-

How to Reduce the Financial Impact of Security Incidents by 90% or More with Smart SOAR
“By 2024, organizations that adopt a cybersecurity mesh architecture to integrate security tools, so that they work together as an ecosystem, will reduce the financial…
-

Automatically Triage and Respond to Mimikatz Alerts with CrowdStrike, Okta, and Smart SOAR
Credential dumping alerts are a sign that a device has been compromised. Your ability to verify this threat, measure the scope of the breach, and…
-

Why Smart SOAR is the Best SOAR for SentinelOne
D3 Security’s integration with SentinelOne offers an end-to-end solution for incident response teams. The video below shows an example of ingesting threats from SentinelOne, triaging…
-

Why Smart SOAR is the Best SOAR for Microsoft Defender for Endpoint
In the fast-paced world of cybersecurity, security teams must continuously adapt to protect their organization’s digital assets. Streamlining and automating incident response processes is essential…
-

Leverage Your Microsoft Stack to Shut Down Phishing Campaigns in Seconds
Phishing attacks continue to be a major threat to organizations of all sizes, with cybercriminals becoming increasingly sophisticated in their methods. As a result, security…
-
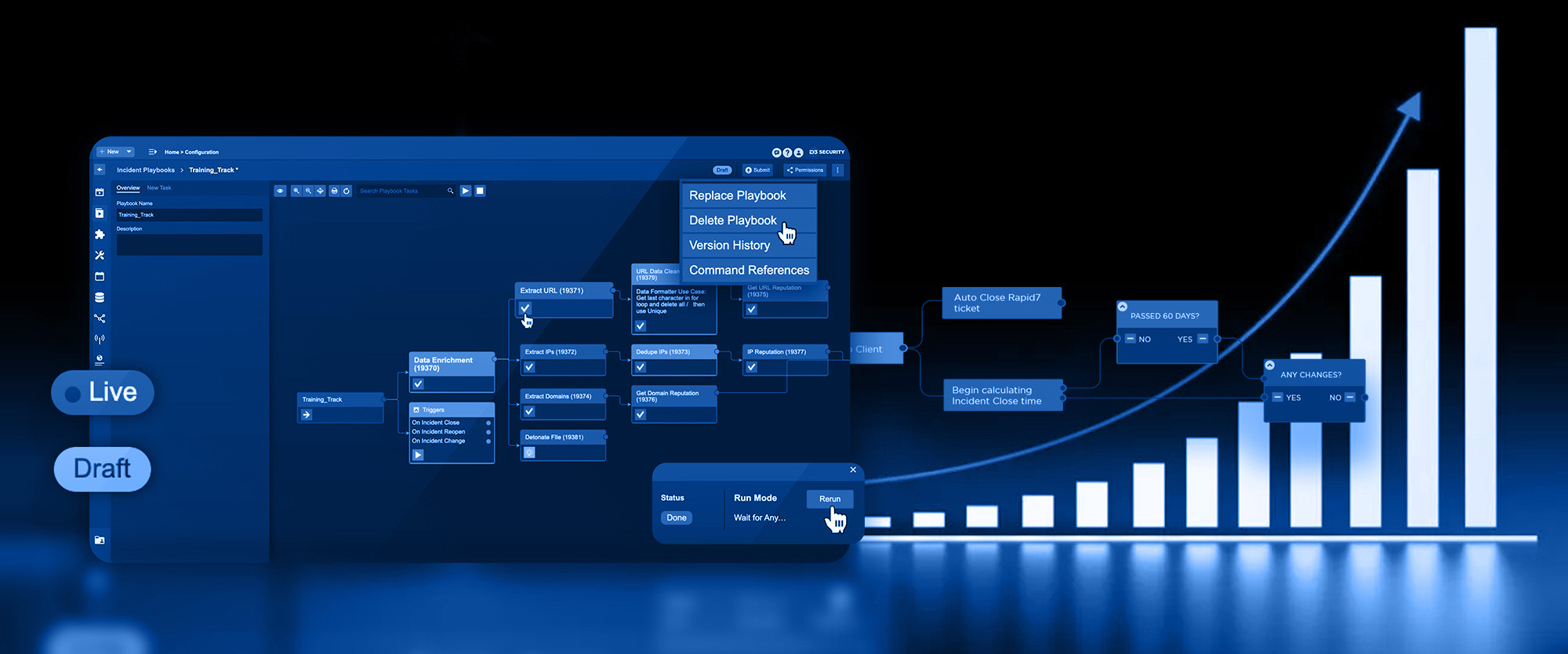
How MSSPs can Serve their First 50 Clients with One SOAR Playbook
What MSSP Customers Say About D3 “D3 is giving a much better possibility for our business to grow, so even though we are rapidly growing,…
-

Respond to Trojan Alerts in Seconds with SentinelOne, VirusTotal, and Microsoft Entra ID
In this post, we’ll be using SentinelOne, VirusTotal, and Microsoft Entra ID to investigate and respond to a potential trojan virus. SentinelOne provides deep enrichment…
-

Playbook Breakdown: Cross-Stack Analysis with CrowdStrike, Zscaler, and Active Directory
In this post, we explore how CrowdStrike, Zscaler, and Active Directory can be used in one playbook to investigate and respond to a remote file…
-

AI-Assisted Kill Chain Investigation with ChatGPT and Smart SOAR
As cyber threats continue to grow in sophistication and frequency, security teams are under immense pressure to detect and respond to incidents quickly and effectively.…
Pierre Noujeim
Select a term…