In the fast-paced world of cybersecurity, security teams must continuously adapt to protect their organization’s digital assets. Streamlining and automating incident response processes is essential for effective defense against threats. One way to achieve this is by integrating powerful cybersecurity tools like Microsoft Defender for Endpoint with a robust security orchestration, automation, and response (SOAR) platform, such as D3 Smart SOAR. In this playbook breakdown, we’ll explore the benefits of D3 Security’s Microsoft Defender for Endpoint integration and discuss how Smart SOAR playbooks can help security teams efficiently investigate and respond to endpoint detection and response (EDR) alerts.
Optimizing Incident Response with the Integration of Microsoft Defender for Endpoint and D3 Smart SOAR
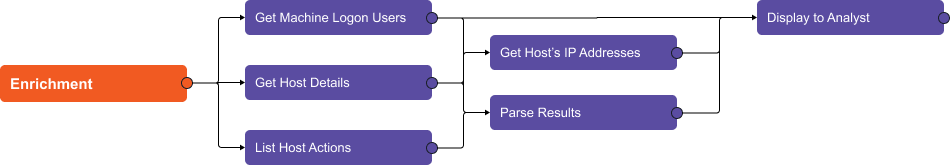
The playbook we’re reviewing has three main stages: Enrichment, Correlation, and Response.

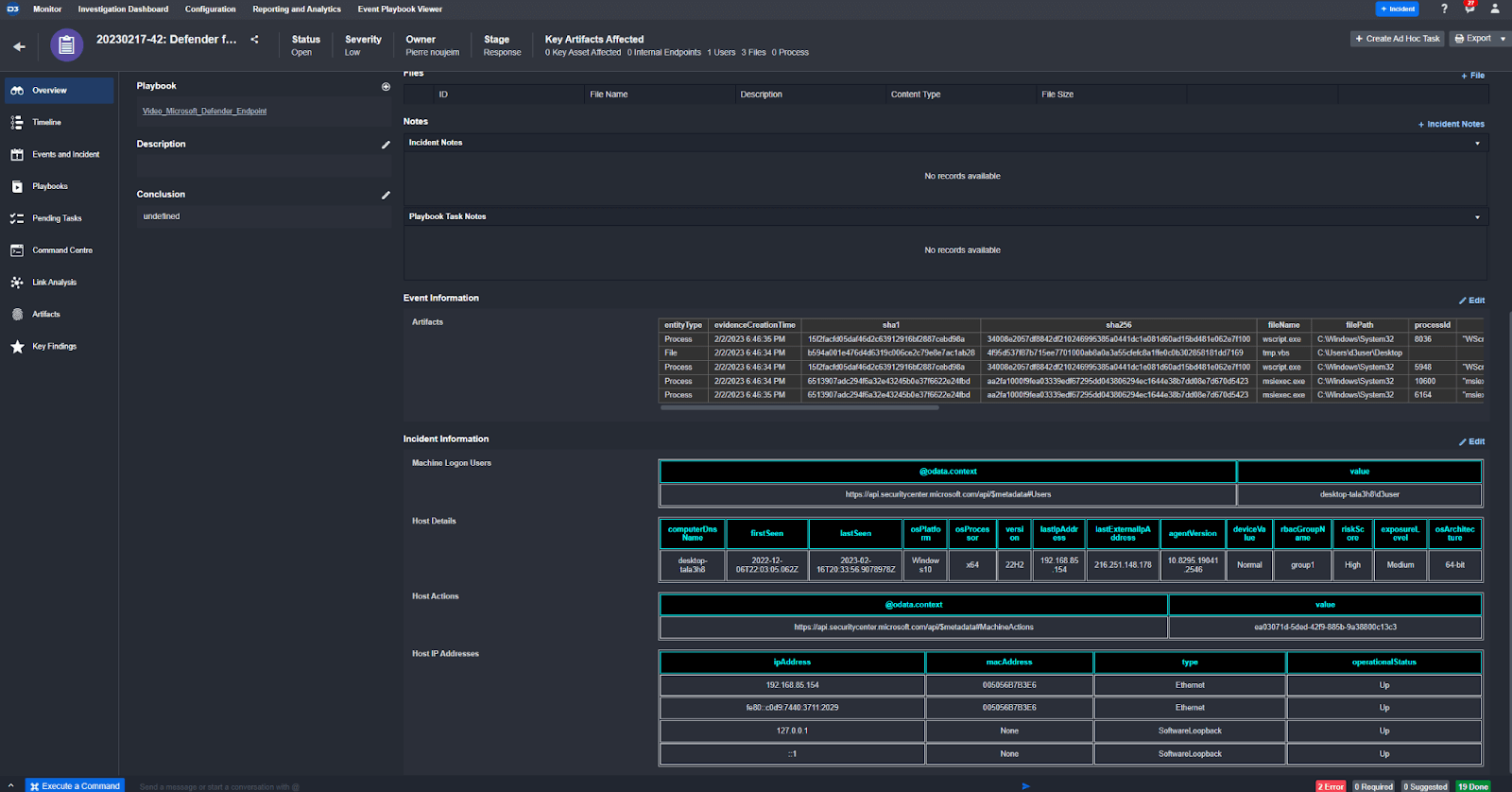
Within the enrichment section of the playbook, Microsoft Defender for Endpoint’s API calls are used to gather information on the affected host, including active users, operating system, IP addresses, and actions. The results are then parsed and displayed to the analyst for review.
