A recent survey revealed that up to 90 percent of companies were hit by ransomware in 2022. In the wake of such unrelenting attacks, often perpetrated by state-sponsored threat actors, spending on new cybersecurity technologies is usually on the top of mind for every CISO and security manager. But no matter how much budget you’ve structured to protect your organization from cyber threats, unless you spend it on the right technology, processes, and people, you’re wasting your money.
Security Orchestration, Automation and Response (SOAR) is quickly becoming a foundational element of modern enterprise security architecture. Using SOAR in your organization can transform your security operations and help you achieve a strong cybersecurity posture.
What’s the key benefit of SOAR? In a nutshell, SOAR is a force multiplier that boosts the quality and scale of incident response at the security operations center (SOC). In this blog, we are going to answer the question of how it enables this outcome and explore why SOAR has become an indispensable capability for SOC teams.
SOAR Improves SOC Productivity
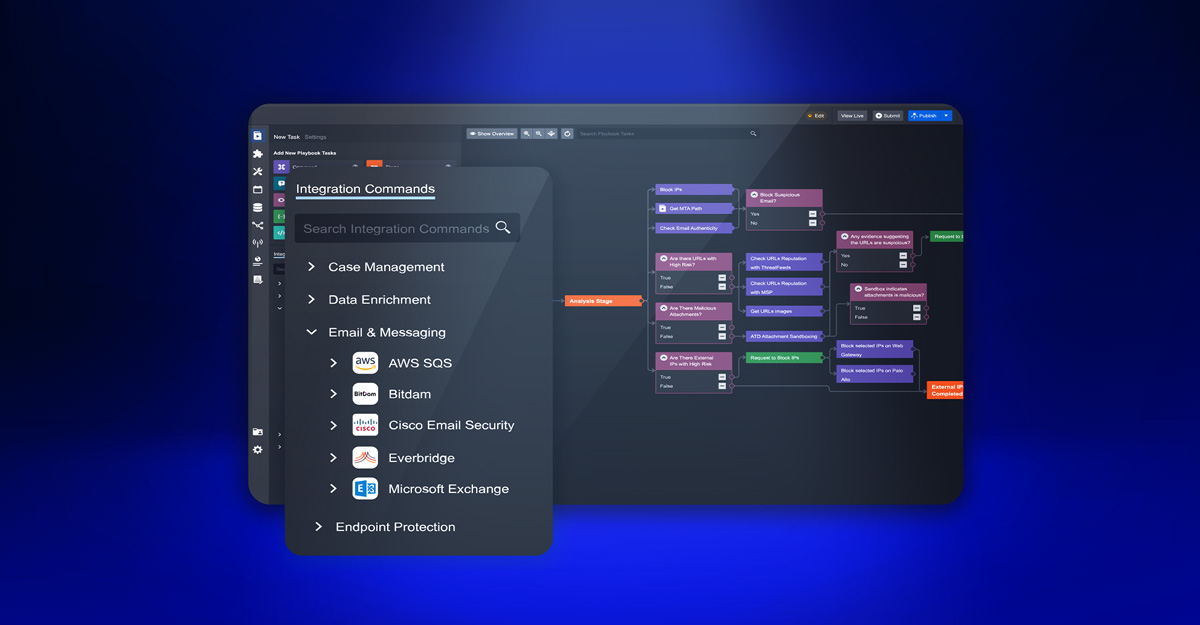
The SOC’s effectiveness relies on its ability to aggregate and react quickly to security incidents, but this pursuit can be hampered by a lack of automation. SOAR playbooks help operationalize institutional knowledge, upskill SOC resources, and enhance the quality and consistency of incident response. SOAR enables faster incident detection, mitigation, and containment through the automation of repeatable incident response tasks along with improved situational awareness across disparate data sources. This allows teams to spend less time on routine tasks, such as running queries when an alert fires, sending a file to a detonation chamber and checking the reputation of hashes, IP addresses, and domain names. Such tasks can be automated, enabling them to allocate their time and attention to investigating cases or developing new skills. With playbooks designed to accelerate time to resolution, users can quickly deploy response actions without having to leave the SOAR platform or having to copy/paste between systems. Ultimately, this leads to quantifiable improvements in SOC metrics such as MTTR (mean time to remediation), MTTT (mean time to triage), etc.
