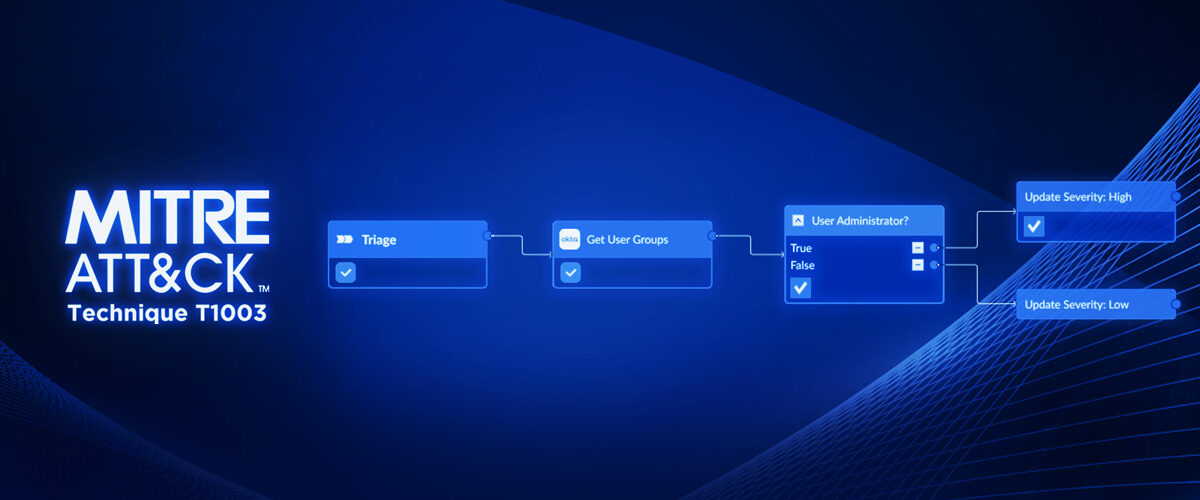
In this blog post, we will outline four incident response playbooks for MITRE ATT&CK Technique T1003: OS Credential Dumping. Credential Dumping is a technique that allows adversaries to steal user authentication materials, such as usernames and passwords, often from system memory. The indicators of compromise associated with this technique include unexpected and extensive read operations on system memory, suspicious processes, and anomalous network traffic patterns. By leveraging automation, security teams can become more strategic with their incident response and rest easy, knowing that there is a consistent process in place to contain and recover from T1003.
Playbook One: CrowdStrike, Palo Alto Next-Generation Firewall (NGFW), and Okta
Triage
In this playbook, we use an event playbook to set a more accurate severity for the incoming alert. For example, if the user involved does not have administrative privileges, their attempt to harvest credentials using lsass will fail. In this case, CrowdStrike EDR has detected a possible credential dumping alert, which has been ingested into Smart SOAR. Then, an event playbook triggers and uses identity data from Okta to categorize the alert as high severity, if the user who executed the command has administrative access to their device.
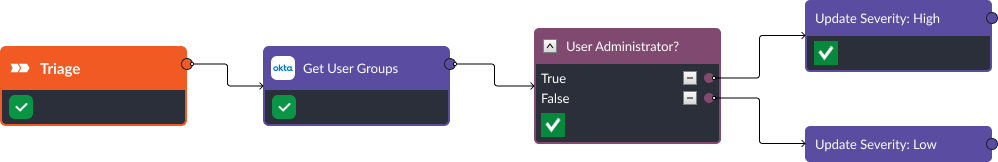
Event playbook checks user permission and sets severity to high if the user is admin.
Incident Response
Enrichment
The incident playbook has three main sections: enrichment, containment, and recovery. In the enrichment phase, Okta, CrowdStrike, and Palo Alto are used to get more details on the user, device, and security rules. This data is parsed and displayed to the analyst or investigator for quick decision-making.

