“By 2024, organizations that adopt a cybersecurity mesh architecture to integrate security tools, so that they work together as an ecosystem, will reduce the financial impact of individual security incidents by 90%, on average.” – Gartner
In 2017, Equifax, one of the largest credit reporting agencies in the United States, suffered a massive data breach that exposed the personal information of nearly 147 million consumers. The breach resulted in estimated financial losses of over $1.4 billion, including legal settlements, regulatory fines, and remediation costs.
One of the critical factors that contributed to the Equifax breach was the lack of integration and coordination between the company’s disparate security tools. The attackers exploited a known vulnerability in the Apache Struts web application framework, which Equifax had failed to patch. Despite having multiple security tools in place, including intrusion detection systems, web application firewalls, and vulnerability scanners, the company was unable to detect or prevent the breach.
The lack of integration and communication between these security tools led to several missed opportunities to identify and remediate the vulnerability. The vulnerability scanner, for instance, did not have an up-to-date version of the Apache Struts component, which led to the vulnerability being overlooked during scans. Additionally, the intrusion detection system failed to flag the suspicious activity due to misconfigurations and a lack of proper monitoring.
If Equifax had implemented a cybersecurity mesh architecture, as recommended by Gartner, the various security tools would have been integrated into a cohesive ecosystem, working together to identify and respond to threats more effectively. This would have increased the likelihood of detecting the vulnerability and the subsequent intrusion, potentially preventing the breach and saving the company from the significant financial and reputational damage it suffered.
A good cybersecurity mesh architecture will mitigate the following risks:
- Missing relevant information because data is spread out between tools.
- Missing patterns because alert structure is not standardized between tools.
- Missing steps in an investigation process because SOPs are not defined.
Mature security teams typically use one-to-two-dozen different security tools. They’ve procured the best and now it’s about making the most out of those investments.
Many cybersecurity vendors are now offering “all-in-one” solutions, taking advantage of their capabilities in network, endpoint, identity and email security. But these all-in-one solutions mean enterprise security and risk leaders have to sacrifice their goal of best-in-class tools in every category. Smart SOAR is built to be an alternative that lets our customers consolidate just as well as an all-in-one solution, but with best-in-class tools.
Any enterprise that is looking to consolidate, but does not want to change the technology they have in place, needs a solution that delivers across five dimensions:
- A consolidated alert queue, including comprehensive case management.
- A normalized data structure to enable cross-tool data analysis.
- Flexible automations that can handle the enterprise’s use cases.
- Integrations that fill the gaps between tools.
- Environment-wide reporting, analytics, and monitoring.
With a tool that can deliver on all five, enterprise teams can transform siloed security tools into a unified ecosystem that work together to mitigate the impact of individual incidents.
SOAR tools are uniquely positioned to help consolidate tools that don’t have natural compatibility, but many vendors sacrifice these capabilities or provide shallow functionality across tools. That’s why 70% of our new customers in 2022 were replacing an existing SOAR tool.
Smart SOAR is the only SOAR tool on the market that delivers deep capabilities across each of these five dimensions. Below, I’ll go into detail about each one and answer some common questions about the relevant functionality.
Capability 1: A Consolidated Alert Queue and Comprehensive Case Management
Single-Pane-of-Glass
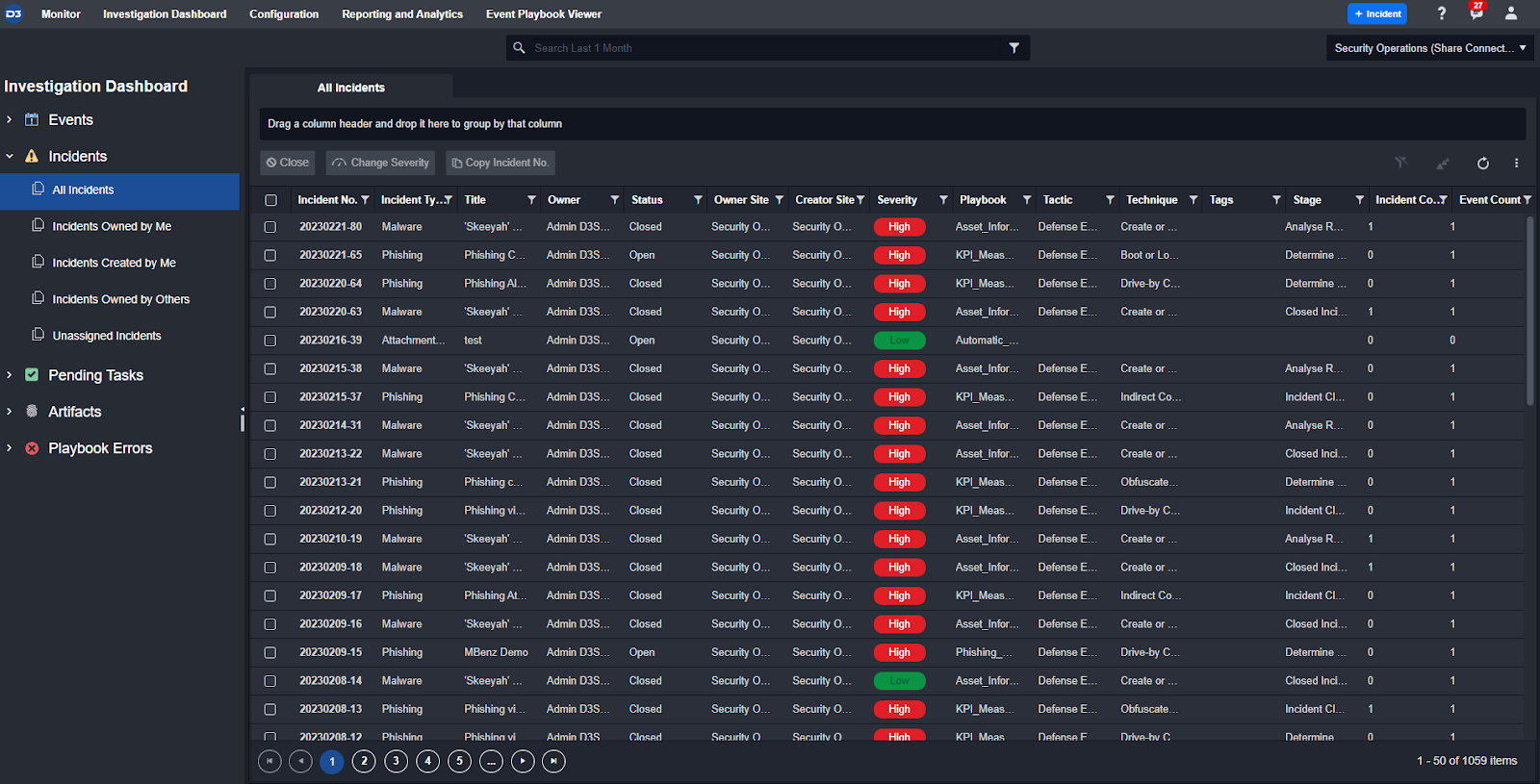
Consolidate alerts from your EDR, SIEM, network, email, and cloud applications in D3’s investigation dashboard:
Smart SOAR’s Investigation Dashboard is a single queue that holds alerts ingested from all tools. Alerts are stored in Smart SOAR as either events or incidents. This allows for two levels of automation: one for triage at the event level and another for remediation at the incident level. I’ll explain this more in the automation section but for now it’s important to know that analysts can spend all of their time reviewing a single queue in Smart SOAR, rather than jumping between tools to make sure they have caught everything.
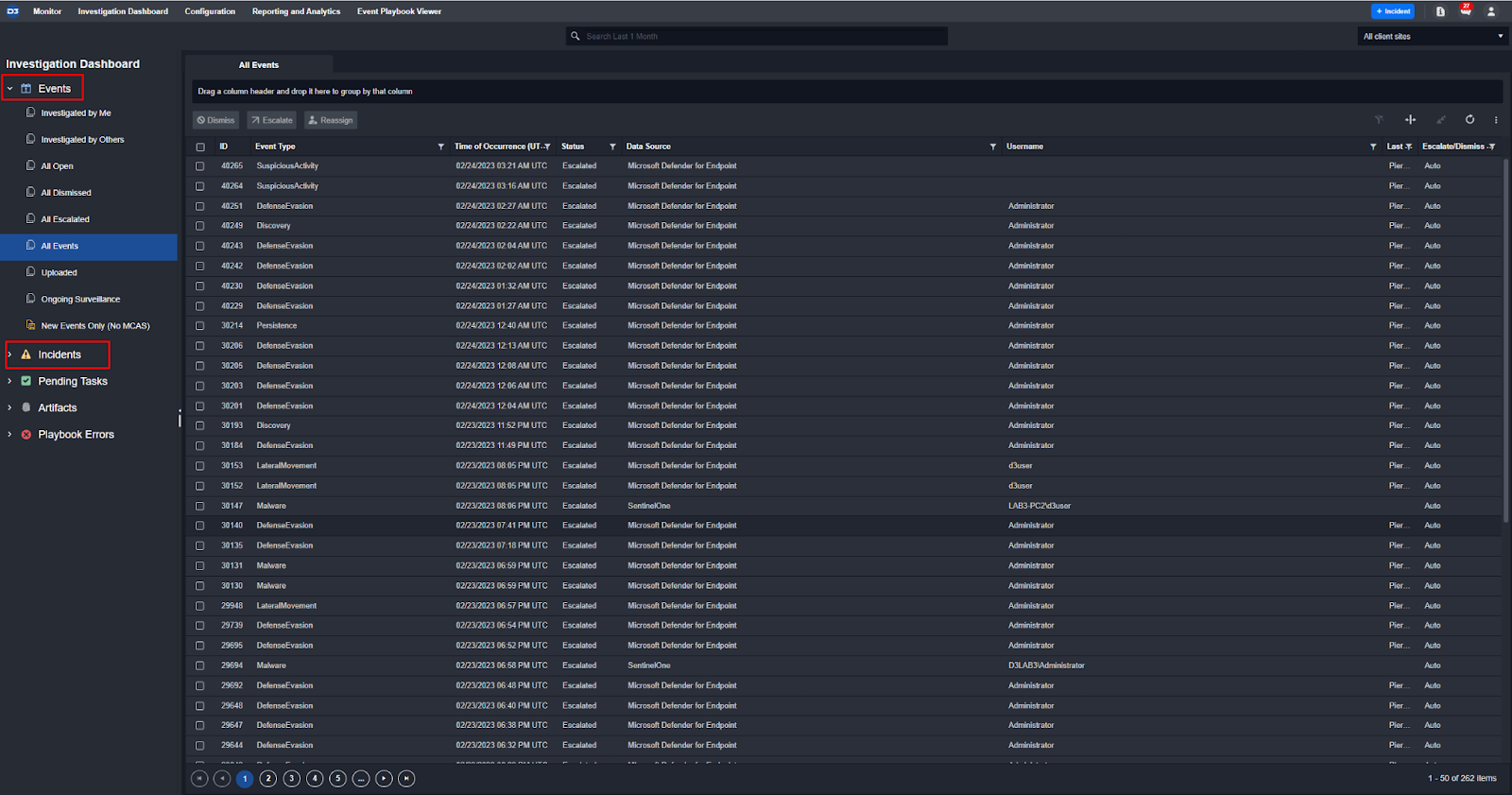
Sidebar: How Data Ingestion Works
Typically, customers fetch alerts from their systems using scheduled API calls. These calls take a set of inputs, such as search condition or filter, and return the results as events. Beyond API calls, Smart SOAR users can also leverage webhooks, emails, and file uploads to ingest and centralize alerts.
