

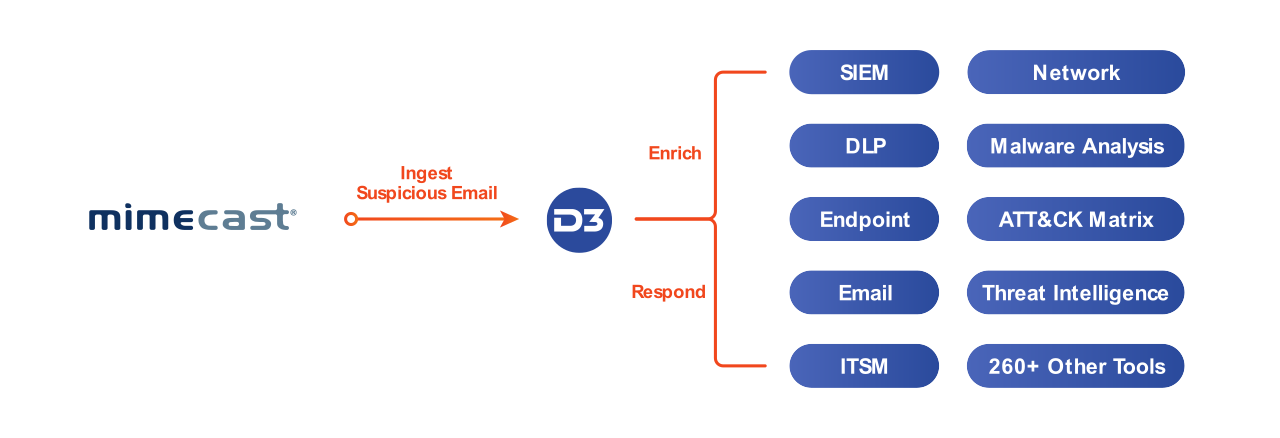
Even in the most sophisticated security infrastructure, email can be a weak link. D3’s integration with Mimecast connects advanced email security capabilities to automation-powered analysis and response. D3 can orchestrate more than 20 actions in Mimecast, without analysts needing to switch screens, even when conducting complex tasks. This enables efficient and effective handling of phishing and other email-based threats, with orchestration across the entire environment.
Phishing is a cheap and effective way for adversaries to target your organization. Most breaches still begin with some form of social engineering because human error is inevitable. Organizations need quick and effective ways to respond to potential phishing incidents without wasting analysts’ precious time.
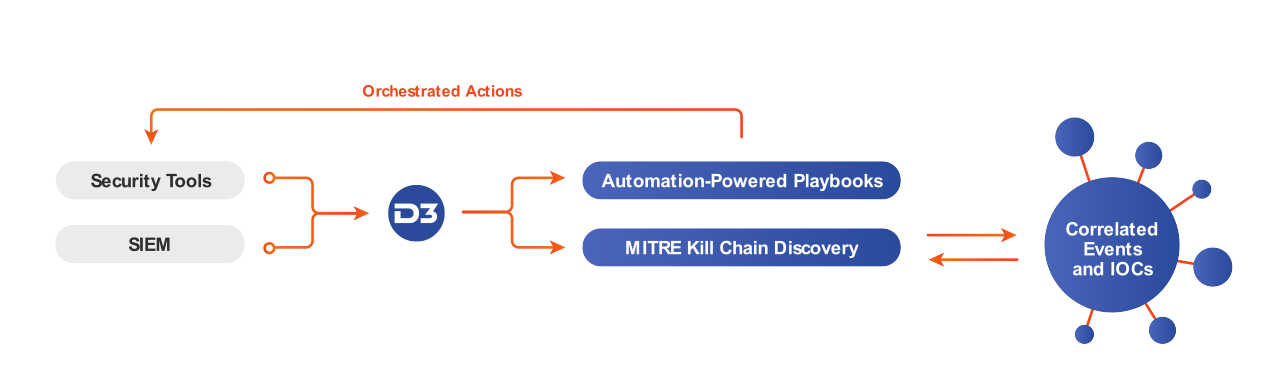
When a suspicious email is detected by Mimecast, the alert is escalated to D3 for investigation.D3 then triggers a phishing playbook, which extracts all the elements of the email, including any attachments, URLs, and the sender’s domain. All those elements are then checked against integrated threat intelligence tools as well as past incidents to identify known malicious IOCs. Attachments can also be detonated in an integrated sandbox. If the incident is confirmed as a genuine threat, D3 can orchestrate a response through Mimecast and the rest of the security infrastructure, such as searching for the malicious file hash across other inboxes, blocking the sender, and retrieving any related emails that might be part of the same campaign.