Here, you can see the enriched information formatted into tables in the incident overview.
In the correlation section, the playbook searches both Defender for Endpoint and Smart SOAR for alerts that contain the same file hash. If found, they are attached to the existing incident for further analysis. Additionally, the playbook searches for other devices that have been affected by the same file hash, and initiates a scan on those devices.

Once all relevant information has been collected, the playbook presents the analyst with the option to determine if a malicious artifact has been found. If yes, the artifact is flagged as an indicator in Defender for Endpoint and an email is sent to the device owner’s manager to approve the isolation of the affected device.

By automating these tasks, security teams can quickly review the information and make a decision about how to proceed, helping to reduce response time and mitigate risks. With D3’s other playbooks, you can automate actions across all the tools in your security stack, providing a complete picture of the event.
Enhance Case Management and Data Enrichment with D3 Security’s Smart SOAR Platform
D3 Security’s Smart SOAR platform comes with over 20 integration commands for Microsoft Defender for Endpoint that cover case management, data enrichment, and response activities. In the case management section, you can ingest alerts into D3 and update alerts in Defender for Endpoint using API calls from the application. You can also gather host and artifact information, such as active users and related file events. Finally, you can quarantine devices and artifacts, initiate scans, and put them back on the network.
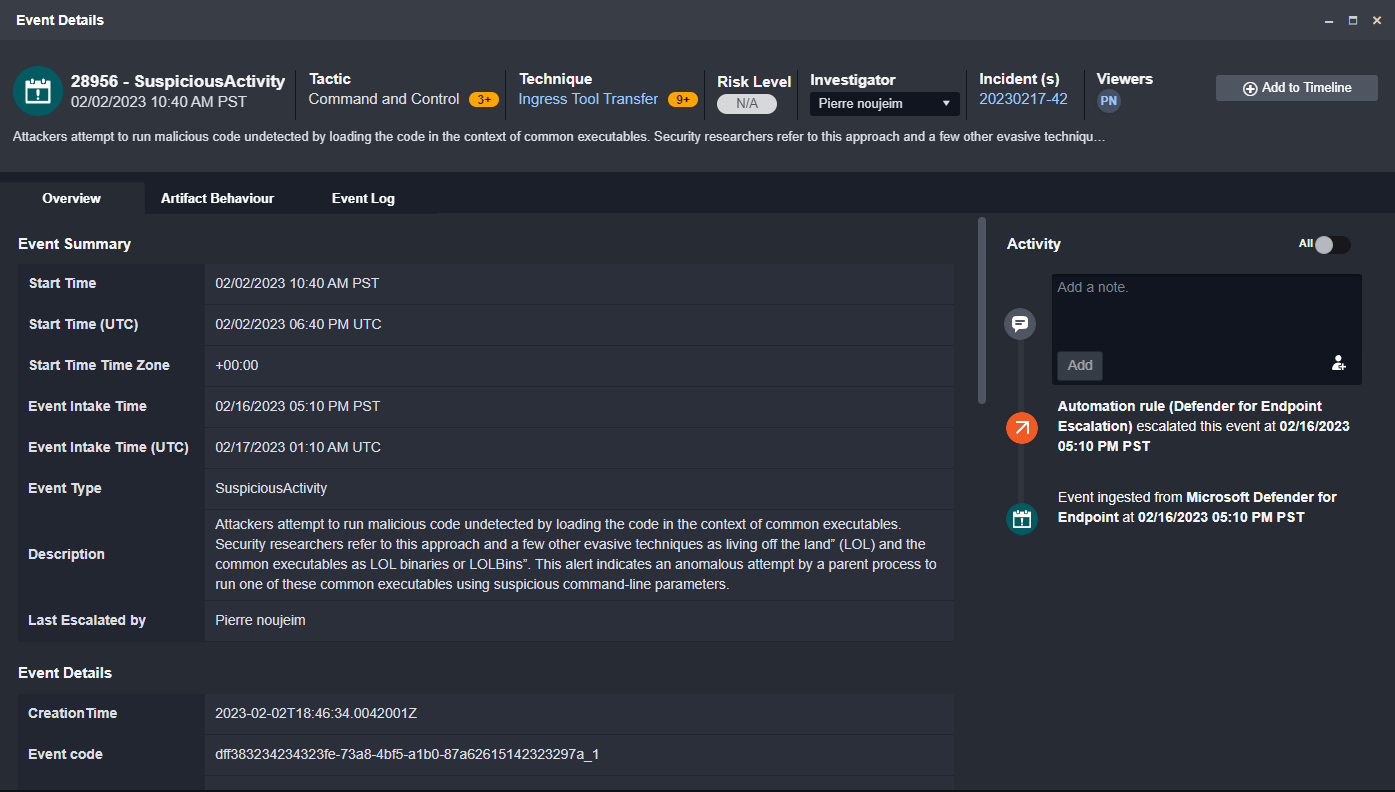
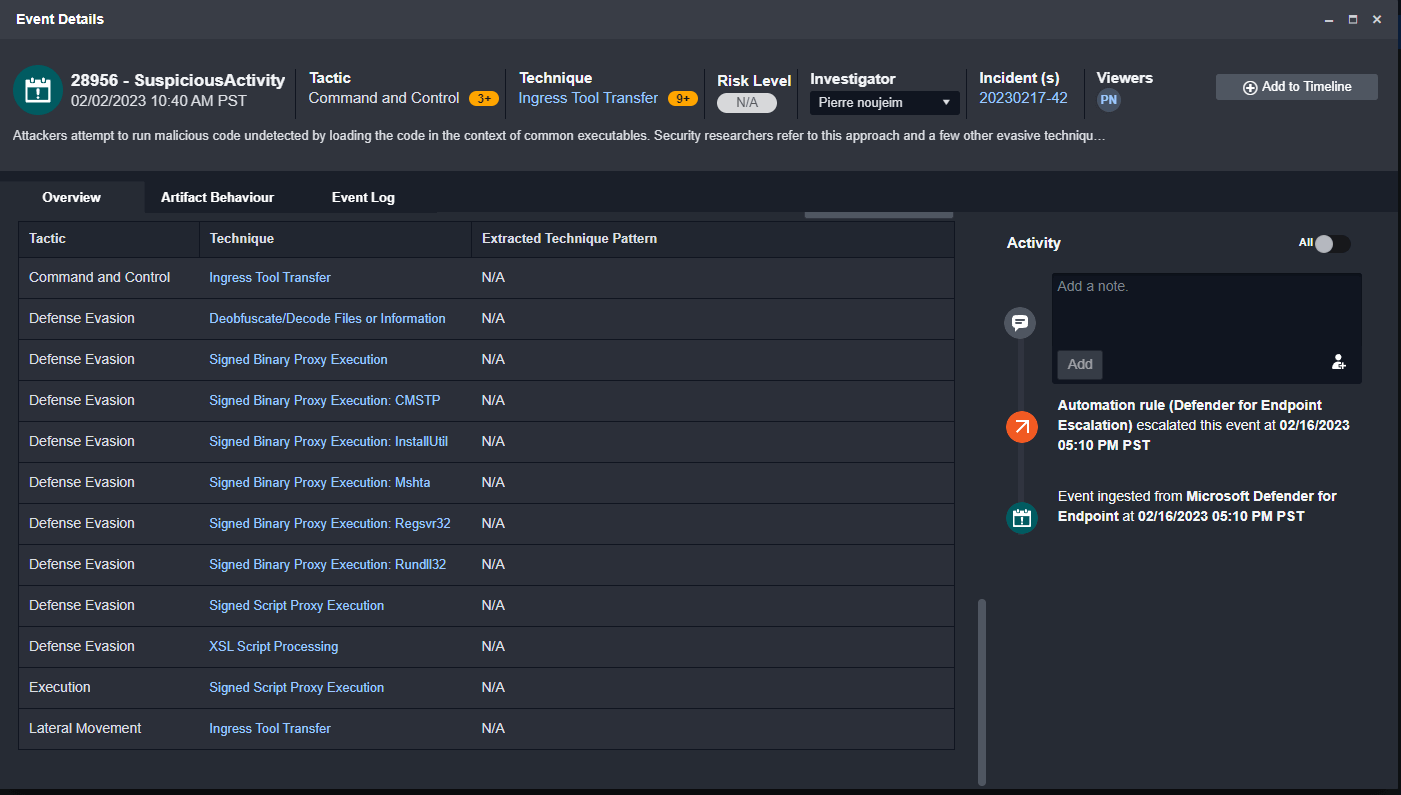
MITRE TTPs automatically tracked.
Conclusion
In conclusion, integrating Microsoft Defender for Endpoint with D3 Security’s Smart SOAR platform offers an efficient and automated approach to investigating and responding to cybersecurity incidents. By leveraging D3’s playbooks and integration commands, security teams can quickly analyze, correlate, and respond to threats, reducing response times and effectively mitigating risks. With D3 Security’s comprehensive SOAR capabilities and Microsoft Defender for Endpoint’s robust EDR features, organizations can significantly enhance their security posture and stay ahead of evolving cyber threats.




