
Incident response is a critical process for any organization to minimize the impact of cyber attacks. However, there are two key challenges faced in this process: spending a significant amount of time investigating false positives and handling “yellow” alerts. Being able to accurately set an incoming alert’s severity or dismiss it as a false positive before it hits your alert queue saves teams hundreds of hours every week. In other SOAR tools, every ingested alert enters a queue and triggers an incident playbook. In Smart SOAR, however, users can run event playbooks, which trigger on ingestion, and can automatically triage or dismiss incoming alerts. In this blog post, we will show you how event and incident playbooks can be used together to filter out unnecessary alerts.
Architecture
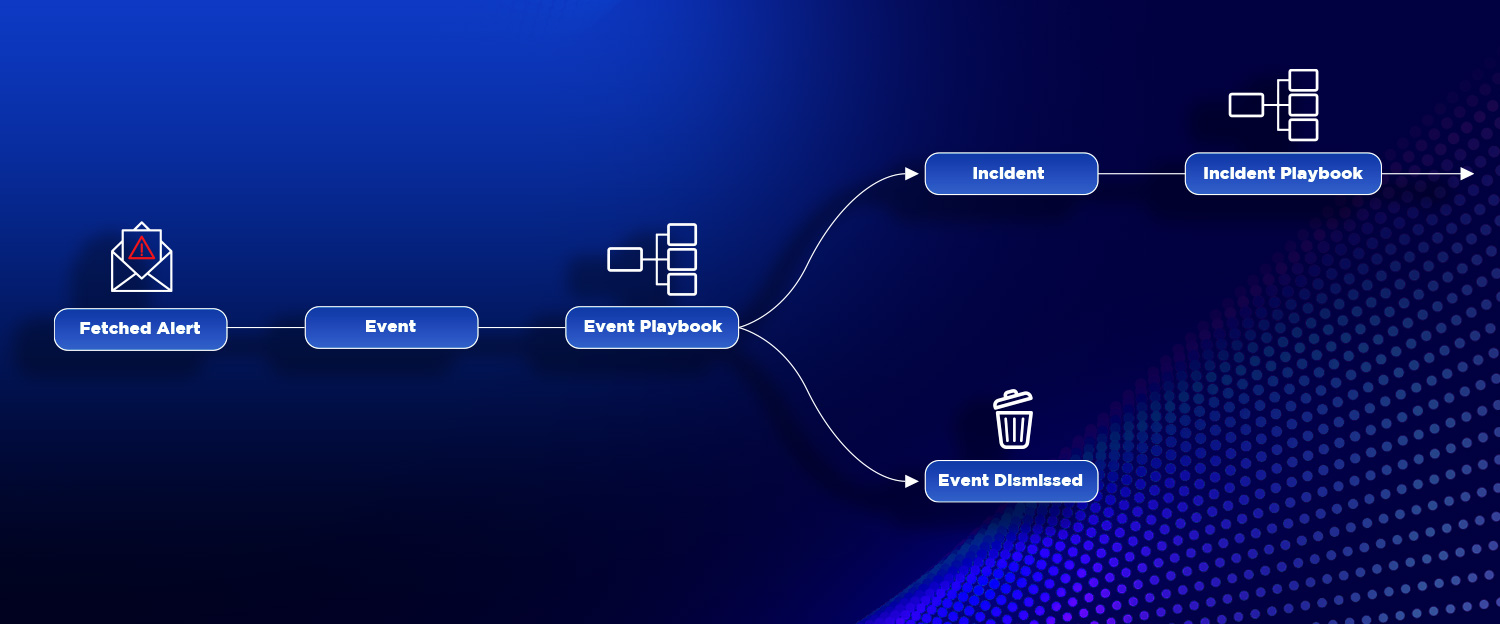
In Smart SOAR, alerts are separated into two categories: events and incidents. Alerts are initially ingested as events and are escalated into incidents only if they meet certain criteria.

The reason we have two levels of alerts in Smart SOAR is so that users can run automated workflows at each level. At the event level, users typically execute correlation, triage, and other filtering logic, while the incident level playbooks consist of enrichment and response actions.
