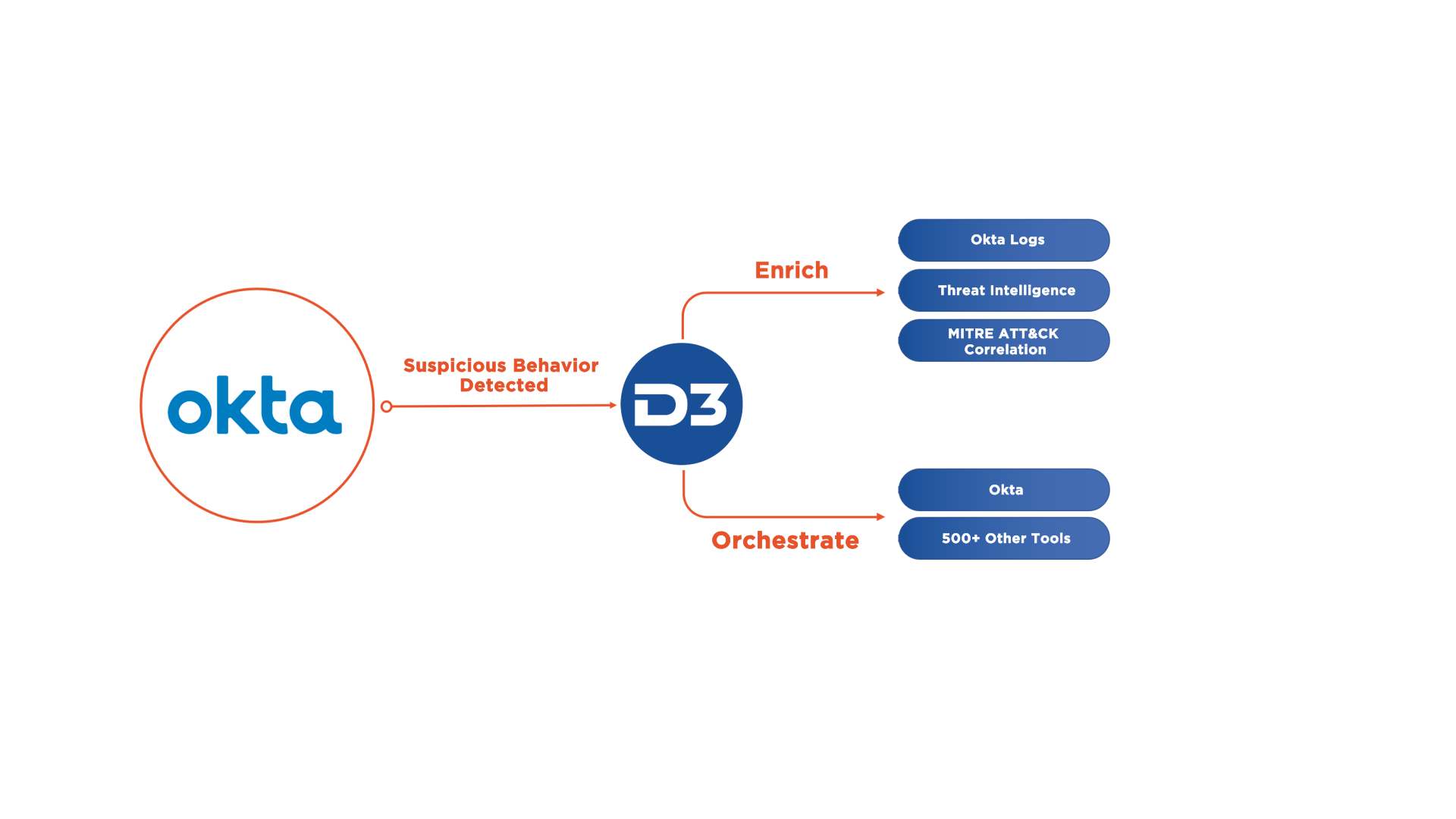
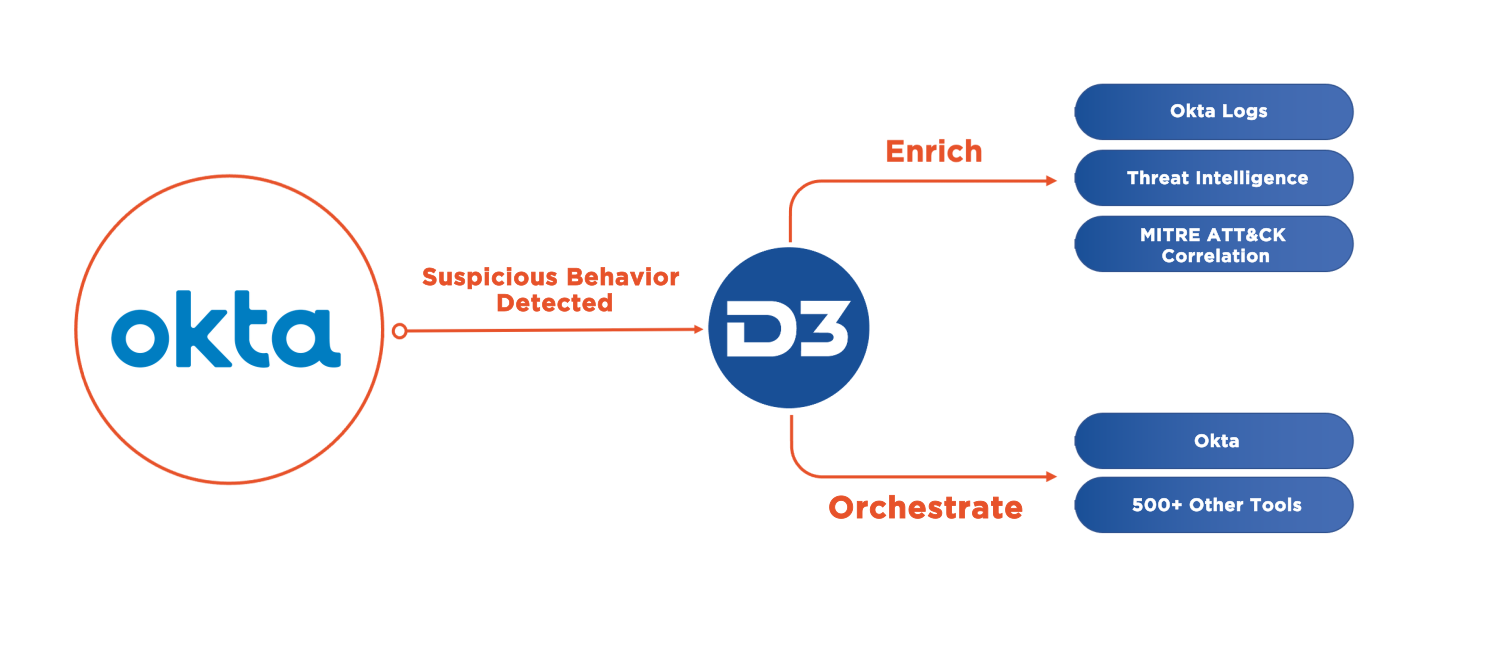
Sophisticated attackers often use compromised credentials to gain access to sensitive systems, which can completely elude signature-based defenses. D3 Smart SOAR integrates with Okta’s identity cloud to handle credential-based attacks. Users can escalate suspicious events to Smart SOAR, such as failed login attempts, which in turn trigger investigations in Smart SOAR. During which, Smart SOAR can retrieve event logs from Okta and orchestrate response actions, such as temporarily blocking access for a compromised user.
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.