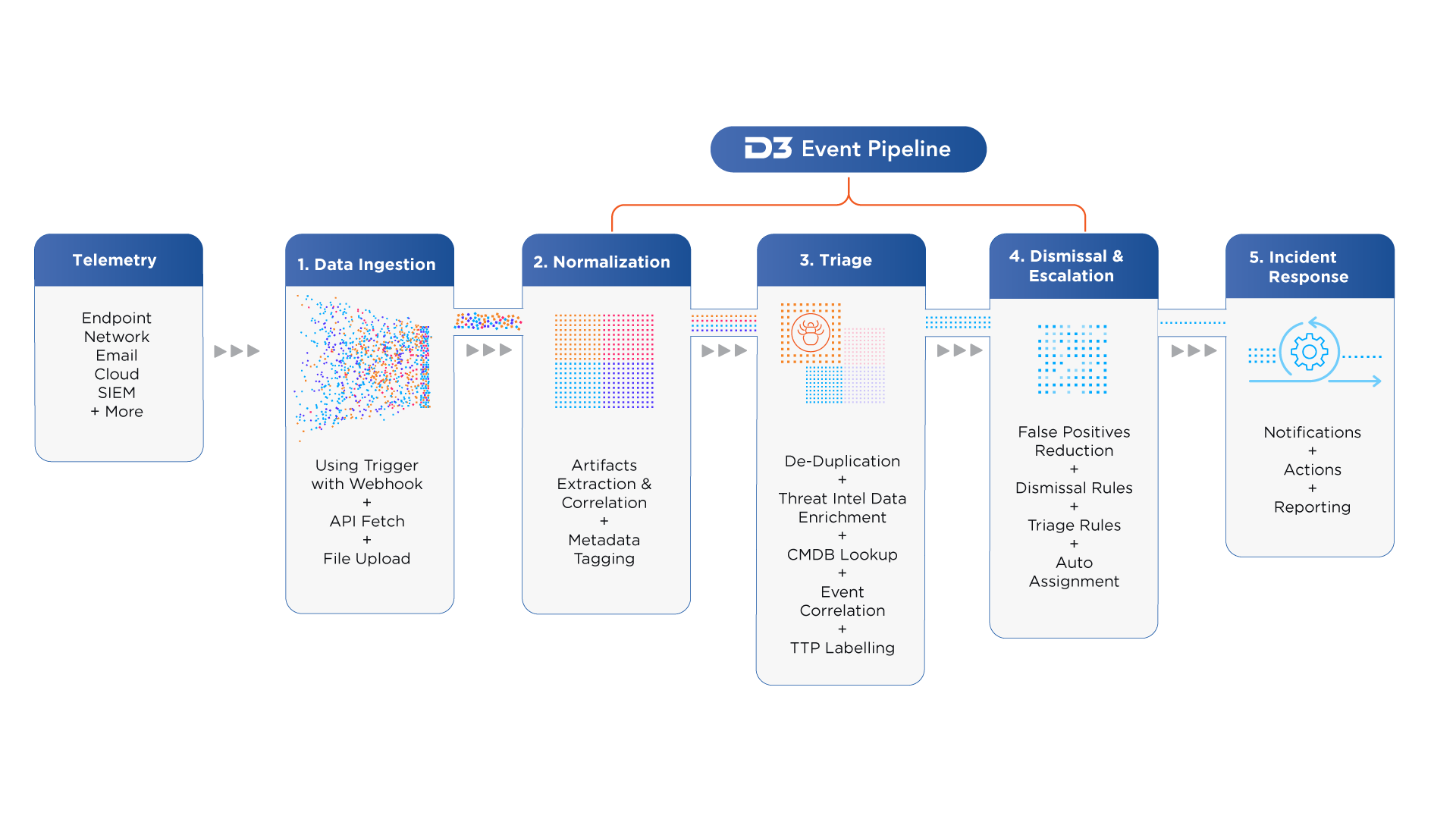
D3’s Smart SOAR has a deep integration with Microsoft Sentinel. This integration gives security teams the ability to triage, investigate and respond to Sentinel alerts and Sentinel incidents, in the consolidated, automation-powered D3 work space. Events from Microsoft Sentinel and any other products are ingested into D3 where they are instantly normalized, de-deduplicated, enriched, and triaged by Smart SOAR’s built-in Event Pipeline, so you can identify and prioritize malicious activity at machine speed and scale. When further investigation is warranted, incident responders can use D3 to search for related IOCs, IOBs and TTPs across the full security stack, correlating data from endpoint, email, network, identity, etc. The full picture of an incident is understood, triggering remediation workflows with surgical accuracy.
