

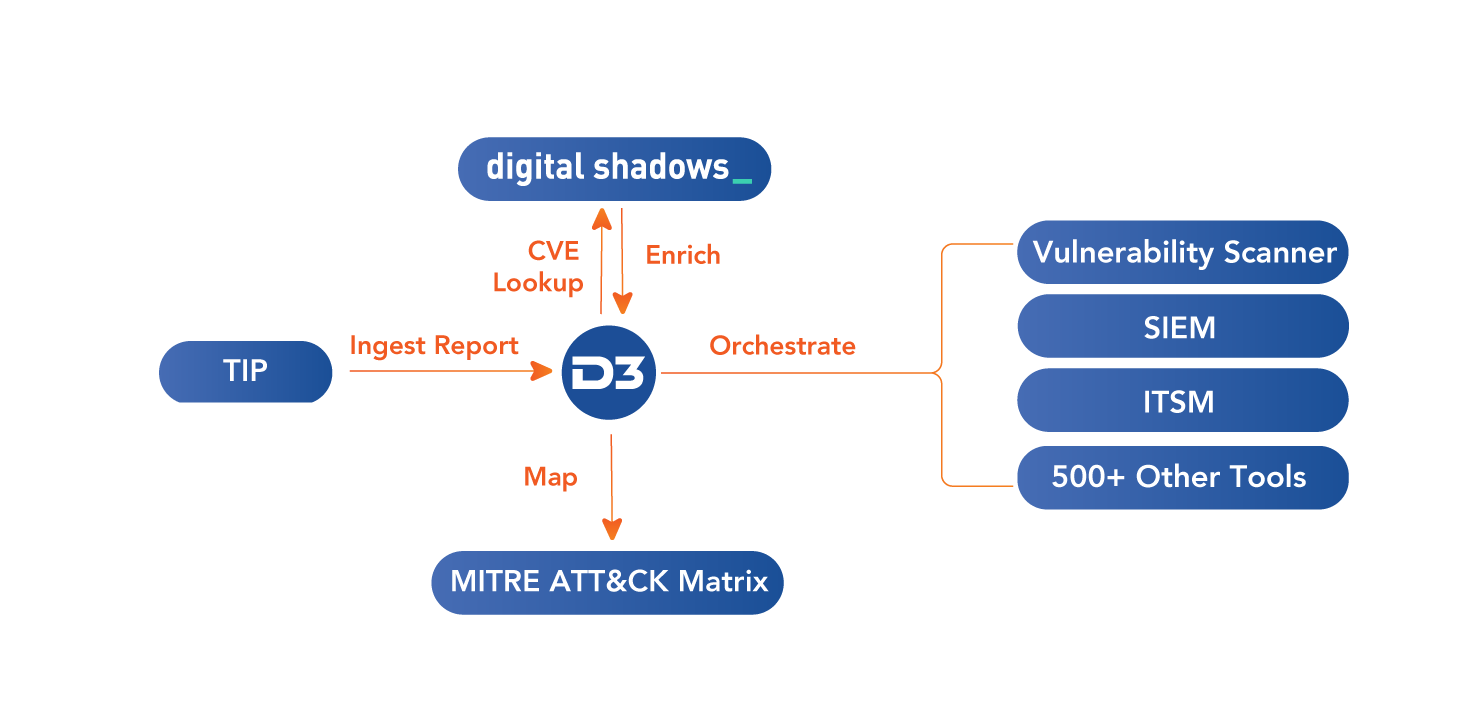
D3 integrates with Digital Shadows SearchLight to connect threat intelligence, brand protection, data leak detection, and more to automated triage and response. D3 users can enrich alerts with Digital Shadows intelligence, as well as retrieve valuable data on ingested threat reports, including mapping threats to D3’s built-in MITRE ATT&CK Matrix.
Many security teams find that they have access to an abundance of valuable threat intelligence reports, but fail to act on most of that intelligence because they do not have the necessary workflows in place. With D3 and Digital Shadows, you can create an automated process for ingesting threat intelligence reports, assessing their risk, and hunting for IOCs and vulnerabilities in your environment.
In D3, users can set up a scheduled utility command to retrieve threat reports on a weekly cadence (or whatever cadence they are published on) from integrated TIPs, such as Qualys. D3 then parses the report and extracts the details, including any CVEs. Then, each CVE is sent to Digital Shadows SearchLight to retrieve the CVSS score, a risk score, and the MITRE ATT&CK TTPs involved. The analyst can then quickly assess the risk level and trigger the appropriate threat hunting playbook. This might include running a scan in an integrated TVM tool for vulnerabilities in the report, searching an integrated SIEM for IOCs, and generating notifications to close any known vulnerabilities.
