In this post, we’ll be using SentinelOne, VirusTotal, and Microsoft Entra ID to investigate and respond to a potential trojan virus. SentinelOne provides deep enrichment on the endpoint, VirusTotal will tell us if the file has been marked as malicious by the wider community, and Microsoft Entra ID will give us more information on the user involved. We will also use Entra ID to reset the user’s sign-in session.
The alert we’ll be reviewing was generated by SentinelOne. Here we can see key details extracted from the alert and mapped to D3’s system fields. This normalization lets you analyze artifacts between different tools in your environment. The artifacts we’re most interested in are the agent id, threat id, file hash, and the affected user.
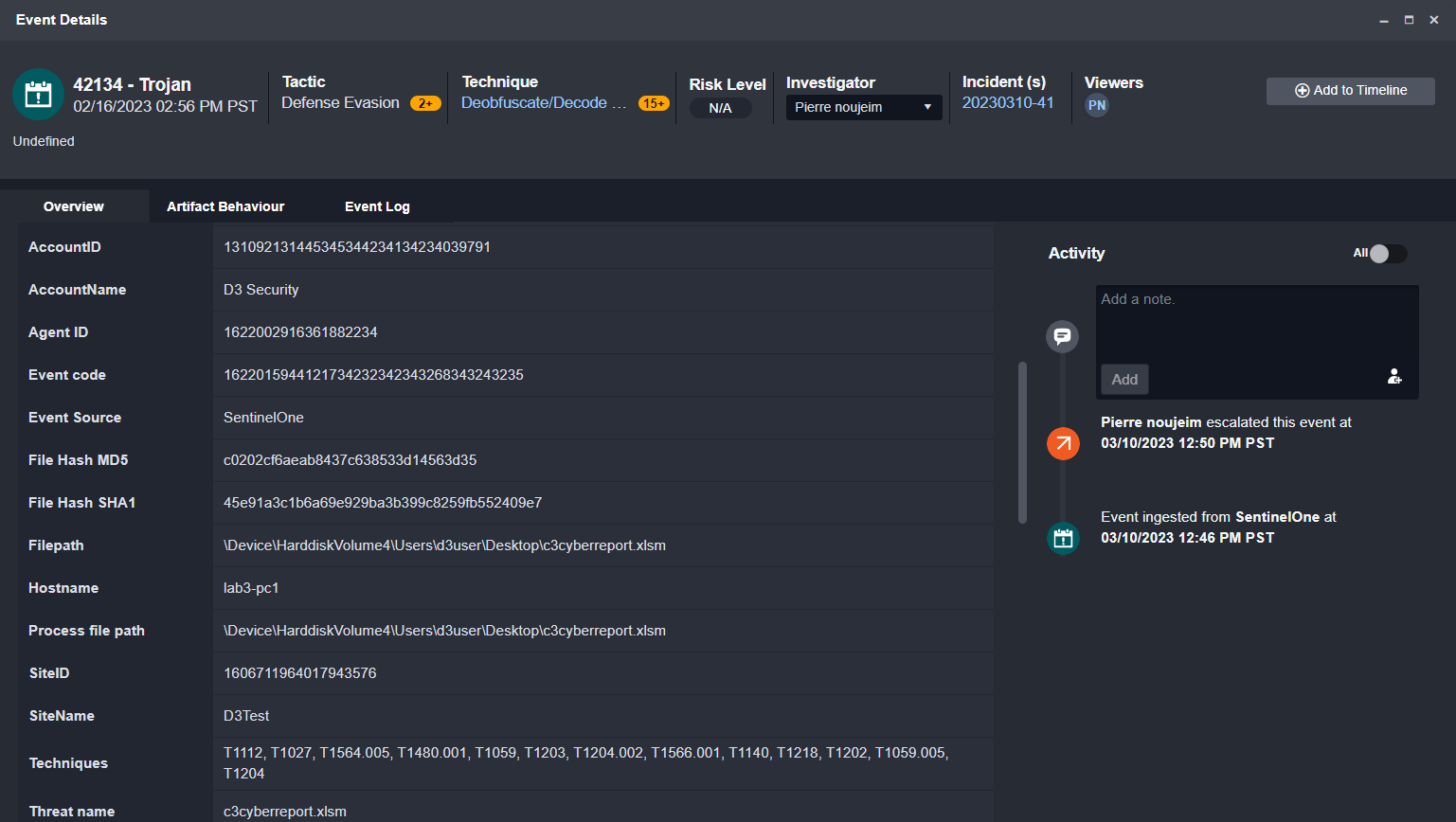
