In this post, we will outline three incident response playbooks for MITRE ATT&CK Technique T1566: Phishing. This technique poses a serious risk due to its ability to take advantage of human error. Phishing remains a time-drain on security teams. Smart SOAR can help operationalize your phishing incident response playbook, automating dozens of tasks per alert, giving teams the freedom to work on more demanding threats.
Understanding MITRE ATT&CK Technique T1566: Phishing
Phishing is a technique where adversaries trick users into revealing sensitive information, such as usernames, passwords, or credit card details, by impersonating a trustworthy entity in digital communications. Indicators of compromise associated with this technique include suspicious email communications, anomalous network traffic, and abnormal user behavior. By detecting these indicators, organizations can proactively mitigate potential attacks.
Read: What Are MITRE ATT&CK and MITRE D3FEND?
Read: How to Build a Phishing Playbook
Playbook One: Office 365, Microsoft Defender for Endpoint, Zscaler, and Okta
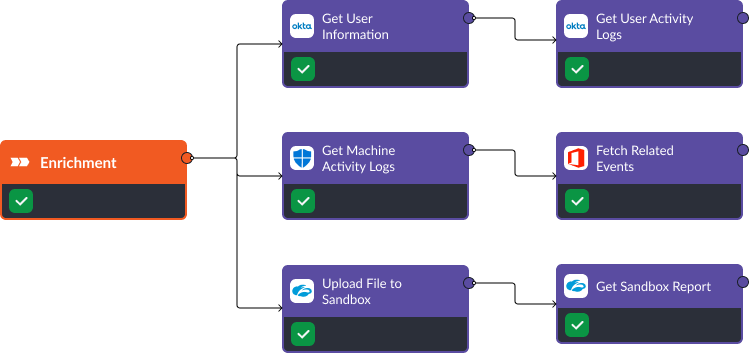
Enrichment
In the enrichment stage, we collect activity logs on the user, and their machine, to identify suspicious activity that indicates that the user’s account or device has been compromised. Additionally, Office 365’s “Fetch Related Events” command can retrieve common emails across the enterprise that may indicate a larger phishing campaign.
At the same time, Zscaler’s API lets us upload files to its sandbox and retrieve the reports automatically, helping users classify the threat as malicious or benign.
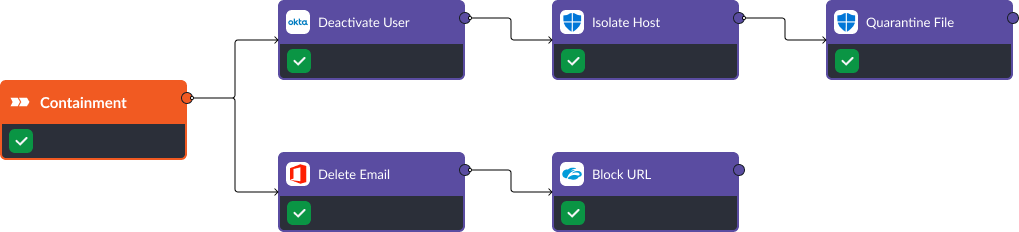
Containment
If the phishing attempt was successful, we can deactivate the user, isolate the host from the network, quarantine the file, and block the email and any URLs associated with the threat. These are comprehensive containment commands that are available out-of-the-box and are capable of stopping an adversary from capitalizing on a compromised account.
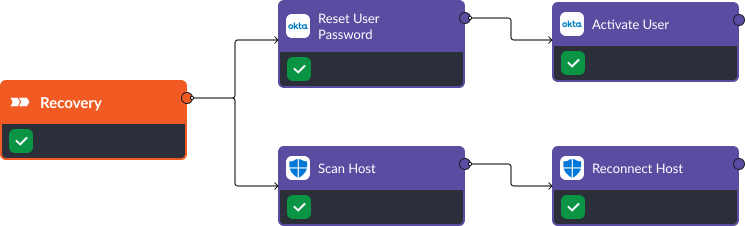
Recovery
Once the threat has been contained, the playbook moves on to the recovery stage. In this stage, the compromised user’s credentials are reset and they are brought back online shortly after. At the same time, a scan is initiated on the affected machine, and if no vulnerabilities are found, it is brought back onto the network.