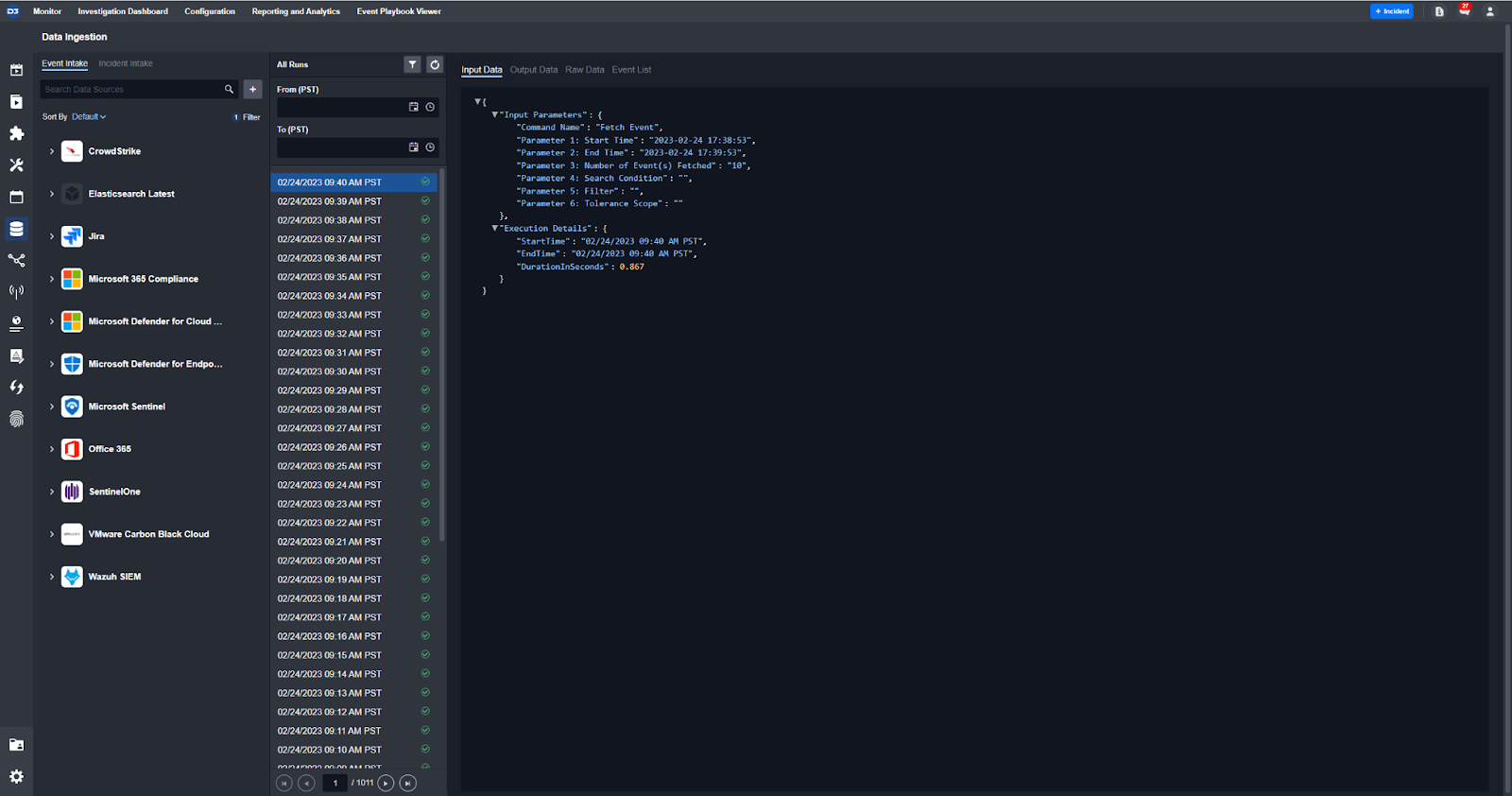
Data ingested here using scheduled GET requests.
Define your interval, search condition, and retroactive lookup period to eliminate data loss.
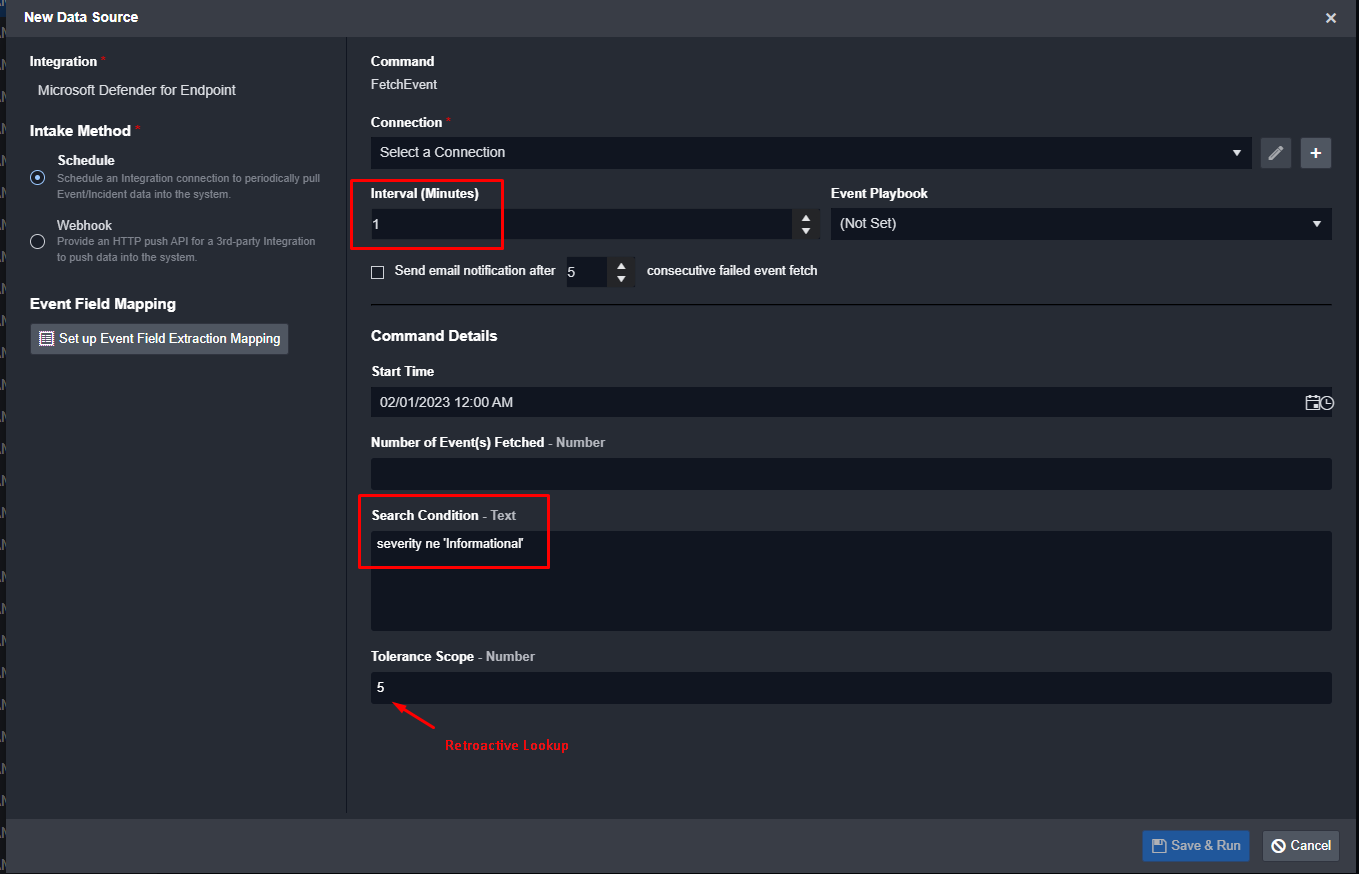
Once the alerts are in the platform, they can be worked on with Smart SOAR’s case management features.
Case Management
Investigating incidents using Smart SOAR gives users the ability to:
- Maintain a tamper-proof incident log recording all actions taken, using D3’s Command Center.
- Store files for reference in the incident overview.
- Assign incidents to individuals or groups.
- Customize severity.
- Customize IR templates.
- Highlight key information for fast review.
- Support multiple analysts collaborating on a single case.
- Automatically export incident reports.
