-

How MSPs can Start Delivering Security Services with Automation
Learn how SOAR tools integrate with NinjaOne and CrowdStrike to deliver automated threat response and streamline MSP operations.
-
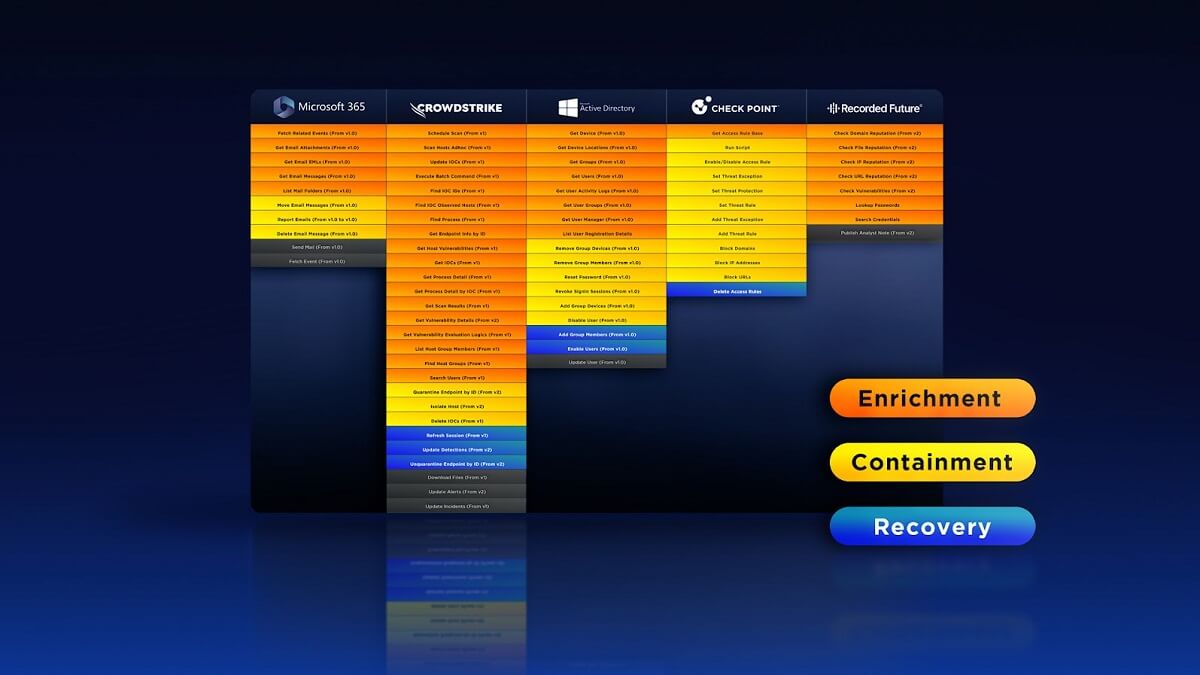
How to Build a Phishing Playbook Part 1: Preparation
Automating response to phishing attacks remains one of the core use-cases of SOAR platforms. In 2022, the Anti-Phishing Working Group (APWG) logged ~4.7 million phishing…
-

