Ever wish you had a crystal ball for cyber threats? Meet MITRE ATT&CK and MITRE D3FEND, your digital fortune-tellers. In a fast-moving threat landscape, staying ahead of your adversaries is crucial. MITRE ATT&CK unveils adversary tactics, giving you the upper hand in fortifying your organization’s defenses. Meanwhile, MITRE D3FEND is all about defense strategies. Join us as we break down these frameworks, explore their real-world applications, and uncover how they can bolster your organization’s security strategy.
What Is MITRE ATT&CK?
MITRE ATT&CK (Adversarial Tactics, Techniques, & Common Knowledge) is a framework developed by the MITRE Corporation for documenting common behaviors exhibited by cyber attackers, or adversaries, in real-world security incidents.
Who Is MITRE?
MITRE is a not-for-profit organization that supports American governments at the federal, state,
and local level and also works with academia and various industries. MITRE works in many domains, with a focus on technology.
The name MITRE looks like an acronym, but it actually isn’t. The name dates back to 1958, when, as the story goes, it was chosen by a board member because it had a nice feel, without having an existing meaning.
The History of MITRE ATT&CK and D3FEND
ATT&CK was created in 2013 as part of a MITRE research project about post-compromise detection in enterprise networks. The researchers found that they needed a framework for documenting adversary tactics, techniques, and procedures (TTPs) that:
- Drew from real-world incidents
- Went beyond conventional indicators of compromise (IOCs)
- Was more actionable than existing kill chain and life cycle models
ATT&CK was developed for MITRE’s internal use but proved so useful that the company decided to release it publicly in 2015. Since then, ATT&CK has expanded significantly, with regular updates to encompass a broader range of TTPs. It has gained widespread adoption across industries, becoming a standard reference for threat intelligence, detection, and incident response. The framework’s success led to the creation of the ATT&CK Evaluations program, which evaluates security products’ capabilities against real-world attack scenarios.
Recent years have also seen the introduction of the specialized matrices ATT&CK for Mobile and ATT&CK for ICS. Additionally, ATT&CK has expanded to include Detections, providing a practical guide for creating detection rules and enhancing security monitoring, as well as Software and Groups, which offer in-depth analysis of adversary tools and threat actor behavior, empowering organizations to better understand and counter cyber threats across a wide range of domains. In the spring of 2021, MITRE introduced D3FEND, a complementary framework that focused on defensive techniques.
