D3 Security’s integration with SentinelOne offers an end-to-end solution for incident response teams. The video below shows an example of ingesting threats from SentinelOne, triaging them through Smart SOAR’s event playbook, then enriching and responding to escalated events.
Out-of-the-box, Smart SOAR users can choose from over 40 SentinelOne commands. These commands cover case management, data enrichment, incident response, and recovery.
The commands used in this demo are:
- Fetch Event
- Get Agent Info
- Get Agent Applications
- Get Sites
- List Accounts
- Create Query
- Get Events
- Block Hash
- Disconnect Agent from Network
- Initiate Scan
- Mitigate Threats
- Connect Agents to Network
- Update Threat Incident
Triage with the Event Playbook

Once an event has been ingested from SentinelOne, the event playbook parses it to see if the threat has been mitigated by the analyst or not. If it has been mitigated, it’s automatically dismissed and no further automations are executed. If it has not been mitigated, the event playbook searches for existing, open incidents that have affected the same agent. If a match is found, it will attach the event to the existing incident. If not, it will escalate the incoming event as its own incident.
Enrichment & Response with the Incident Playbook
![]()
The SentinelOne incident playbook has four main stages:
- Enrichment
- Correlation
- Eradication, and
- Recovery
Enrichment
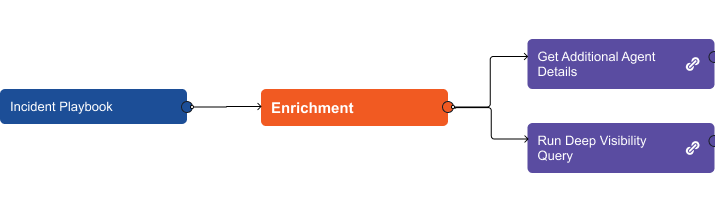