D3’s Incident Overview
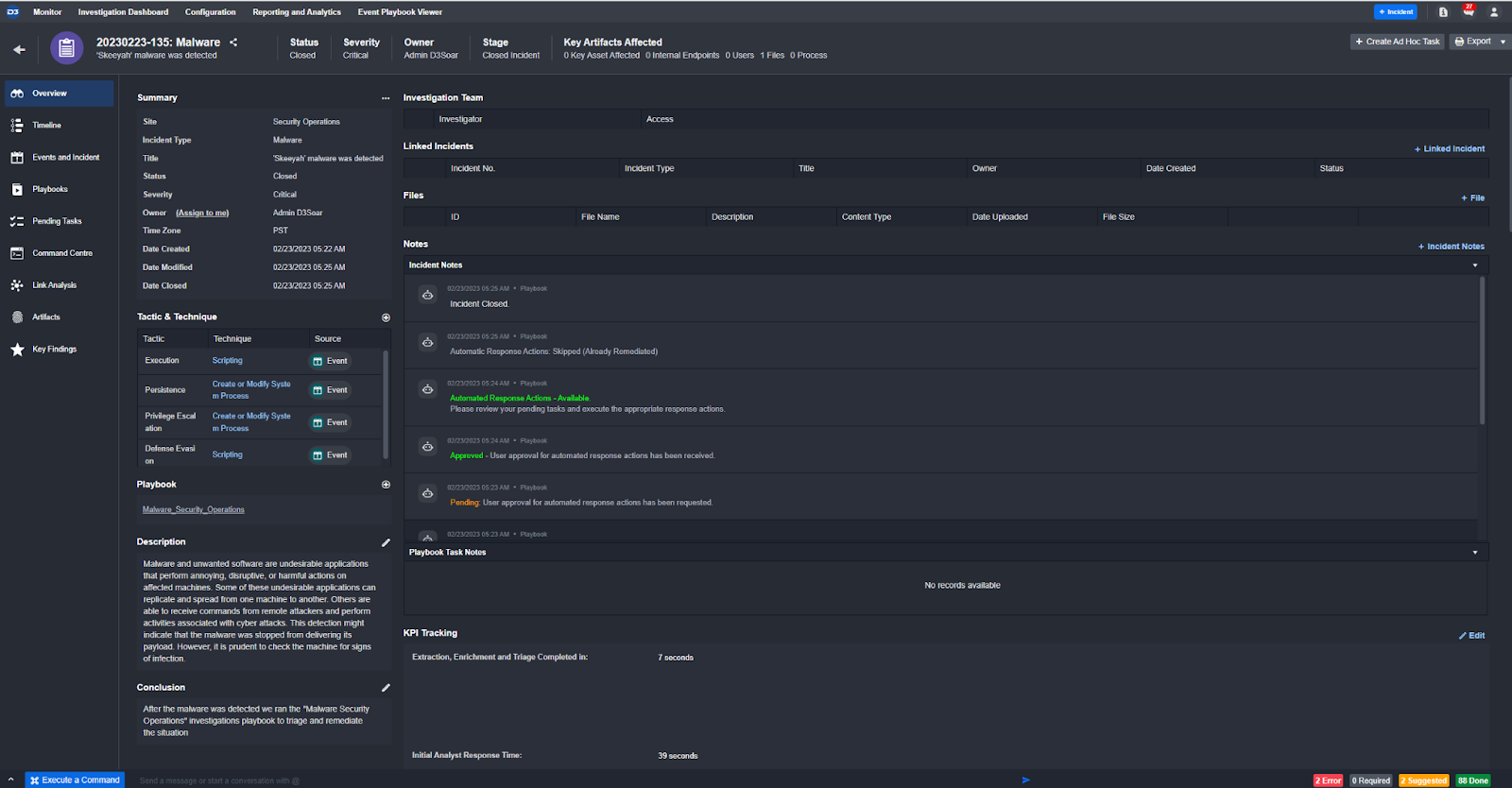
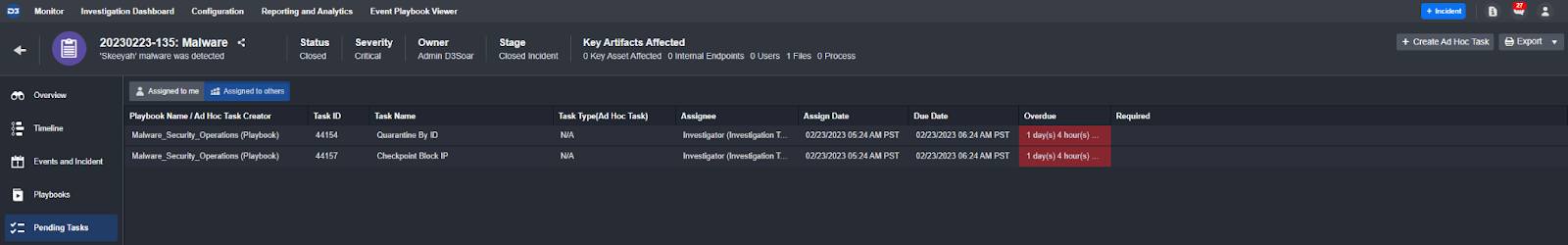
Pending task section so investigators always know what needs to be done next:
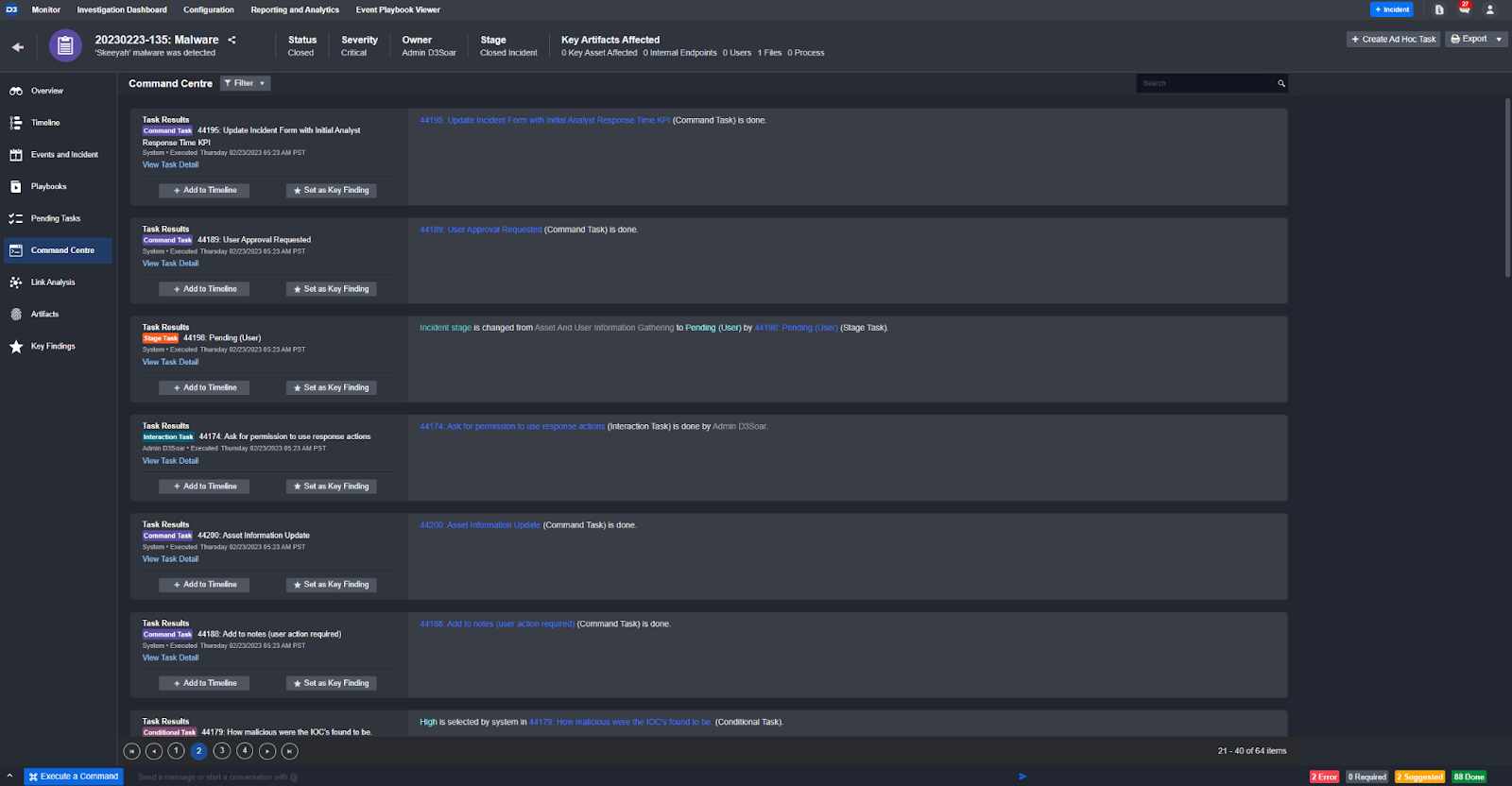
Immutable record of automated and manual actions taken on an incident:
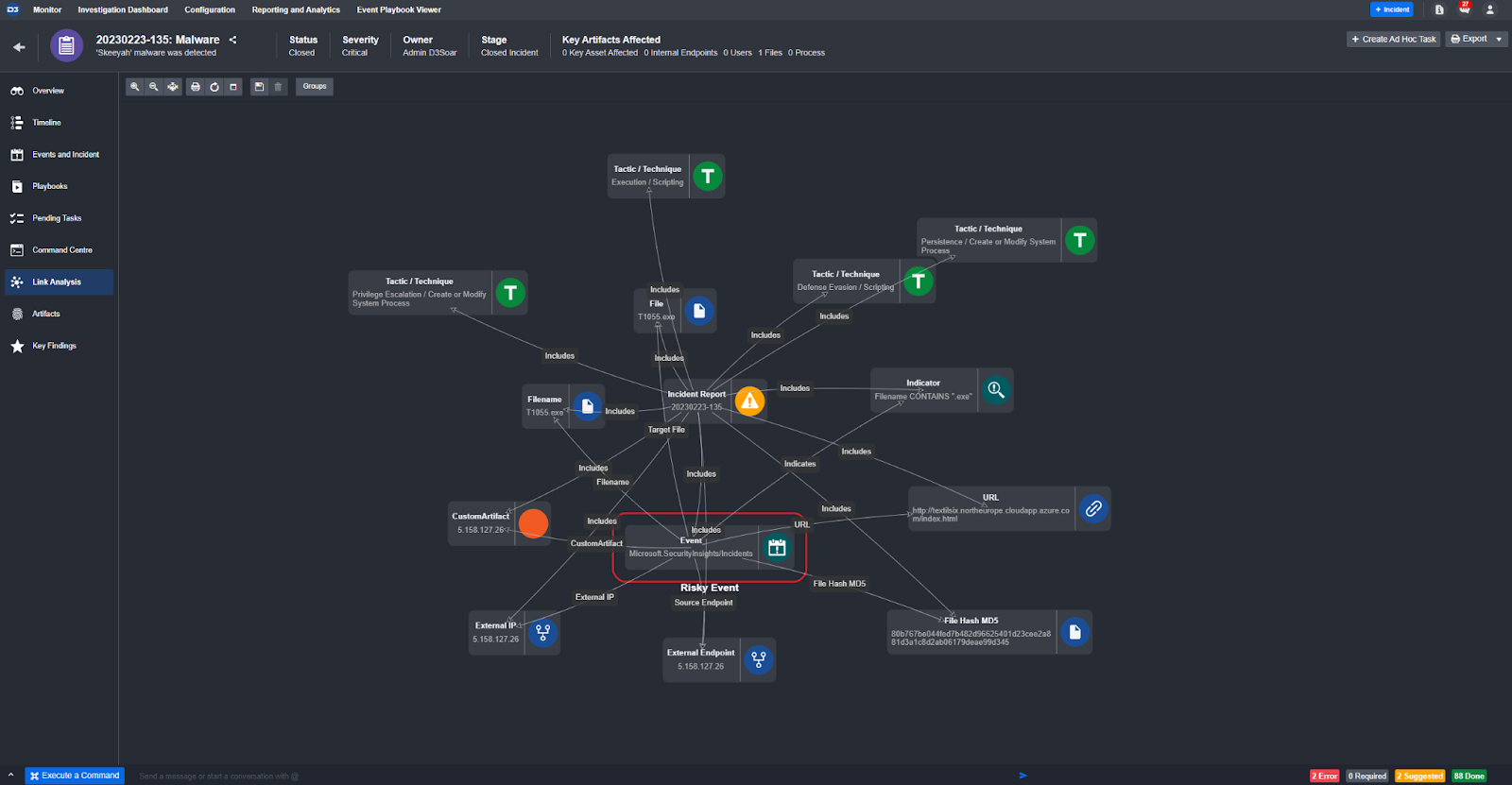