The combined solution of D3 and Digital Shadows creates an almost entirely automated process for operationalizing threat intelligence, threat hunting, and vulnerability management. This helps to ensure that important threat reports are always acted on immediately, not just when someone has the time to look into them.
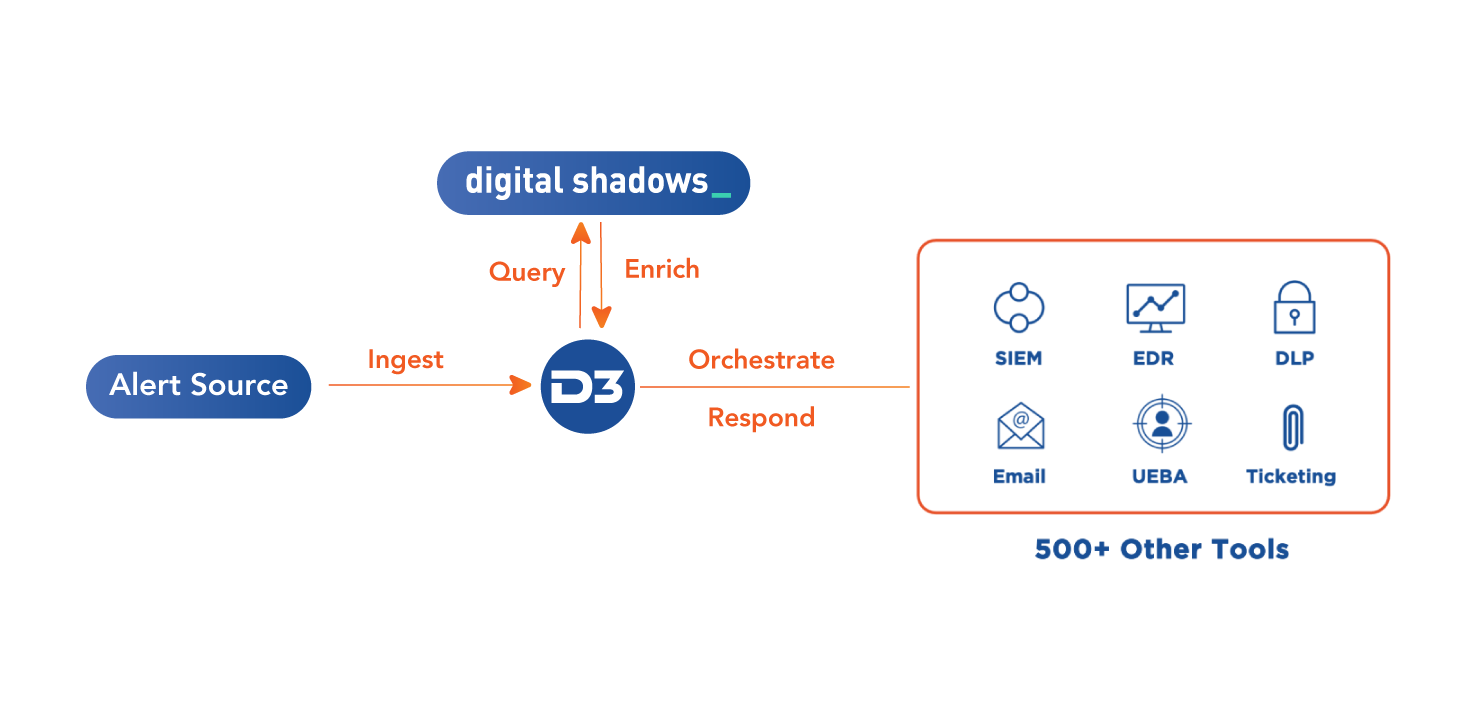
Security events, whether they’re genuine threats or false positives, can upend your security team by requiring analysts to gather contextual data while dealing with screen switching, data silos, and a lack of up-to-date information. Analysts spend too much of their time completing mundane tasks like copying and pasting URLs and hashes for threat intelligence lookups, which slows down analysis and allows real incidents to slip by uninvestigated.
By integrating D3 and Digital Shadows, you can automatically enrich alerts from your detection tools with valuable intelligence from Digital Shadows SearchLight, including IP, URL, and hash information. This enables you to immediately assess the risk of an alert and trigger the appropriate response. Or, to completely automate the process, users can create conditional tasks based on factors like the reputation score of the IOCs, which can automatically trigger nested playbooks.
The worst kept secret of the SOC is that most alerts don’t get investigated. By automating threat intelligence enrichment from Digital Shadows, D3 can help streamline alert triage and analysis. Analysts can identify false positives and low-risk events, while saving time they can use to properly respond to real incidents.
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.