The enrichment section uses a nested playbook that can be easily added to other playbooks. The link icon to the right of the task name shows that there is a workflow underneath. By expanding on the nested playbook we can see the commands that run behind the scenes.
Get Additional Agent Details
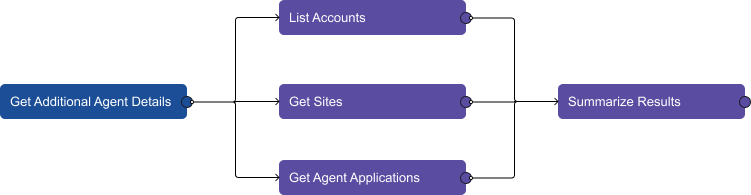
This workflow searches for sites that the involved user has been active on. It also searches for accounts associated with the target device and any applications running on that device. Then, the playbook parses the results and summarizes them for the analyst to review.
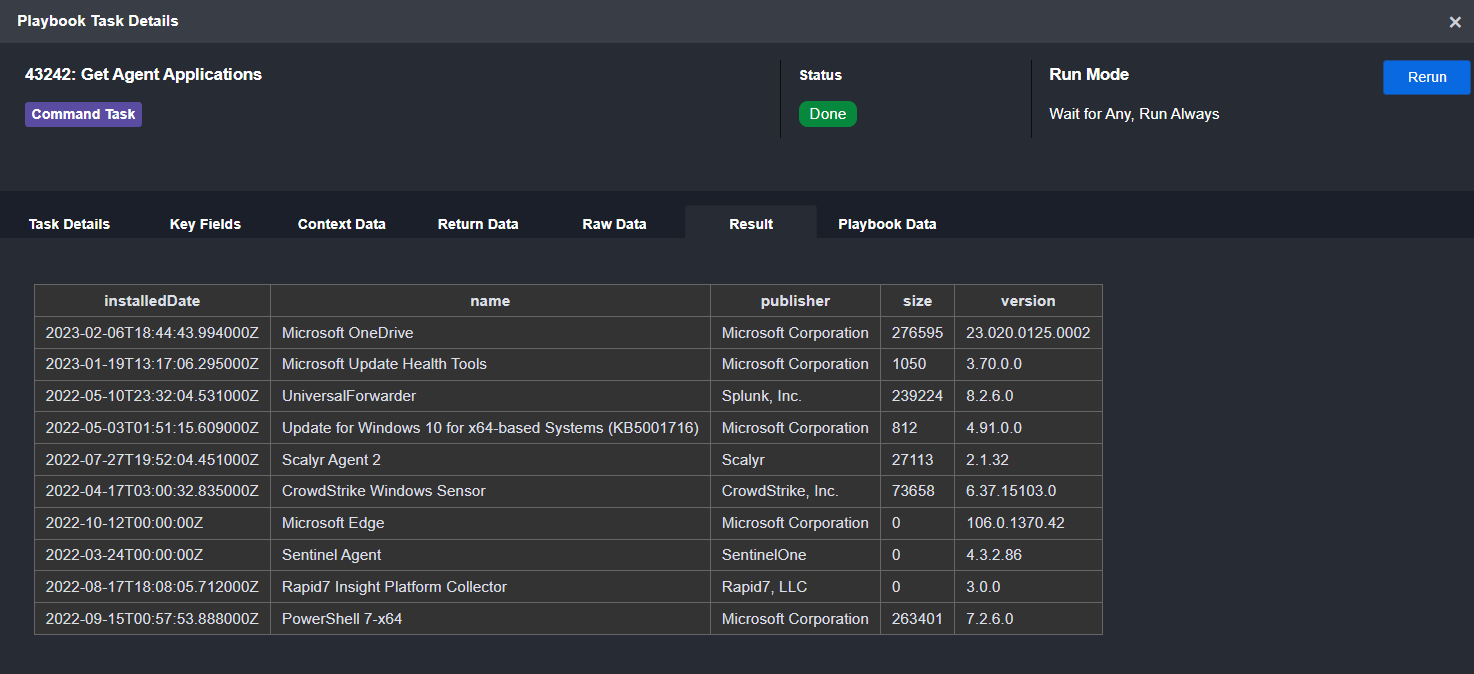
Agent Applications
Correlation
Once the enrichment stage is done, the playbook:
- Searches for related events in SentinelOne using a dynamic Deep Visibility Query.
- Searches D3’s incident database for related incidents, and
- Collects user activity logs from Active Directory.
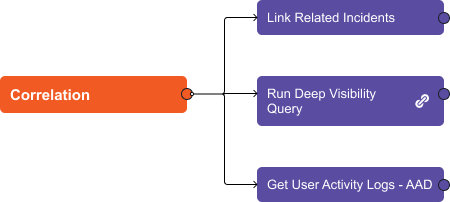
Deep Visibility Query
![]()
This nested playbook creates a deep visibility query to search for related alerts in SentinelOne and adds them to the D3 incident if they’re found.
The query is built using dynamic paths that point to fields in the original alert. Here you can see we’ve created two variables. One for SrcProcName and the other for TgtProcName:
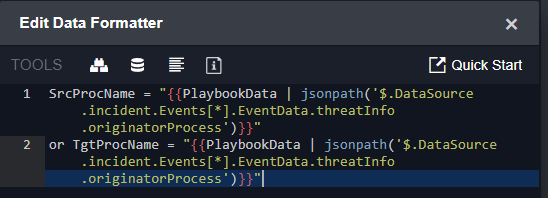
You can see the values populated when the command is executed with real data:
Eradication
Once enrichment is complete and the investigation team has reviewed the data, they can proceed with eradication.