What Are the Different ATT&CK Frameworks?
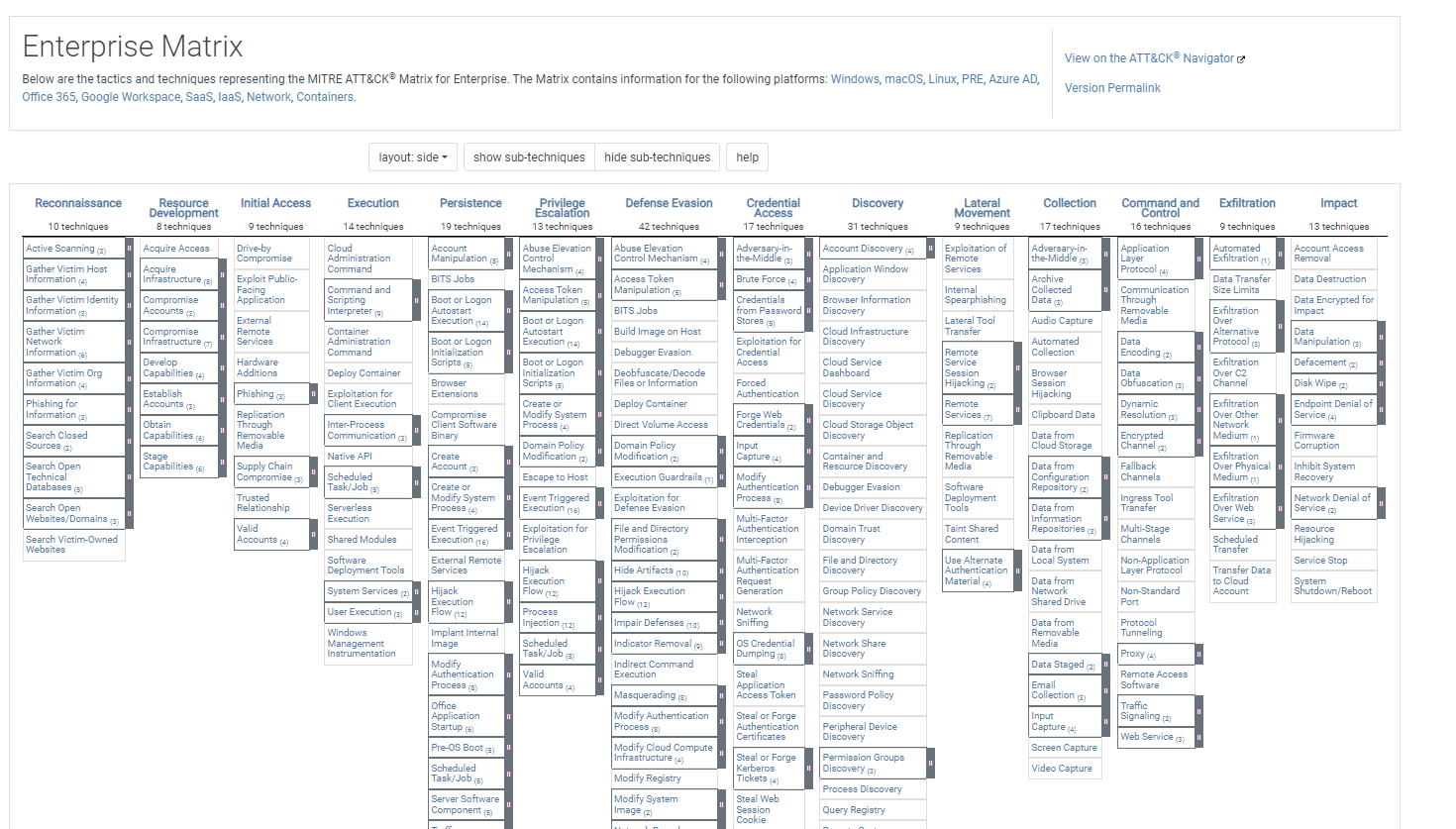
MITRE ATT&CK for Enterprise
The enterprise matrix is the original matrix, and is what people are generally referring to when they talk about MITRE ATT&CK. The enterprise matrix can be separated out into the PRE Matrix, which covers preparatory techniques, as well as matrices based on operating systems—e.g. Windows or Linux—or technologies—e.g. cloud or containers.
MITRE ATT&CK for Mobile
There are two matrices for mobile, one for iOS and one for Android. They provide a comprehensive framework for understanding and countering cyber threats directed specifically at mobile devices and operating systems. These matrices delve into techniques like app installation abuse and device discovery, which are unique to the mobile ecosystem.
MITRE ATT&CK for ICS
The MITRE ATT&CK Matrix for Industrial Control Systems (ICS) focuses on cyberattack techniques uniquely relevant to critical infrastructure, such as manipulating process control systems, compromising industrial protocols, and exploiting hardware vulnerabilities. This specialized matrix assists in recognizing, analyzing, and thwarting threats targeting the operational technology layer, safeguarding vital industrial processes and systems from cyber risks.
How Many Tactics and Techniques Are in MITRE ATT&CK?
ATT&CK Tactics
The current ATT&CK Matrix for Enterprise has 14 tactics. These tactics represent what an adversary is trying to accomplish at that stage of an incident. The order of the 14 tactics reflects the path adversaries may follow in pursuit of their goals. This makes ATT&CK a variation on the “cyber kill chain” model. Lockheed Martin created the cyber kill chain model to define the sequence of a typical attack. Understanding the sequence gives security teams a better chance to anticipate an attacker’s next step and disrupt it, thereby breaking the “chain.”
The 14 tactics in MITRE ATT&CK are:
- Reconnaissance. Adversaries gather information about target systems, networks, and entities to identify potential weaknesses and plan subsequent attacks.
- Resource Development. Adversaries create or acquire tools and infrastructure required for their operations, such as malware, credentials, and malicious websites.
- Initial Access. Adversaries try to gain an initial foothold into a system, network, or device.
- Execution. Adversaries run malicious code to achieve their objectives.
- Persistence. Adversaries establish mechanisms to maintain access even after system reboots or interruptions.
- Privilege Escalation. Adversaries exploit vulnerabilities to obtain higher levels of access and control.
