-

Stop Ransomware in its Tracks: Suspicious File Activity
The Threat Scenario Consider a scenario where your file server, “D3Cyber-FileServer,” triggers an alert. The alert indicates an encryption attempt on “important_document.docx” by the command-line…
-

Implementing MITRE D3FEND for ATT&CK Technique T1059: Command and Scripting Interpreter
Command and Scripting Interpreter attacks were the second most common technique seen in MITRE’s Engenuity’s Sightings Ecosystem report, representing 15.77% of 1.1 million sightings. MITRE’s…
-

Implementing MITRE D3FEND for ATT&CK Technique T1053: Scheduled Task/Job
Scheduled task/job threats, which make up MITRE ATT&CK Technique T1053, can have severe implications for an organization’s security. MITRE also outlines how to address this…
-
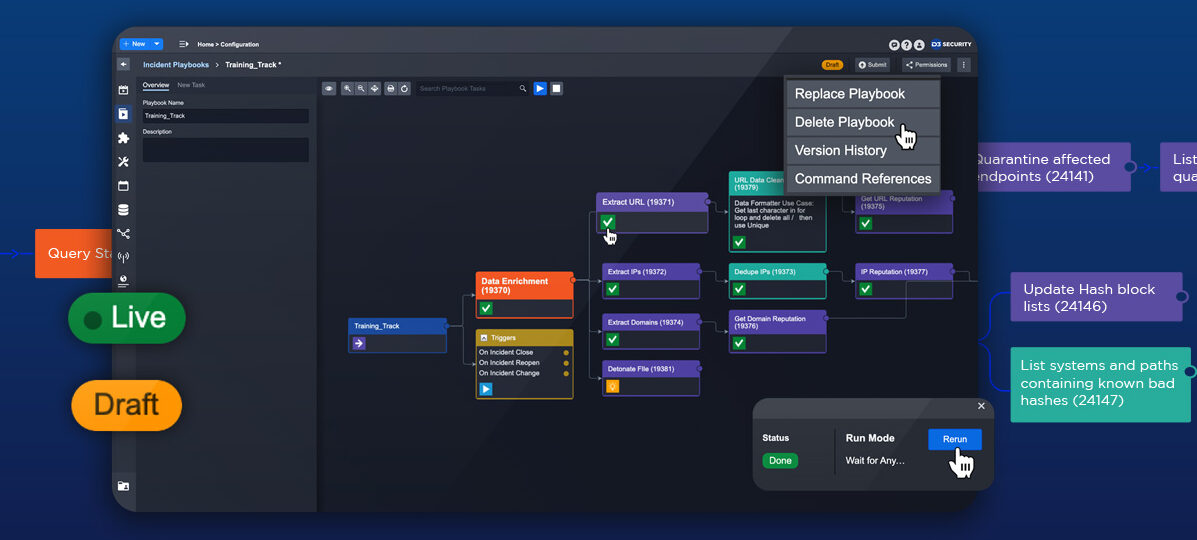
Smart SOAR Gives You the Best Cybersecurity Playbooks
Security operation center (SOC) teams need security orchestration, automation, and response (SOAR) because it provides a simple, efficient, and effective method for response to the…
-

Why Smart SOAR is the Best SOAR for SentinelOne
D3 Security’s integration with SentinelOne offers an end-to-end solution for incident response teams. The video below shows an example of ingesting threats from SentinelOne, triaging…
threat mitigation
Select a term…