

At D3 we help power and water authorities, utility regulators and mega-size utility corporations achieve new levels of security, investigation and employee safety. Most of the work is directed by our Energy & Utility Practice Group, an internal team dedicated to ensuring the success of D3’s utility customers.
We asked team leaders to share the utility industry’s biggest security challenges—and how D3’s Incident Management Software and Physical Security Platform are used to achieve them.
1) Copper Theft Incident
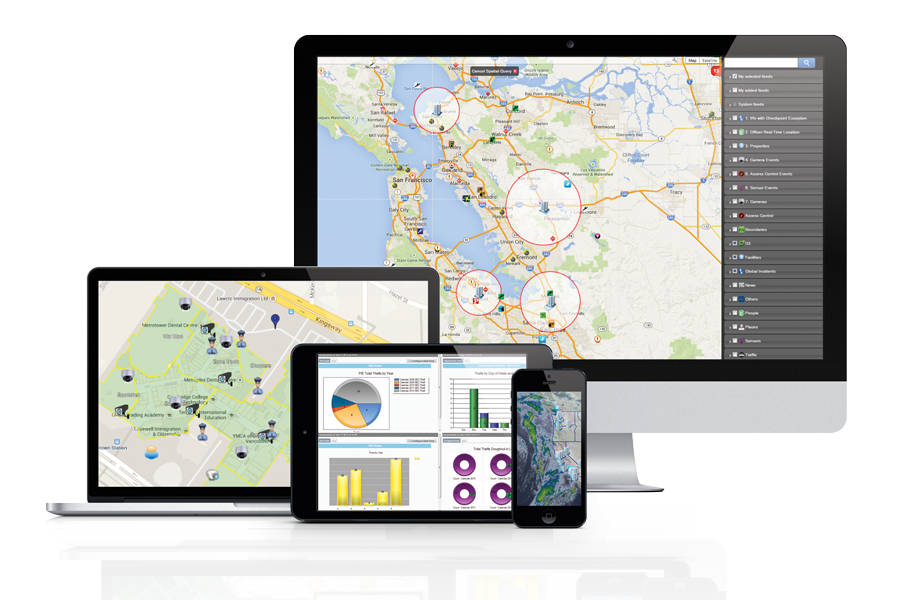
D3 GIA, our award-winning geo-intelligence platform, helps utilities solve the problem of copper theft by monitoring vast service areas, triggering response to events in progress (such as break-ins or alarms), and displaying historical copper thefts on a layered map interface.
Site dispatchers or SOCs use GIA to monitor facilities in real-time and deploy security resources as needed. For remote sites or night shifts, auto-workflows can deploy officers on the basis of incident thresholds and configurable SOPs. Integration with CCTV and access control systems further enhance GIA’s security response capabilities.
Asset protection teams use GIA to display, filter and analyze geo-located copper theft incidents. Users apply filters to explore patterns in time-of-day, location, security response and other variables. When clicked, a map-based theft report reveals all its details and any linkages to other incidents, suspects and investigations.
Trend reports, incident heat maps and site security assessments are easily created from the map interface, and GIA’s 120+ third party feeds—such as weather tracking, police reports, drone alerts and NERC/FERC notifications—provide another valuable layer of intelligence.
2) Investigating Electricity Theft
D3 helps utilities combat meter tampering, diversion to marijuana grow ops and other types electricity theft, which caused $6 billion in losses to US utilities in 2013.
First, D3 provides a web portal for public reports, a mobile reporting app for utility employees, and workflows that collect reports from different internal divisions. All reports are centrally organized so that investigators or revenue protection teams can establish linkages and apply their resources efficiently.
Second, with D3’s unlimited customization options, each incident report carries with it highly actionable data such as theft type (e.g. power theft), subtype (diversion to suspected marijuana grow up); location (GPS coordinate of single family home), evidence (no snow on roof/blacked out windows); witness statements (concerned neighbor notices suspicious activity); presence of safety issues (guard dogs present), etc.
Armed with high quality data, investigators and revenue protection teams can analyze and act upon the most important or egregious electricity thefts. The data also ensure the right resources attend any mitigation efforts; billing or internal security are sufficient for some incidents whereas law enforcement may be required for repeat offenders, marijuana grow ops, or proximity to school zones.
