Symantec Enterprise Cloud is a powerful suite of technologies that provide comprehensive detection and response capabilities. The automations inside Smart SOAR let users eliminate repetitive tasks and create a more consistent incident response process across Symantec tools and hundreds more The integrations and commands that are available within Smart SOAR for Symantec Cloud Enterprise are:
Symantec Messaging Group
- Block Domains
- Unblock Domains
Symantec Endpoint Protection
- Block Hashes
- Get Computer IDs
- Quarantine Endpoints
- Start Full Scan
- Unquarantine Endpoints
Symantec Data Loss Prevention
- Fetch Incident
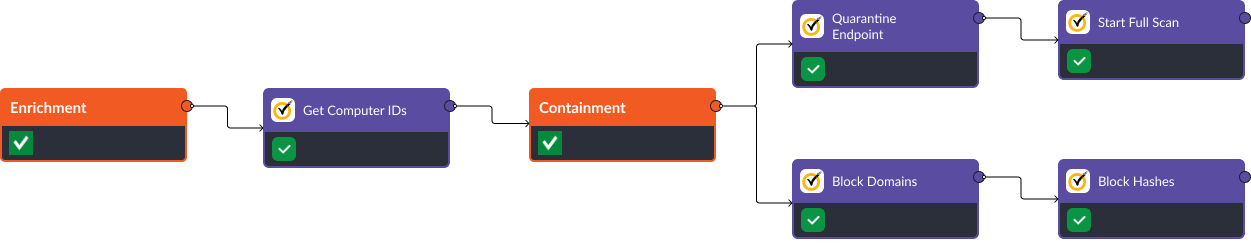
The commands above can be combined into a workflow that covers data ingestion, incident enrichment, containment, and recovery.
The workflow below shows the first two stages of this process. The Get Computer IDs command is used to retrieve all important information about devices involved in a potential breach. The data returned from this command includes network information, such as IP addresses, subnet masks, and DNS servers. It also includes system information, such as processor type, operating system and version, domain, and computer name. The device’s owner is also retrieved, which can be enriched with tools like Okta and Active Directory.
In the containment stage, Quarantine Endpoint, Block Domains, and Block Hashes can be used to prevent damaging activity or access to a compromised device. The Start Full Scan command can be used to scan the affected device and retrieve a list of vulnerabilities. This will help the incident response team prioritize and plan next steps.
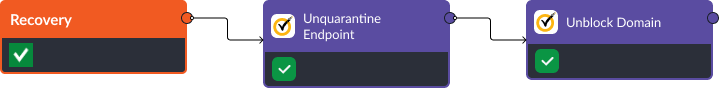
To bring devices back online and re-enable communication to suspicious domains, the Unquarantine Endpoint and Unblock Domain commands re-enable devices and domains that may have been blocked in the previous stage.
Takeaway
The combination of Smart SOAR and Symantec Enterprise Cloud tools gives incident response teams a consistent, automated answer to various threats they’re seeing in their network. The device enrichment and artifact containment commands are applicable in malware, credential compromise, suspicious email, and more advanced threats. These workflows save teams hundreds of hours throughout the week and are easy to set up in an instance of Smart SOAR.