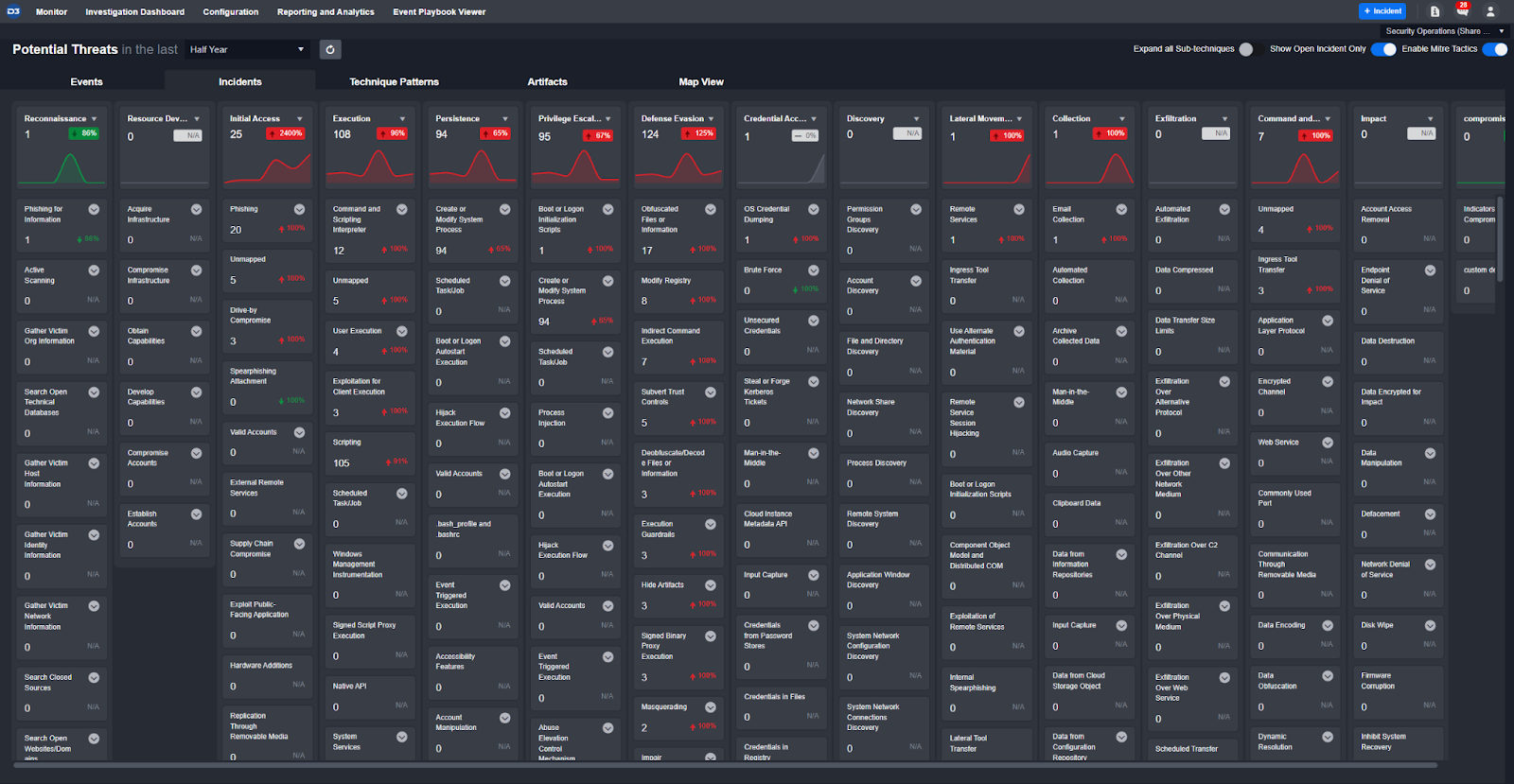
SentinelOne has also included MITRE TTPs in the original alert. D3 automatically adds them to our global Monitor dashboard so users can have a birds-eye view of the active threats in their environment:
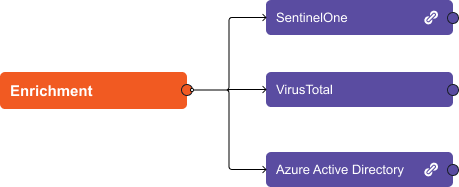
The incident playbook executed on this alert has three main stages: enrichment, correlation and remediation.

Playbook Stage: Enrichment
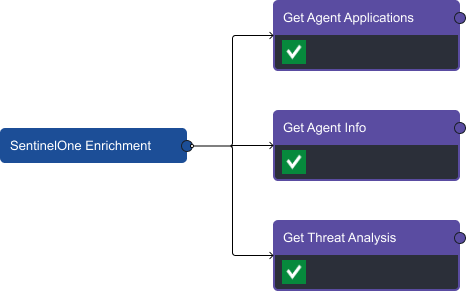
In the enrichment stage, we use SentinelOne, VirusTotal, and Microsoft Entra ID to collect relevant data on the agent, file hash, and user. The ‘link’ to the right of the task name means there is a nested playbook within it. By expanding on the SentinelOne task we can see three enrichment tasks: Get Agent Applications, Get Agent Info, and Get Threat Analysis.