Playbook Two: CrowdStrike, FortiGate Next-Generation Firewall (NGFW), Active Directory
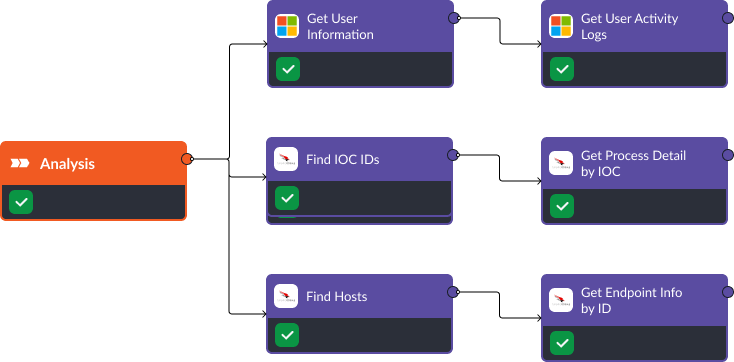
Analysis
Using Active Directory’s “Get User Information” and “Get User Activity Logs” commands, we can identify possible breaches due to phishing. For example, suspicious processes could indicate a successful attack. Utilizing CrowdStrike’s “Find Hosts” and “Find IOC IDs” commands, we can get host details and collect related IOCs. The “Get Process Detail” and “Get Process Detail by IOC” commands allow us to deep-dive into any suspicious processes and flag abnormal activity.
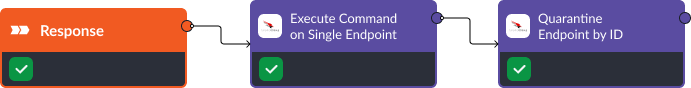
Response
Once we’ve verified a phishing attack, we move to the response phase. At this stage, actions can be both automated and manual, depending on the severity and complexity of the threat. For instance, CrowdStrike’s “Execute Command On Single Endpoint” can be employed to halt any malicious processes automatically, while “Quarantine Endpoint by ID” may require manual approval to avoid unintended isolation of critical systems.
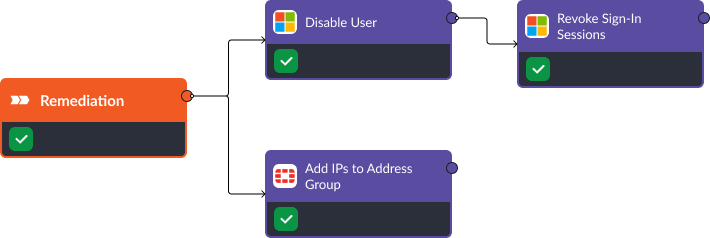
Remediation
The remediation phase will ensure future attacks by this adversary are less likely to succeed. FortiGate’s “Add IPs To Address Group” command allows us to block any malicious IP addresses involved in the attack. Meanwhile, Active Directory aids in securing user accounts. The “Disable User” command temporarily deactivates any compromised accounts, and “Revoke Sign-In Sessions” terminates all active sessions of affected users.
Post-incident, it’s essential to review and strengthen security policies, conduct employee awareness training, and manage software patches to prevent future similar attacks.
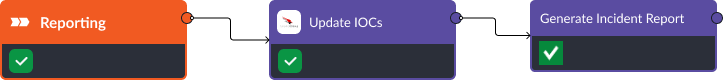
Reporting
Keeping a detailed record of the incident is vital for continuous improvement. When an incident is closed, CrowdStrike’s “Update IOCs” command allows us to document all identified IOCs and the responses taken. Then, Smart SOAR’s “Generate Incident Report” command will compile a list of detailed findings, actions taken, the individuals involved, and suggestions for improvement. This report can be automatically shared with all relevant stakeholders, such as IT, management, and security teams, contributing to better risk management and fostering a culture of cybersecurity awareness.