Why It Matters
Security Information and Event Management (SIEM) products are core components of many security programs; however, even the most sophisticated organizations struggle to utilize SIEM for rapid threat detection and response. The level of expertise required to operate a SIEM effectively, combined with the lack of security resources and high rate of false positives creates a significant burden for security teams.
Smart SOAR’s Sentinel integration includes numerous capabilities, which together have the effect of minimizing the amount of noise, and generating fewer, higher-fidelity alerts for investigation. Here’s a brief look.
Easy Setup
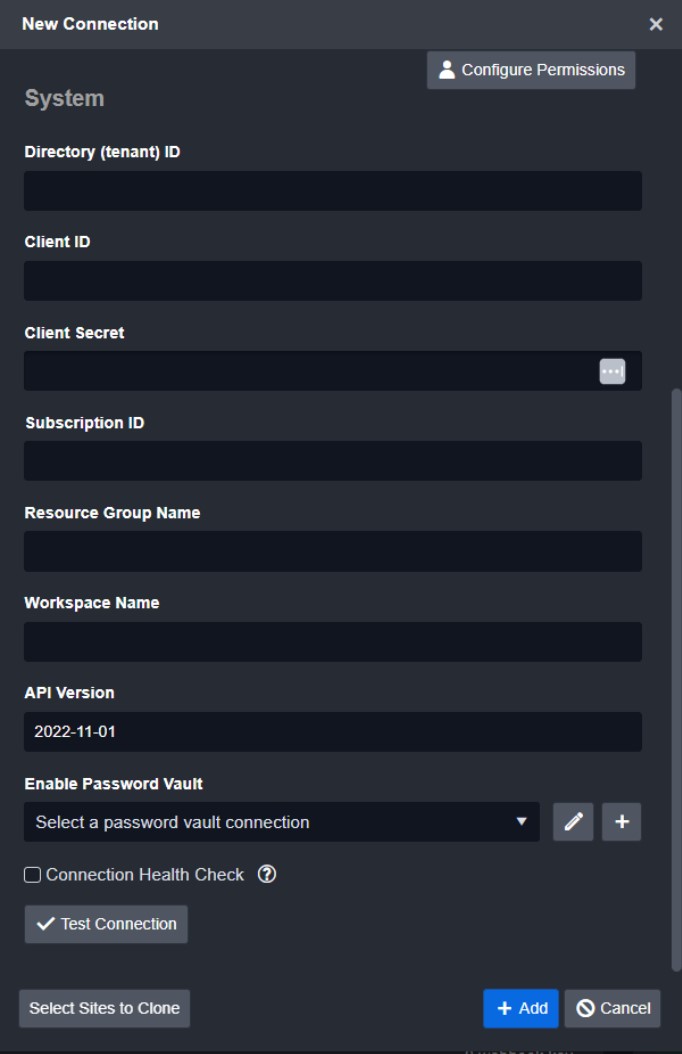
You can connect your Sentinel instance to Smart SOAR in minutes. Here’s what you need:
- Directory (tenant) ID
- Client ID
- Client Secret
- Subscription ID
- Resource Group Name
- Workspace Name
- API Version
Compatibility with Sentinel’s Alert Tables
In D3, you can choose any of the three main Sentinel tables as your data source: Security Event, Security Alert, or Security Incident. Unlike other SOAR security systems, which have trouble handling the constantly changing information in Sentinel Incidents, D3’s incident ingestion system collects all current and future security alerts and groups them together into one incident. This way, if a new alert is added, it will be included in the existing incident, not a new one.