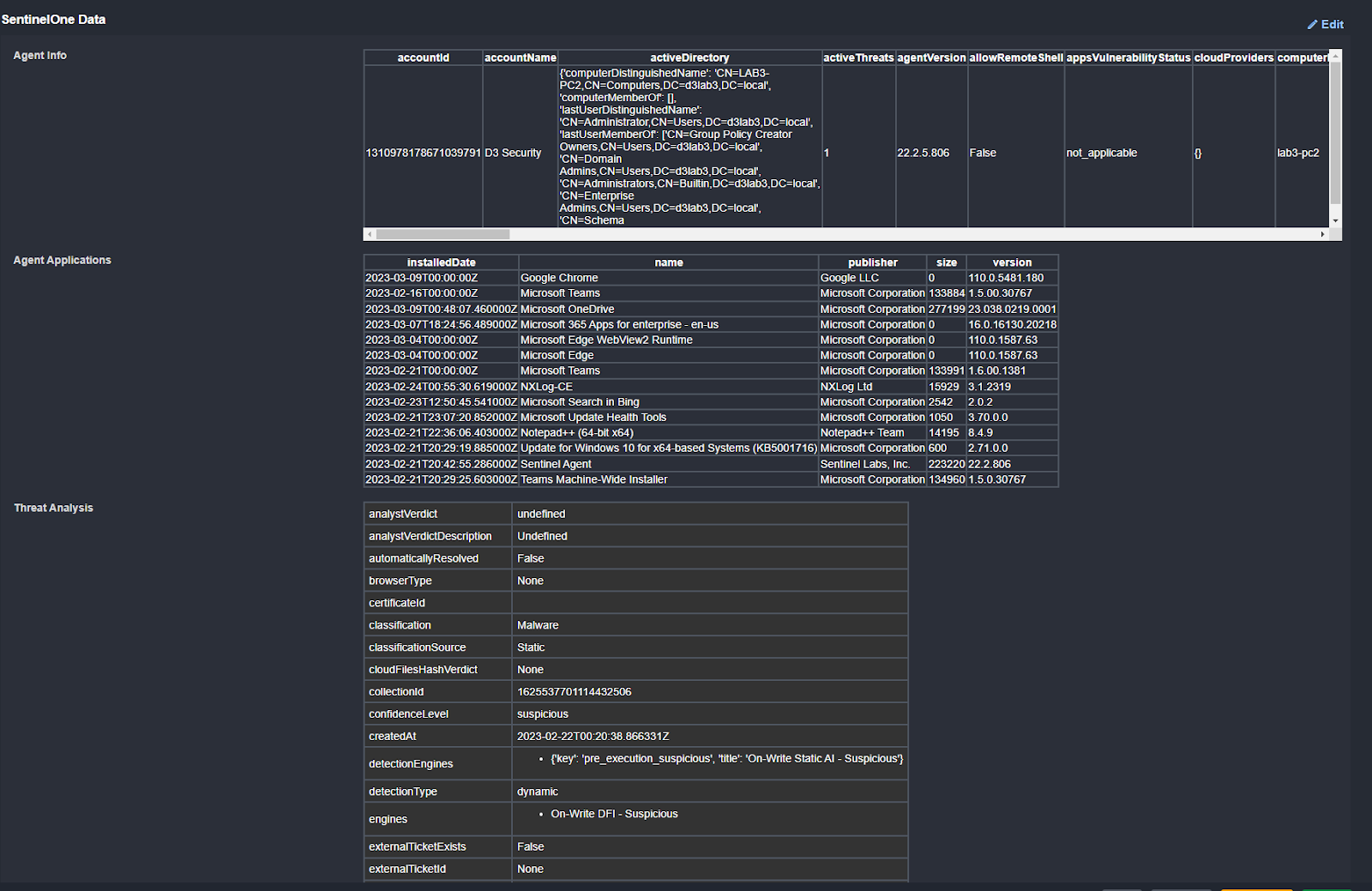
Get Agent Applications shows us all of the applications installed on the agent. Nothing suspicious is found here:
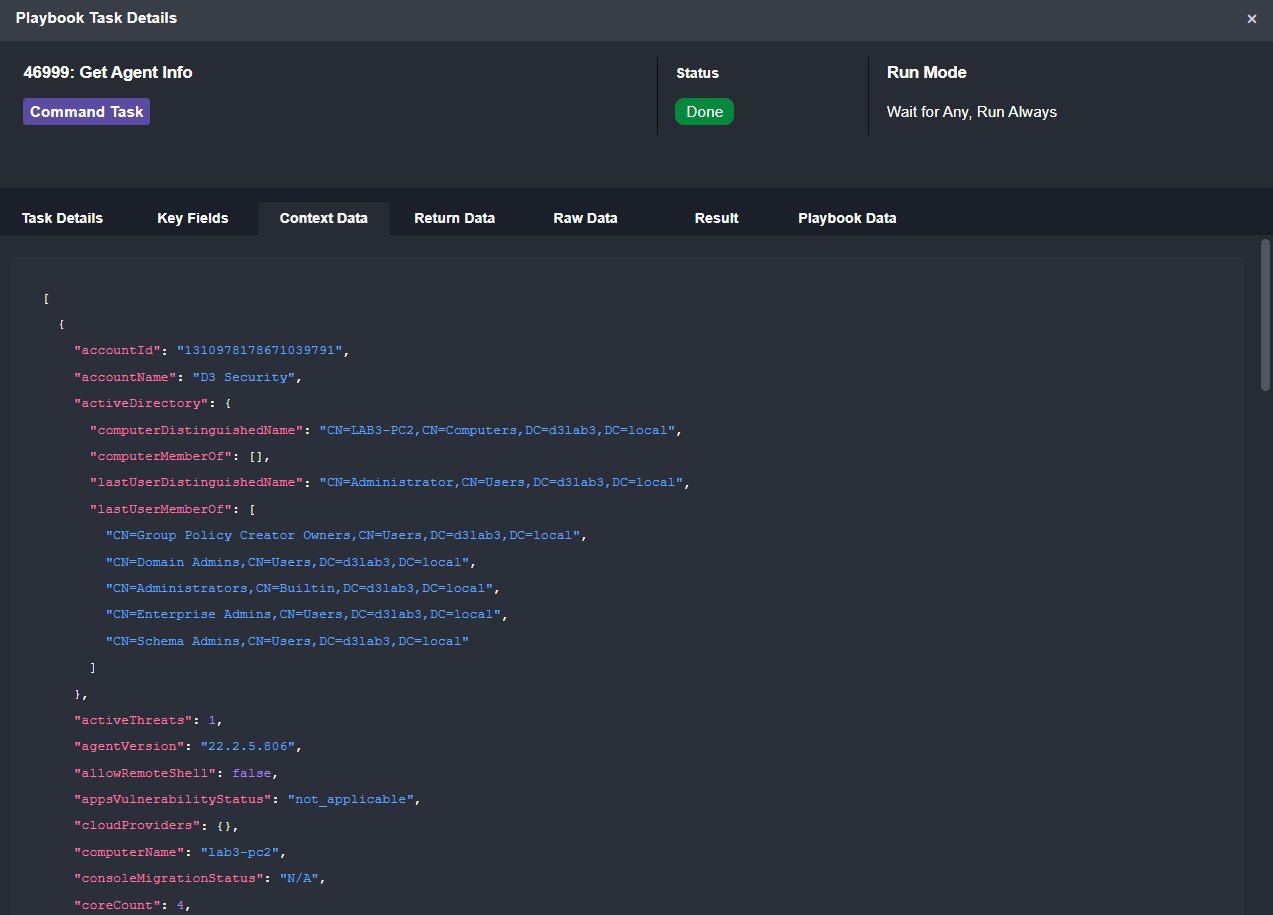