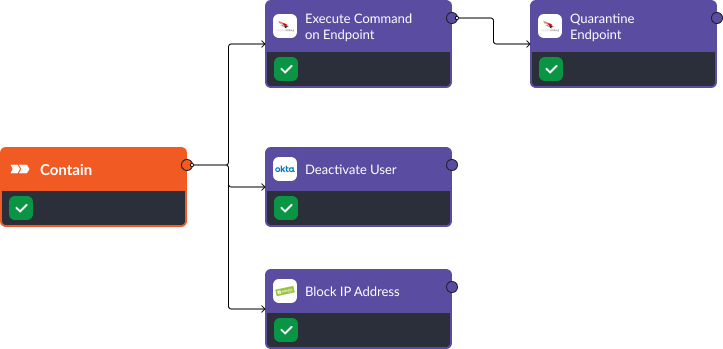
Containment
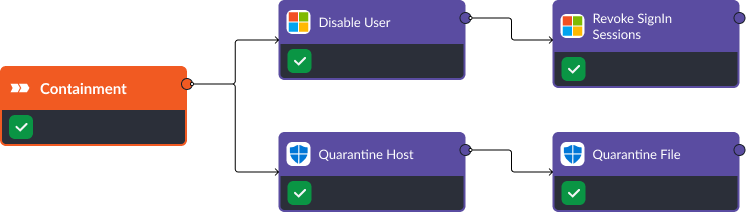
Once the threat has been confirmed, CrowdStrike and Okta are used to deactivate the user and stop the malicious process. At the same time, Palo Alto NGFW can block any communication with a suspicious IP address and the investigator can take things further and quarantine the device. These commands can be triggered automatically or manually.
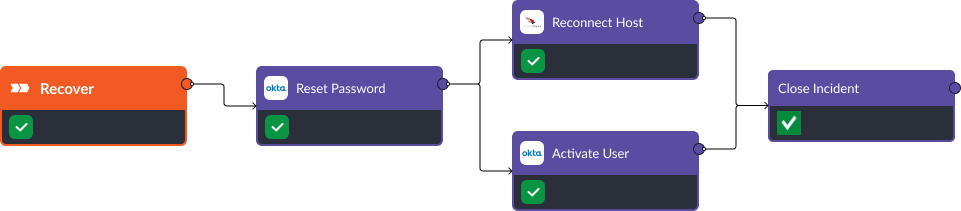
Recovery
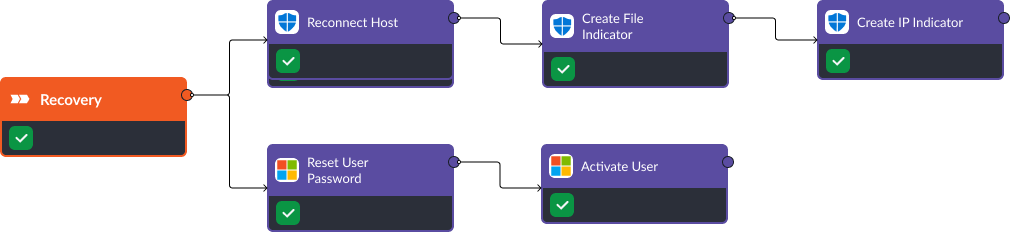
In the recovery stage, the analyst is prompted to reset the affected user’s password. Once this is done, they can reconnect the host back to the network and re-activate the user’s account. Then, the incident is closed and the status of the alert is updated in CrowdStrike.
Playbook Two: Microsoft Defender for Endpoint, Palo Alto NGFW, and Okta
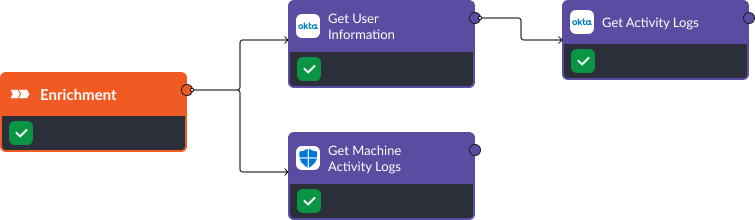
Enrichment
The first stage of this playbook is enrichment. In this stage, Okta and Microsoft Defender for Endpoint are used to consolidate all activity logs on the user and device that are suspected of running the malicious process. These logs can indicate any suspicious outbound connection requests or the execution of common credential dumping commands.