Additionally, some security alerts come with a Kusto Query Language (KQL) query in their extended properties, to help with investigations. However, running this query can be time-consuming. D3 makes things easier by automatically running the query and updating the list of artifacts, saving your team time and effort.
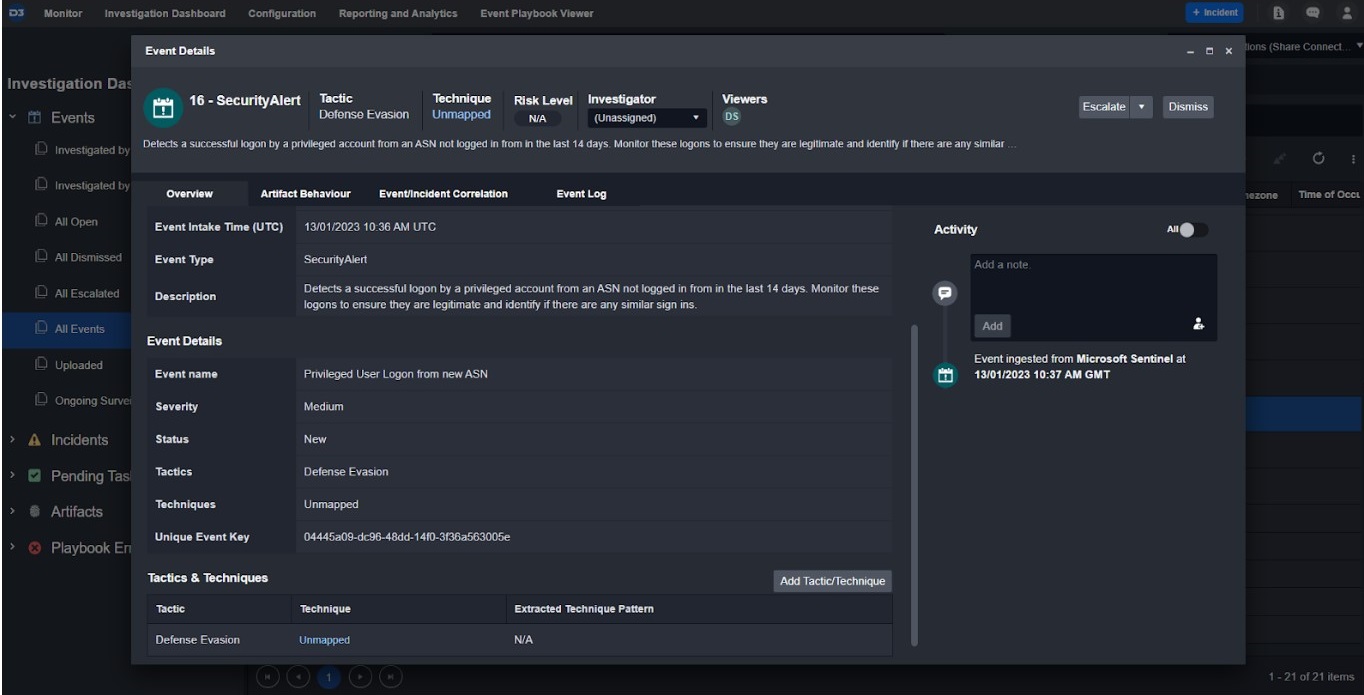 Security Alert ingested as an Event
Security Alert ingested as an Event
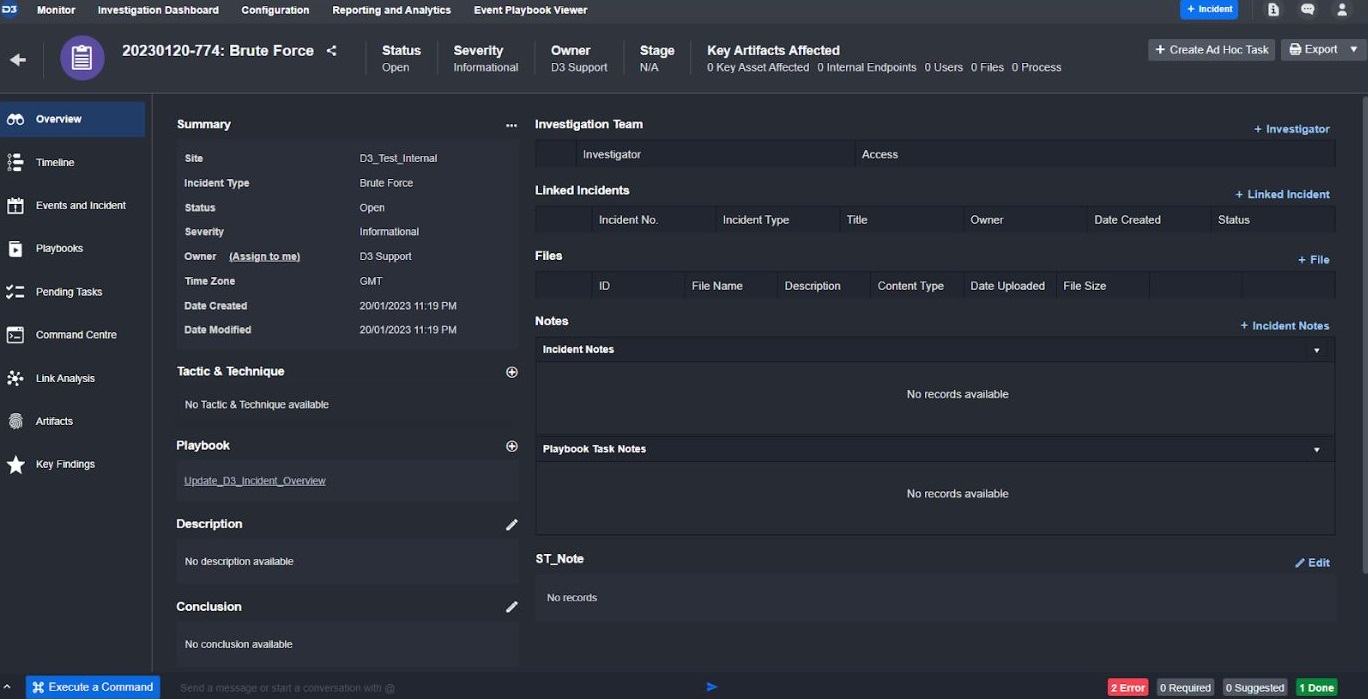
