
Hyperautomation is a term coined by Gartner at the start of this decade to describe a strategic approach that integrates different tools and technologies to automate business and IT processes as much as possible. The term has many implications and applications in the field of cybersecurity, given that SOC teams are overworked and looking for ways to minimize manual tasks.
As a pioneer in SOAR (Security Orchestration, Automation and Response) D3 Security was recognized as a representative vendor in the security hyperautomation space by Gartner in their 2021 research report: Emerging Technologies and Trends Impact Radar: Security. Security hyperautomation continues to be a central theme in Gartner’s latest emerging technologies report, released in late 2023. In this blog, we’ll take a look at what Hyperautomation is and isn’t, and share some benefits of hyperautomation in the SOC.
What is Hyperautomation?
Gartner defines Hyperautomation as:
A business-driven, disciplined approach that organizations use to rapidly identify, vet and automate as many business and IT processes as possible. Hyperautomation involves the orchestrated use of multiple technologies, tools or platforms, including:
- Artificial intelligence (AI)
- Machine learning
- Event-driven software architecture
- Robotic process automation (RPA)
- Business process management (BPM) and intelligent business process management suites (iBPMS)
- Integration platform as a service (iPaaS)
- Low-code/no-code tools
- Packaged software
- Other types of decision, process and task automation tools
The key takeaway here is that hyperautomation is not a specific type of technology, but a strategic business initiative to identify, evaluate, and automate business and IT processes. It’s achieved by orchestrating the use of multiple automation technologies such as AI, machine learning, RPA, low-code and other automation tools. Hyperautomation is not:
- A short-term cost-cutting measure
- Simple task automation or RPA alone
- A one-time implementation of automation tools
- Limited to a specific department or process
- Intended to replace human workers entirely
Hyperautomation Vs. Automation: What’s The Difference?
Hyperautomation is a more advanced and comprehensive approach to process automation that leverages multiple technologies, enables end-to-end automation, provides decision-making capabilities, offers scalability and flexibility, and facilitates continuous process improvement. Let’s examine these points in detail to understand how hyperautomation is different from traditional automation:
Scope and Complexity
Automation typically focuses on automating specific, repetitive tasks or processes within a single system or application. In contrast, Hyperautomation takes a holistic, end-to-end approach to automate complex business processes that span multiple systems, data sources, and decision points.
Decision-Making Capabilities
Basic automation typically follows predefined rules and lacks the ability to make complex decisions or adapt to changing conditions. Hyperautomation leverages a variety of technologies to enable intelligent decision-making capabilities. It can analyze data, learn from historical patterns, and make informed choices, allowing it to handle more complex and dynamic processes that require cognitive abilities.
Scalability and Flexibility
Traditional automation solutions may require significant effort to adapt to new tasks or processes, limiting their scalability. Hyperautomation is designed to be highly scalable and flexible, allowing organizations to quickly adapt and accommodate a wide range of processes and use cases across different domains.
Continuous Improvement
While basic automation solutions may require manual adjustments when processes change, Hyperautomation systems are designed for continuous improvement. They can identify inefficiencies, bottlenecks, and opportunities for optimization and suggest or implement improvements automatically, enabling ongoing process refinement and optimization.
Benefits of SOAR-Driven Hyperautomation in Cybersecurity
Many security teams rely on basic automation tools that can handle simple tasks, but often fall short when it comes to complex workflows. Additionally, SOC environments often include a mix of security tools from different vendors, further complicating the process.
Smart SOAR addresses these challenges head-on, making it the ideal platform for enabling hyperautomation in your SOC. Its no-code playbook editor empowers security analysts to build complex automations without writing a single line of code. Hundreds of D3-maintained integrations and commands are readily available, allowing you to seamlessly connect and orchestrate actions across your entire security stack. This simplifies automation significantly, freeing up valuable analyst time and resources. Plus, Smart SOAR ensures easy integration with new security tools you might adopt down the road, enabling streamlined end-to-end incident response regardless of your current or future security stack.
Smart SOAR’s hyperautomation capabilities have helped SOC teams reduce false positives by over 99%, and achieve 8x faster response times. As your infrastructure grows, Smart SOAR accommodates and expands your cybersecurity capabilities. Smart SOAR enables:
Consistent and Standardized Response: Smart SOAR playbooks enforce consistent response protocols across your security operations. This reduces human error and ensures everyone follows the same steps when responding to incidents. Playbooks can be shared and collaboratively edited across security teams, fostering better communication and knowledge sharing.