Link analysis:
Run automation ad-hoc:
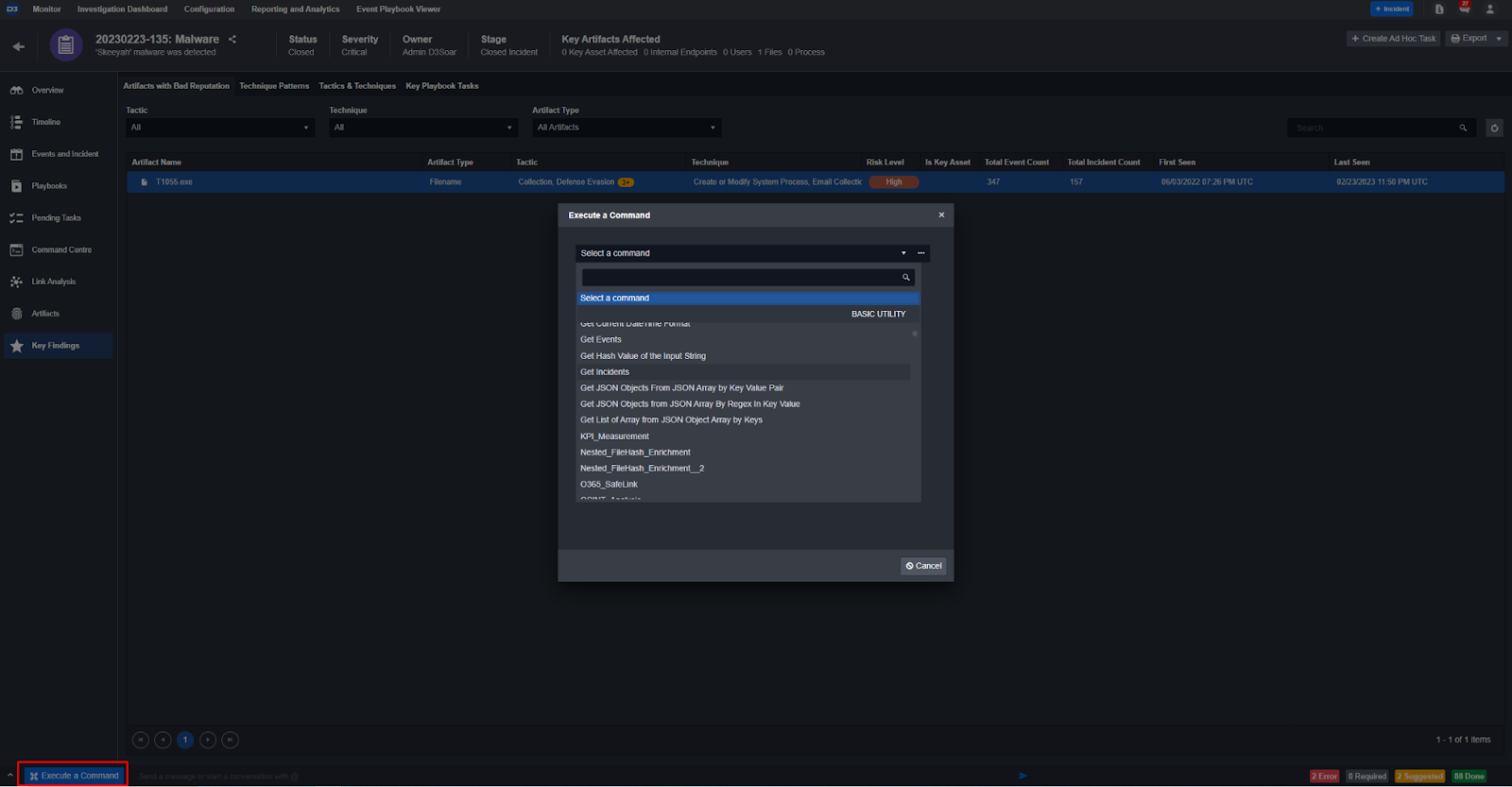
Automatically export custom incident reports:
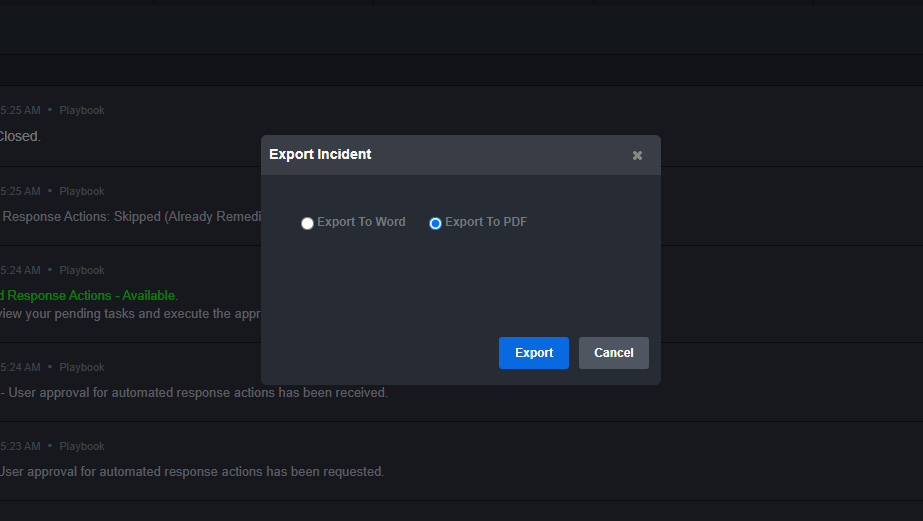
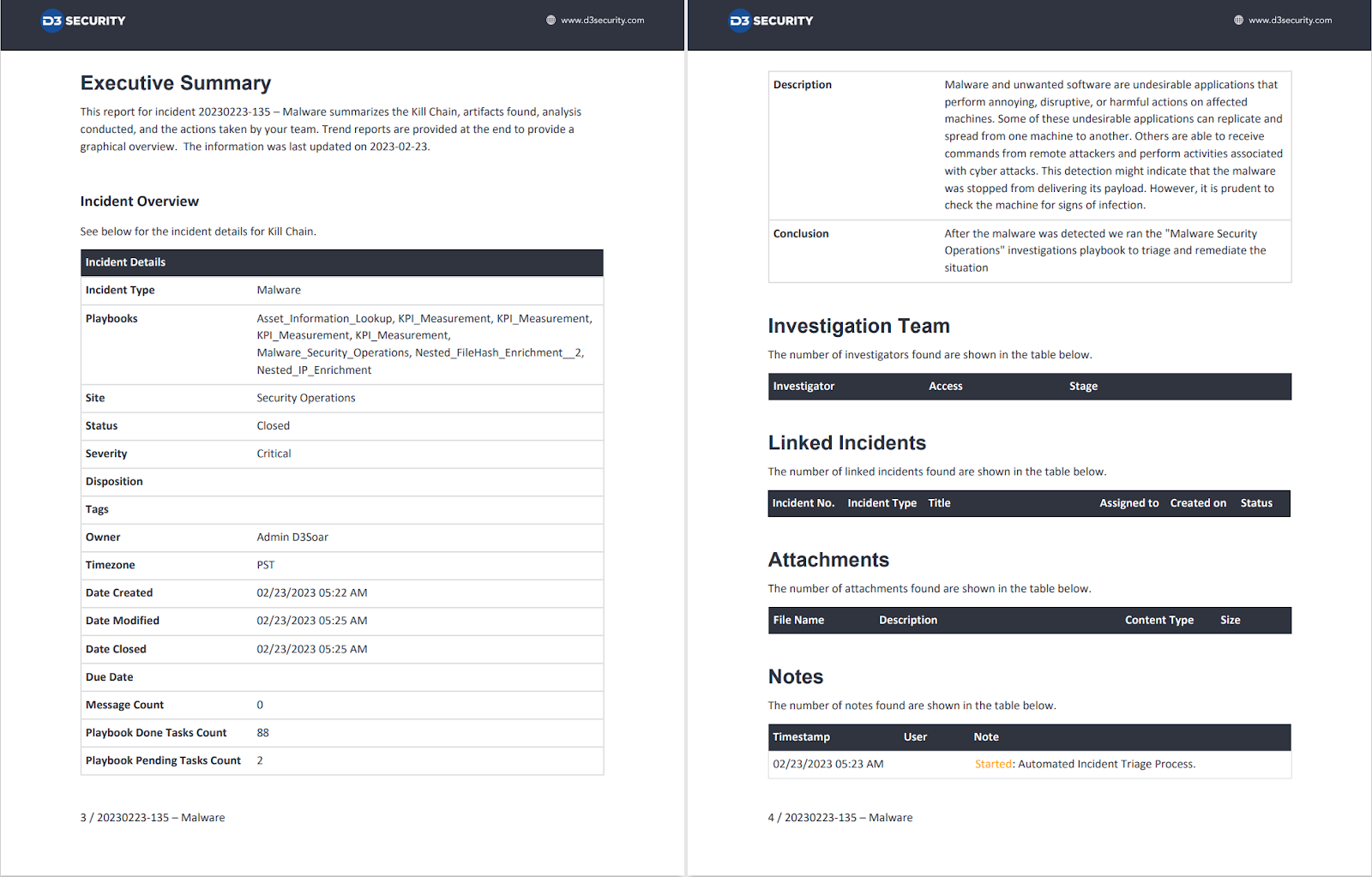
Sidebar: Bi-Directional Sync
With incident triggers, you can keep alerts synchronized between D3 and the original data source.