- Defense Evasion. Adversaries employ techniques to bypass or hinder security measures.
- Credential Access. Adversaries steal, collect, or crack passwords and tokens to gain unauthorized access.
- Discovery. Adversaries gather information about the target environment to plan their attacks.
- Lateral Movement. Adversaries move within a network to expand their influence.
- Collection. Adversaries gather data from various sources for exploitation.
- Command and Control. Adversaries establish communication channels to remotely manage compromised systems and execute malicious commands.
- Exfiltration. Adversaries steal and transfer sensitive information to an external location.
- Impact. Adversaries disrupt or damage systems, data, or operations.
ATT&CK Techniques
There are 193 techniques that represent the specific behaviors an adversary may use to try to achieve the goal of the associated tactic. Many techniques are associated with more than one tactic. For example, Access Token Manipulation may be used by an adversary to achieve either the tactic of Privilege Escalation or Defense Evasion.
In 2020, MITRE added sub-techniques for an additional layer of specificity. There are currently 401 sub-techniques.
What Does MITRE ATT&CK Include Other than Tactics and Techniques?
MITRE ATT&CK includes a great deal of detail on technique pages, as well as separate information that is relevant to adversary behavior and methods for counteracting it.
Platforms
Platforms are the operating systems and applications in which a specific technique could occur. The enterprise matrix can be broken down by platform, and platforms are listed on the detail page for each technique.
Mitigations
Mitigations are defenses organizations can adopt to counteract adversarial techniques, such as patching vulnerabilities or deploying detection systems. By integrating ATT&CK’s recommended mitigations, organizations bolster security, reduce attack surfaces, and mitigate cyber threats.
Detections
Detections are the ways that security teams can identify ATT&CK techniques in their environments, enabling rapid response. Detections include the data sources and data components needed to identify a technique. For example, one of the detections for T1189, Drive-by Compromise, requires the data source network traffic, with the components network connection creation and network traffic content.
Groups
More than 100 groups are classified by MITRE based on their techniques, targets, and motivations. Each group has a unique profile of tactics, techniques, and procedures, enabling organizations to anticipate and counter specific adversary behaviors.
Campaigns
Campaigns are groups of related activity attributed to a single threat actor or group with a single goal, for example, the Solarwinds Compromise of late 2020. MITRE has mapped the known techniques used in these campaigns to the ATT&CK Matrix, so security teams can visualize the controls they need in place to prevent similar attacks.
Software
Software refers to the tools, malware, and utilities employed by threat actors to execute their tactics. ATT&CK outlines software usage to enhance understanding of adversary techniques and facilitate proactive defense measures.
What Are the Most Common ATT&CK Techniques?
The MITRE Engenuity Center for Threat Informed Defense, a non-profit research and development organization operated by MITRE, published a report in 2021 called Sightings Ecosystem: A Data-Driven Analysis of ATT&CK in the Wild. The report looked at more than six million sightings of techniques in the real world from 2019-2021.
15 techniques made up 90% of the observed techniques, providing an invaluable list of priorities for security teams with limited resources.Those techniques, in order, were:
- Scheduled Task/Job (T1053) – 24.1%
- Command and Scripting Interpreter (T1059) – 15.8%
- Hijack Execution Flow (T1574) – 12.6%
- Proxy (T1090) – 8%
- Non-Application Layer Protocol (T1095) – 7.8%
- Masquerading (T1036) – 4%
- Signed Binary/Proxy Execution (T1218) – 4%
- Create or Modify System Process (T1543) – 3.6%
- Process Injection (T1055) – 1.7%
- Impair Defenses (T1562) – 1.7%
- Obfuscated Files or Information (T1027) – 1.4%
- Windows Management Instrumentation (T1047) – 1.4%
- Remote Services (T1021) – 1.3%
- Modify Registry (T1112) – 1.3%
- Ingress Tool Transfer (T1105) – 0.9%
What Is MITRE D3FEND?
MITRE D3FEND is an ongoing project by MITRE Corporation, the same organization responsible for MITRE ATT&CK. D3FEND is designed to complement ATT&CK by focusing on defensive techniques and strategies, whereas ATT&CK primarily focuses on describing offensive techniques used by adversaries. It includes guidance on how organizations can defend against known attack techniques described in MITRE ATT&CK.