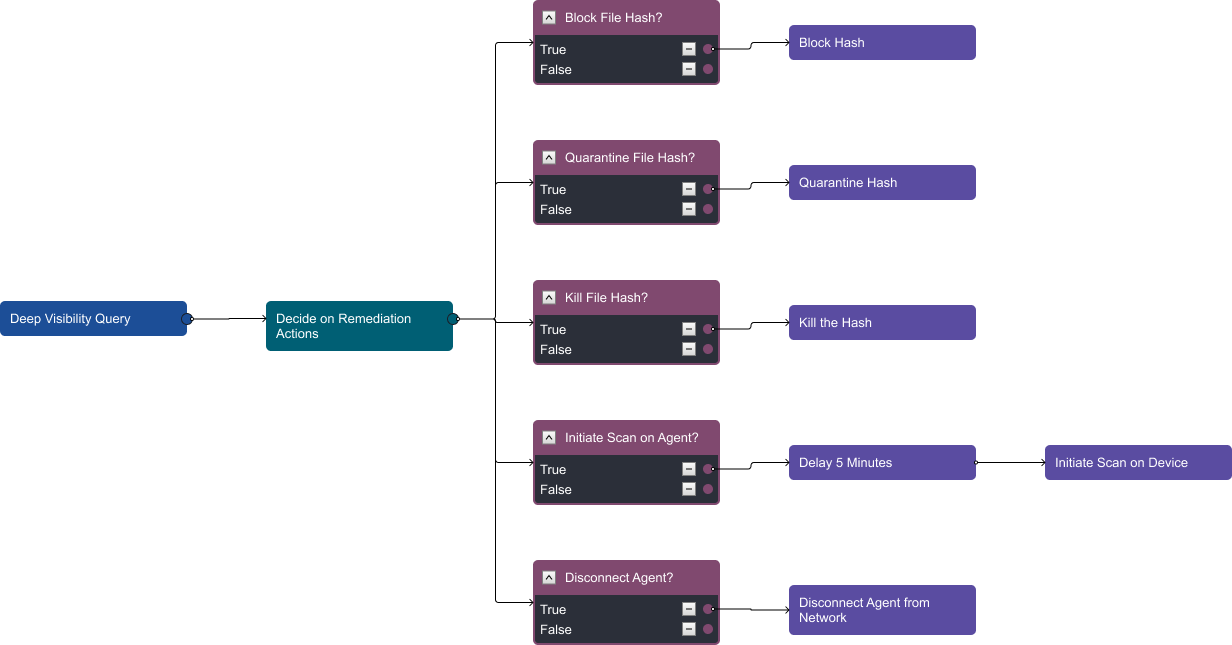
The interaction task prompts the analyst to determine which remediation actions they would like to take. After marking true or false in the inputs, their response will be recorded and the correct path in the conditional tasks will trigger:
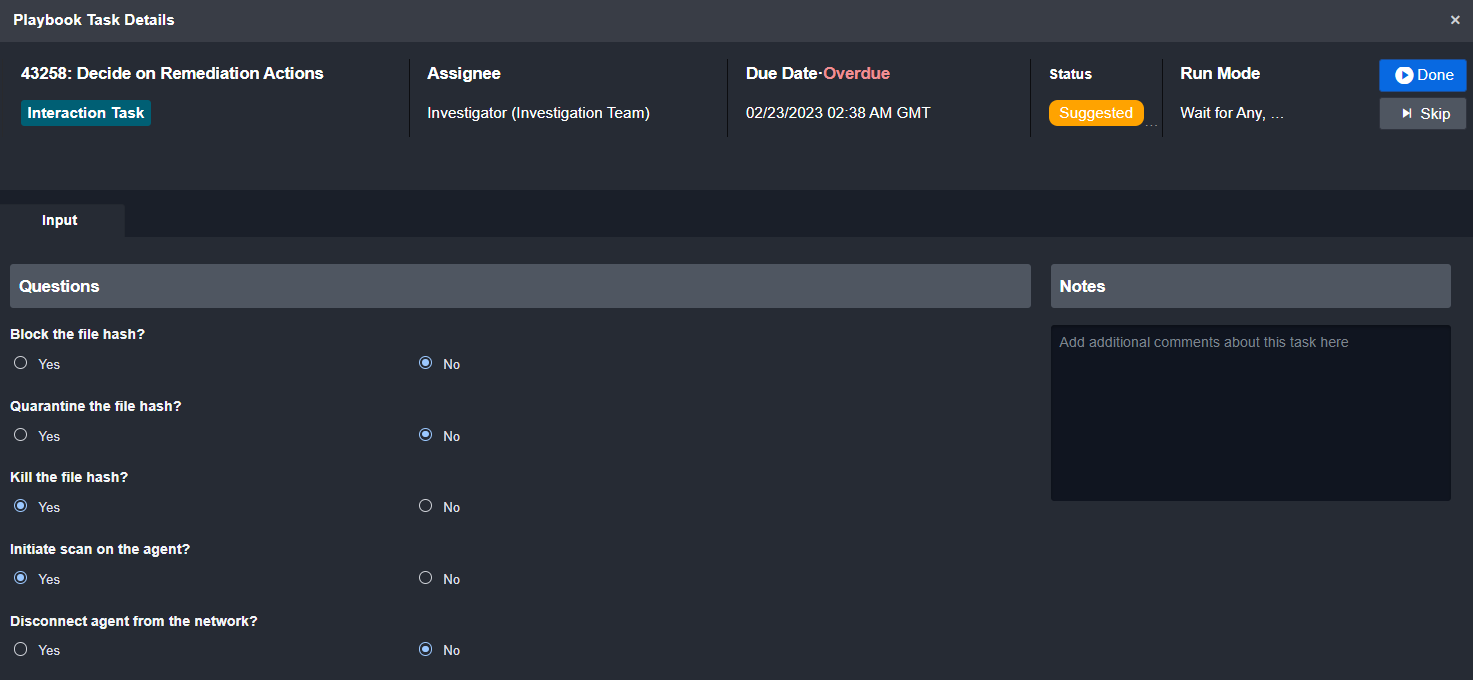
Input prompt
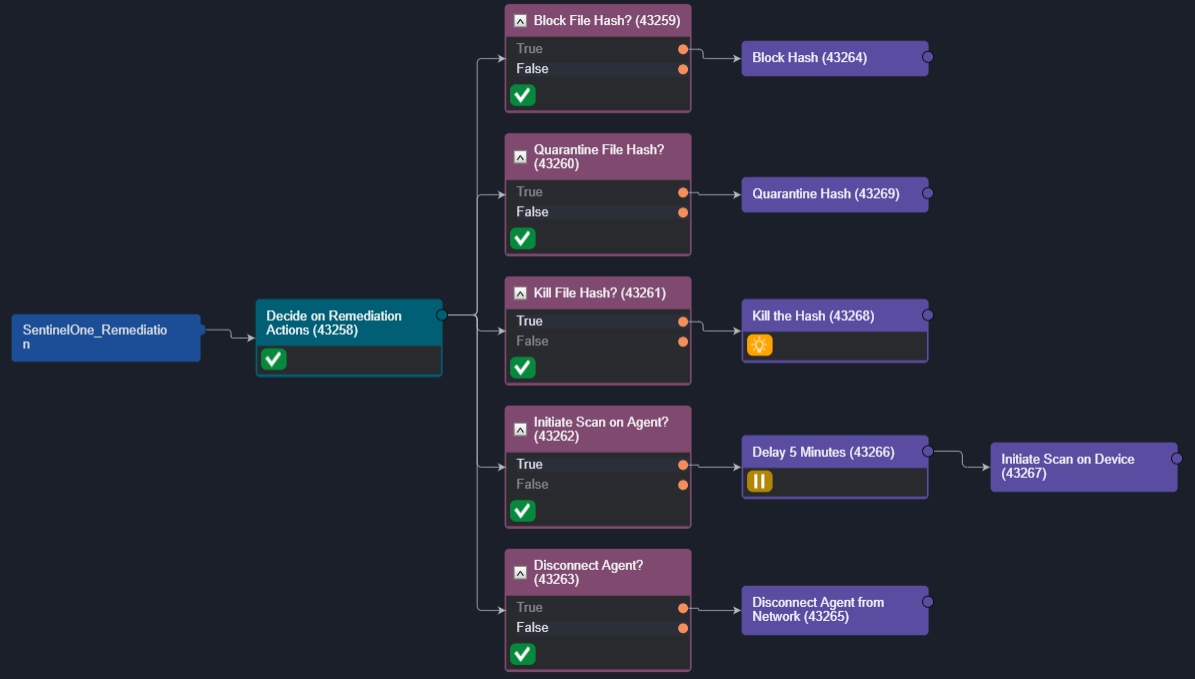
Inputs recorded by conditional tasks.
Recovery

Finally, agent information is collected to see if there are active threats found by SentinelOne. If none are found, the playbook reconnects the agent back to the network, closes the D3 incident, and closes the threat in SentinelOne for synchronicity.
Conclusion
D3 and SentinelOne make a powerful combination that helps users quickly find indicators of false positives, dismiss them, and run eradication activities in the devices that pose serious risks.
A typical workflow takes 60-90 minutes. With D3’s integration to SentinelOne this same workflow takes 5-10 minutes. At the same time, D3 is always updating our SentinelOne integration to keep you at the edge of what’s possible.