Get Agent Info shows us any data on this agent that wasn’t included in the original alert.
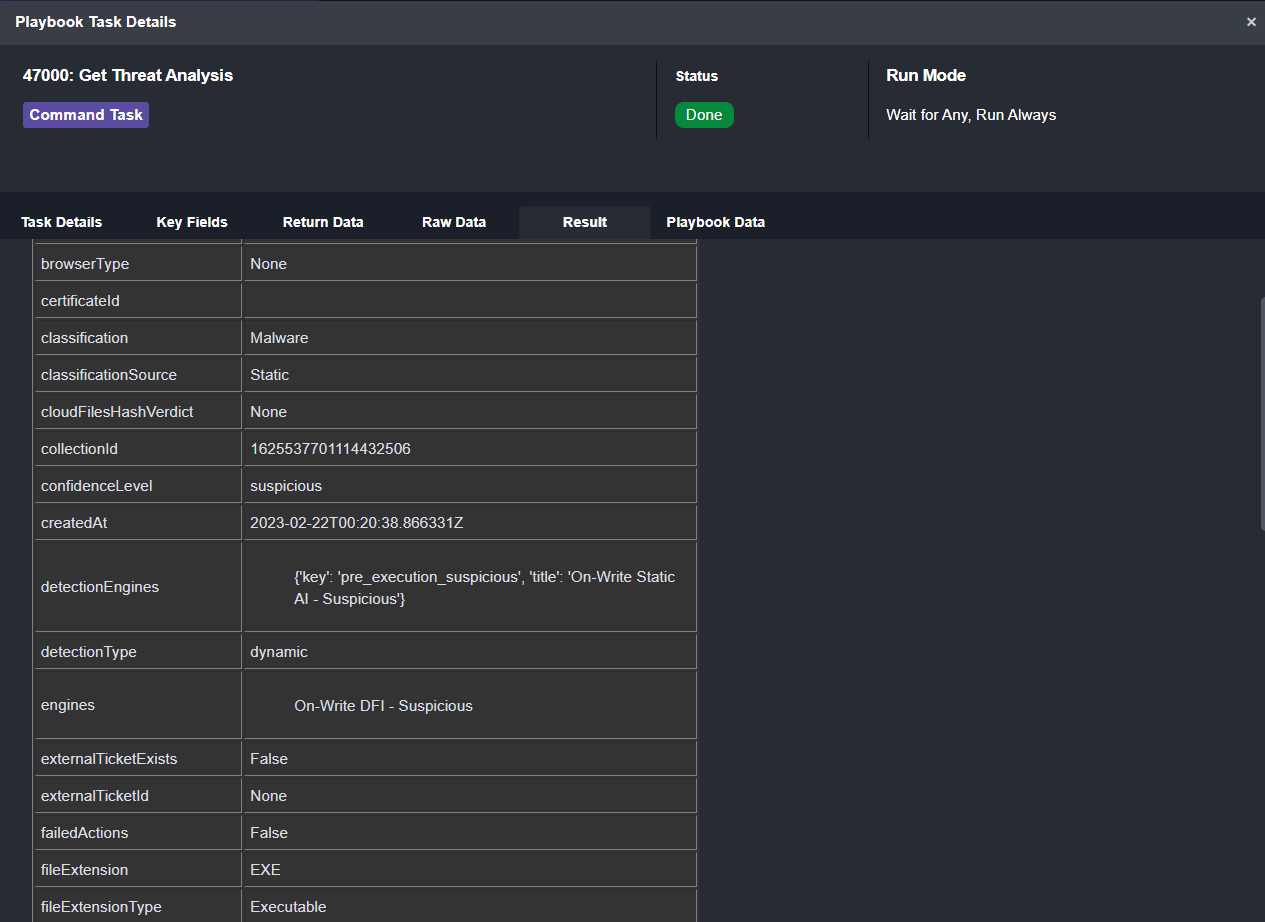
Get Threat Analysis uses