Read: How a Global Fintech Company Improved its MTTR by 10x
SOAR Keeps Your Focus on Threats That Matter
Without automation, SOC analysts must play a constant game of alert Whack-A-Mole, chasing alerts from one system to another in search of meaningful information. SOAR helps you manage the high volume of security alerts by reducing false positives. By taking alerts from multiple sources, enriching them with threat intelligence, and correlating them with data from other security tools, you can consolidate and auto-dismiss low-fidelity alerts to significantly reduce your alert volume. When incidents do occur, SOAR can connect the dots, so you see what information is missing from an alert or which events happened immediately before or after an incident occurred. That way you can make better decisions about how to respond.
Read: Automate up to 98% of Alerts With the Event Pipeline
SOAR Helps You Prevent Burnout and Upskill SOC Talent
It takes a lot of effort to recruit and retain SOC resources, due to a persistent skills gap, compounded by a high degree of stress faced by SOC resources on the job. For most security professionals, long hours and poor work-life balance are unavoidable realities. Nearly two out of three SOC resources have considered changing careers due to on-the-job pain, according to a survey conducted for Ponemon’s 2021 SOC Performance Report. Information overload (70%), lack of resources (58%), and inability to capture actionable intelligence (56%) were cited as major pain points of working on the SOC.
“It’s a life-sucking job to sit there and look at massive amounts of data coming in and trying to figure out what you should be paying attention to. You’re petrified that you might miss something and have a customer suffer from that,” says Stephan Tallent, CRO at Master MSSP High Wire Networks in a recent workshop, describing SOC life. With D3, they improved average response times from 30 minutes to an hour, to 5.5 minutes.
SOAR can help you retain SOC talent by eliminating manual and repetitive actions that add little value and crush morale. It addresses the resource crunch by automating such tasks. By prioritizing, consolidating, and auto-dismissing benign alerts and providing context on serious threats, it helps manage alert overwhelm. Leverage SOAR’s automation to ensure that your SOC doesn’t have to write an incident report again. With SOAR, SOC teams can focus their efforts on more challenging and rewarding pursuits. SOAR playbooks and workflows make it easy for every SOC resource to lock on to the codified IR practices and processes documented by the SOC’s most experienced members, enabling them to perform tasks above and beyond their level of expertise.
