It’s no use knowing about vulnerabilities in your environment if you don’t have the resources to quickly turn that knowledge into action. It may sound obvious, but vulnerabilities often stay unresolved much longer than they need to, even when the fix is simple. Communicating what needs to be fixed and making sure it happens can take lot of time and effort from busy threat and vulnerability management (TVM) teams.
That’s why we’ve teamed up with ThreatWorx (formerly known as ThreatWatch) to integrate our security orchestration, automation, and response (SOAR) platform with their vulnerability management and third-party risk tool. Our integrated security operations solution solves the problem of turning intelligence into action and minimizing the window of risk.
We’ll be demonstrating the combined power of our software during a joint webinar on April 27, at 10:00 AM PDT. We’re lucky enough to be joined by ThreatWorx CEO Ketan Nilangekar, who will be presenting alongside D3’s Stan Engelbrecht. Even if you can’t make the live webinar, sign up anyway. We’ll send out the recording to everyone who registers.
Use Case: How to Improve Vulnerability Management for Known CVEs, Including Log4j and Print Nightmare
The focus of the webinar will be shortening the vulnerability detection and response lifecycle by using D3 to operationalize ThreatWorx vulnerability alerts and automate the remediation of vulnerabilities to known threats. When a major vulnerability is found and added to the common vulnerability and exposure (CVE) database, a solution is usually not that far behind. Even with a series of issues along the way, there was a successful patch for Log4j within a week. But you still need to know what vulnerabilities impact your organization and how to put those fixes into action.
The detection side is handled by ThreatWorx, which scans its customers’ assets for vulnerabilities and generates alerts. Normally, it would be up to the customer to handle the remediation from here, but customers that also use D3 can ingest those alerts to trigger an automated vulnerability remediation playbook.
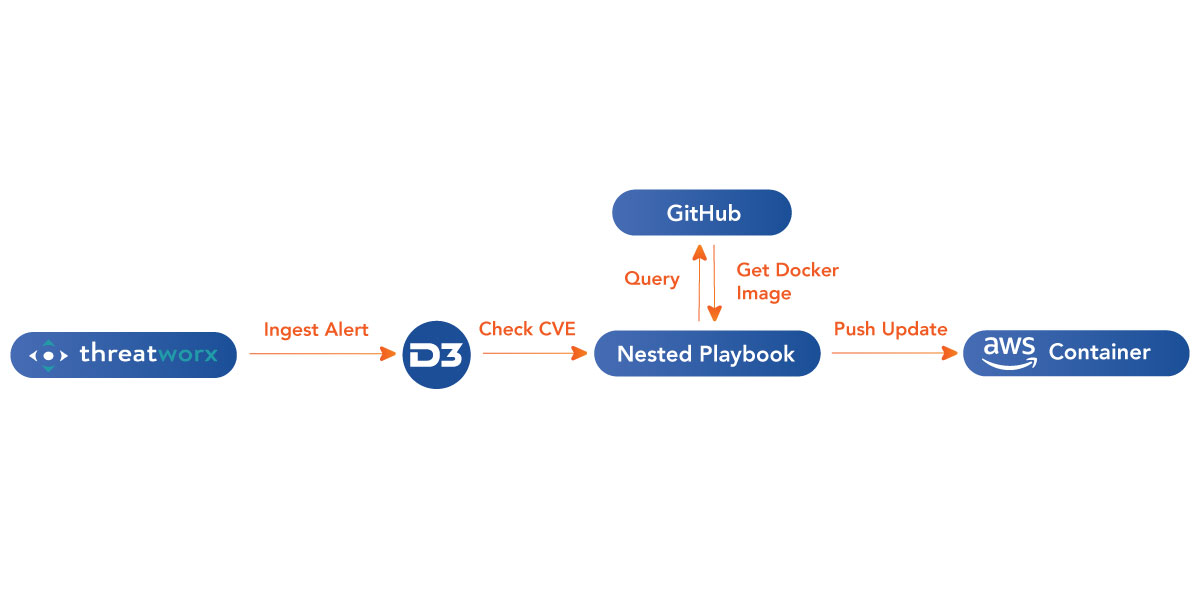
When D3 ingests an alert from ThreatWorx, it cross-references the alert against the CVE database and tags the alert with the relevant CVE number. All CVEs come with a severity score, which security teams can use to set automation rules in D3. For example, a rule could be made to automatically escalate all CVEs with a score of 7.0 or higher to incident status, which would trigger notifications to stakeholders.
D3 comes with out-of-the-box nested playbooks for many important CVEs, so when a vulnerability alert is ingested, D3 knows to orchestrate the remediation. Let’s take the example of Log4j. If ThreatWorx detected a Log4j vulnerability and escalated it to D3, the platform would follow a Log4j playbook that included actions like:
- retrieving the AWS Docker image file from GitHub;
- building the Docker image;
- and pushing the update to the vulnerable AWS container.
The result is an automated patching process that virtually eliminates dwell time.
