Command and Scripting Interpreter attacks were the second most common technique seen in MITRE’s Engenuity’s Sightings Ecosystem report, representing 15.77% of 1.1 million sightings. MITRE’s D3FEND matrix outlines how to address this technique however security teams struggle to consistently implement D3FEND’s recommendations.
This blog demonstrates how Security Orchestration, Automation, and Response (SOAR) can be used to consistently implement each stage of the D3FEND framework.
MITRE ATT&CK Technique Overview
The Command and Scripting Interpreter technique (ATT&CK ID T1059) refers to the exploitation of command-line interpreters to execute malicious commands on a targeted system. Interfaces, such as PowerShell, Bash, or Windows Command Prompt, provide a direct means to interact with the underlying system, allowing users to execute commands and scripts to perform legitimate administrative tasks. These interpreters are far-reaching and common across many devices, making them attractive targets.
The D3FEND Matrix
The MITRE D3FEND Matrix has six stages: model, harden, detect, isolate, deceive, and evict. Each has different tasks that can be completed to address T1059. In the examples below, I will show you how Smart SOAR playbooks can turn D3FEND’s recommendations into automated workflows.
Read: What Are MITRE ATT&CK and MITRE D3FEND?
Stage One: Model
D3FEND Recommendation: Asset Vulnerability Enumeration. In stage one, MITRE recommends running vulnerability scans on affected devices. This is possible in Smart SOAR using one of our many integrations. For example, Qualys Vulnerability Management can be used to:
- Get Scanned Hosts: Retrieve a list of hosts that have been previously scanned by the Qualys vulnerability management solution. If the target machine has not been scanned recently, the playbook progresses to the next task.
- Launch Vulnerability Scan: Initiate a new vulnerability scan on a specified set of target hosts. During the scan, Qualys actively checks for security vulnerabilities, misconfigurations, and potential weaknesses in the target hosts.
- Fetch Scan Results: This task allows administrators to access detailed reports, including lists of identified vulnerabilities, their severity levels, and recommended actions for remediation. The scan results provide a clear overview of security issues, allowing organizations to prioritize and address the most critical vulnerabilities.

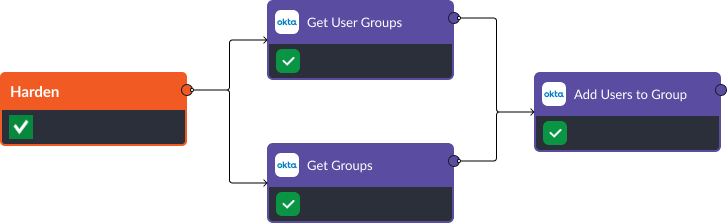
Stage Two: Harden
D3FEND Recommendation: Local File Permissions. If a compromised account has been confirmed, permission restriction is the next stage of the D3FEND framework. An identity and access management tool can be used to view user permissions, available groups, and limit access to files, applications, or devices. In this example we use Okta to execute these tasks.
- Get User Groups: By providing the user’s identifier or username, this task queries Okta’s identity and access management system to return a comprehensive list of groups the user is a member of.
- Get Groups: By executing this task, Okta’s identity platform provides details about each group, such as group names, unique identifiers, and other attributes. This information is valuable for understanding the user’s access rights and privileges.
- Add Users to Group: By providing the group identifier and the corresponding user identifiers, administrators can add the selected users as members of the targeted group. This task simplifies user management by centralizing access assignments and helps maintain a structured approach to access control.
Stage Three: Detect
In stage three, MITRE recommends conducting a detailed file analysis including dynamic, emulated, and file analysis. Many security tools have this capability. For example, CrowdStrike can be used to submit files to a sandbox environment and review the results of the report directly within Smart SOAR. The commands include:
- Submit Files: This task lets users upload suspicious or potentially malicious files to the CrowdStrike Falcon platform for analysis.
- Check Analysis Status: After submitting files for examination, this task queries the CrowdStrike Falcon platform to retrieve real-time updates on the analysis process.
- Get Reports: This task lets users access detailed reports and insights generated by the CrowdStrike Falcon platform. These reports typically include comprehensive information about detected threats, malware behaviors, attack patterns, and affected systems.

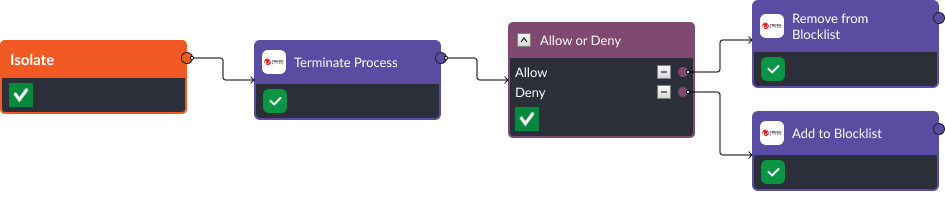
Stage Four: Isolate
D3FEND Recommendation: Executable Allow/Denylisting. If a malicious file is found to be running on a device, then the next action a security team needs to take is to add the process it’s executing to the denylist. Conversely, if the executables are found to be benign, and triggered from a false positive, they can be added to an allowlist to eliminate future false positives.
- Terminate Process: The “Terminate Process” task in Trend Micro Vision One allows security administrators to forcefully end a running process on a system.
- Remove from Blocklist: By removing an item from Trend Micro’s blocklist, administrators can allow its normal and legitimate operation, preventing unnecessary disruptions.
- Add to Blocklist: When suspicious or confirmed malicious entities are encountered, administrators can proactively add them to the blocklist, preventing their execution or access.
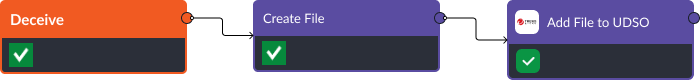
Stage Five: Deceive
D3FEND Recommendation: Decoy File. Playbooks can create new files and add the hashes to an EDR’s watchlist to monitor the file and detect suspicious activity. This is a way for security teams to trick an adversary, monitoring their actions, and ultimately removing them from the network.
- Create File: Users can provide the file’s content, format, and location to generate a custom file.
- Add File to User-Defined Suspicious Objects list (UDSO): The UDSO list in Trend Micro Vision One can be updated via the playbook to specify files, applications, or other entities that need to be monitored for suspicious activity.
Stage Six: Evict
D3FEND Recommendation: File Removal. The final stage of the D3FEND framework is Eviction. For Command and Scripting Interpreter threats, this means removing malicious files from the network. CrowdStrike’s Delete IOCs command is one example of an integration command that can be used to remove the file from affected devices.

Conclusion
MITRE D3FEND is a reliable framework; however, it’s difficult to implement consistently because of its detailed nature. Without an automated workflow, it’s easy for teams to miss crucial steps in the incident response process. By building playbooks inside of Smart SOAR that are directly in line with MITRE D3FEND best practices, security teams can follow the right process, everytime.
Read More: Implementing MITRE D3FEND for ATT&CK Technique T1053: Scheduled Task/Job