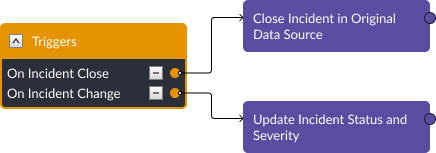
Additionally, all of D3’s commands can be executed remotely. So, if your data source can send POST requests to D3, you can update D3 incidents as incidents are closed, escalated, or changed:
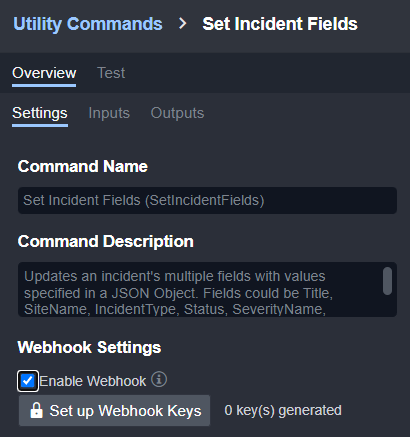
Capability 2: A Normalized Data Structure
Normalization converts the alert data from its original form to a standard model. Storing artifacts in this way lets you analyze them regardless of which data source generated it. This is useful with identity-driven security, where alerts involving the same application, device, or user, can be detected quickly.
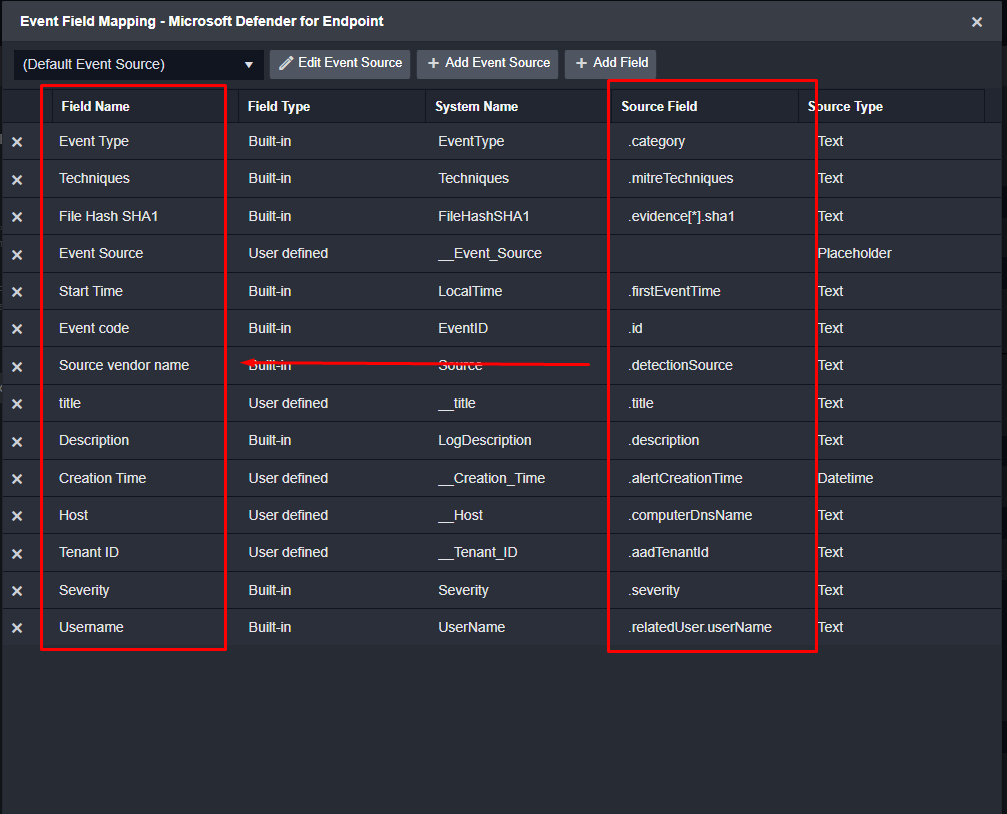
D3 users can create simple and complex field mapping logic, depending on the consistency of the data source. For example, if alerts will always be in the same structure, then static field mapping will do:
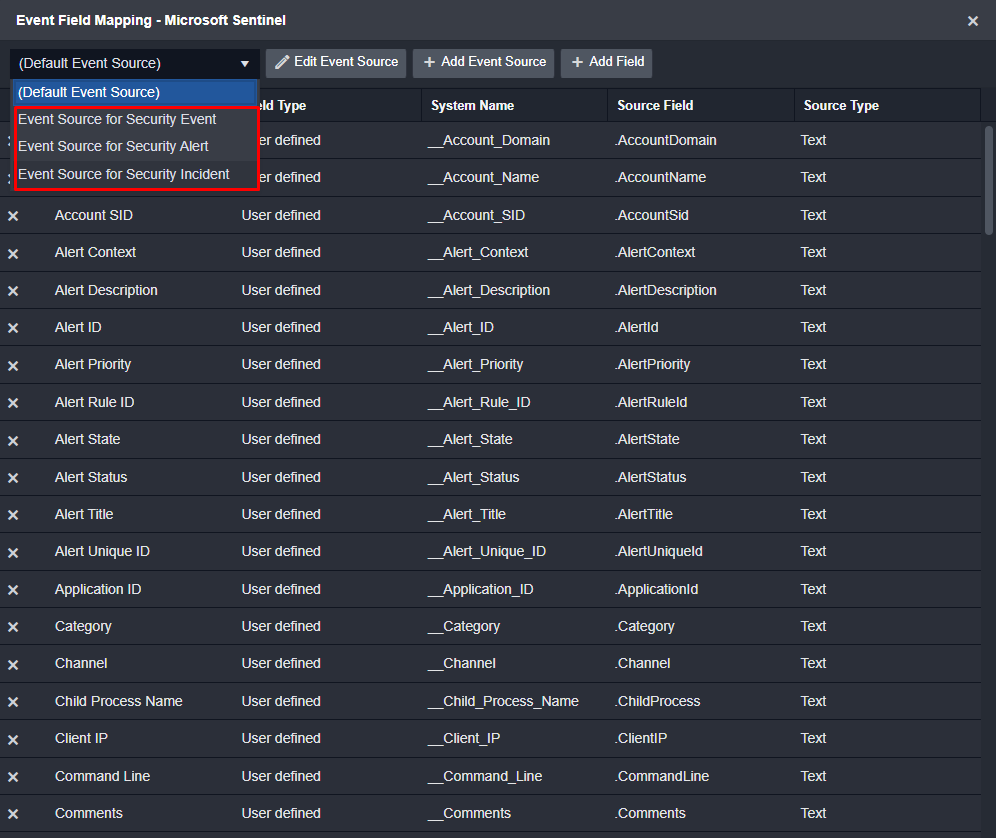
However, if the alert structure depends on the table that’s being queried, you can create multiple field-mapping settings and have them applied dynamically on ingestion. D3 will detect which table you’re ingesting from and apply the appropriate mapping. For example, Microsoft Sentinel has three basic tables: Security Events, Security Alerts, and Security Incidents. Each are given their own mapping and can be dynamically applied on ingestion:
Here you can see the alert data on the right and D3’s system field on the left:
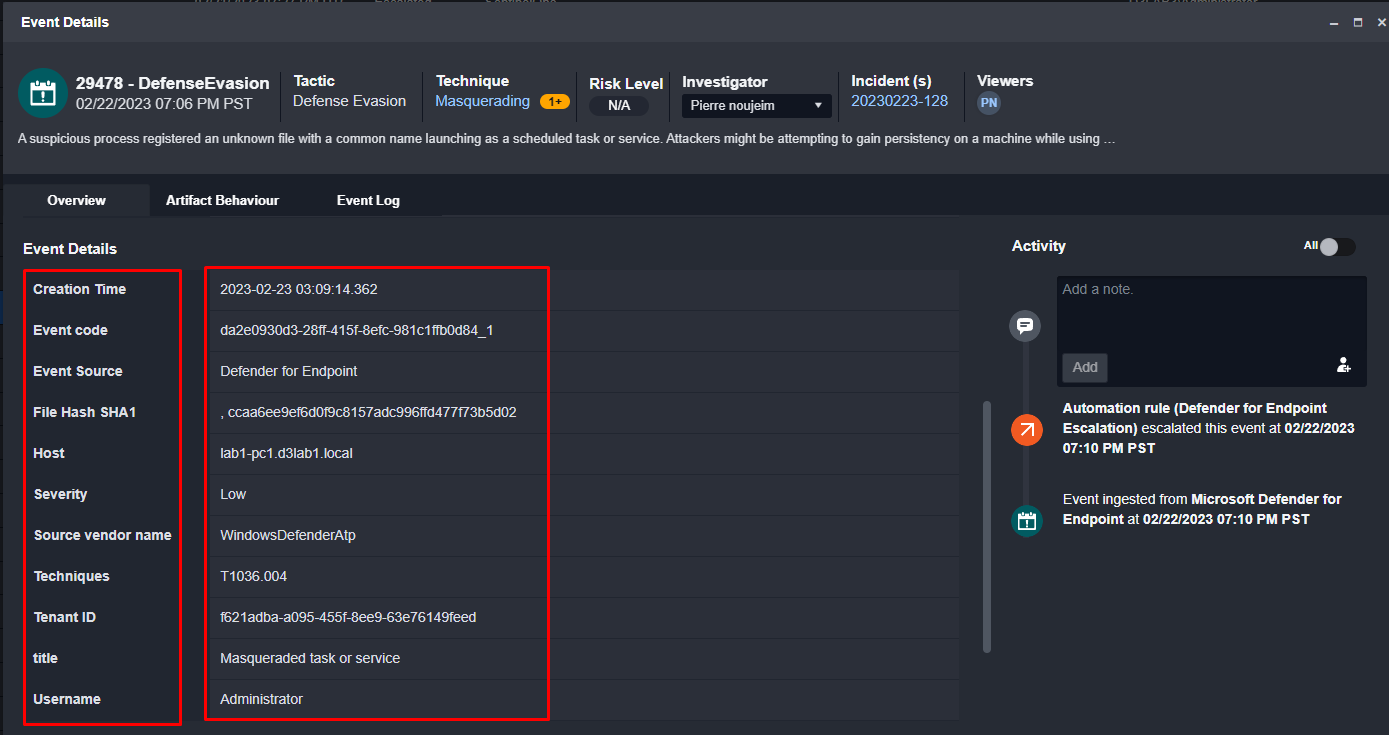
These values are then logged as artifacts in D3’s system:
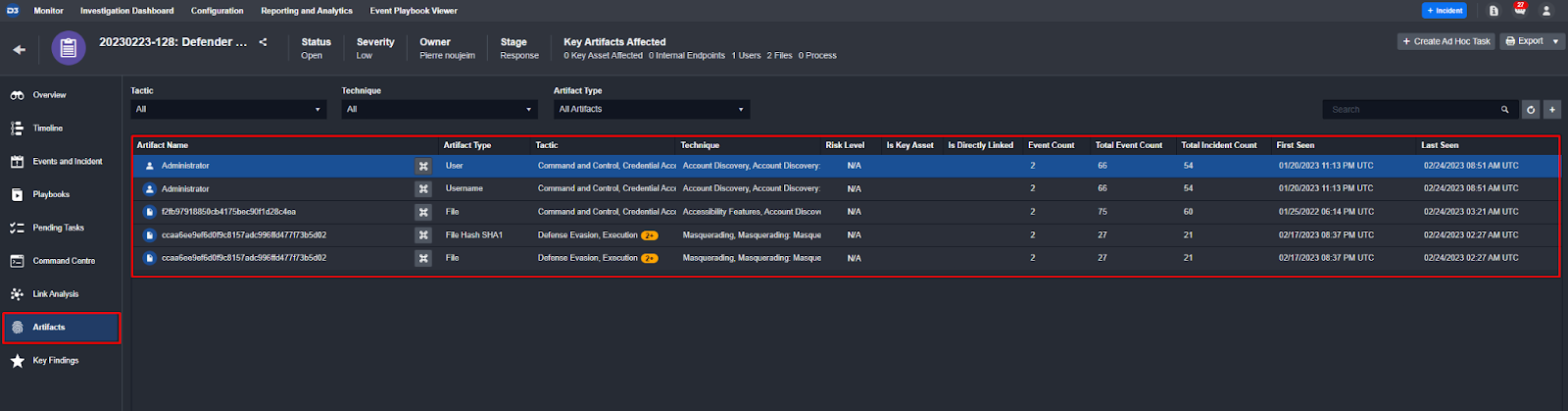
Capability 3: Automation that can Handle Standard and Advanced Use Cases
In D3, automated workflows can be triggered on:
- Event ingestion,
- Incident creation & change,
- Custom schedules, and
- An ad-hoc basis.