To take another example, D3 also has a pre-built nested playbook for PrintNightmare. In that playbook, D3 retrieves the asset IPs and endpoint info, disables the print spooler, and installs the necessary Windows update. As you can see, leveraging D3’s hundreds of integrations across the environment, makes orchestrating vulnerability management a fast and easy process for security operations teams.
Use Case: How to Operationalize ThreatWorx Threat Intelligence with D3’s Automated Playbooks
Another use case for ThreatWorx and D3 is turning threat alerts into automated action. This use case won’t be focused on in the webinar, but you can read more about it in our ThreatWorx joint solution guide. Similar to what we described with vulnerabilities, there is a big gap between receiving threat intelligence and consistently putting that information to use. D3 and Threat Worx can automate that process, so you can run threat hunting playbooks across your environment.
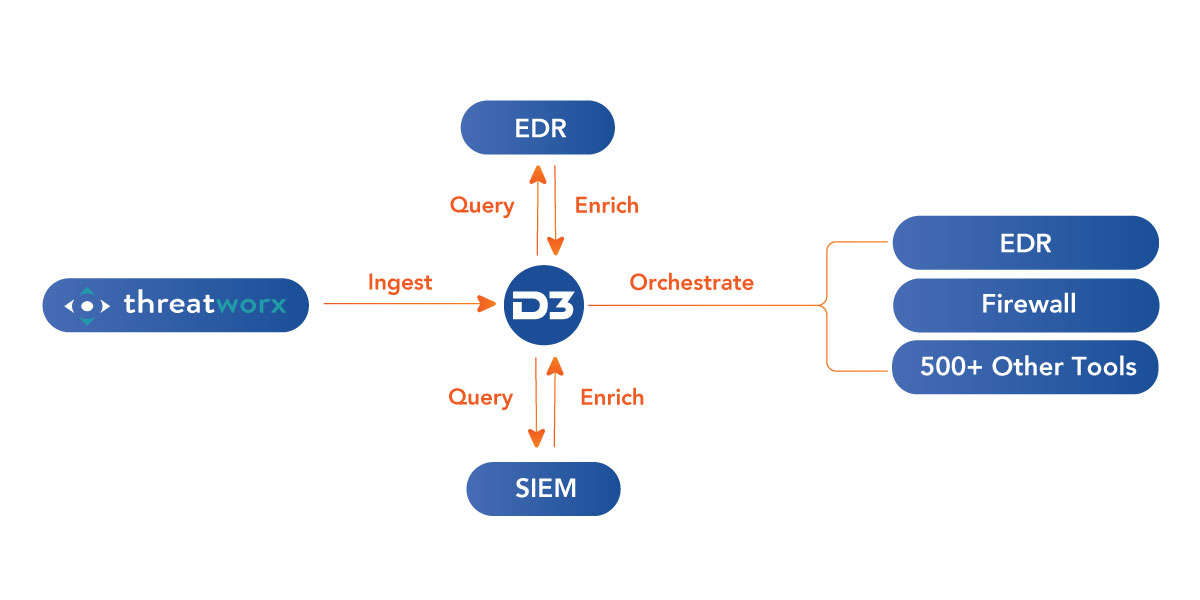
Here’s how it works. ThreatWorx provides detailed intelligence in the form of threat alerts. D3 ingests threat alerts and parses out the IOCs, such as file hashes, URLs, IP addresses, and domains. Then, D3 can hunt for those indicators of compromise (IOCs) in the environment. In the case of a file hash, D3 can query an integrated endpoint detection and response (EDR) tool to find out if the hash is present on any company endpoints. If the hash is found, D3 can orchestrate the EDR tool to quarantine the endpoint, once approval is given by the appropriate person. In the case of IPs and URLs, D3 can add them to the blocklist on any integrated firewalls.
Whether ThreatWorx is your only threat intelligence source, or it’s one of dozens in your security operations center (SOC), having D3 to operationalize threat alerts can be the difference between taking prompt action against threats, and not taking action at all.
Join our Webinar with ThreatWorx on April 27th at 10AM PDT
If any of this sounds like it could help you and your organization, you don’t want to miss our joint webinar with ThreatWorx on April 27th. The speakers will be Ketan Nilangekar and Stan Engelbrecht.
Ketan is the CEO and Co-founder of ThreatWorx, a cyber security platform designed to provide real-time vulnerability and threat assessment, which has now been adopted by a growing set of customers. Prior to founding ThreatWorx, Ketan had stints at Symantec and Veritas Technologies.
Stan is an accredited CISSP and the director of D3 Security’s cybersecurity practice. He works closely with security teams and leadership at global organizations as well as with bespoke Managed Detection and Response (MDR) firms. Outside of his work with D3 Security, Stan speaks about cyber security issues at conferences and universities and is the president of a security special interest group.
Sign up here for the webinar. We’ll be live on April 27th at 10AM PDT / 1PM EDT. And as a reminder, even if you can’t make the live webinar, sign up anyway. We’ll send all registrants the on-demand recording of the webinar as soon as we have it.




