

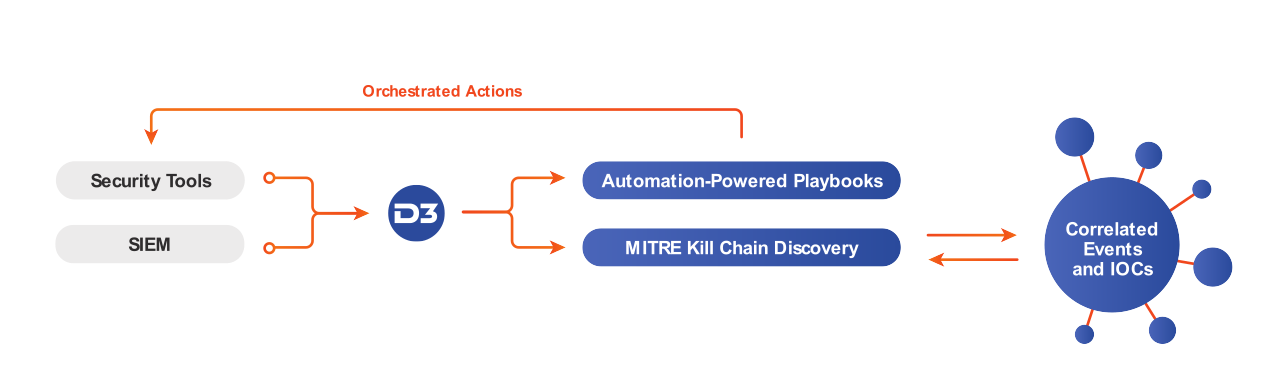
D3’s integration with MaxMind enables automated enrichment of security events with IP risk scores and geolocations. Integrating MaxMind intelligence into security workflows streamlines the analysis of, and response to, phishing emails, suspicious logins, and other potential security incidents. D3’s automated playbooks orchestrate responses across unlimited integrated tools, ensuring that threats are addressed before they cause damage.
With the high volume and growing sophistication of phishing attacks, security teams need reliable ways to assess the risk of suspicious emails. The existing solutions in most SOCs require analysts to switch screens and copy-and-paste information between tools dozens of times per day.
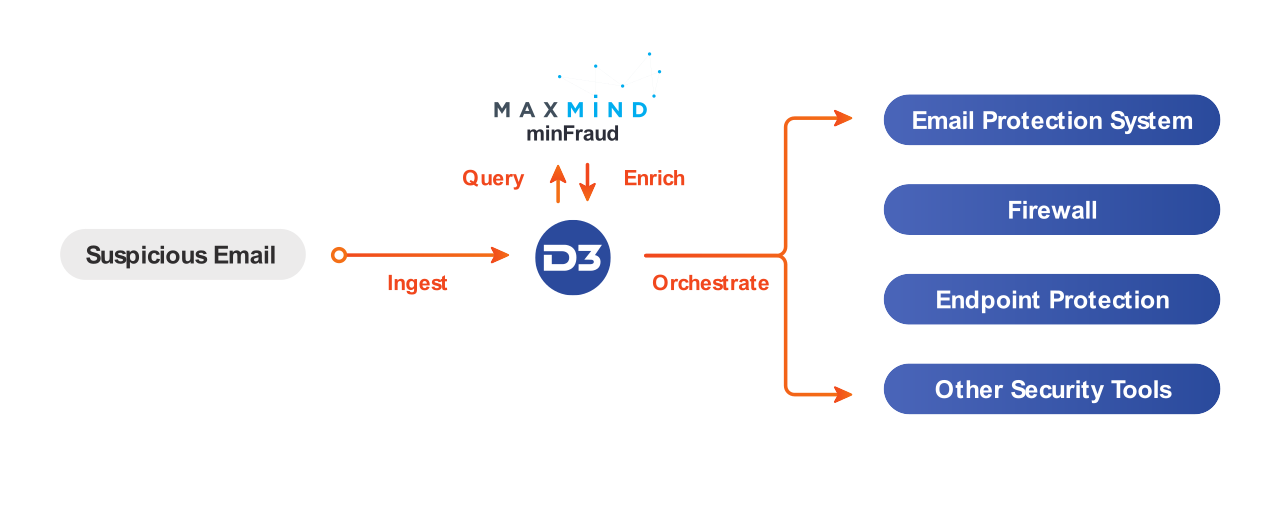
When a potential phishing email is escalated to D3, either through an email protection system or manually by the recipient, D3 extracts the sender’s domain and the URL of any links in the message. D3 then uses VirusTotal or another integrated service to retrieve the IP address associated with the sender and/or URL. Next, D3 looks up that IP via MaxMind’s minFraud service and retrieves a risk score that is added to the incident. Based on the risk score, the D3 user can then trigger a response playbook to block the IP, blacklist the sender, notify the email recipient, and orchestrate any other appropriate actions. If the risk score is low, the incident can be closed as a false positive.
