

We recently published a whitepaper detailing D3’s vision for the future of SOAR, and how we’re making it a reality. We’re calling it SOAR 2.0, and while that might sound grandiose, we think it reflects how important this step in the evolution of SOAR could be. You can download the whitepaper here to get all the details, but in this post, I’ll give you a quick overview of the concepts involved.
Moving from Event-Based to Intent-Based Response
D3’s SOAR 2.0 represents the shift from event-based response, where the SOAR platform intakes, analyzes, enriches, and remediates each event separately in a linear fashion, to intent-based response, where events are handled as links in a larger chain of adversarial intent.
This is achieved by integrating with the MITRE ATT&CK framework to place correlated events in the context of the cyber kill chain.
What is the MITRE ATT&CK framework?
The MITRE ATT&CK framework is an expanded version of the cyber kill chain, which outlines the steps that an adversary might take to complete a cyber attack. MITRE, a non-profit organization that has analyzed thousands of cybersecurity incidents, turned the kill chain into the ATT&CK matrix, which comprises 12 ‘tactics’—the steps of the attack—each with numerous associated ‘techniques’—the specific methods an attacker might use to realize the tactic.
SOAR Without the Kill Chain
Without incorporating a kill chain framework like ATT&CK, SOAR is event-based. This model of SOAR can be very effective for quickly responding to attacks by enriching events with contextual data and orchestrating actions across security tools. The shortcoming of event-based SOAR is that it doesn’t give you any understanding of how an event functions as part of a larger attack. So you might catch an attacker in your system trying to escalate the privileges of a compromised user account, but you won’t have a reliable method for finding how they initially gained access, what other tactics they’ve attempted, and what they are likely to do next.
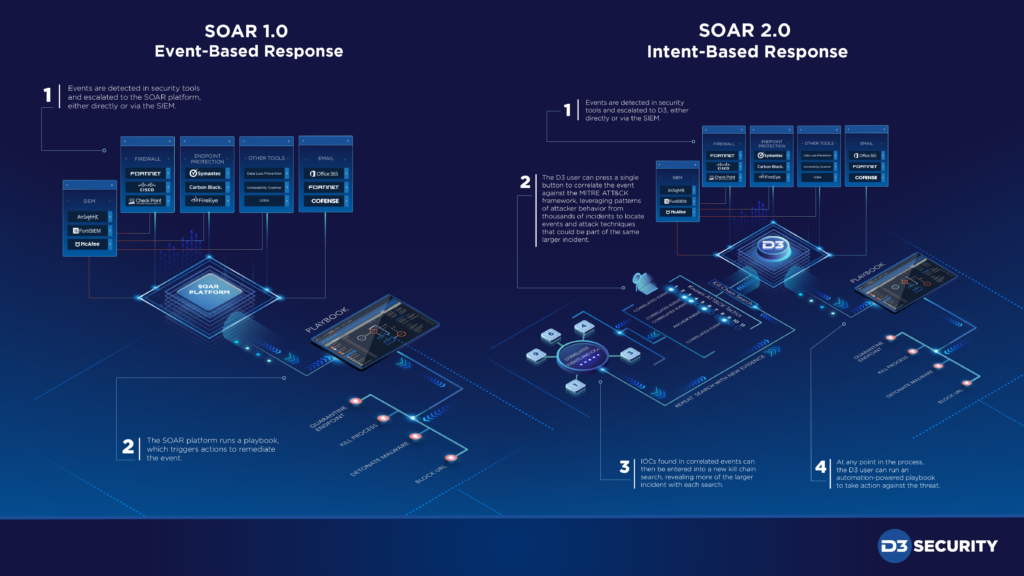
Click the image to expand the diagram and see the differences between event-based and intent-based SOAR.
SOAR With the Kill Chain
In order for SOAR to become intent-based, it needs to leverage the insights of the kill chain framework. This is what D3 has done by integrating ATT&CK. When an event comes into D3, instead of immediately firing off a response playbook, the user can run choose to run a ‘kill chain search’, which identifies correlated events that could be part of the same kill chain, based on the techniques used and extracted IOCs. Using the predictive power of the ATT&CK framework, you can search back across previously overlooked events, and forward to find out if the attacker has already taken additional steps. With each correlated event that you find, you can run the search again with new techniques, IOCs, and evidence, thereby expanding your web of correlations and refining your understanding of the attack. At any point, you can choose to run automation-powered playbooks to act against the threat.
With SOAR 2.0, if you catch one link in the chain, you have an excellent chance at uncovering the entire attack. This is what sets it apart from SOAR 1.0, which relies on the hope that each event will be caught separately by security tools.
Read our whitepaper on SOAR 2.0 for a step-by-step breakdown of how D3’s new methodology works.
