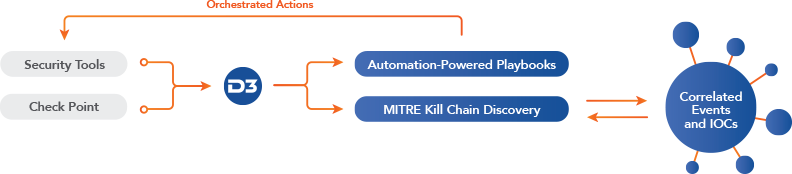
The combination of Check Point and D3 Smart SOAR provides the SOC with vastly improved visibility, intelligence, and agility. Events in Check Point trigger automated playbooks in Smart SOAR, which gather context from across the security ecosystem, including correlation against the MITRE ATT&CK framework. If the event is convicted, Smart SOAR will execute the remediation plan, which can be fully or partially automated. The whole process takes only seconds.
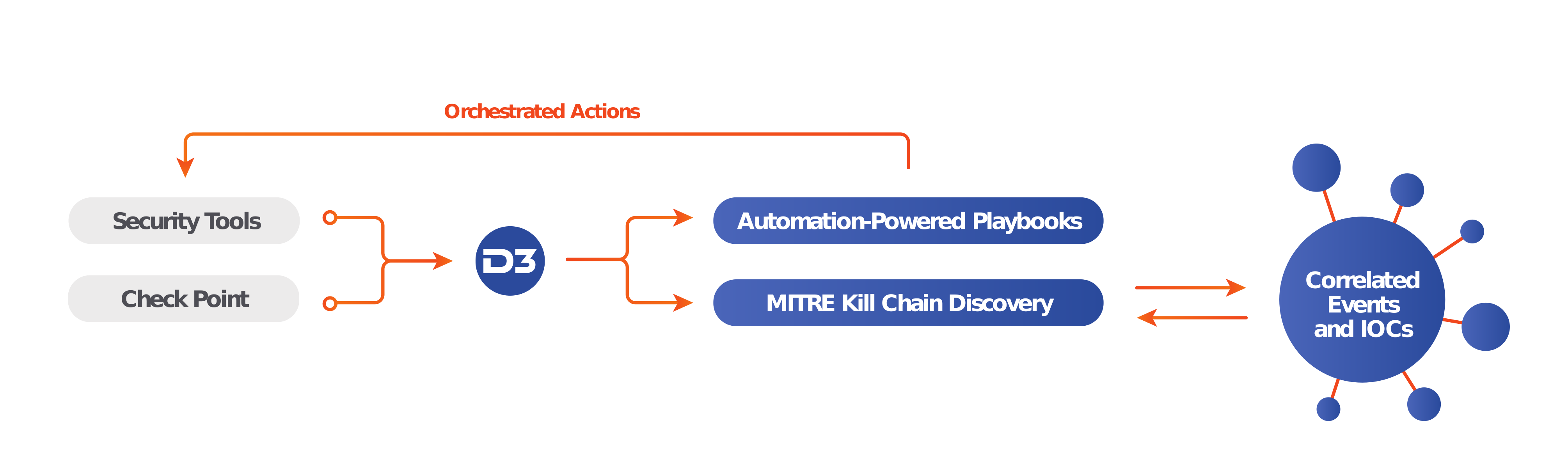
Smart SOAR can monitor a phishing inbox and create an event by pulling suspicious email content and attachment(s). The file reputation is then automatically checked in the Check Point Threat Prevention module. If the file is not found, an API call will be triggered to upload the original file for sandboxing. Smart SOAR will search SIEM logs for suspicious network flows occurring on the involved endpoints and also automatically enrich external IPs and URLs. If an IOC’s reputation is malicious, a response playbook will be triggered to quarantine endpoints and block IPs and URLs.
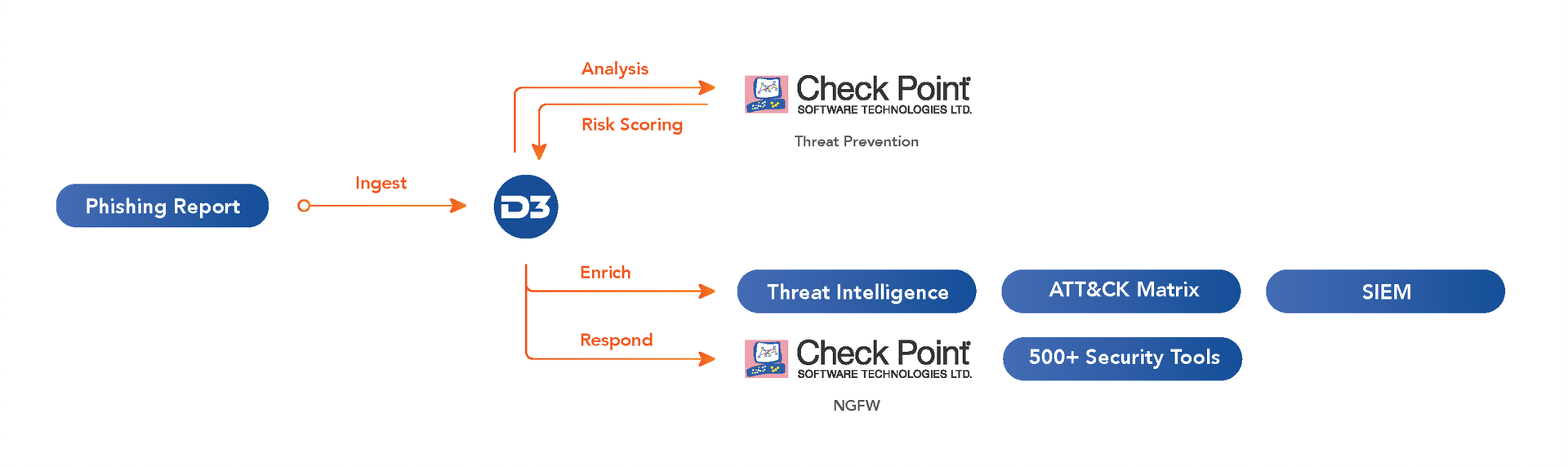
When Check Point’s Next Generation Firewall detects suspicious traffic, the alert is escalated automatically to Smart SOAR for investigation. Smart SOAR then correlates the alert against additional data sources, most importantly, the SIEM, which contextualizes the alert with log data. This data will include other activity of the implicated IP address in recent logs, any recent changes in privileges to associated user IDs, and other relevant data related to the IOCs that Smart SOAR found in the alert. The full context of the alert is then presented to the analyst, who can dismiss the alert as a false positive or trigger an automated playbook to respond to the threat, including updating firewall rules.
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.