What Does D3FEND Stand For?
According to MITRE, D3FEND stands for Detection, Denial, and Disruption Framework Empowering Network Defense.
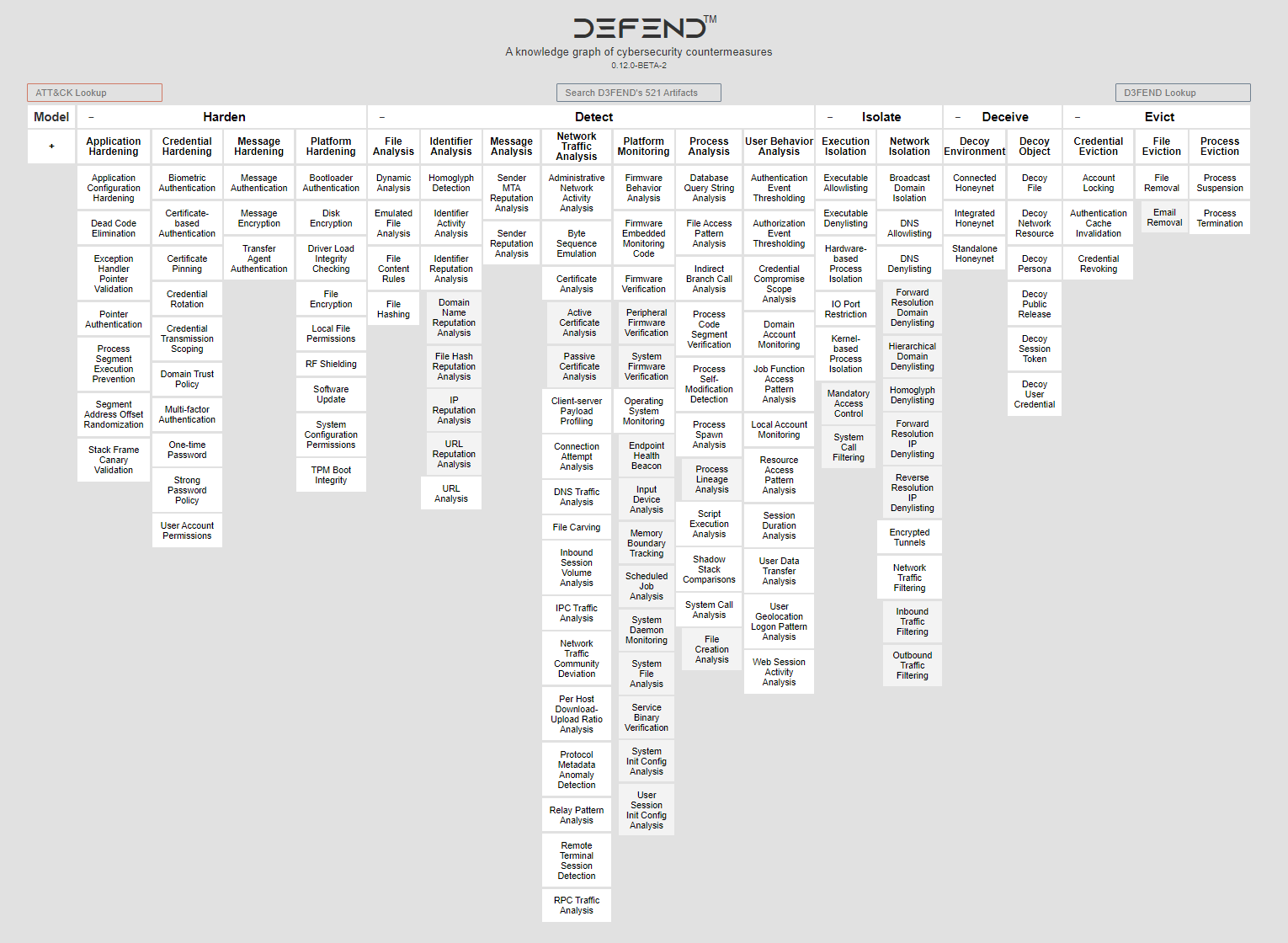
What Are the Stages of MITRE D3FEND?
The D3FEND Matrix is laid out in six stages, or tactics:
- Model
- Harden
- Detect
- Isolate
- Deceive
- Evict
The Model tactic includes techniques for applying analysis to an organization’s systems in order to build a complete understanding of the systems.
