

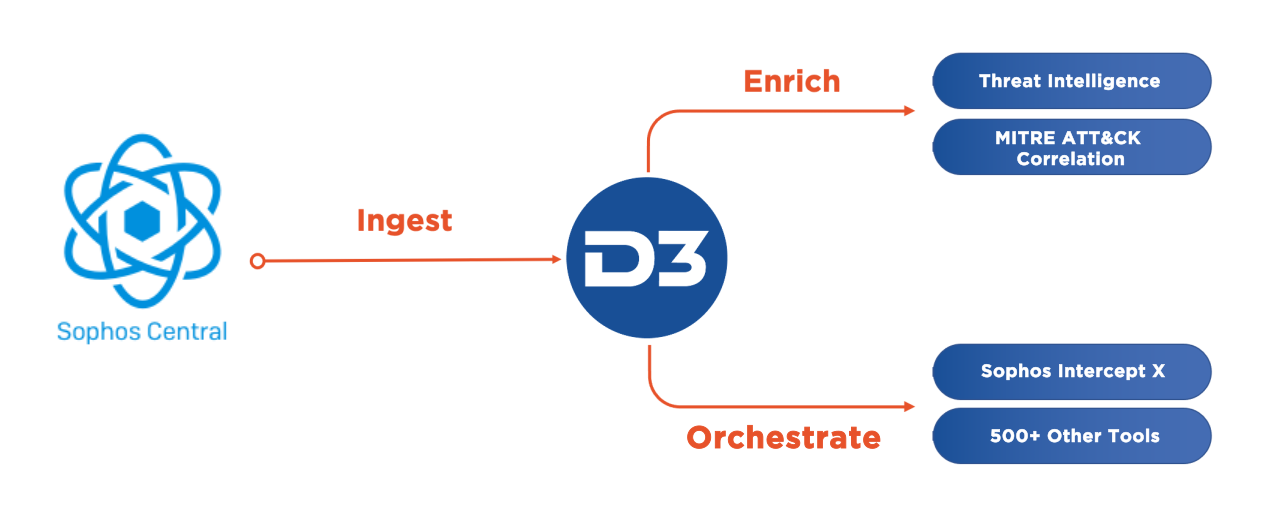
Integrations with Sophos Central and Sophos Intercept X make D3 the perfect command center for intaking events, scanning for malicious files, and orchestrating actions across endpoints. D3’s automation-powered playbooks, MITRE ATT&CK framework, and deep investigative capabilities bring effective and repeatable workflows to all endpoint events.
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.