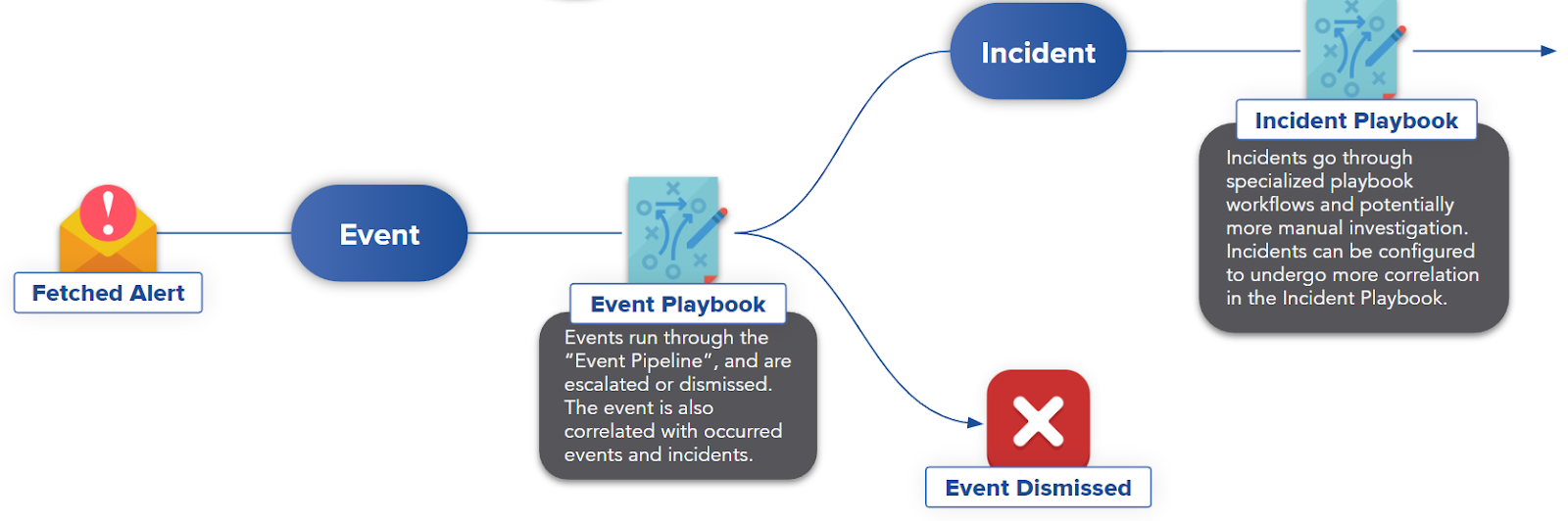
Automation at the Event Level
When an alert is ingested into Smart SOAR, it is first processed by an event playbook. The event playbook can consider third-party data when determining an incoming alert’s priority and then classify it critical, high, medium, low, or informational. It can also correlate it to an existing incident or dismiss it entirely.
Here, we show how threat intelligence platforms can contribute to the weighted risk level of an incoming alert, and how that can determine if the alert is dismissed or escalated:
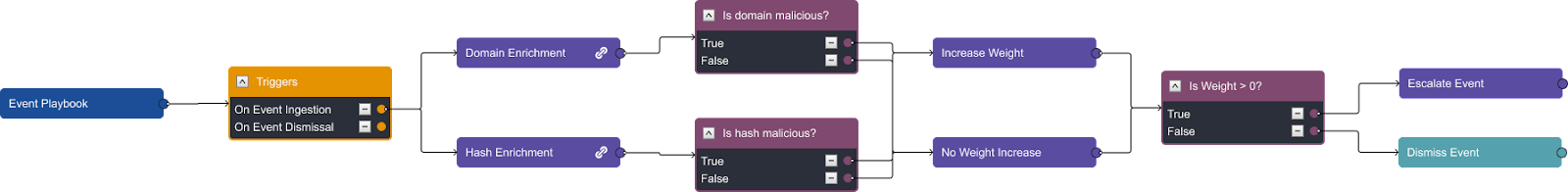
Digging into the stages further we see:
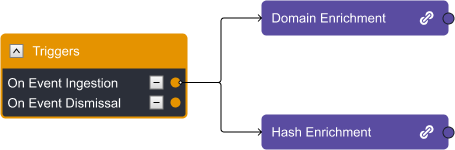
At step one, the IOCs from an alert are extracted and run through the appropriate enrichment actions. Here, we’re using domains and hashes as an example. The purple tasks contain nested playbooks, which you can identify by the link icon to the right. When reviewing the underlying playbook, we can see four different threat intelligence platforms being used to compile a risk score for this artifact:

Those scores are summarized and passed upward to the parent playbook where conditional tasks review the scores and move the alert down either the “dismiss” or “escalate” path:

The runtime for an event playbook is typically less than three seconds. More complicated workflows are executed in under 15 seconds. Data from other tools can be included in this process, such as user information from Active Directory or device information from SentinelOne.