the threat ID from the original alert and pulls in its classification, confidence level, verification type, initiated users, and more:
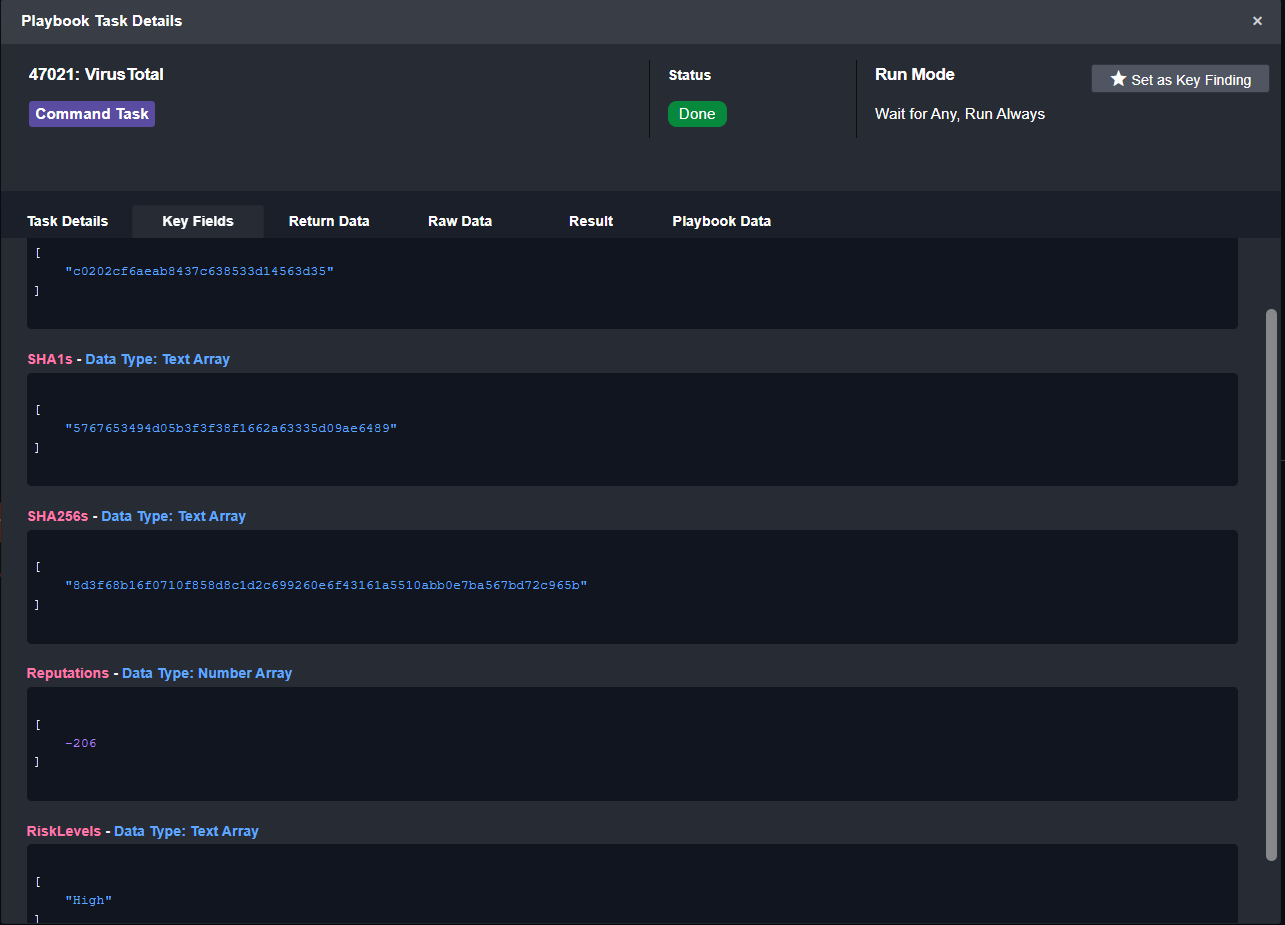