The Harden tactic comprises techniques for implementing defensive measures to strengthen a system’s security posture, reduce vulnerabilities, minimize the attack surface, and make the system more resistant to attacks.
The Detect tactic contains techniques aimed at identifying and promptly recognizing suspicious or malicious activities within an organization’s network or systems.
The Isolate tactic involves techniques for containing, segregating, or isolating compromised systems, devices, or network segments to prevent the spread of a cyberattack and limit potential damage.
The Deceive tactic involves applying techniques and technologies to mislead or confuse adversaries and deter them from conducting successful cyberattacks. This tactic creates a hostile and uncertain environment for attackers, making it more challenging for them to identify genuine assets, data, or vulnerabilities.
The Evict tactic includes techniques for forcefully removing unauthorized or malicious entities from a network, system, or environment once they have been detected.
How Is ATT&CK Used in Security Operations?
Where to Begin with MITRE ATT&CK
Many organizations say they want to “implement MITRE ATT&CK”, but what does that mean exactly? It can be overwhelming to put this invaluable knowledgebase to work in your security operations. Here are some use-cases to start with.
Assessing Coverage
One of the first things you can do to put ATT&CK into action is assess which ATT&CK techniques your current security tools and processes cover. Mapping your coverage across the entire ATT&CK matrix all at once is going to be out of scope for most organizations, so begin by assessing your coverage of one technique at a time, starting with the most important.
The ATT&CK website lists data sources and detection information for each technique, which you can use to assess coverage. Take the technique you’ve decided to start with, and check the listed data sources. If the sources are in place, move on to detection. Compare what’s listed in ATT&CK to the analytics you have, such as active rules in your security information and event management (SIEM) or endpoint detection and response (EDR) tool.
For example, sophisticated adversaries who are “living off the land” within a compromised environment may use the Windows Task Scheduler or utilities like schtasks to run malicious programs to maintain persistence. An organization that wanted to know if it was properly monitoring for such behavior could look up the Scheduled Task technique (classified as technique T1053 in the ATT&CK matrix). ATT&CK’s list of data sources needed to detect this technique includes Windows event logs, file monitoring, process monitoring, and process command-line parameter monitoring. With some luck, you’re already monitoring these data
sources and have detections in place, even if you weren’t classifying the behavior as an ATT&CK technique. If you haven’t been monitoring the data sources, you now know this gap should be closed. If you have the data sources, but not the detections, create a new analytic or leverage an existing open-source analytic.
Mapping Coverage
By assessing more techniques, you can begin to build a map of coverage. To broaden your understanding of your coverage, start by taking an inventory of your data sources. Some data sources, such as File Monitoring, Process Monitoring, and Process Command Line, are especially valuable because they’re involved in the detection of many different techniques. As you progress with your assessments, you can track the results of your assessments in the ATT&CK Navigator, a web app from MITRE, available for free on GitHub. You can manipulate the ATT&CK matrix to create heat maps, add notes, and more. Find ATT&CK Navigator at https://mitre-attack.github.io/attack-navigator/enterprise.
Evaluating Tools
ATT&CK is also a useful framework for evaluating new tools. If a tool doesn’t help you close gaps and cover relevant techniques, it isn’t worth your money. For example, imagine a company in the oil and gas industry that’s weighing investments in various security tools. Say the company has facilities and operations in the Middle East. A review of the ATT&CK framework identifies groups like MuddyWater (classified as group G0069 in ATT&CK) as well as the Iranian APT 33 (G0064) groups as active in that region with a history of targeting oil and gas companies.
The techniques used by those groups includes phishing emails with malicious Microsoft Word documents or HTML applications (T1204); the use of PowerShell for execution of malicious payloads (T1086); and the harvesting of credentials from web browser caches and files using tools like LaZagne and MimiKatz (T1003). However, neither group is associated with dedicated denial of service (DDoS) attacks.
Based on this analysis, DDoS protection isn’t the highest priority. Web application firewall capabilities could address some attack vectors but aren’t suited to groups that favor malicious email payloads. The most relevant tools are UBA technology to detect malicious activity on compromised endpoints or threat intelligence services that alert you to the activities of known advanced persistent threat (APT) groups.
