

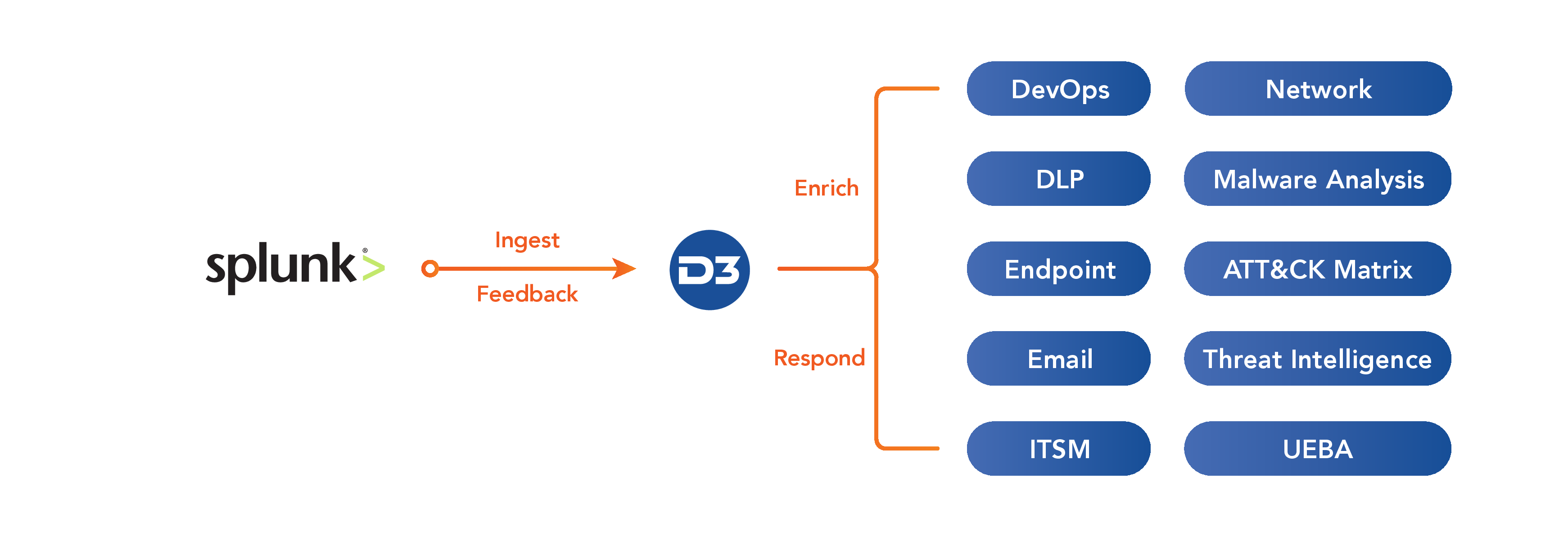
D3 Smart SOAR acts as a unified dashboard for analysis and investigation of Splunk events, enriching notable events with correlated MITRE ATT&CK matrix techniques, threat intelligence, and historical incident data. From Smart SOAR, Splunk users not only benefit from automation and orchestration-powered response workflows, but also robust investigative case management and reporting toolsets.
By combining Splunk for threat detection with Smart SOAR for incident enrichment and response, you can automatically escalate real threats to incident status in Smart SOAR and assess their criticality through data enrichment and MITRE ATT&CK matrix correlation. Smart SOAR can then trigger an automated response playbook or guide human analysts efficiently through manual steps, all within a single window.
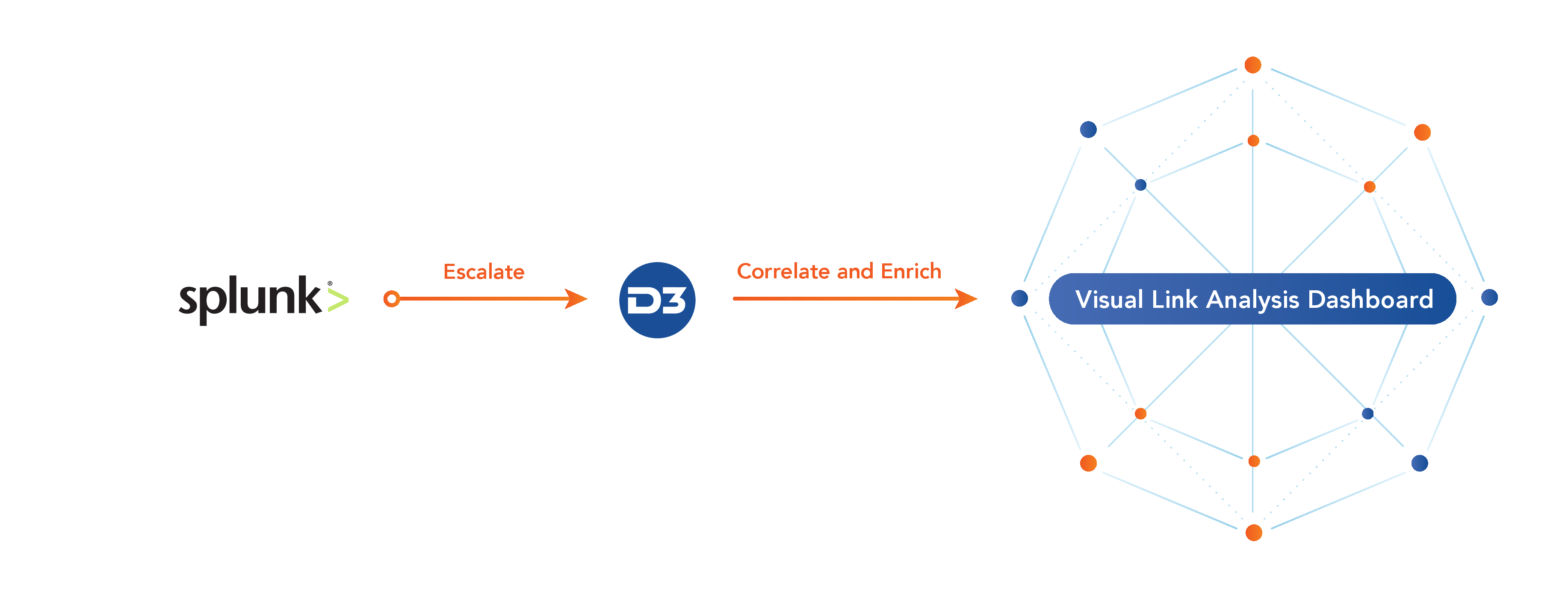
Once an event has been escalated, Smart SOAR can correlate IOCs—such as source IP/domains, destination IP/domains, file hashes, etc.— and MITRE ATT&CK techniques against threat intelligence, historical incident data, and potential traces of a larger kill chain, painting a complete picture of the threat. An intuitive link analysis dashboard provides analysts with the dexterity and visualizations needed for complex investigations.
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.