SOAR FEATURE
Security Automation and Orchestration
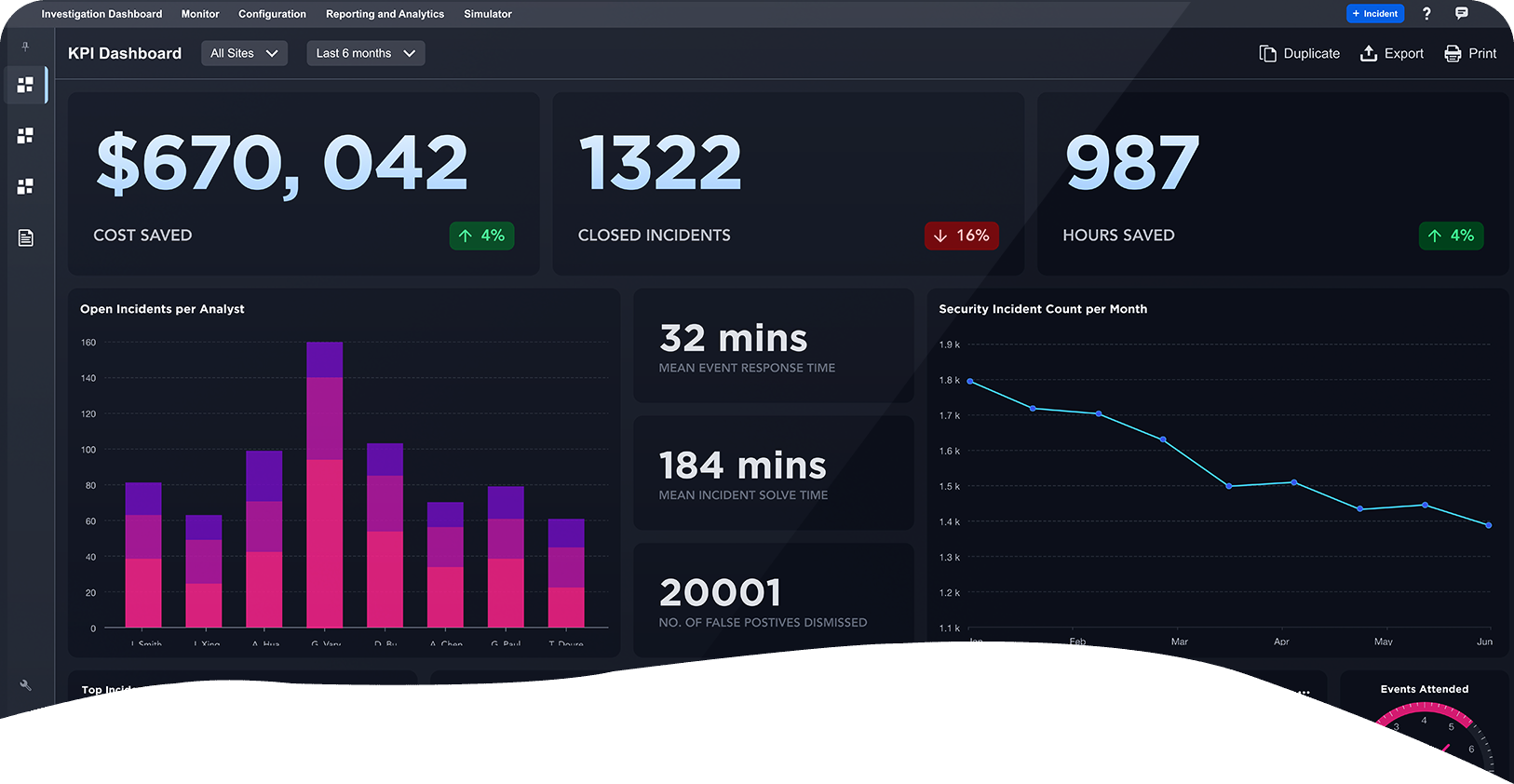
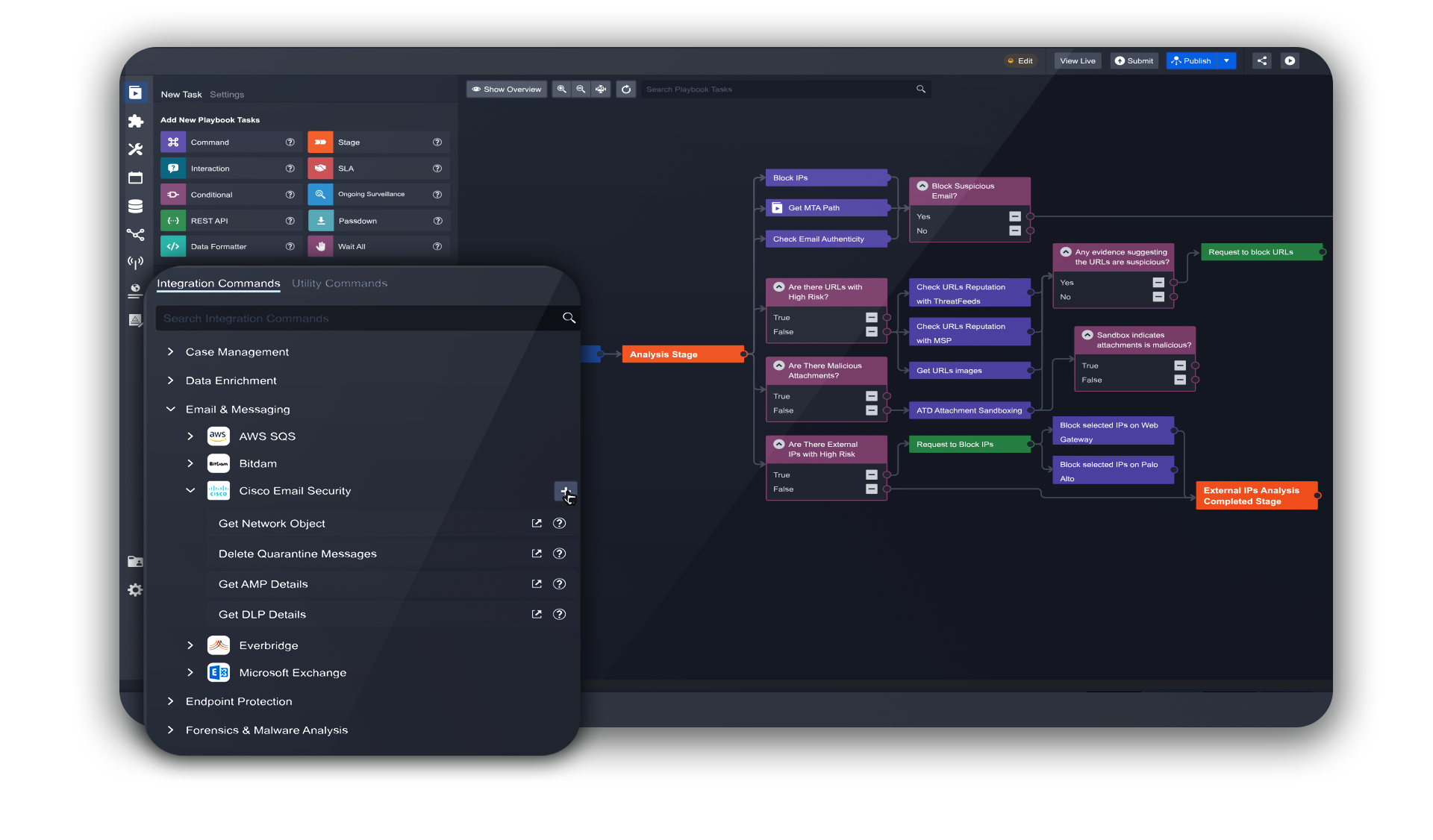