Security Incident Ingested as an Incident
Threat-Specific Playbooks
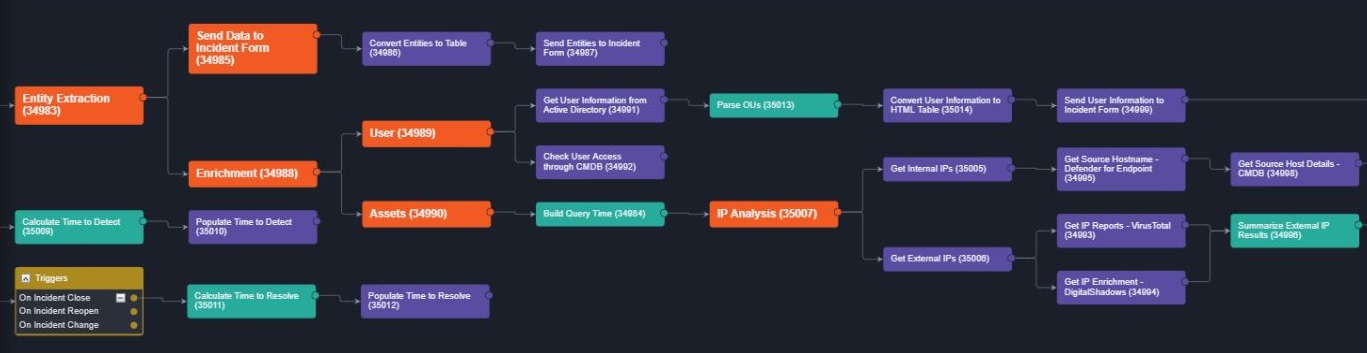
Malware threats, brute force and suspicious logins each require unique investigation and response procedures. In D3 there is no guesswork and no missed steps. The exact actions that need to occur for each threat are executed automatically. The key information is summarized and presented to the investigator to act on, or the incident is auto-closed if it is classified as a false positive.