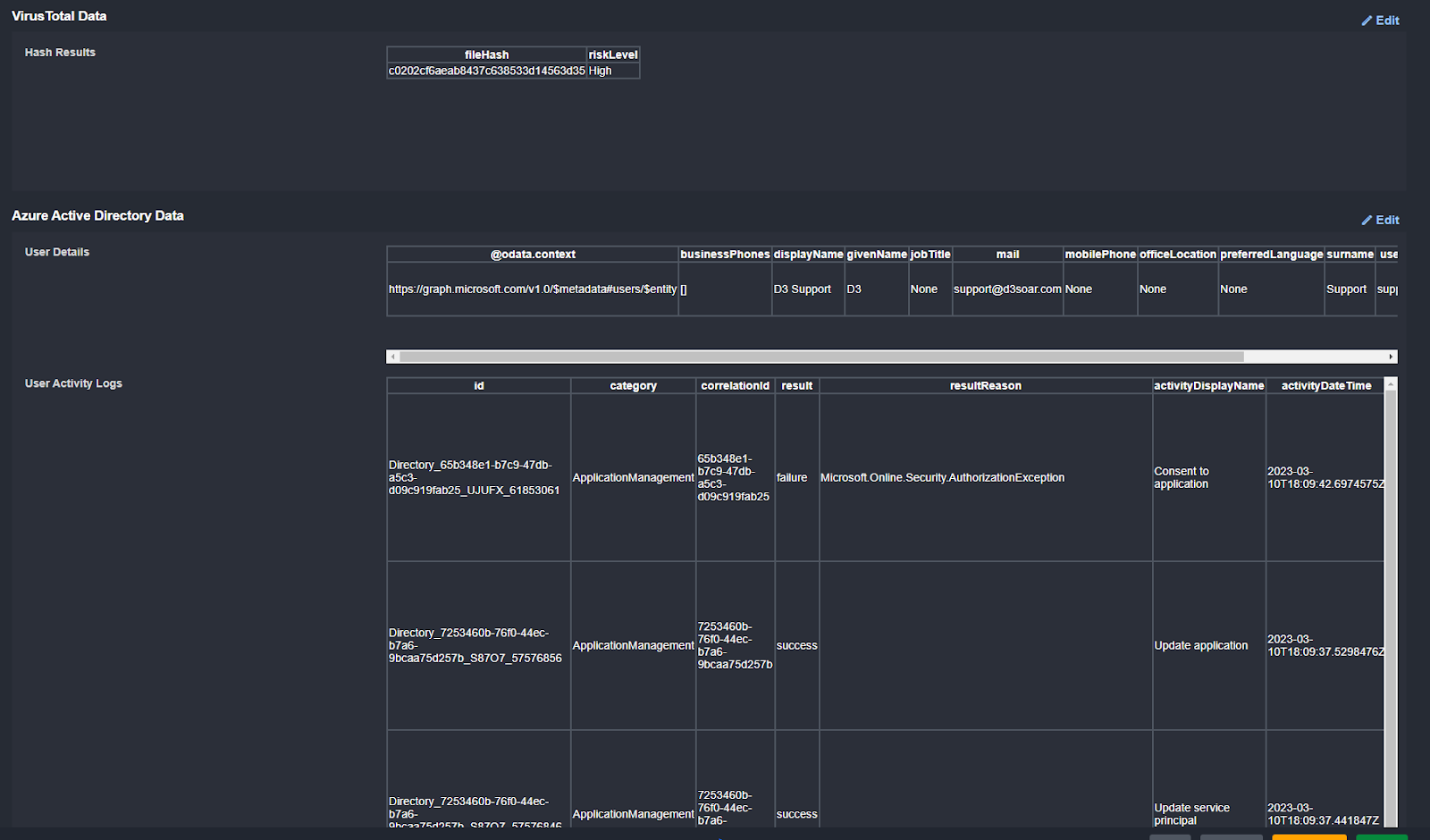
From VirusTotal we can retrieve the reputation and risk levels for the MD5 hash. From the summary we can see that the risk level is “High”.