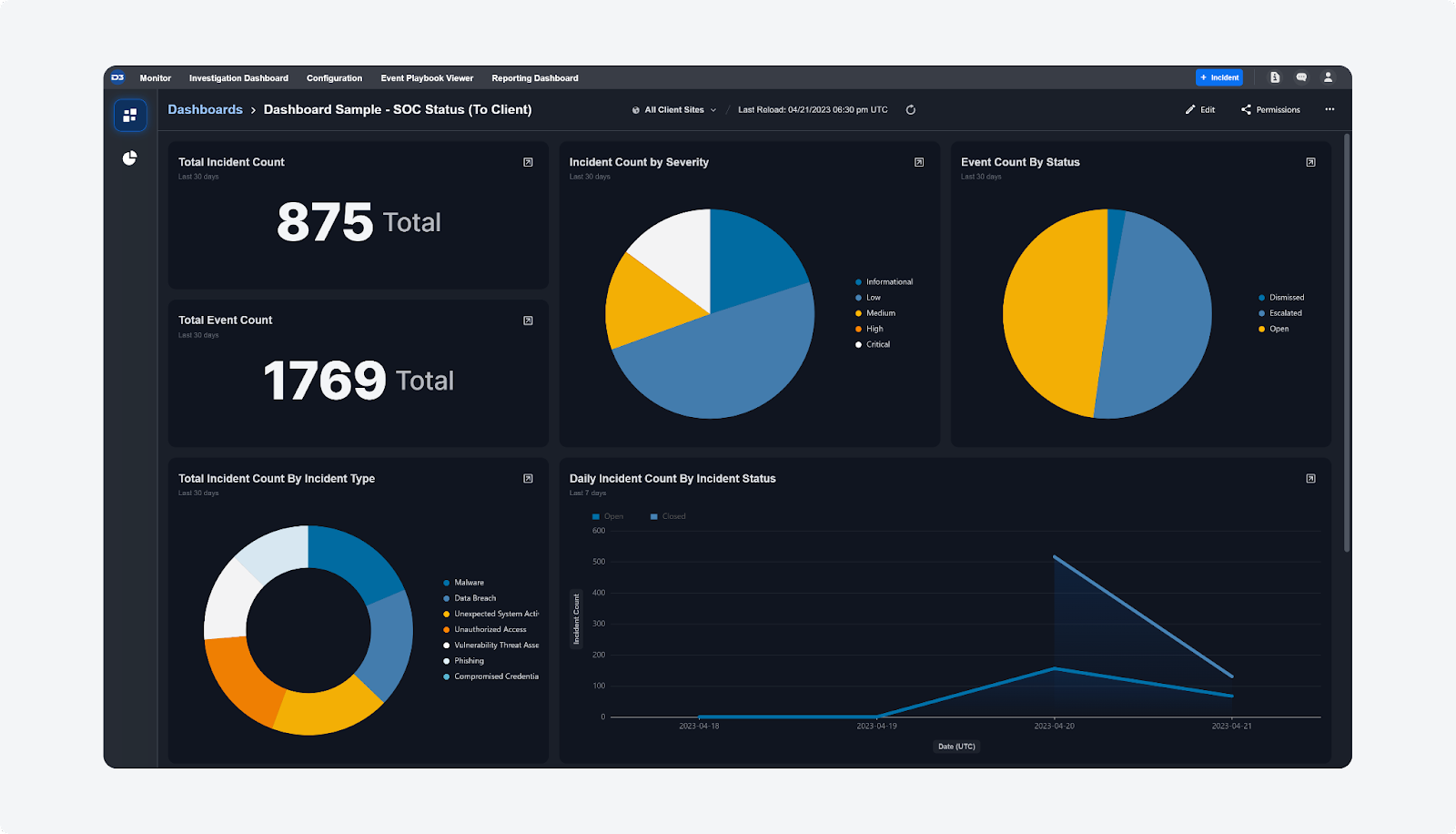
SOAR Makes it Easy to Measure Your SOC’s Operational Efficiency
SOAR platforms capture a ton of metrics that can help SOC teams continuously improve the efficiency of their security operations. Smart SOAR’s custom dashboards and reports provide real-time data on key metrics such as Time to Respond, Time to Contain, Time to Remediate, Time to Resolve, and Time to Complete for cases and incidents. You can analyze these data points to get insights into patterns and trends and areas for improvement. We also understand that your analysts don’t have time to fill up spreadsheets – Smart SOAR lets you schedule reports to be sent to key stakeholders.
SOAR Improves Your Cybersecurity Posture
As a second-order effect of improved operational efficiency and alert prioritization, SOAR makes your organization more resilient and prepared to thwart cyberattacks by reducing response and dwell times. Smart SOAR takes it a step further by operationalizing the MITRE ATT&CK framework, enabling SOC teams to correlate and validate alerts with ATT&CK TTPs, perform kill chain investigations, and get visibility into overall ATT&CK trends. Instead of just being reactive, it also enables you to proactively hunt for threats and put IOCs and TTPs under surveillance.
Benefits of SOAR for MSSPs
In addition to all the security operations advantages we’ve described so far, managed security service providers (MSSPs) can draw many unique benefits from SOAR as well. Here are a few outcomes enabled by Smart SOAR:
Faster Onboarding of New Customers
Our out-of-the-box playbooks and unlimited codeless vendor integrations shorten implementation time for MSSPs of any size. One of our customers, a global MDR leader with thousands of customers, has reduced their customer tenant onboarding process to a simple 5-minute and 9-click process through a custom Zendesk integration.
New Revenue Streams
We enable MSSPs to provide high-value capabilities such as Managed Detection and Response (MDR), MITRE ATT&CK TTP reporting and gap analysis, threat hunting, vulnerability management, and identity management.
Improved Profitability
Through operational improvements from automation and orchestration, MSSPs can lower their overhead and improve their customer-to-analyst ratio.
Unlock More Benefits With The World’s Leading Independent SOAR Platform
At D3 Security, we’re laser-focused on just one thing: building the industry’s most advanced SOAR platform. As a result of our work with Fortune 500 companies and leading MSSPs, our SOAR platform is capable of scaling up to meet the most demanding SOC teams. Learn more about Smart SOAR’s benefits, and how we can customize it to your unique requirements. Sign up for a demo today.