This is different from other SOAR tools which only allow you to run a playbook on incident creation.
This gives user the option to use playbooks to:
- Automate correlation, classification and triage of incoming alerts.
- Bring all relevant information on an attack together in the incident overview.
- Respond to incidents in a manual, hybrid, or fully automated way.
- Be re-used as nested components in other playbooks.
- Run on a schedule independent of incoming alerts (this opens the door for advanced use-cases such as threat hunting or vulnerability scanning).
- Be executed ad-hoc, mid investigation to bring in more information or take actions on devices and tools.
Automation at the Event Level
Almost every alert coming into D3 is first handled as an event. Event playbooks are used to:
- Find existing incidents that are related for correlation.
- Adjust priority based on data from other tools not included in the detection.
- Identify and dismiss false positives.
- Automate ‘house-keeping’ tasks such as ticket creation and updating databases.
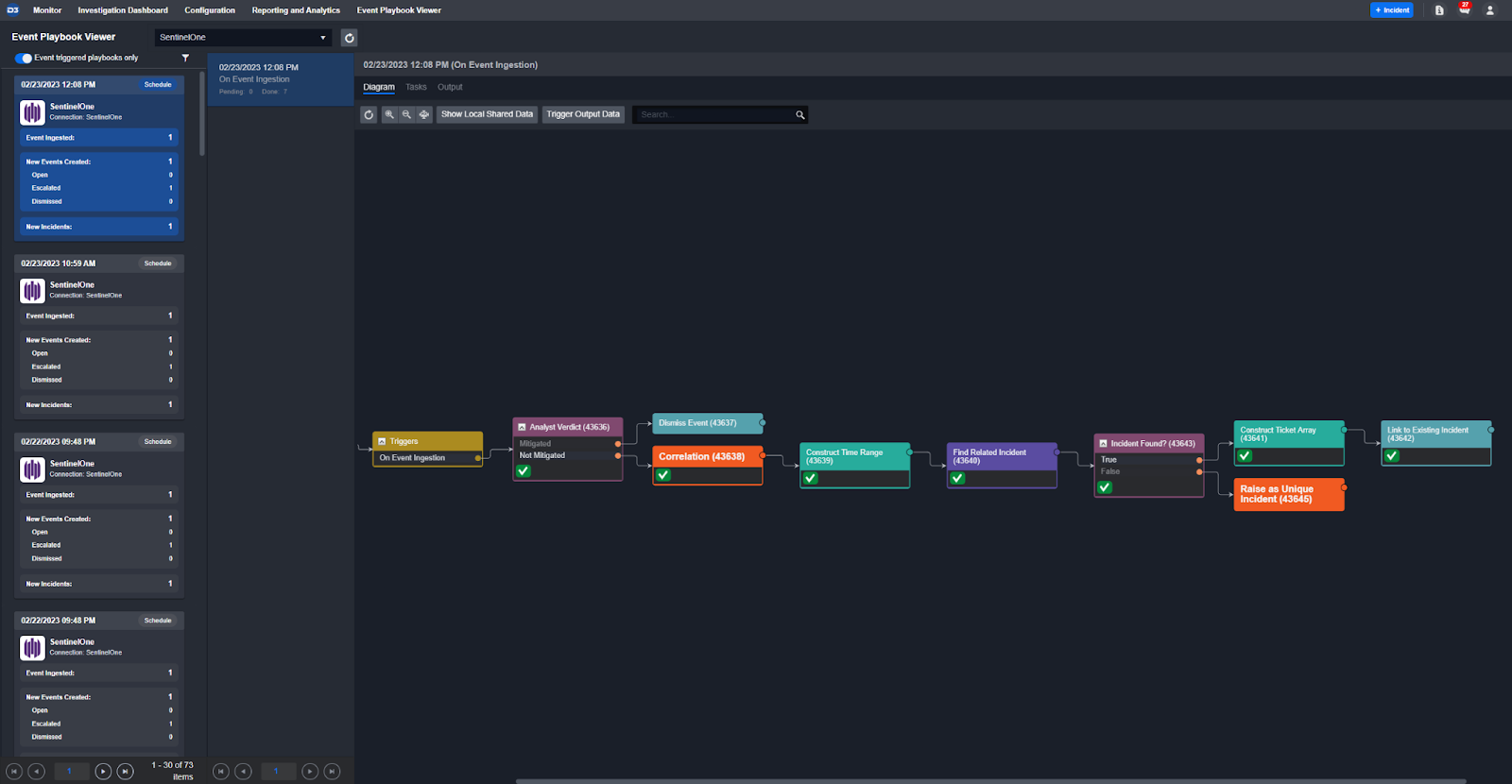
Automation at the Incident Level
Playbooks can also be triggered on incident creation. This happens after the event has been ingested and run through an event playbook. At this stage, the playbooks are mainly built for data enrichment and remediation.
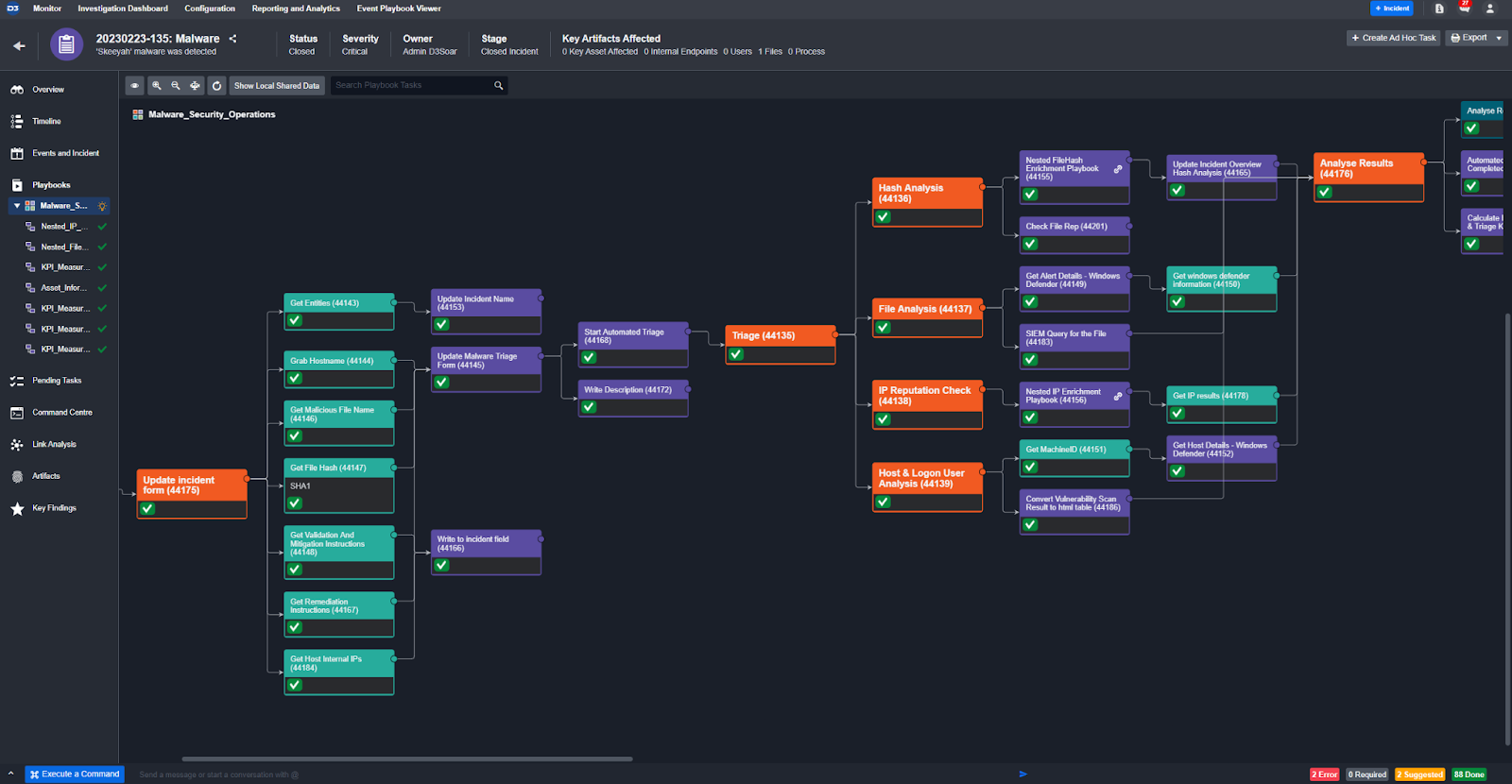
Automation on a Schedule
Not all automations require an incoming event or incident. You can build workflows and set a cadence for them to run. These workflows could be used for a use case such as collecting SBOMs from your third-party vendors, analyzing them, and emailing out new vulnerabilities.