Playbook Three: Trellix Endpoint Security, Palo Alto NGFW, Office 365, and Okta
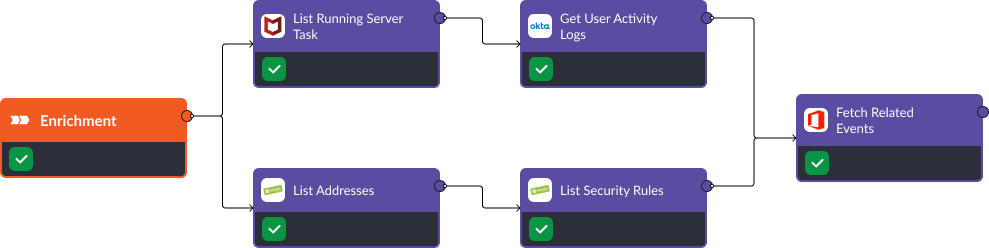
Enrichment
The first stage of this playbook is enrichment. In this stage Trellix and Okta are used to gather activity data from the user and device. Similarly, Palo Alto NGFW’s “List Addresses” and “List Security Rules” helps us understand what network activity is currently allowed. Additionally, Office 365’s “Fetch Related Events” command is used to search for any related phishing attacks that may have been sent to other users.
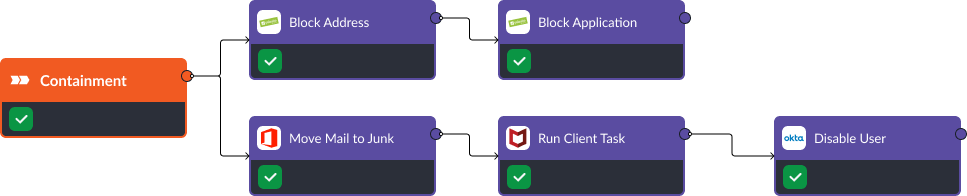
Containment
Upon identifying a phishing attack, Office 365 is used to remove the malicious email while Palo Alto prevents any further communication with a malicious website or IP address. “Run Client Task” is used to terminate any malicious processes active on the device, while “Disable User” ensures a compromised account does not have further access to the network.
Remediation
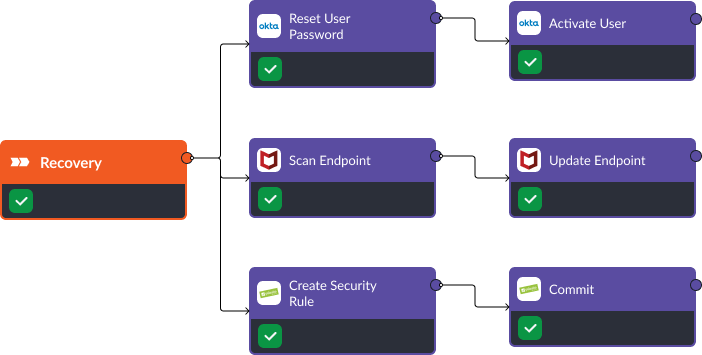
Once the issue has been contained, the user’s password and access can be reset with the Okta integration. At the same time, the device can be scanned and updated to fix any vulnerabilities with Trellix while Palo Alto’s security rules are updated to prevent any other employee from accessing the malicious assets in the future.
Takeaway
Phishing is a common, time-consuming alert. But most organizations use tools that can be called to identify, contain, and recover from these threats automatically. Smart SOAR is the best choice for teams looking to automate incident response across their security tools because it is vendor agnostic with the deepest integration library in the industry. Most SOAR companies offload integration development and testing to their clients, but D3 takes that responsibility in-house, deploying the largest integration team on the market to continuously develop and test integrations with the tools you’re using every day. With Smart SOAR playbooks, you can eliminate blind spots between siloed tools and benefit from automation to make the most out of the tools you’ve already deployed.