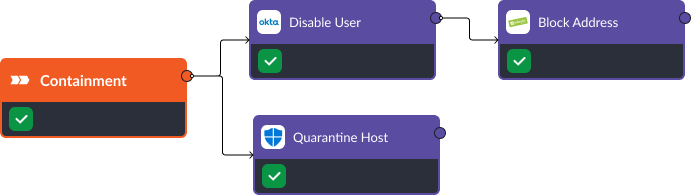
Containment
Once a credential dumping threat has been confirmed, Smart SOAR can automatically disable the user, quarantine the device, and block any suspicious entities, such as destination IPs and local files. This prevents the threat actor from establishing persistence or moving to a later stage attack like lateral movement.
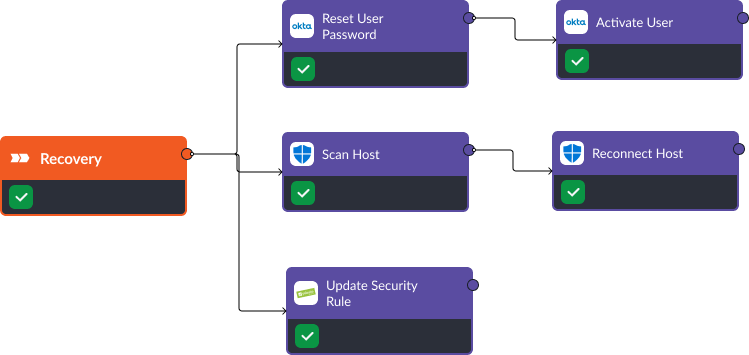
Recovery
In the recovery phase, Okta can reset the compromised user’s account and initiate the same process for all users whose credentials may have been exposed in the attack. Then, the playbook can reactivate the user isolated in the containment phase. Similarly, Defender for Endpoint scans can be triggered and devices brought back onto the network when they are approved. Finally, Palo Alto NGFW security rules can be updated to prevent access to malicious sites or IP addresses that may have been used to gain access in the first place.
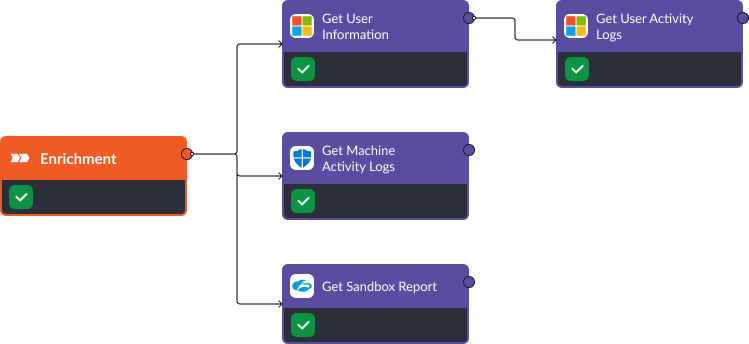
Playbook Three: Microsoft Defender for Endpoint, Zscaler, and Active Directory
Enrichment
Similar to the previous playbook, the first stage in this playbook is enrichment. This is where Smart SOAR consolidates relevant data from systems that were not included in the original alert. For example, user information from Active Directory, such as groups and management chains, and activity logs for the device and user. This data was not included in the original alert from Microsoft Defender for Endpoint, but can be retrieved through playbooks via APIs. The playbook also retrieves a file analysis from Zscaler if a malicious file is suspected of originating the attack.
Containment
Microsoft Defender for Endpoint and Active Directory are perfect for containing an attack. If a user and device are compromised, they can both be taken offline and the user’s application access can be revoked. In the recovery stage, we can take these assets back online after they have been remediated.