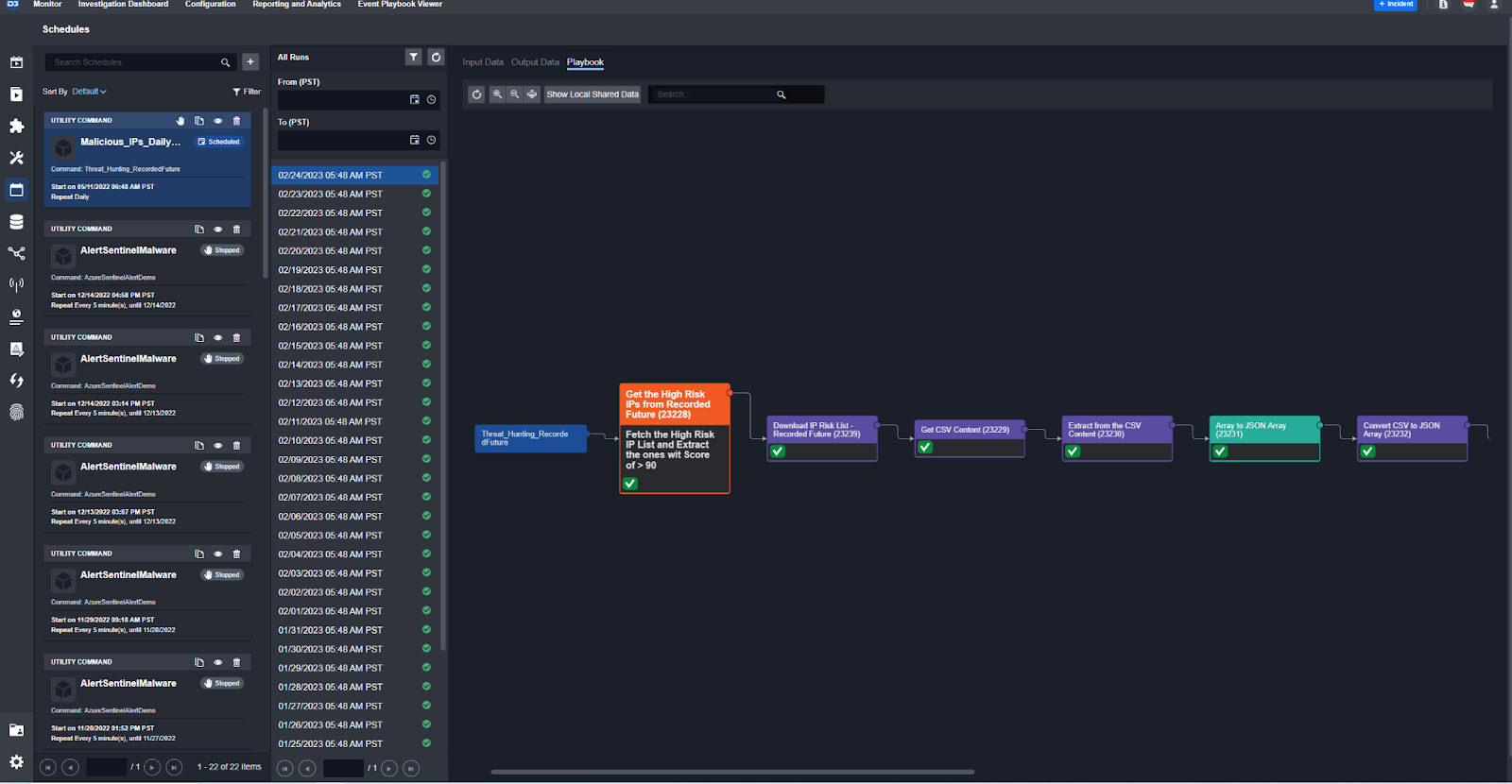
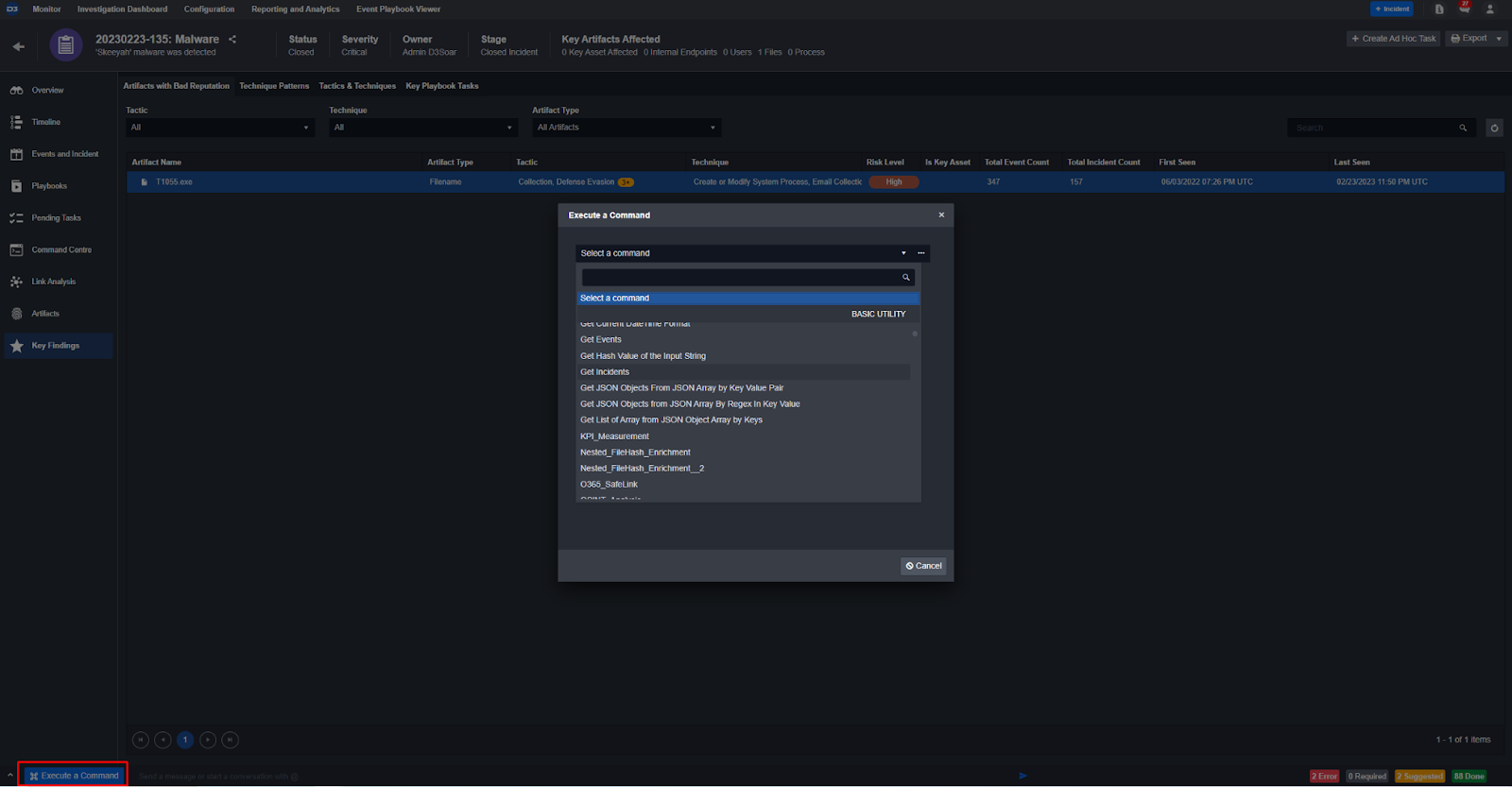
Ad-Hoc Automation
At any time during an incident investigation, users can run commands and full workflows ad-hoc. These include integration commands and modular playbooks:
Capability 4: Integrations that Fill the Gaps Between Best-in-Class Tools
The integrations within the platform are researched, designed, and built by our engineers. New integrations and updates are included free-of-charge because we know how complicated it is to manage integrations yourself. Our clients can take back hundreds of hours that they would have spent reading through API docs and writing code.
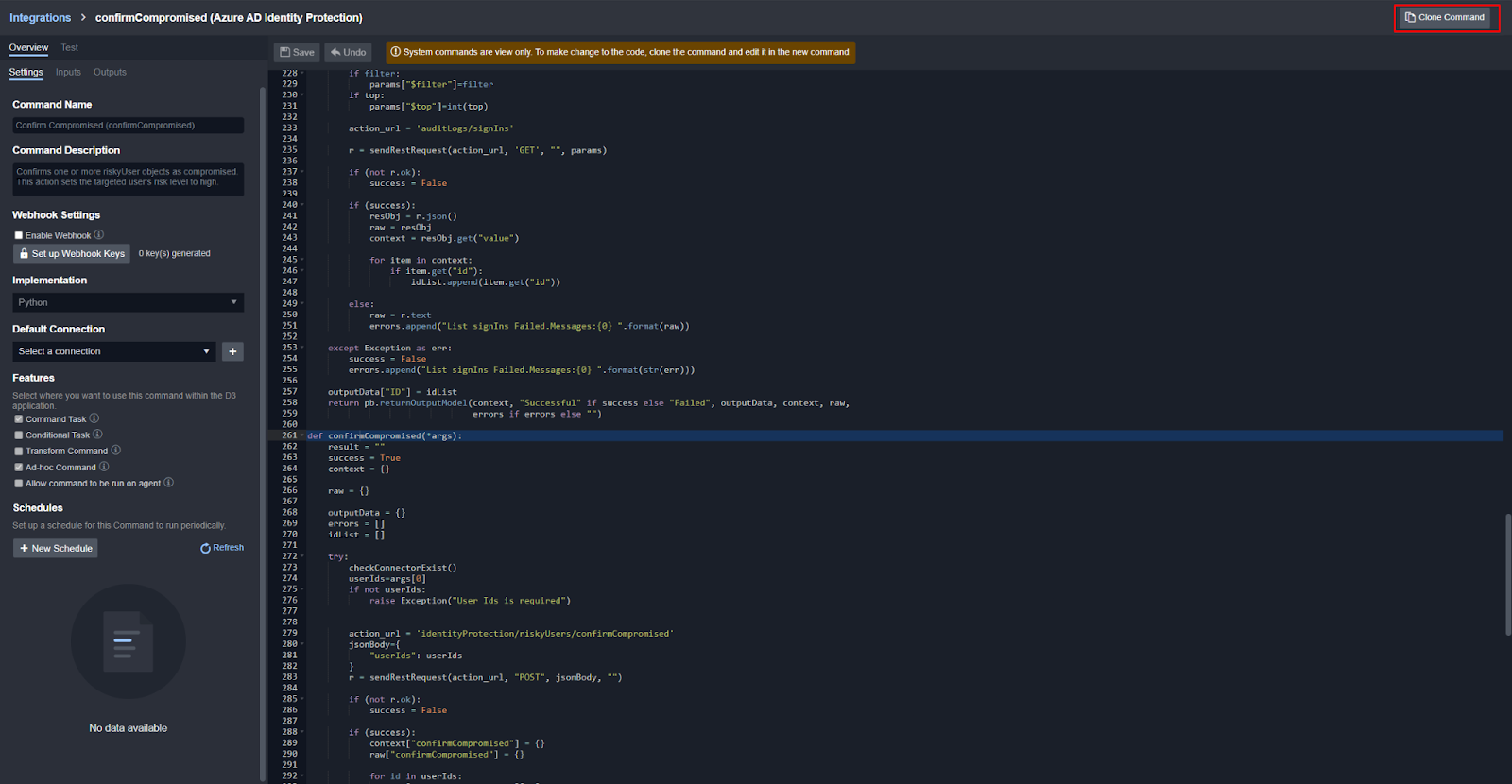
Integrations are available out-of-the-box and users can customize them using REST APIs and the built-in code editor. Multiple connections can be added and shared to specific tenants within D3. Windows and Linux-based proxy agents are available for on-premise integrations as well.