By running phishing investigations through D3, you can quickly identify and eliminate threats while reducing the time spent by your analysts on each attack. This is because D3 can aggregate related alerts into a single investigation and orchestrate a scalable response across all the necessary tools.
With so many alerts in the typical environment, security teams need a way to filter out the noise without missing dangerous alerts. Analysts don’t have time to investigate every alert, so meaningful incidents are left in the queue while endless false positives take up all the time.
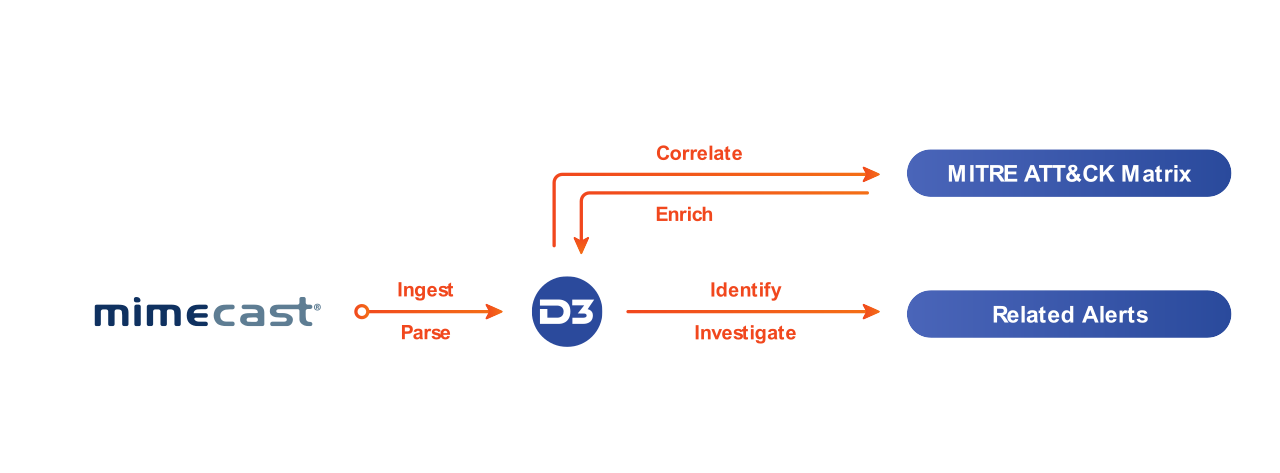
By running all events from Mimecast and other detection tools through D3’s Event Pipeline, security teams can automate data normalization, threat triage, and dismissal of benign events—eliminating up to 98% of events and keeping analysts focused on real threats. For email alerts ingested from Mimecast, this will include artifact extraction and correlation, de-duplication, threat intelligence enrichment, and assignment to the appropriate analyst if necessary. All of this occurs at the event level and is completely automated. Once a real incident is escalated to an analyst, they can trigger the appropriate playbook to resolve the threat.
D3’s Event Pipeline ensures that Mimecast alerts and other security events don’t get overlooked, no matter how much telemetry is produced by security tools. The unique architecture supports massive amounts of automated processing before human intervention is required. No more chasing false positives, fighting through an endless queue of alerts, or manually checking events against threat intelligence.
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.