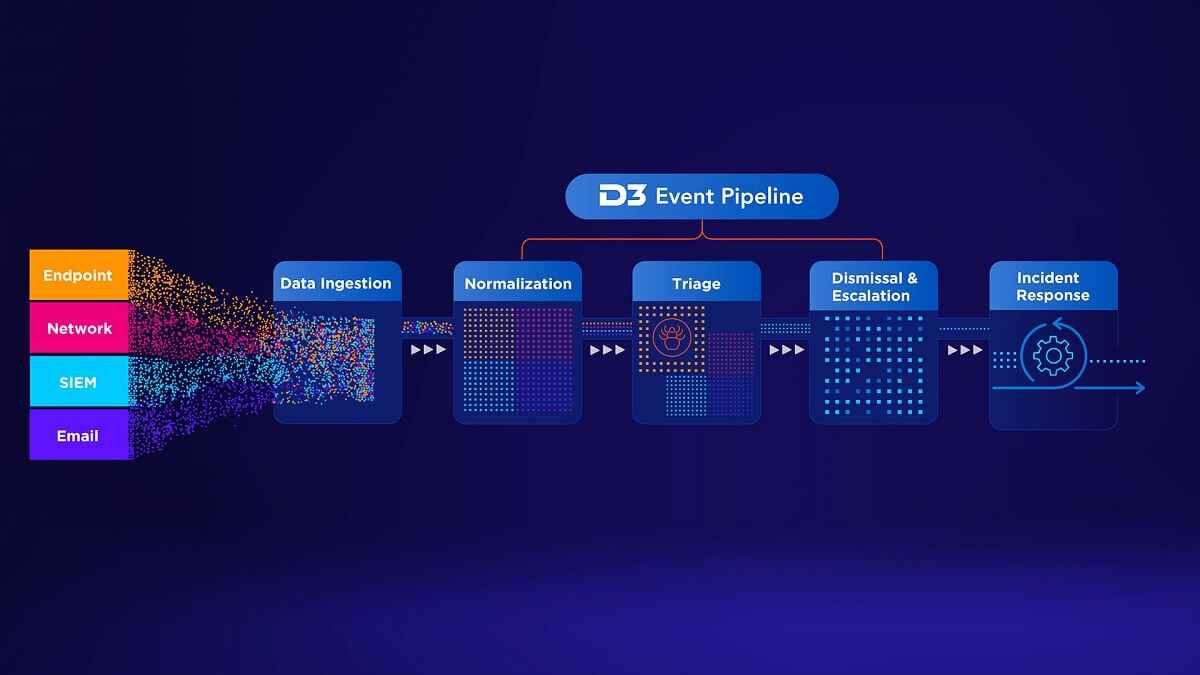
Automated Triage and Escalation: Smart SOAR’s hyperscalable Event Pipeline is a global playbook that is triggered upon the ingestion of an alert from any source (EDR, SIEM, etc). It automatically normalizes, deduplicates, enriches, and triages alerts, dismisses false-positives, and escalates true positive alerts to high-fidelity incident records. Incidents are enriched with contextual data to provide analysts with a complete picture to make an informed decision.
Smarter Incident Response: Repetitive tasks like artifact analysis and initial containment can be automated through predefined workflows in Smart SOAR’s codeless playbook builder, freeing up valuable analyst time for in-depth investigations instead of repetitive tasks.
Automated Threat Hunting: Smart SOAR automates threat hunting tasks that were previously manual. It uses playbooks to automate incident triage, correlation, and escalation. It can also automate searching for indicators of compromise (IOCs) and respond with predefined actions. Smart SOAR allows for scheduled searches for IOCs and integrates with other security tools. This enables continuous threat monitoring and improves analyst efficiency.
Automated Compliance Checks: Smart SOAR can ingest Software Bill of Materials (SBOM) data and run automated vulnerability assessment checks to ensure continuous monitoring and compliance on internal devices and on third-party vendors.
Read: SOAR Use Case: Employee Onboarding and Offboarding
Smart SOAR’s HyperAutomation Saves You Time and Money
Gartner says that organizations can expect to lower operational costs by 30% by leveraging hyperautomation technologies. D3’s Smart SOAR platform has been at the forefront of enabling hyperautomation and as such, has been acknowledged as a representative vendor in the space by Gartner. Smart SOAR’s vendor-agnostic stance helps you leverage orchestration capabilities to the fullest, regardless of your security technology stack. D3 takes responsibility for maintaining the integrations, helping you coordinate response actions across multiple security tools and technologies with ease. Our no-code playbook editor is versatile and easy to use, and supported by hundreds of utility actions that help you automate a wide range of security use cases. Schedule a demo to see how Smart SOAR helps free up your team’s time for strategic projects that truly move the needle.