Automation at the Incident Level
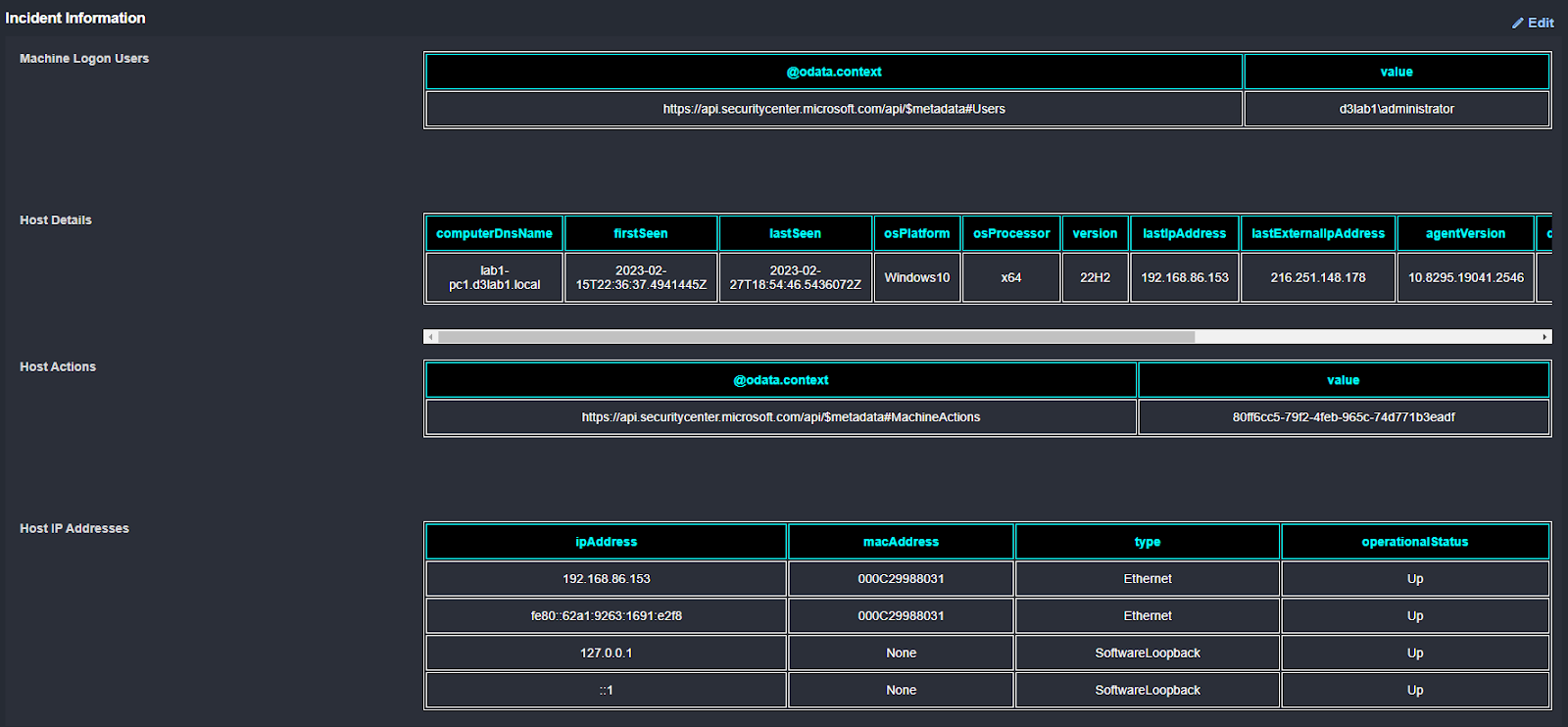
When an event is escalated into an incident, playbooks are executed to collect additional information and take action to contain the threat. In the workflow below, Microsoft Defender for Endpoint is used to collect:
- Active users on the device in question;
- Details on the host, including operating system and asset value;
- The host’s IP addresses, and;
- The actions taken on that device.
That information is summarized and presented to the analyst in the Incident Overview:
Once the investigation is complete, users can trigger remediation tasks such as quarantining the endpoint, blocking malicious artifacts, and resetting user login credentials.
![]()
Conclusion
Smart SOAR is the only SOAR tool on the market that has two-tiers of playbook automation. By giving our users the ability to run triage and correlation playbooks at the event level, their investigation teams are left with a smaller, more accurately prioritized queue of incidents to investigate. With automation at the incident level, contextual data is automatically gathered and displayed for their review, and remediation actions can be easily triggered to prevent threats from escalating.