3) Protecting Community Workers
Serving notices, installing smart meters and following up on customer disputes can create a high level of risk for a utility’s community workers.
D3 helps utilities manage risk to in-the-field employees through its mobile app, available for Android, iPhone and Windows Mobile. Workers are tracked on GPS and can quickly create an incident report, including pictures and voice-to-text functions. There is two-way communication with dispatchers and alerts to law enforcement or the security team can be made through the Panic and Self-Dispatch features.
Data from the field is also used to create proactive measures; incident heat maps illustrate where higher risk or incident clusters exist. A utility can create data-driven policies: a law enforcement escort may be required for high-risk areas or households where a threat of violence has occurred. Three-person teams may be required for service calls after 8 pm.
4) Optimizing Security at Remote Sites
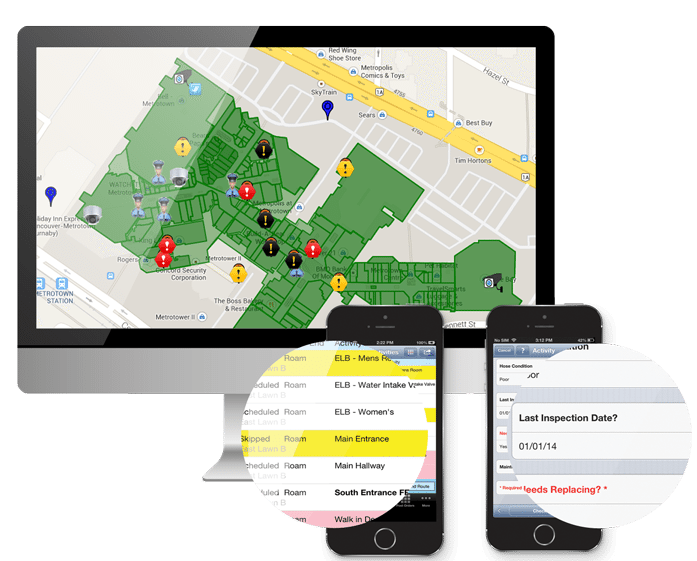
D3’s Guard Tour system can manage remote sites easily, and in a way that ensures regular security presence, managerial oversight and proper maintenance. Security vehicles that visit remote sites are equipped with a handset or tablet running D3’s mobile app. The device’s GPS function tracks the vehicle as it travels to remote sites; dispatch or SOC operators can see the unit’s location on the GIA map interface, ensuring officer safety and operational readiness.
Once at the remote site, officers remove the handset or tablet from the in-vehicle dock and use the D3 app to scan checkpoint(s) at the remote location. Scanning the barcode, iBeacon or RFID tag can prompt the officer to perform additional activities, such as filling an item’s condition report, doing a perimeter inspection or performing seasonal duties (i.e. removing snow from a vent covering). Each scan and any additional duties are logged in D3’s inspection module, and all entries are time-, location- and officer ID-stamped.
The subsequent benefit to the utility is multifaceted: security officers are tracked and perform multiple tasks; remote sites receive the maintenance they require, and dispatchers and on-the-ground security teams are more integrated, and therefore ready to respond.
5) CIP-104 Vulnerability Assessment & Security Plans
D3 can assist with several functional components within CIP-014. To begin, D3’s Entities database maintains a list of ‘functional entities’, per CIP-014-4.1, and assigns risk assessments to the site-level CPP contact. Forms can be built to match the utility’s preferred assessment format and information access controls are used to redact private information during third party reviews. Once approved, notifications can be set in D3 to remind users of future scheduled assessments, typically every 30 or 60 months, or as required by a regional NERC/FERC authority.
Utilities can also leverage D3’s data intake, data storage and report-building capabilities to support further CIP-014 activities such as storing key law enforcement contacts, documenting incidents and attacks, querying data for vulnerability and risk assessments, informing security plans, and intake of alerts from NERC/FERC, the Electric Reliability Organization (ERO), or the Electricity Sector Information Sharing and Analysis Center (ES-ISAC).
Click the button below to schedule your one-on-one software demo.