Recovery
As quickly as Defender and Active Directory can take assets offline, they can bring them back, granting the user the access they need to continue working. Then, new indicators are created in Defender to help identify threats sooner.
Playbook Four: Trellix (formerly McAfee) EDR, FortiGate NGFW, and Okta
Enrichment
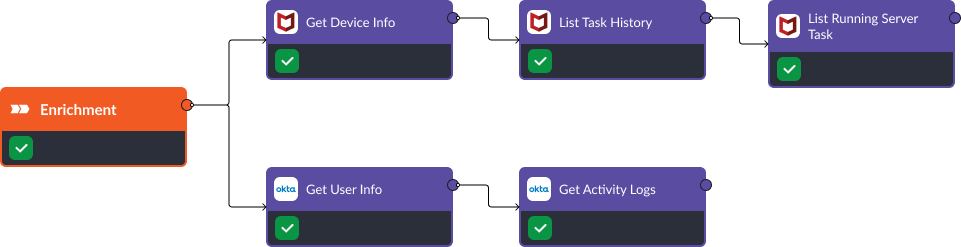
In the first stage of this playbook, we retrieve relevant information on the user and potentially affected device. Trellix’s “Get Device Info”, “List Task History”, and “List Running Server Task” commands help us get a clear picture of what activity has been taken on the device. At the same time, Okta’s “Get User Info”, and “Get Activity Log” commands show us user details.
Containment
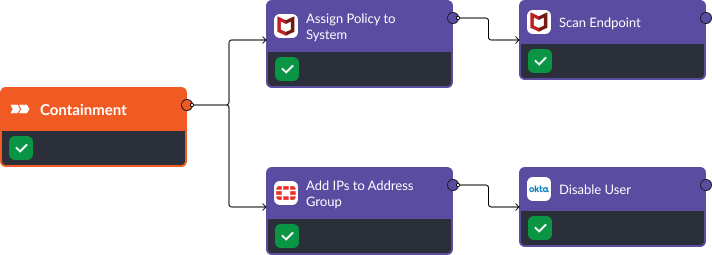
Upon identifying Credential Dumping, we activate the response stage. Using Trellix’s “Assign Policy to System” command, we apply appropriate security policies to affected systems. The “Scan Endpoint” command is used to further investigate the vulnerabilities on the device. FortiGate is used to block suspicious IP addresses and Okta is deployed to disable the compromised user account.
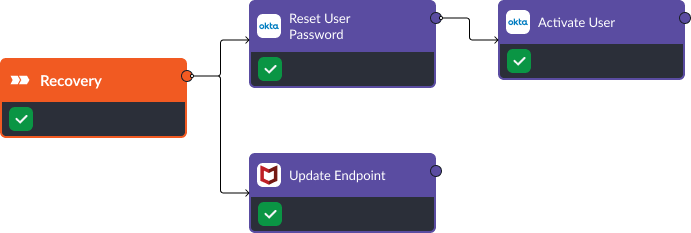
Recovery
During the recovery stage, FortiGate’s “Add IPs to Address Group” command enables us to isolate IP addresses associated with the attack, thereby disrupting the threat actor’s communication channels. Okta’s “Reset User Password” and “Activate User” commands secure potentially compromised accounts and bring disabled users back online.
Takeaway
These four playbooks are examples of how security teams can use Smart SOAR to integrate their standalone security tools into a unified system. This creates an automated, 24/7, consistent approach to incident response.
In this scenario we used Trellix EDR, CrowdStrike, and Microsoft Defender for Endpoint to gather details on affected machines then assist with containment and recovery. We also used Okta and Active Directory to check user permissions and perform account resets if needed. Zscaler and Palo Alto NGFW were used to monitor and block suspicious network traffic. Smart SOAR integrates with hundreds of security tools. Reach out to us if you’re curious about how it can complement your stack.