Modeling Threats
On the ATT&CK website, APT groups are cataloged with the industries they’re known to have targeted. You can look up the major threats to your industry and see which techniques those APT groups use most frequently. For example, a quick search in ATT&CK for the APT group known as “Carbanak” or “Anunak” reveals that it relies heavily on Remote Access Tools (T1219) like AmmyAdmin and Team Viewer to conduct remote command and control of infected systems.
By using Navigator, you then map the techniques onto the ATT&CK Matrix. If you’ve already done analysis of what techniques you have coverage for, map your coverage as a layer to compare against the threats posed by APT groups. This action immediately highlights high-risk gaps and vulnerabilities in your detection and response capabilities.
How to Use the MITRE ATT&CK Navigator
The ATT&CK Navigator is a freely available tool developed by MITRE that serves as an interactive and customizable interface for the MITRE ATT&CK framework. Security teams can use Navigator for:
- Visualizing ATT&CK Data: Navigator provides a visual representation of the ATT&CK matrix, which users can customize to focus on specific tactics or techniques relevant to their organization, industry, or threat landscape.
- Mapping and Tracking: Navigator enables users to map known adversary behaviors and incidents to specific techniques within the matrix. This helps in understanding the techniques employed by adversaries and tracking them over time.
- Strategic Planning: Security teams can use Navigator to strategize and plan their cybersecurity defenses by aligning their defenses and detection capabilities with known adversary tactics.
- Incident Response: During security incidents, the ATT&CK Navigator can be used to track and visualize adversary tactics and techniques as they are discovered, aiding in response and mitigation efforts.
- Threat Intelligence Integration: Users can incorporate threat intelligence data into Navigator to stay informed about the latest adversary behaviors and tactics.
- Reporting and Documentation: Navigator can be used to generate reports and visualizations, making it easier to communicate findings, recommendations, and cybersecurity strategies to stakeholders and management.
How to Increase MITRE ATT&CK Coverage
The end goal of leveraging MITRE ATT&CK is to improve your organization’s defenses against known adversary techniques. Here are a few ways that organizations can use ATT&CK information to improve their coverage of TTPs.
Developing Analytics
Analytics, in this context, are search queries that can be run from a tool (generally a SIEM) across collected log and event data to detect the behaviors associated with an ATT&CK technique. If, like most security teams, you don’t have the detailed understanding of ATT&CK techniques required to write detection analytics from scratch, you can leverage existing ATT&CK analytics, including those created by MITRE. These open-source analytics provide pseudocode that can be run in a SIEM as a search query. If the code doesn’t match the SIEM your organization uses, tools, such as Sigma, can translate the query for different platforms. After you’re running analytics and receiving results in your SIEM, analyze the results for false positives and make changes to filter them out. When an analytic works properly, you can use it to trigger an alert in your SIEM or SOAR platform.
Mitigations
Just as every technique in the matrix contains data source and detection information, it also has mitigations, which may be policies, tools, or security controls, such as Multi-Factor Authentication (classified as mitigation M1032 in ATT&CK), Network Segmentation (M1030), and SSL/TLS Inspection (M1020). To check where you have this level of coverage, look up mitigations on the ATT&CK page for each technique, or start by looking up a mitigation you know you have in place and see all the techniques it can be used against.
Testing Coverage
Test your defenses with adversary emulation, an exercise where a red team replicates the behaviors of a known adversary. One simple way to start, even if you don’t have a red team, is to use a collection of existing open-source scripts, such as Atomic Red Team, that replicate ATT&CK techniques. This approach may look like this:
- Pick an APT group, list its known techniques, and compare those techniques to your map of existing detections or mitigations.
- Run an Atomic Red Team script for each adversary technique, and compare what your security tools detect and mitigate to what you expected based on your coverage assessments.
Correlating Events with ATT&CK
A lot of security vendors are working the ATT&CK framework into their products. For example, some EDR tools will tag events with ATT&CK techniques when they match MITRE’s criteria. Some of these tools provide a map of the techniques that they can capture, saving you from having to assess your coverage of those techniques manually.
How to Use D3FEND in Security Operations
Where to Begin with MITRE D3FEND
Because D3FEND is much newer than ATT&CK, most security teams have still yet to meaningfully operationalize it. Here are a few ways to get started.