The system code is available for users to review. They also have the option to clone and customize this code if a different function is needed:
Capability 5: Environment-Wide Reporting
Most security analytics tools used are domain-specific, and organizations typically use multiple security analytics tools alongside each other in a nonintegrated manner. A broader security analytics and monitoring tool could use risk scores and IOBs from siloed tools and apply it in a different context.
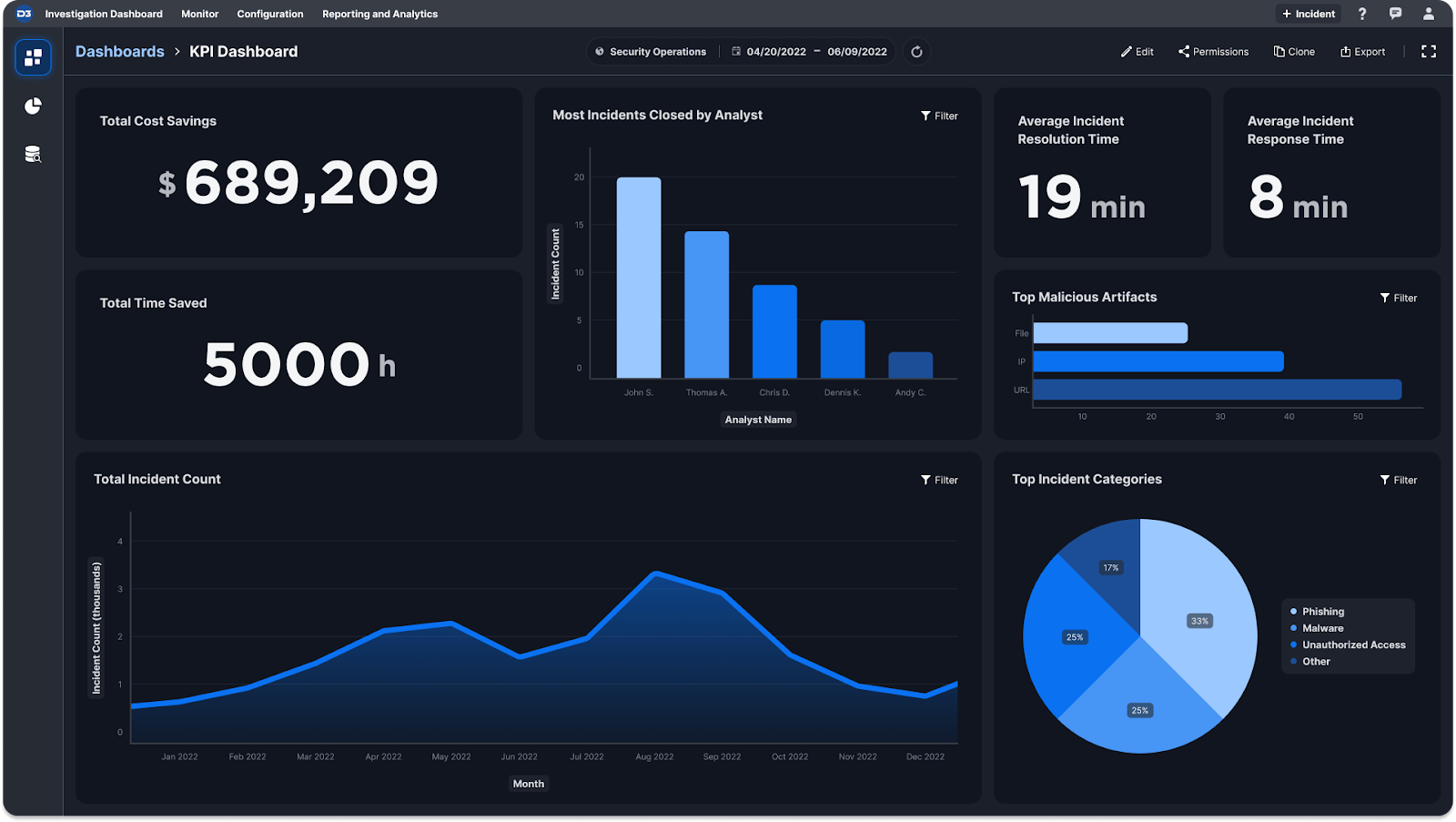
D3 Smart SOAR’s system data from events, incidents, artifacts, and playbooks, as well as external data from third-party integrations, can be used to build metrics, dashboards and reports. External data can be imported into D3 Smart SOAR manually as CSV files or automatically via API calls. The built-in query builder can query and transform system or external data to create charts that visualize queried data and find meaningful insights about a client’s security posture. These charts will serve as building blocks for creating dashboards. Specialized dashboard views can be organized and constructed, including ROI dashboards, admin management dashboards, and system health dashboards with the associated custom/built-in charts.
Users benefit from:
- Reduced time updating dashboards because of automated data importing from third-party tools via API calls.
- Minimized risk of catastrophic incidents by taking preemptive actions as indicated by system health dashboards.
- Enhanced SOC operational performance and increased profits by making data-driven decisions from measuring and monitoring ROI and KPI metrics.
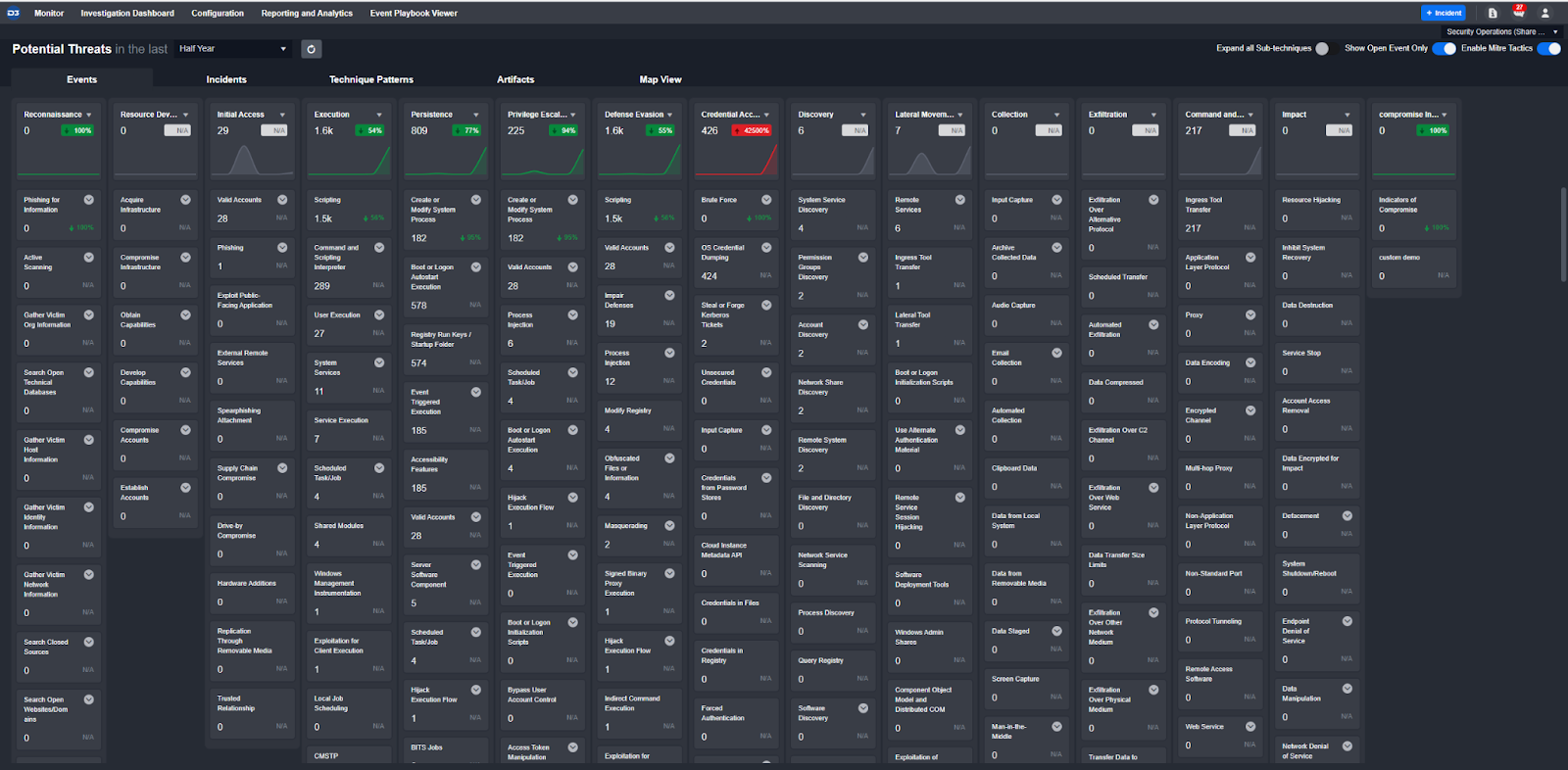
MITRE TTP Monitoring
D3 also tracks MITRE TTPs across sites and consolidates them for a high-level review of your threat landscape. The detection logic is built-in and can be customized based on your environment:
Takeaway
Teams with siloed, best-in-class, security tools stand to eliminate the risk that comes with blind spots and complex operations by integrating them together into a cybersecurity mesh architecture. However, integrating these tools is not an easy feat. Most SOAR vendors offer one of the five dimensions needed to create a cybersecurity mesh architecture, or they offer shallow functionality across a handful of them. Smart SOAR is the only SOAR tool on the market that delivers robust capabilities across all five dimensions:
- A consolidated alert queue, including comprehensive case management.
- A normalized data structure to enable cross-tool data analysis.
- Flexible automations that can handle the enterprise’s use cases.
- Integrations that fill the gaps between tools.
- Environment-wide reporting, analytics, and monitoring.
This means that our customers don’t have to choose between best-in-class and consolidation. They’ve turned dozens of siloed security tools into a unified ecosystem that work together to reduce the financial impact of individual security incidents.