Implementing MITRE D3FEND for ATT&CK Technique T1110: Brute Force
When account credentials are unknown, attackers may use a brute force attack in order to gain access. This can occur as an early stage of…
-
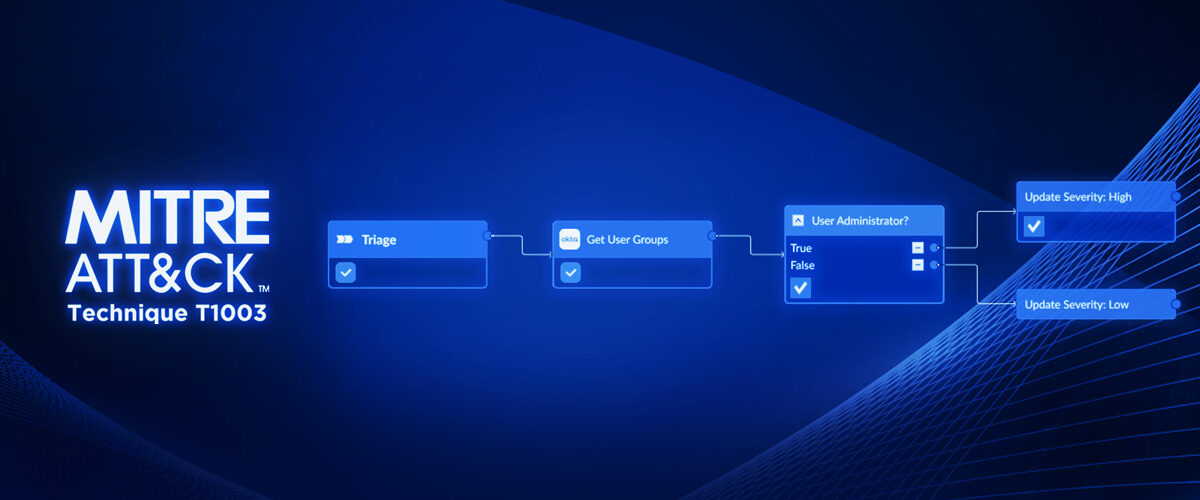
How to Automate Incident Response to MITRE ATT&CK Technique T1003: OS Credential Dumping
In this blog post, we will outline four incident response playbooks for MITRE ATT&CK Technique T1003: OS Credential Dumping. Credential Dumping is a technique that…
-
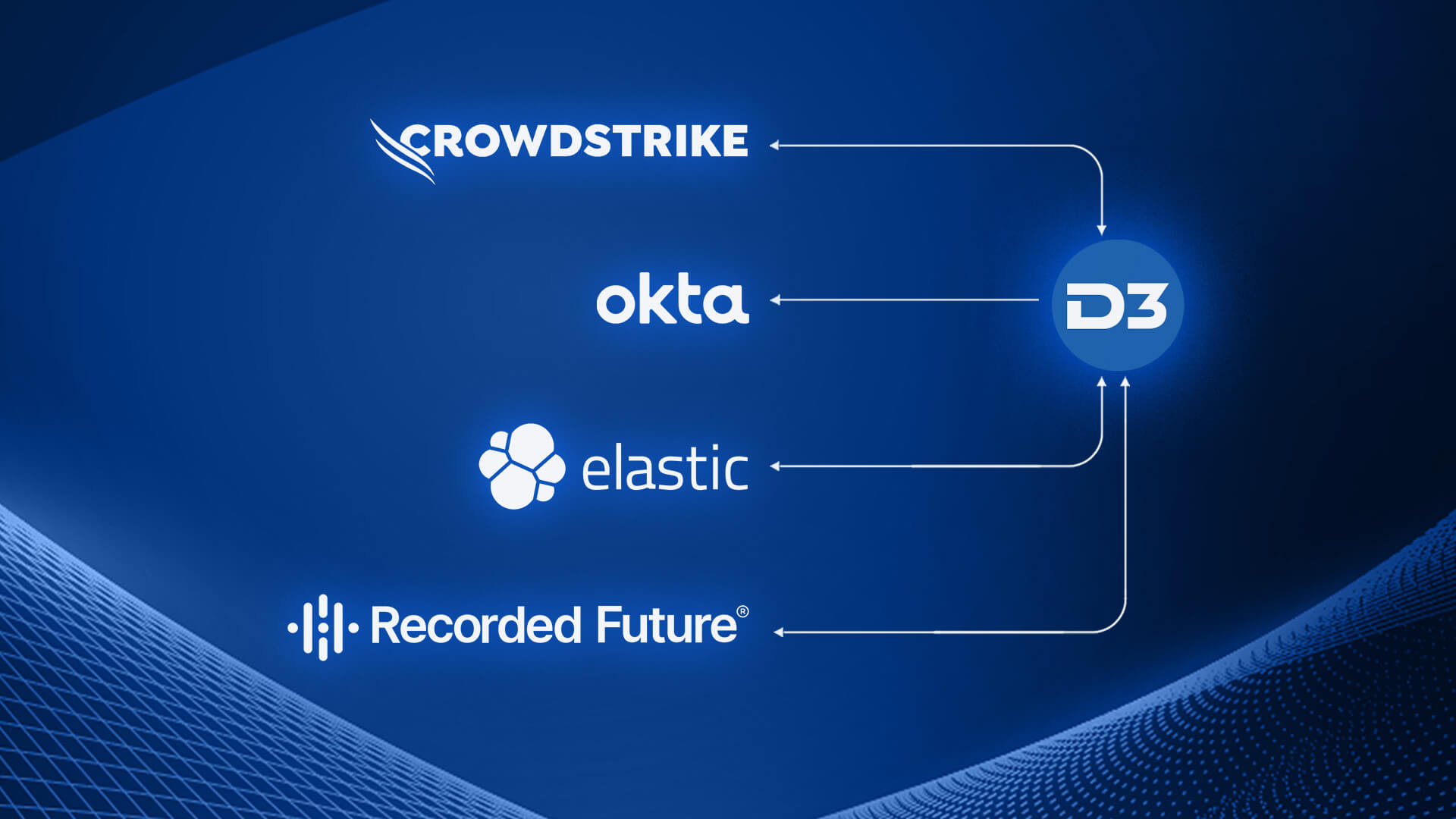
Defending Against Valid Account Threats: A Holistic Workflow with CrowdStrike, Okta, Elastic, and Recorded Future
As organizations seek to bolster their cyber defense strategies, the MITRE ATT&CK framework has emerged as a valuable resource for understanding and categorizing real-world threats.…
-

Automatically Triage and Respond to Mimikatz Alerts with CrowdStrike, Okta, and Smart SOAR
Credential dumping alerts are a sign that a device has been compromised. Your ability to verify this threat, measure the scope of the breach, and…
-
D3’s Smart SOAR is the Best SOAR for CrowdStrike. Here’s Why
As cyber attacks become more sophisticated and frequent, organizations must ensure that they have a robust security system in place. CrowdStrike Falcon and D3 Smart…
-

Playbook Breakdown: Cross-Stack Analysis with CrowdStrike, Zscaler, and Active Directory
In this post, we explore how CrowdStrike, Zscaler, and Active Directory can be used in one playbook to investigate and respond to a remote file…
Crowdstrike
Select a term…
