

We are proud to announce the release of our most ambitious and innovative project yet: D3 SOAR 2.0. While it may be a bold claim to make, we truly see this new release as pushing the SOAR market forward with both improvements to previous capabilities and entirely new capabilities that no other platform offers. In this article, we will describe all the highlights of the new platform.
Before we get to all the features, here are what we see as the three most important takeaways for our current and future clients:
- D3 SOAR 2.0 has the most powerful playbooks. Our revamped playbook engine does more than just orchestrating actions across security tools. It now encompasses other task types that incorporate conditional factors, stage-based controls, and SLA monitoring.
- D3 SOAR 2.0 is the easiest platform to maintain. The cost of the person-hours that go into long-term maintenance of a SOAR platform can sneak up on buyers. This is not an issue with D3. Because of our codeless integrations, no user scripting is required, including no new scripts when an integrated tool is updated or internal rules are changed.
- D3 SOAR 2.0 is the only SOAR platform with the MITRE ATT&CK Matrix completely built-in. D3 correlates every event against ATT&CK TTPs then extracts all the related IOCs to find related events that might be part of the same attack. ATT&CK is at the core of D3 SOAR 2.0, with a dedicated dashboard to track adversary TTPs (tactics, techniques, and procedures) in real time.
If you want to see the platform in action, schedule a one-on-one demo with our product experts today.
Product Highlights
More than 200 Out-of-the-Box Integrations
D3 SOAR 2.0 supports more than 200 out-of-the-box integrations with cybersecurity tools such as SIEMs, Endpoint Detection and Protection, Threat Intelligence, Network Security, and ITSM. Clients’ SOC engineers can set up their preferred cybersecurity tools in a centralized place to connect with D3 SOAR. The D3 Data Model allows SOC teams to seamlessly digest, normalize, and transform raw event data, and set predefined mappings to D3 from a multitude of cyber event sources.
Codeless Playbook Editor
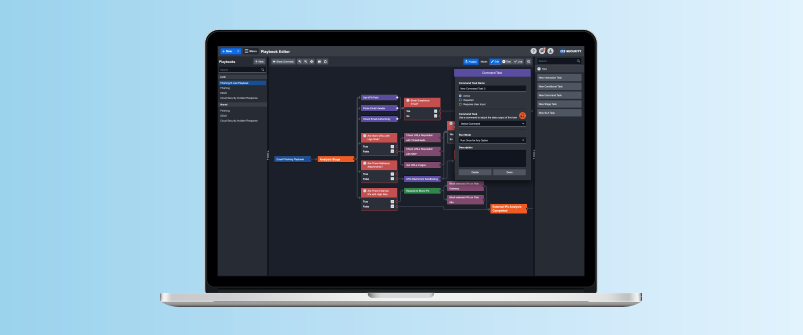
D3’s Codeless Playbook Editor allows SOC teams to easily modify D3’s out-of-the-box playbooks and set up complex workflow logic. The flexible nature of the Playbook Editor enables organizations to meet their unique incident response requirements. The workflow is visually mapped to allow SOC teams to contextually configure the orchestration and automation of tasks. This allows D3 to support the continuous interaction between the analyst, information sources, and action receivers.
Playbook Tasks offered in our SOAR 2.0 platform include:
- Command Task: This task allows the analyst to conduct comprehensive data processing, data transformation, system actions, and third-party integration actions. All of these actions are made possible via 400+ out-of-the-box commands across 200+ third-party integrations.
- Interaction Task: The SOC team can define best practices and SOPs using this task. The interactive questions and prompts will guide the analyst’s decision-making process throughout the cyber incident response.
- Conditional Task: The analyst can set up complex conditions using logical operators to create branching workflows.
- Stage Task: The analyst can auto-assign the relevant investigator(s) to an Incident and enforce stage-based access controls. This promotes cross-team collaboration across the various stages of an incident response lifecycle.
- SLA Task: The analyst can set precise service-level agreements for all tasks in the incident response lifecycle. The SLA task provides managers with reporting and monitoring of the SOC team’s compliance with SLA guidelines.
Time-Based Link Analysis
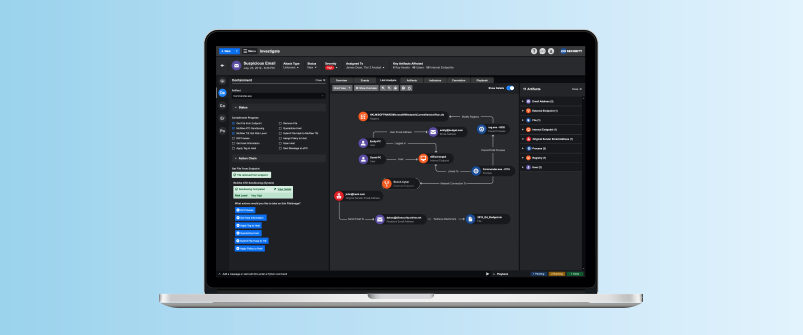
Link Analysis provides a visual representation of the relationship between incidents, artifacts, and techniques. It allows the analyst to gain a comprehensive view of what has happened, and easily identify any correlated components like TTPs used by the adversary.
One main benefit of Link Analysis is that the analyst can understand the relationships between artifacts and events without having to read pages of reports. The on-screen visual also allows them to spot attacks where traditional detection methods fail to provide adequate information.
Time-Based Link Analysis highlights include:
- Visualizing relationships between events, incidents, artifacts, techniques, and more.
- Enabling the analyst to review the whole picture of a cyber attack before taking action.
- Event Timeline to view how the attack progresses over time.
- Highlighting artifacts with bad reputation scores to speed up analysis.
- Quick access and easy navigation to artifact details.
