Cybersecurity Incident Response
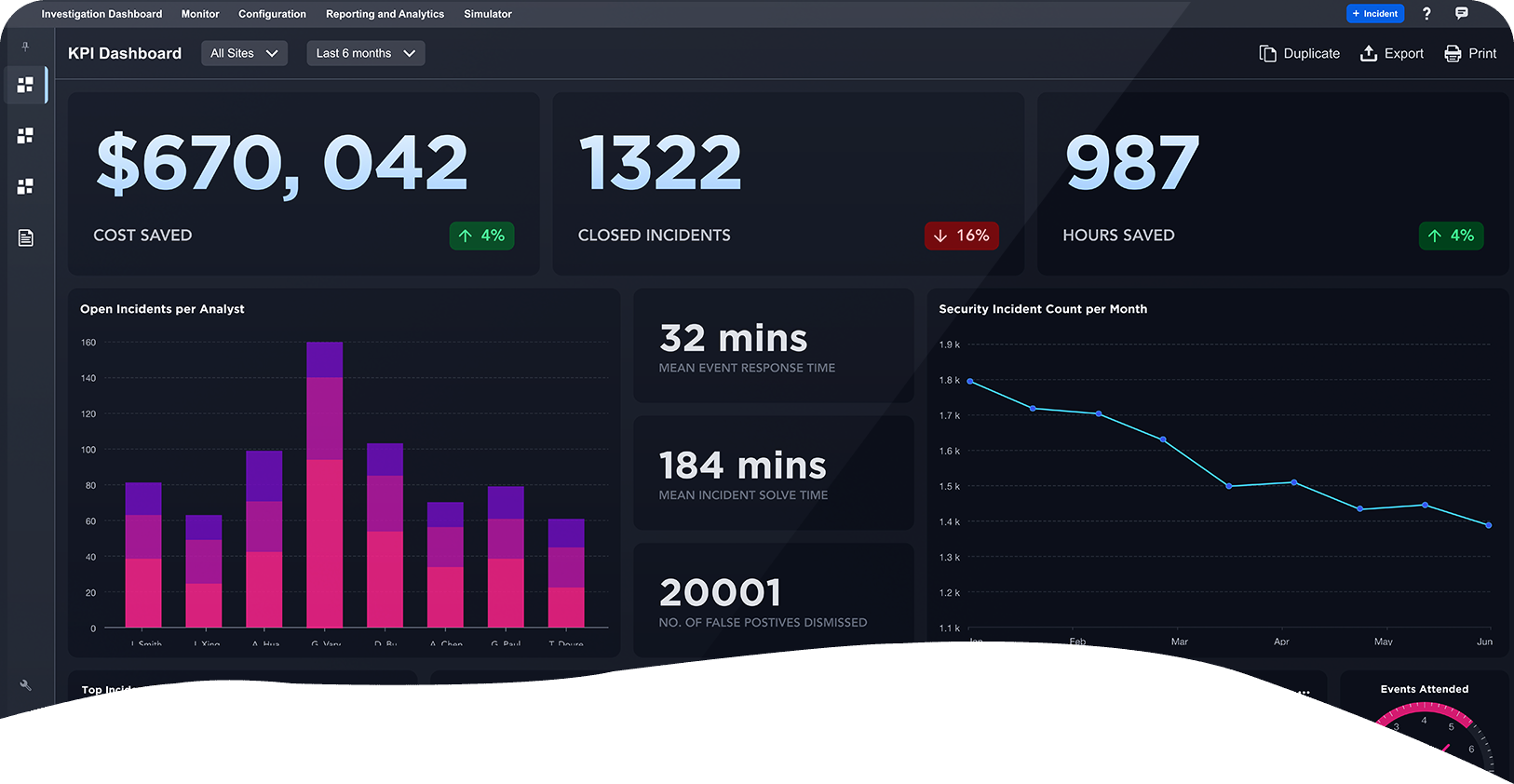
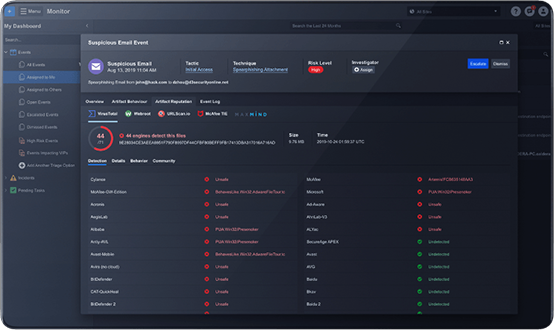
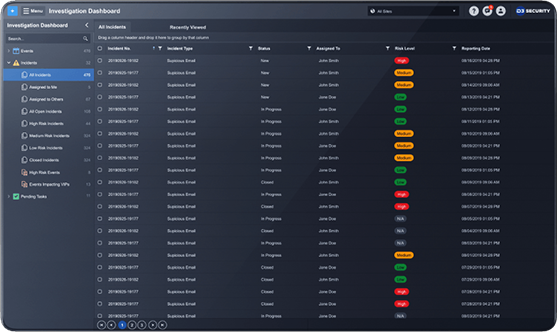
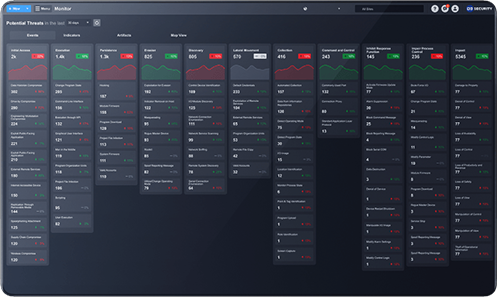
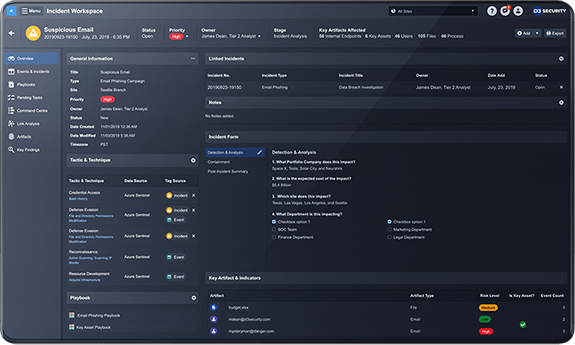
Smart SOAR brings security orchestration, incident response and case management together, enabling your team to harness the power of its processes, people and technology. Automate incident response and keep your team laser-focused on the most comprehensive and pervasive threats.