

D3 Security’s Smart SOAR (security orchestration, automation, and response) is a powerful platform designed to unite disparate security tools and streamline incident response workflows. Palo Alto Next Generation FireWall (NGFW) is a leading network security solution that helps organizations protect their networks from various cyber threats. In this article, we’ll explore how integrating the Palo Alto NGFW with Smart SOAR enables use-cases such as automated threat blocking; streamlined security rule and tag management; and efficient address and address group management.
The Benefits of Palo Alto NGFW Integration in Smart SOAR
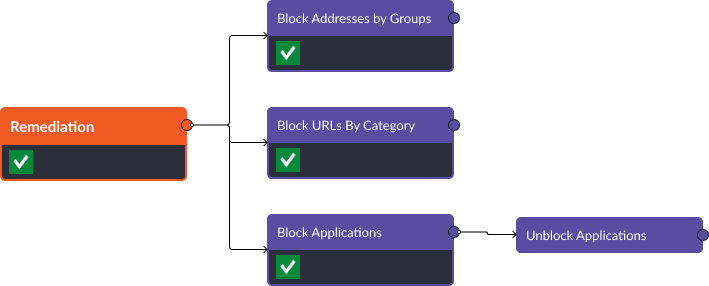
Automated Threat Blocking
Smart SOAR’s integration with Palo Alto NGFW allows security teams to automate threat blocking efficiently. When a threat is detected, Smart SOAR can use the “Block Addresses By Groups,” “Block Applications,” or “Block URLs By Category” commands to automatically block malicious IP addresses, URLs, or applications, protecting your network from potential attacks.
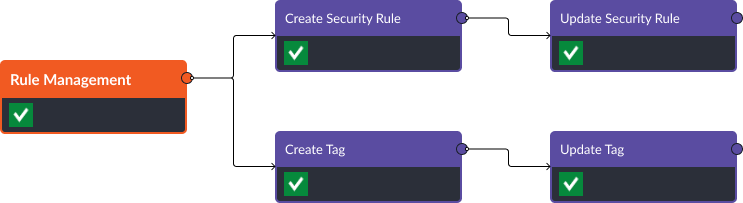
Streamlined Security Rule and Tag Management
Managing security rules and tags in the Palo Alto NGFW can be complex and time-consuming. Smart SOAR’s integration simplifies this process by allowing security teams to create, update, or delete security rules and tags directly from the platform using commands like “Create Security Rule,” “Create Tag,” “Update Security Rule,” and “Update Tags.” This reduces the risk of misconfiguration and helps maintain a consistent security posture across the organization.
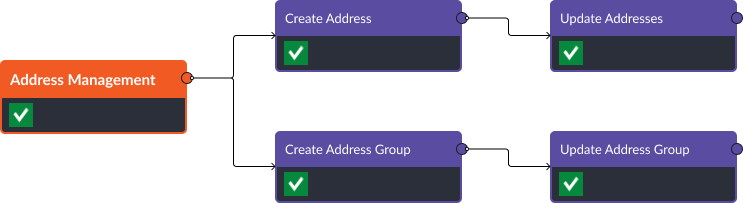
Efficient Address and Address Group Management
With Smart SOAR’s integration, security teams can effectively manage addresses and address groups in the Palo Alto NGFW. Commands like “Create Address,” “Create Address Group,” “Update Addresses,” and “Update Address Groups” enable analysts to add, modify, or delete IP addresses and address groups, streamlining network security management.
Conclusion
Smart SOAR’s integration with Palo Alto NGFW is a powerful way to enhance your organization’s network security, streamline operations, and ensure the consistent application of security policies across all integrated tools. By automating threat blocking, simplifying security rule management, and providing centralized visibility into network activities, organizations can turn siloed tools into a unified ecosystem that works together to minimize the impact of individual security incidents.