Within the Microsoft Entra ID enrichment task we can ingest activity logs on the user as well as general information on the account:

From the activity logs we can see the category of action and whether or not it was successful:
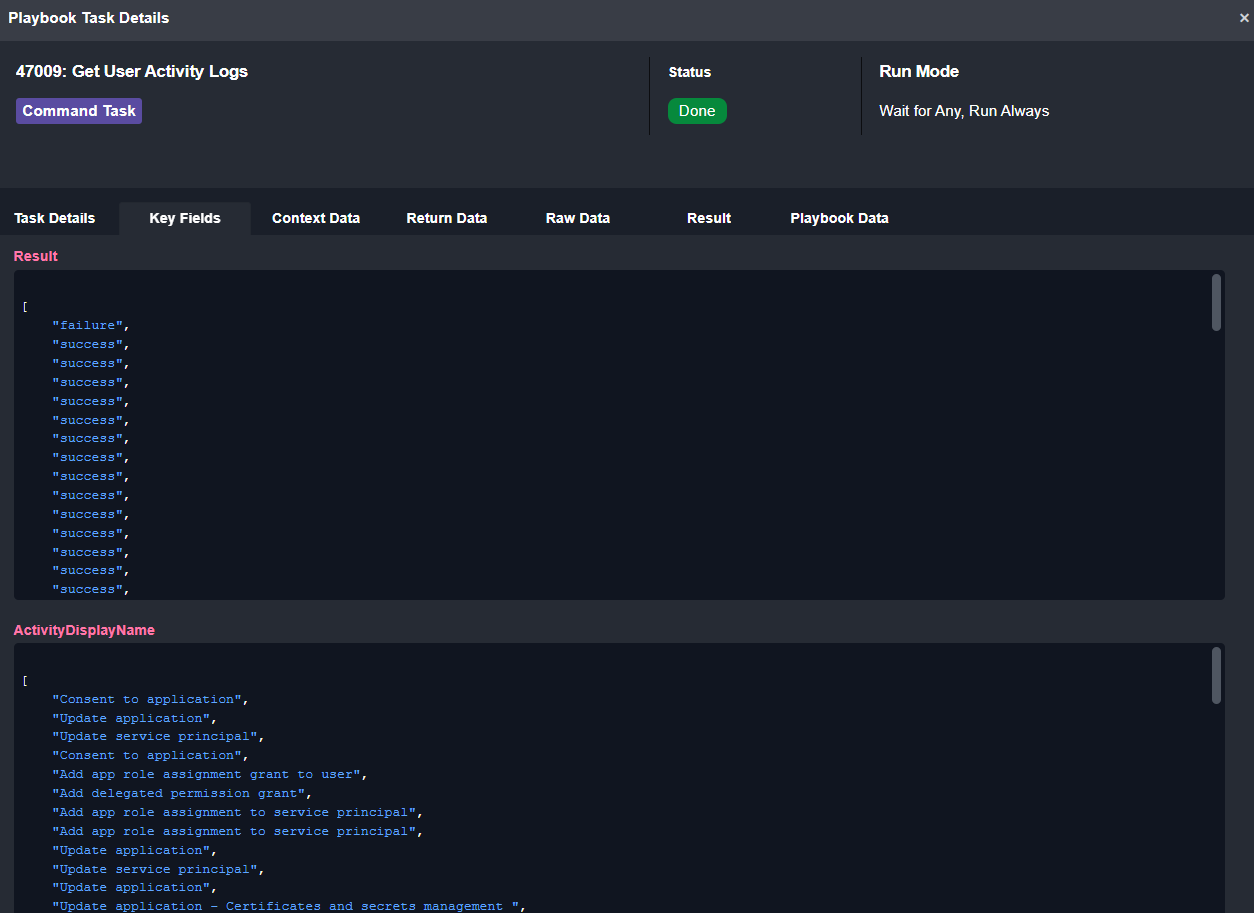
All of the enrichment data is displayed to the analyst in table format so they don’t have to comb through lines of raw data:
Playbook Stage: Correlation
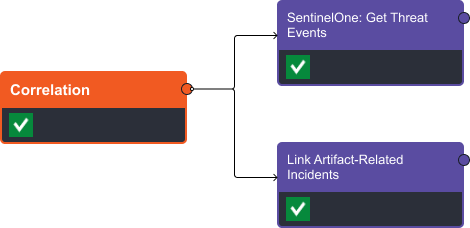
In the correlation stage we search the SentinelOne database for any events that contain the threat ID associated with our trojan file and search D3’s incident database for other incidents that have this file included as an artifact.