Automated Event & Artifact Enrichment
D3 automatically enriches Events and Artifacts through a variety of threat intelligence platforms, the client’s local systems, and D3’s database. This enables the analyst to quickly obtain additional information, such as the artifact’s reputation, to facilitate the investigation and incident response.
Enrichment highlights include:
- Event categorization using the MITRE ATT&CK Framework. This can be based on system and/or user-defined technique search criteria.
- Automated reputation checks on artifacts such as URLs, Files, and IPs, using a variety of external tools like VirusTotal.
- Sandboxing artifacts such as URLs and Files.
- Generating file hashes on all retrieved files to be used in analysis.
- Value-added enrichments such as providing snapshots of suspicious websites.
Simplified Event Correlation & Deduplication
D3 SOAR 2.0 automatically correlates events and incidents from local and external data sources. Examples of these external data sources include SIEM, email servers, Endpoint Detection and Protection, and Network Security.
The event deduplication process performed by the system ensures duplicate events are identified and subsequently grouped into a new incident or linked to an existing incident.
This substantially accelerates the analyst’s process of monitoring large volumes of security alerts by intelligently showing correlated events so that the analyst can remove false positives in bulk.
Granular Access Control
D3 SOAR 2.0 introduces stage-based access controls at the playbook and incident level. The incident owner is provided with the flexibility to customize privileges, workflows, and auto assignments of investigators based on the incident stage.
In addition, D3 offers granular access control at the user, role, group, and site level. The SOC Team can restrict what information is visible in the event, incident, and playbook. This control can be extended to user privileges when performing certain actions, such as editing an incident description.
Group level controls allow the SOC team to be logically separated based on the needs of the department. This separation of the application helps streamline processes for the department and controls the types of information each team member can access.
Site level controls allow large corporations to set up individual environments for their unique organizational structures and requirements.
Multitenancy Support
D3 SOAR 2.0 has been designed to support granular access control, centralized account management and cloud big data use-cases for MSSP clients and cloud big data multitenancy.
D3’s distributed architecture and cross-site Single-Sign-On allows MSSPs’ new clients to be onboarded within a few minutes with access-controlled visibility and isolated databases. Incident response playbooks can be established, standardized, and automated for each client. Customizable SLAs can be incorporated to increase service delivery and build customer trust.
D3 enables MSSPs to collaborate with clients in a unified workspace for incident investigation. MSSPs can perform data enrichment and remediation activities in client-specific playbooks directly on the client network with secure remote connection for streamlined managed service operations and real-time data visibility.
D3 supports cloud big data multitenancy through the ability to connect to big data services like Microsoft Azure and Amazon AWS. D3 ingests events and feeds them into D3’s multitenancy pipeline. This provides physical and logical separation, and access control-based data centralization and sharing. Privileged users can easily maneuver across physical and logical separations.
Advanced Reporting & Analysis
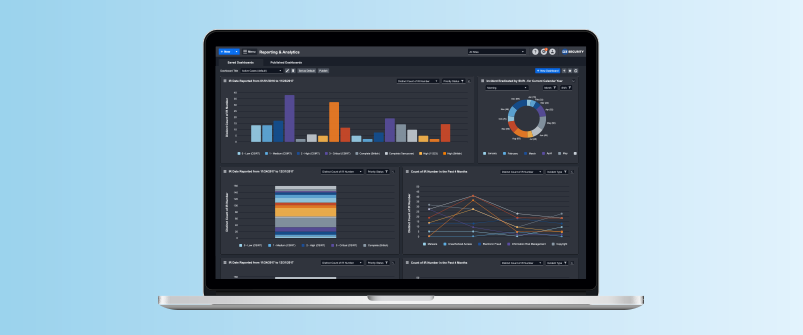
The Reporting & Analytics dashboard provides a space for SOC managers or executives to review operational KPls.
Key metrics are provided out-of-the-box to help track the organization’s security posture and the SOC team’s performance. These features include the ability to:
- Build new charts and slice-and-dice reports on demand.
- Conduct complex analysis using multiple dimensions to reveal patterns and trends.
- Schedule reports to be sent to key stakeholders.
Phishing Email Campaign Case Study
Below is an example of how the SOC Team would typically respond to a phishing email campaign using D3 SOAR 2.0:
- An internal user forwards a suspicious phishing email to the phishing email reporting inbox.
- The phishing email event is automatically ingested into the D3 platform. D3 SOAR supports ingestion from a multitude of integration sources, so the SOC team has an all-in-one place to triage, investigate, and take action on all the security events for the organization.
- Artifacts from this phishing email event will be automatically extracted and enriched via data enrichment tools such as Virus Total, Webroot, URLScan.io, McAfee TIE, and MaxMind. Extracted artifacts include Email Addresses, External IPs, URLs, Files, and Email Headers.
- The Tier 1 Analyst will use the event list in the central dashboard to review event details and conduct their initial analysis. The event details contain key enrichment information, such as the artifact reputation and the linkages between artifacts, to facilitate the analyst’s event analysis.
- After the analysis, the Tier 1 Analyst can either escalate or dismiss an event. For escalation, the analyst will select a relevant playbook to initiate automated actions such as Data Enrichment or Analysis and Remediation playbook tasks.
- The assigned Tier 2 Analyst will be automatically notified about the new incident and can begin their analysis and the remediation phase.
- Within the Incident workspace, the Tier 2 Analyst is given multiple dashboards with which to analyze the situation.
- Suggested playbook tasks, guided procedures, and conditional prompts are provided to help guide the analyst in the analysis and remediation process.
- The SOC Manager will review the incident summary once the Tier 2 Analyst has completed the analysis and remediation phase. At this time, they will be able to make the final decision to close the incident.
- Upon the closing of the incident, the phishing email reporter will be automatically sent an email notification with the investigation status.