Visualize Your Coverage
The D3FEND matrix makes it possible to visualize your current ability to execute defensive measures. This will reveal the gaps in your security, for example, an overemphasis on the later stages at the expense of the Model and Harden tactics. Visualizing coverage can also be a useful way to evaluate the impact of new tools. If a tool won’t help you cover more techniques, it might not be the right investment.
Set Benchmarks for Improvement
Every security team wants to improve their posture over time and D3FEND gives them a way to quantify improvements and set benchmarks. This is also a valuable way for MSSPs to demonstrate improvements to their clients.
Using D3FEND Best Practices in Playbooks
MITRE’s recommendations can be used as the basis for effective detection and response playbooks in tools like AI SOCs, SOAR and XDR. By focusing on the most common ATT&CK techniques, you can ensure that you are properly defending against likely threats.
For example, here’s how a D3FEND-based playbook looks in D3’s Smart SOAR platform. This playbook is for ATT&CK Technique T1053, Scheduled Task/Job, which was the most frequently observed technique in a 2021 study by MITRE Engenuity: Implementing MITRE D3FEND for ATT&CK Technique T1053: Scheduled Task/Job.
How are ATT&CK and D3FEND Used Together?
ATT&CK and D3FEND are complementary frameworks that can be thought of as two sides of the same coin: what adversaries do and what security teams do. D3FEND techniques are tied to ATT&CK techniques, so for example, you can look up an ATT&CK technique from within the D3FEND matrix to see what defensive measures can be applied to it.
As previously covered, you can use ATT&CK to determine the most important TTPs to your organization. This can be achieved by using MITRE’s modeling of relevant APT groups, MITRE Engenuity’s study of TTP frequency, or, if you have the ability, by creating trend reports based on TTPs detected in your environment. Based on that information, you can create defensive plans and incident response playbooks for those techniques, following D3FEND best practices.
How Morpheus AI Operationalizes ATT&CK and D3FEND
Morpheus AI transforms MITRE’s frameworks into real-time operations. Where traditional SOAR platforms require manual playbook engineering, Morpheus automatically correlates alerts, validates threat indicators, and applies D3FEND defensive practices across your entire stack.
Correlation and Validation
When endpoint detection and response (EDR) tools tag alerts with suspected ATT&CK techniques, Morpheus validates those tags instantly. It gathers data from your SIEM, network tools, and cloud platforms to confirm or challenge the initial classification. This cross-stack validation eliminates false positives that waste analyst time.
Morpheus incorporates ATT&CK techniques into its triage analysis, applies dynamic risk scores, and links related alerts automatically. You see the kill chain unfold as it happens. If your environment shows gaps in the attack sequence, Morpheus flags them so you can hunt for missing links.
Threat Hunting
Morpheus tracks ATT&CK techniques in your environment in real time, then targets threat hunting investigations automatically. Rather than running searches across each tool individually, Morpheus executes MITRE’s recommended detections simultaneously across all integrated systems.
The platform visualizes which techniques appear most frequently in your environment. Based on that data, Morpheus launches hunts for related behaviors and closes security gaps before they become incidents. You can also flag high-risk techniques for immediate escalation whenever they appear.
Incident Response Playbooks
Morpheus generates incident response playbooks based on D3FEND best practices for all six defensive stages. It creates playbooks for the most common ATT&CK techniques—Scheduled Task/Job, OS Credential Dumping, and others—automatically tailored to your specific tech stack.
Each playbook incorporates MITRE’s detections, mitigations, and recommendations. When an incident occurs, Morpheus doesn’t wait for human input. It executes the appropriate playbook, documents every step in transparent YAML, and presents findings to your team for final approval or refinement.
MITRE ATT&CK and D3FEND Resources
eBooks:
Webinars:
Resources:
Blogs:
- Implementing MITRE D3FEND for ATT&CK Technique T1110: Brute Force
- Implementing MITRE D3FEND for ATT&CK Technique T1059: Command and Scripting Interpreter
- Implementing MITRE D3FEND for ATT&CK Technique T1053: Scheduled Task/Job
- How to Automate Incident Response to MITRE ATT&CK Technique T1003: OS Credential Dumping
- How to Automate Incident Response to MITRE ATT&CK Technique T1566: Phishing
- Why MITRE Calls SOAR “Indispensable” in its Latest Book
- See the Evolution of the MITRE ATT&CK Framework from 2015 to Now