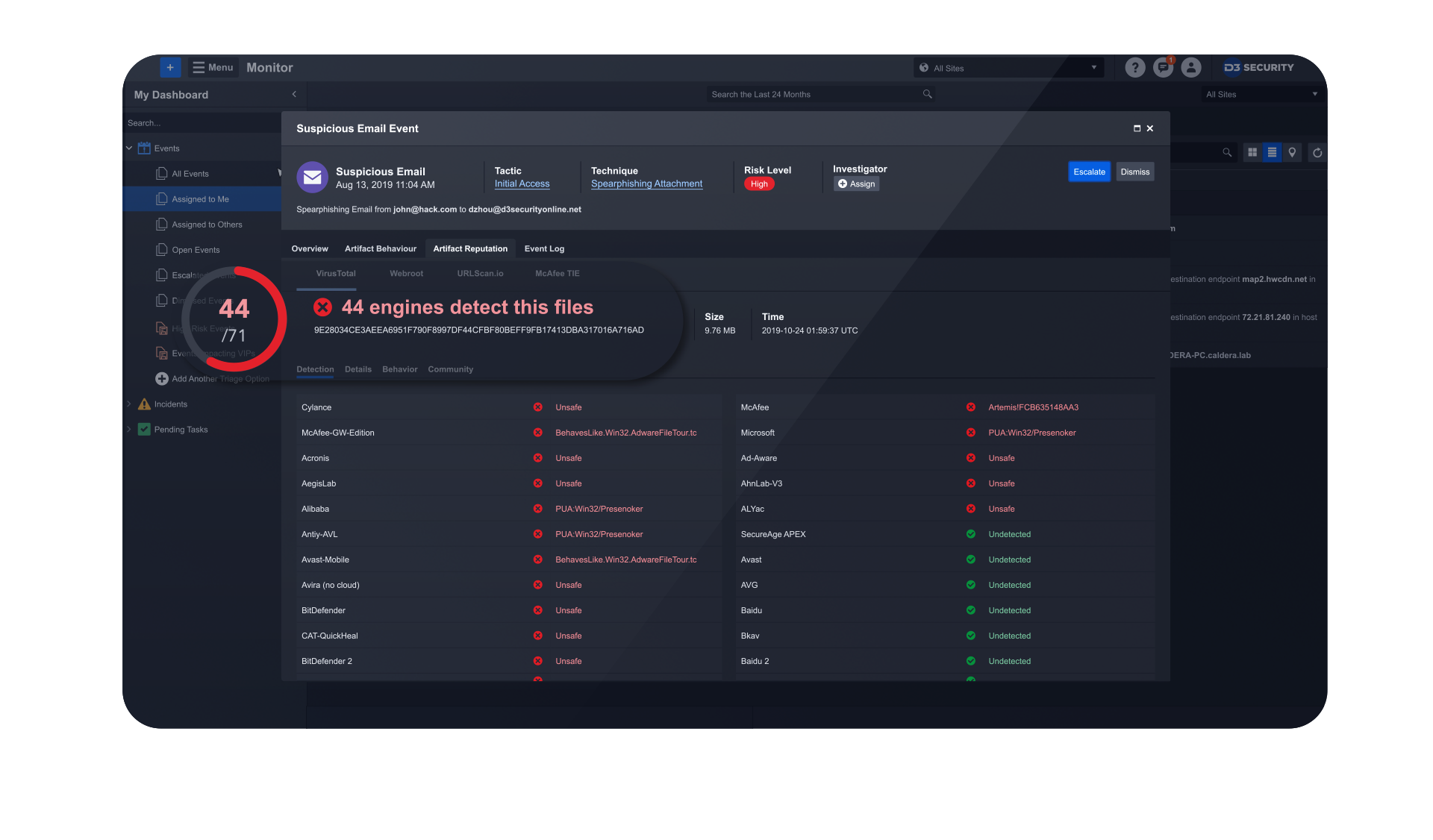
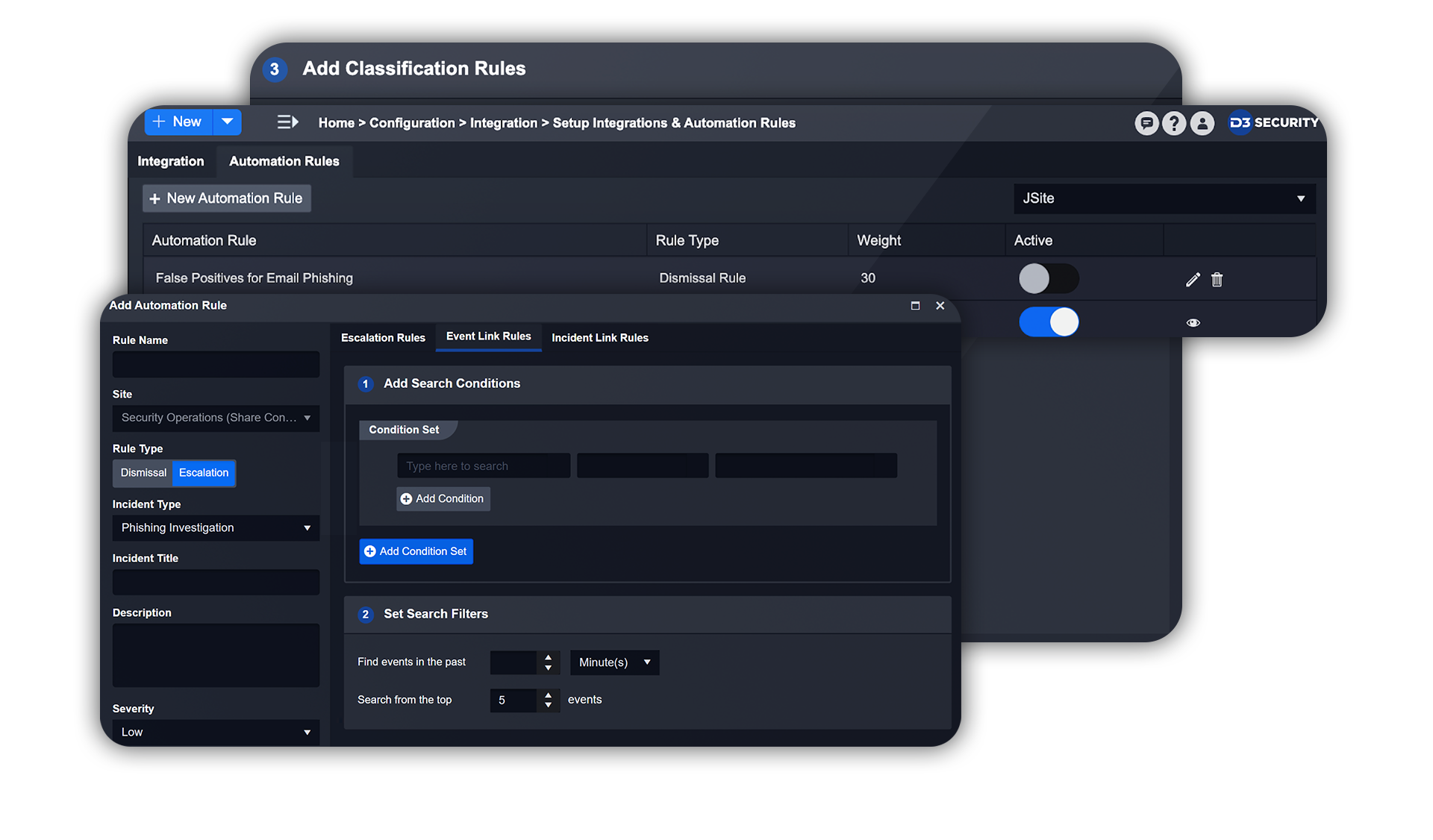
Smart SOAR makes security orchestration, automation and response easy. Connect your tools using REST API and vendor-agnostic integrations, and automate workflows without coding. Attract and retain SOC staff, maximize all of your technology investments, and innovate faster than ever.