Playbook for Multiple Failed Authentication Attempts
Responding to an incident requires automation and orchestration of remediation actions. D3 provides simple remediation actions, such as blocking a URL, as well as complex incident response orchestrations that trigger actions across numerous products.
Synchronization Across Your Full Stack
Alerts in Sentinel will always be updated with progress as incidents are investigated inside D3. If, for instance, the severity of an incident changes and you need an explanation, D3 can update the incident status in Sentinel and add a note to give context for anyone auditing or reviewing the incident. And when the incident is resolved, D3 can close the corresponding Security Incident in Sentinel.
Beyond this, D3 acts as the connective tissue between your security stack. We correlate Indicators of Compromise (IOCs), Indicators of Behavior (IOBs), MITRE ATT&CK Tactics, Techniques & Procedures (TTPs), and identity information from the raw Sentinel alerts with information from across your toolset, making malicious activity easier to spot. Whether you use Microsoft or non-Microsoft products, we have you covered. D3 integrates with popular security suites including CrowdStrike, SentinelOne, Cybereason, Splunk, IBM Security, Zscaler, ExtraHop, Palo Alto Networks, Fortinet, and many more.
Realizing Business Outcomes and Benefits
These features will help security teams and their organizations realize important business benefits and outcomes, including:
Faster Time To Value
With D3 Smart SOAR and Microsoft Sentinel, detection and response teams no longer need to manually coordinate across normalization, de-duplication and enrichment tasks. In fact, traditional Tier 1 and Tier 2 security work is automated. It is no longer a burden that requires significant time. Security teams can focus on making decisions and acting on real threats.
Vendor-agnostic Security Processes
Whether or not SIEM is the central source of your alerting, you will need security processes to act on alerts. Proudly vendor agnostic, D3 allows you to implement processes as agile playbooks that are independent of the underlying tech stack, enabling an infrastructure built for rapid, scalable investigation and response, that can be modified (i.e. swapping out a product for another) without interfering with the daily security processes.
Time and Cost Savings
With Smart SOAR’s Event Pipeline automating traditional Tier 1 work (and much of Tier 2 work), your team can instead spend time on higher-impact activities such as upskilling, threat hunting, and utilizing additional automations. With cross-stack correlation, you’ll be able to detect the full scope of an attack earlier, and with incident response orchestration, you will spend close to 90% less time on repetitive tasks. The end result is being able to do much more, without burning out your resources or budgets.
Increase Your Microsoft ROI
With D3 Security and Microsoft Sentinel, you can supercharge your detection and response program. Eliminate time wasted on false positives, stitching together disparate data, and manual correlations and searching. From a budget perspective, you can even use incentives or budget from your Azure Sentinel commitment to purchase Smart SOAR.
We’re part of the Microsoft Intelligent Security Association (MISA), Azure Marketplace, and are a Microsoft Gold partner. This level of expertise extends to our Microsoft Sentinel integration, which in combination with our crucial Event Pipeline, delivers automated triage, identifying credible threats and helping to improve your detection and response program.
To learn more about Smart SOAR’s integration with Microsoft Sentinel, get our solution guide. To see Smart SOAR in a demo tailored for you, sign up here.