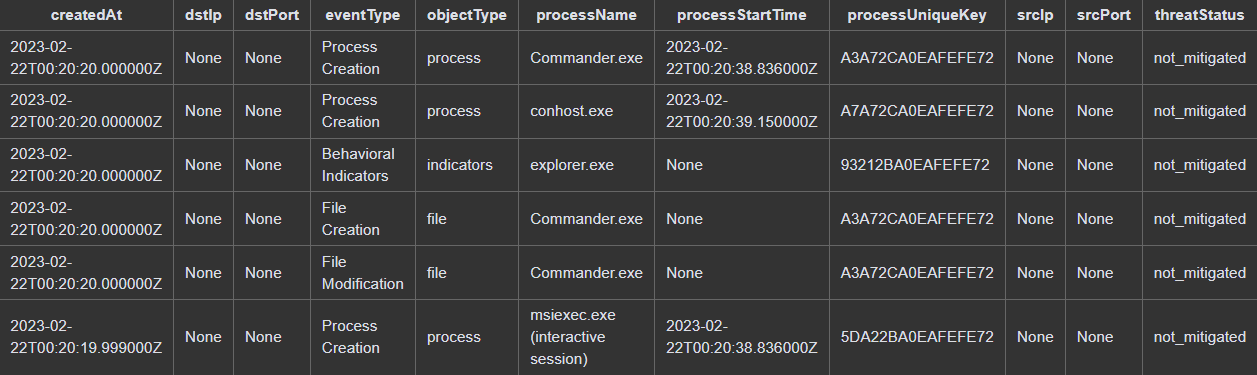
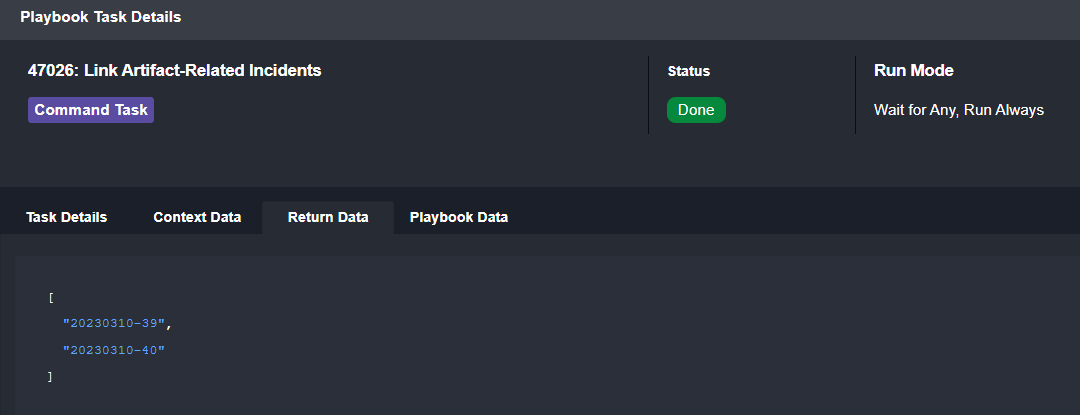
The results show six events from SentinelOne and two related D3 incidents:
Playbook Stage: Remediation
In the remediation stage we have three options:
- Isolate the endpoint with SentinelOne.
- Revoke the user sign-in sessions, and
- Reset the user password.
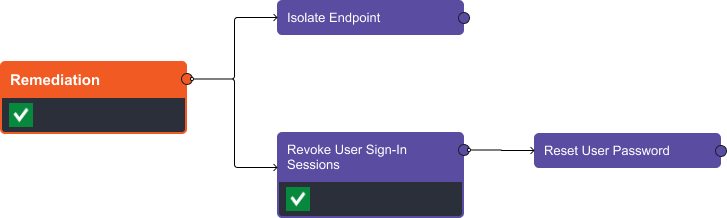
For this case, we’ve revoked the user’s sign-in sessions and have skipped the reset and isolation commands.
Return on Time
As a reusable playbook, this can be executed any time a trojan alert from SentinelOne is ingested into D3. The remediation process can be controlled with manual check points or automated entirely. Typically, playbooks are used to automate the collection of contextual data to assist with the analyst’s decisions.
The enrichment and correlation stages took five seconds to run. When comparing this to the manual process of querying and consolidating data manually, for each alert, it’s easy to save 90% or more of your investigation time on each alert.




