
D3 Security’s Forensics Case Management system garnered a lot of attention from CISOs, corporate investigators and eDiscovery specialists at the world’s largest data security and digital investigations conference, CEIC. They were impressed with how the workflows, automation features and logic built into the system managed custodians, data sources, tasks and evidence so efficiently and in accordance with the industry’s exacting best practices. Many wondered how D3 Security, a relative newcomer to the digital forensics marketplace, was able to “nail it” (actual quote!).
It’s no doubt a relevant question—and we’ve provided the rather interesting answer below. I’ve also taken the liberty of reviewing overwhelmingly positive feedback given to us by CEIC attendees—namely Security Investigations Specialists, IT Forensic Examiners, Incident Response Directors, CISOs, Information Security Officers, and eDiscovery Specialists—to create the following list, D3 Forensics Case Management System: CEIC’s Top 5 Features.
How did D3 Security Create Such a Strong Forensics Case Management System?
In 2012, an unnamed Fortune 50 company (“The Company”) familiar with our incident reporting software and investigation/case management system approached us hoping to solve a problem. The Company had searched thoroughly for a solution that could manage and streamline the massive volume of case requests, custodians, evidence, tasks and reporting increasingly assigned to their global IT Forensics team—and nothing on the market came close. So, they offered to work closely with us to create an IT Forensics Case Management system laser-focused on managing simultaneous digital, mobile and computer investigations from inception through resolution. As noted by CEIC attendees, the system’s workflows and logic work extremely well to streamline cases significantly, and that’s because they’ve been shaped by one the world’s leading corporate IT forensics teams, its senior investigators and data security specialists—each with decades of relevant experience and best practice development. This foundation—particularly when paired with D3’s renowned configurability—is what makes the D3 Security solution such a focused and capable platform for any team conducting computer, mobile and digital investigations.
D3’s Case Management System: CEIC’s Top 5 Features
I’ve taken the feedback from CEIC attendees and created a list of what they thought were the Top 5 features of the D3 IT Forensics Case Management system. These features—and many others—were demonstrated or described on the show floor, and they consistently were hailed as significant improvements over existing products and practices. Primarily, attendees were impressed with the amount of time and effort the D3 system saved through its streamlined user experience, elimination of redundant exercises and numerous automation features. As one user who visited CEIC put it, “your system helps me shave days and weeks from a single case.”
1. The Configurable Web Intake Form
A tailored web form allows users to easily request a case, identify its type, associate a list of custodians and specify any necessary parameters such as keywords, dates or locations. The Case Type tab is fully configurable; selecting a certain case type will trigger default settings in the rest of the form, streamlining the selection of data sources and uploading of custodians. This process works to ensure that all relevant information is consolidated in the case record while also removing any unnecessary fields that contribute to redundancy or the submission of useless information.
The Web Intake Form is integrated with Active Directory and other personnel management systems. Accordingly, users can upload a list of hundreds of custodians with a just a few keystrokes. You can even upload specific groups—such as entire departments, locations or work teams—further streamlining the custodian process and ensuring that only the most thorough cases are requested.
2. Request Summary Notification & Dashboard
- If a Stolen Intellectual Property case type is submitted, D3 will notify a representative of the Legal department, Information Security team, and the IT investigations manager. They will review and add any information as required.
- Approvals processes are easily configured into the Request Summary. A manager will receive a Case Request and subsequently approve it if necessary, whereupon it becomes an official investigation.
- A Case Request can be sent for review to the Legal and Human Resources departments, in order to establish whether or not the company has legal grounds to retrieve and analyze a person’s files.
3. Evidence & Data Source Tracking
Evidence tracking with the D3 solution begins with tag-number barcoding and image file creation of hard drives, tablets, mobile devices, and any removable media. Checking any exhibit in or out is automatically logged in the chain-of-custody, as are any processing and retrieval outcomes and dates. Once data has been acquired from physical devices, it can be viewed, stored and referenced through the Evidence Tracking component’s intuitive tabular window.
From the software application, users can leverage advanced search capabilities, image files, chain-of-custody and processing information to manage physical evidence or analyze acquired data from virtually any type of standard source; email and webmail, web history and cache, chat sessions, audio, compressed files, backups, servers, RAID workstations, disk or RAM memory, plus data from smartphones and tablets.
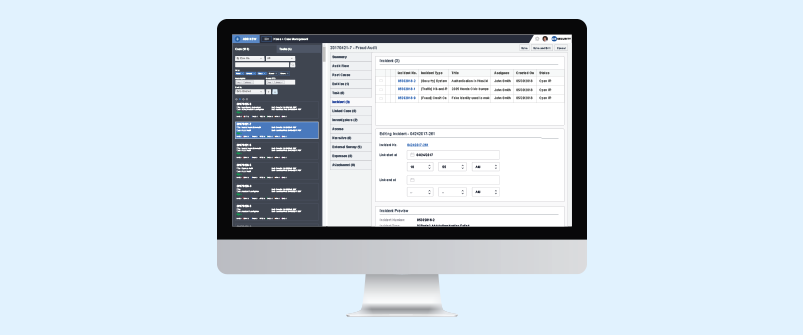
4. Case Management Dashboard & Configurable Tabs
The Case Management interface is an intuitive window that displays case status and related information on the right, including case status, priority level, any due dates stipulated as per an internal Service Level Agreement (SLA), and the date, time and quantity of any data retrieved or processed from each data source. Outstanding tasks are color-coded based on their due date and priority, enabling at-a-glance management.
In addition to this case status dashboard, there are configurable tabs located on the left. These are by default populated with Entities, IT Forensics, and Reviews. In Entities, you can review a case’s custodians and data sources, in addition to the Dynamic Link Analysis feature which allows investigators to establish relationships, test theories and generally use visualized data to improve the effectiveness of their investigations.
In IT Forensics, you can monitor all processing that has occurred or is occurring. Adding a new process is easy and forthcoming integrations with various forensic workstations will only enhance this capability further.
Finally, in the Reviews tab, the user can receive and review any collaborative items such as tasks or feedback completed by other departments, instructions from his or her superiors, or messages that have been received through the External Survey feature, which can be used as a securely encrypted method of distributing questionnaires, witness statements or general commentary from case collaborators.
5. Time Saving Analysis Reports
Reporting from any field in the system is a hallmark of all D3 Security software modules, and the D3 IT Forensics Case Management System is no different. Investigators quickly drill down using a variety of analytics and reporting tools for real-time vision into legal holds, custodians, data sources, SLA phase stages and much more. D3 has also built several straightforward pre-configured reports that generate significant time savings and allow investigators to focus on advancing their cases. For example:
- Nightly Transparency Reporting: In the past, investigators spent much time reporting on case status to the many stakeholders associated to an IT forensics case. But now D3 has built a nightly report that automates this activity. Information access controls govern the content of each case status update.
- Executive Dashboards: Investigators can publish and distribute executive-style dashboards that visualize complex data, facilitating review by outside departments without relying on unnecessarily complex reports.
- Caseload & Investigator Performance: A team manager can quickly see the caseload and associated performance metrics of the investigators, enabling the efficient assignment of resources to a new case.
- Loss & Recovery: This report tracks every investigative endeavor, its time and cost. It’s an easy and straightforward way to determine the impact of a particular case on the organization and its resources. It can also be used to determine thresholds for case types, against which you can then judge the effectiveness of forthcoming investigations.
So, there you have it: the D3 IT forensics solution’s top 5 features—as indicated by the CISOs, computer forensics investigators, data security professionals and eDiscovery specialists at CEIC.
Click the button below to schedule your one-on-one software demo.
