreds of thousands of alerts per day.
Learn More About the Event Pipeline
Check out these resources to answer your questions about this innovative cybersecurity technology.
-
A Comprehensive Guide to Smart SOAR
Learn how Smart SOAR outperforms conventional SOAR tools in every aspect of threat detection, analysis, and incident response.

-
No More Noise! Make Your SOC Your Sanctum
Drowning in alerts? D3’s Smart SOAR is the only SOC automation tool that truly turns down the noise. Achieve 91%+ alert reduction. No More Noise!
-
How High Wire Networks Eliminated 99% of Alert Noise and Increased Capacity 3x Without Adding Headcount
Serving 25k+ customers through a global network of channel partners, Master MSSP High Wire Networks used Smart SOAR to cut alert noise by 99% and 3x client capacity without adding headcount.
Get Started with D3
One platform to stop alert overwhelm. Transform how your security team works, by focusing its resources on real threats.