This reliable and accelerated analysis of phishing emails saves security teams a great deal of time by leveraging automated tasks and integrated tools. Using D3 and MaxMind, analysts can act conclusively against genuine threats without wasting time on false positives.
Unusual patterns of behavior can be valuable factors in assessing security alerts. However, if security tools don’t have all the relevant information, they can miss obvious suspicious patterns, or conversely, catch a huge number of false positives. This can result in frustrating situations, like a security alert being generated every time a user logs in from a different computer than usual.
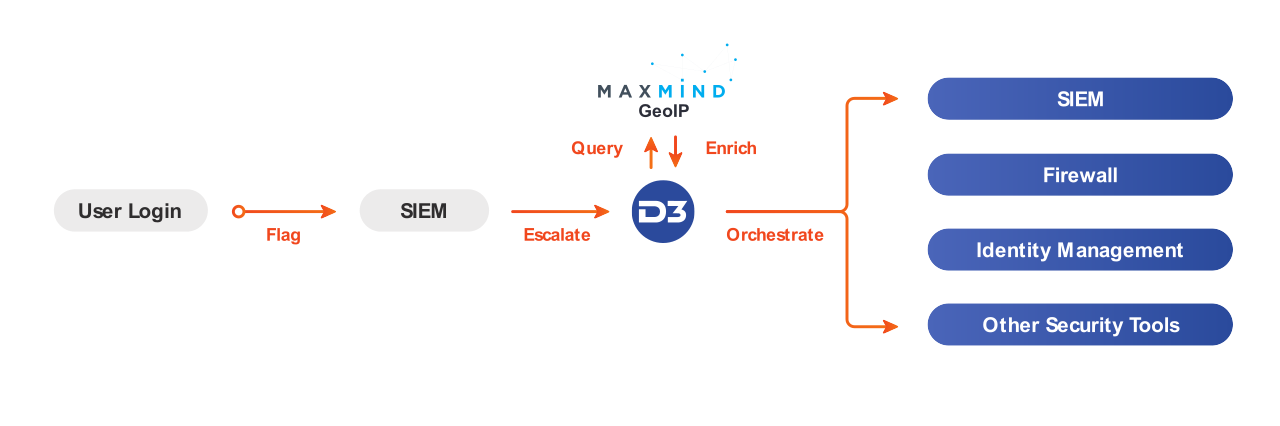
When a user’s credentials are used to log in to the company’s systems from an IP address that is not associated with their user ID, the login may be flagged by the SIEM. The SIEM can then escalate the alert to D3, where the IP address will be parsed and automatically checked against MaxMind’s GeoIP to pinpoint the location of the IP address. The analyst can then use the IP geolocation to determine if this is an unauthorized login, based on the location of previous logins and if it would be possible for them to have traveled to the new location since their last login. If the incident is deemed malicious, the analyst can trigger a playbook to take action.
Integrating D3 and MaxMind allows for fast and conclusive analysis of unusual behavior. By orchestrating this process through D3, you can also correlate against other valuable data, such as historical logs, threat intelligence, and MITRE ATT&CK techniques for additional context.
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.