
The healthcare industry is a lucrative target for cybercriminals. Healthcare organizations are often laggards in adopting cybersecurity and data management best practices, a vulnerability that criminals have been quick to exploit. In the first half of 2017, 149 breaches have compromised nearly 2.7 million Protected Health Information (PHI) records from across the country. Out of those 149 breaches, 53 have been categorized as hacking or IT incidents, including four out of the five largest breaches. Overall, these hacking/IT incidents range from using unsecured channels for the transfer of patient data to ransomware attacks and everything in between.
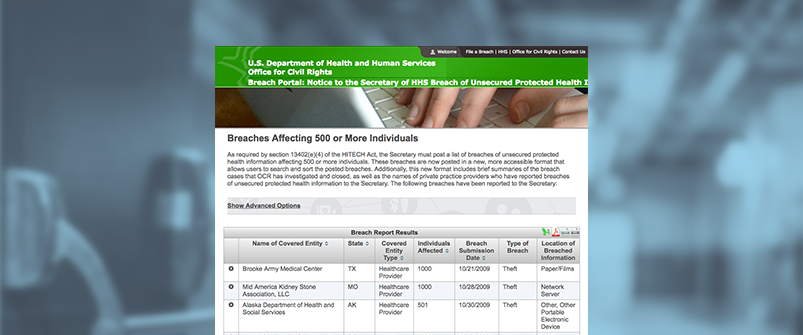
Under The Health Insurance Portability and Accountability Act (HIPAA), the task of protecting patients’ health information is the responsibility of the Office of Civil Rights at the Department of Health and Human Services. Since 2009, the DHHS has published a “wall of shame” that lists healthcare organizations that have reported health information breaches affecting 500 or more individuals.
The Consequences of the “Wall of Shame”
Unfortunately, the immediate operational, financial, and regulatory impacts of a breach are not the only consequences that are associated with breached records. When an organization is featured on the “wall of shame”, its name, the number of records exposed, and a short description of the incident are prominently featured on the list, which is easily accessible by the public.
In this day and age, the long-term reputational consequences of being featured on the “wall of shame” can be detrimental to any healthcare organization regardless of size or the nature of the incident.
In the name of transparency, the “wall of shame” is indexed by all search engines, meaning that when someone conducts an online search of an organization that was involved in a significant breach since 2009, the dreaded “wall of shame” will most likely come up in the first few search results. This can spell disaster for smaller clinics or physician’s offices since most patients will conduct an online search before their initial consultation with a new healthcare provider.
Aside from appearing on online search results, being a member of the “wall of shame” can also wreak havoc to any organization’s brand, which can translate into thousands or millions of dollars in lost revenue in the long run.
Unfortunately, it is no longer just large hospitals and healthcare conglomerates that are at risk of suffering a breach and appearing on the “wall of shame”. With the increase in hacking and ransomware attacks perpetrated against the healthcare community, the risk of falling victim to these types of attacks is increasing by the day. Smaller organizations are more vulnerable to cyber-attacks, since most of them don’t have sophisticated detection and alert capabilities.
According to Mac McMillian, president of security consultancy Cynergis Tek, more hacking related breaches, including those involving ransomware attacks, will be added to the wall of shame in the months to come. The risk of falling victim to a ransomware or other form of online attack that can compromise records means healthcare organizations ought to be prepared. Seemingly innocuous actions such as accessing medical records from public Wi-Fi or clicking on a link from an email could compromise data or infect internal systems with ransomware.
Recent large scale ransomware attacks, such as WannaCry, have affected healthcare organizations across the world. For example, in the UK, WannaCry crippled the NHS by not only exposing records but also temporarily halting several essential healthcare services. As mentioned in a previous blog post, WannaCry could have been averted if organizations had taken the right precautions. Recent reports also suggest that cybercriminals have been specifically targeting small and medium healthcare organizations with powerful ransomware attacks. Unfortunately if an organization suffers a data breach due to ransomware, it will most likely find itself on the dreaded “wall of shame”.
How Can Healthcare Organizations Minimize Risk?
Small- and medium-sized healthcare organizations can reduce their likelihood of falling victim to ransomware and being featured on the “wall of shame” by following some simple practices.
First, all users must be educated on the dangers of clicking on unknown links and accessing unfamiliar websites from workstations within the organization’s network. All organizations should brief employees on the basics of online safety as well as instruct employees on how to report any suspicious messages or links.
Ensure all systems are patched and up to date. This is as easy as making sure all workstations and other online devices are up to date with OS updates and security patches. Many medical equipment systems are still using unsupported or legacy systems such as Windows XP. These systems are more vulnerable to hacking and should be updated as soon as possible.
Ensuring firewall and anti-virus software is up to date and well maintained might be obvious but it can easily be overlooked at smaller organizations where there are no dedicated full time IT resources.
Finally, healthcare organizations should invest in incident response software. While incident response solutions are not primarily preventative, they are critical tools for quickly detecting and responding to attacks like ransomware, in order to limit the number of records breached. A strong incident response platform will also help you collect and understand the incident data you need to close security gaps and prevent future incidents.
To learn about D3’s Incident Management Platform—which leading healthcare providers like UPMC and Mayo Clinic use to report, manage and respond to security incidents—schedule a demo today.
