The managed security services business is a booming industry, projected to grow 15.4% per year through the end of the decade. This presents a great opportunity for MSPs that do not yet provide security services, but gaining a foothold in the market might seem daunting. Fortunately, the customers of MSPs often already have tools deployed that can be used by the MSP to deliver managed security services.
In this article, we’ll outline how a SOAR tool like D3 Smart SOAR can act as a bridge between NinjaOne, a common unified endpoint management (UEM) and IT management solution, and CrowdStrike, a common endpoint detection and response (EDR) to deliver automated endpoint remediation.
How SOAR Works
SOAR integrates with software products via their APIs and lets users build automated workflows that trigger when a specific event occurs. For example, if a suspicious process is detected on a device, the SOAR tool will ingest the alert and then unpack and respond to the threat.
An MSP’s First Security Workflow
The data below is a security alert generated by CrowdStrike, which sits as an agent on many devices and monitors for suspicious activity. When behavior is flagged by CrowdStrike, an alert is created and pushed into Smart SOAR for response.
{
"AlertID": "CS-ALERT-20240813-001",
"Severity": "High",
"DateTime": "2024-08-13T14:23:45Z",
"Device": {
"Name": "LAB-PC2",
"ID": 1
},
"User": "john.doe",
"Process": {
"Name": "powershell.exe",
"ID": 4356,
"CommandLine": "powershell.exe -nop -w hidden -enc JABOAGIAYgBsAGUAIAA9ACAAXwBDAG8AbgB2AGUAcgB0AC0AUwBlAGMAdQByAGkAdAB5AEQAZQBzAGMAcgBpAGUAcgA=",
"ParentProcess": {
"Name": "explorer.exe",
"ID": 2334
}
},
"Detection": {
"DetectedBy": "Falcon Sensor",
"Technique": "Behavioral Analysis"
},
"MITRE_ATTCK_Tactics": [
{
"Tactic": "Execution",
"TechniqueID": "T1059.001",
"Technique": "PowerShell"
},
{
"Tactic": "Defense Evasion",
"TechniqueID": "T1027",
"Technique": "Obfuscated Files or Information"
}
],
"Status": "Pending Investigation",
"Analyst": "Jane Smith",
"Comments": "Immediate attention required. Potential malicious PowerShell activity detected, likely associated with a targeted attack."
}
An MSP with access to NinjaOne can use the various fields in this data to gain context on the alert. For example, the Device ID can be used to gather information on its health status.
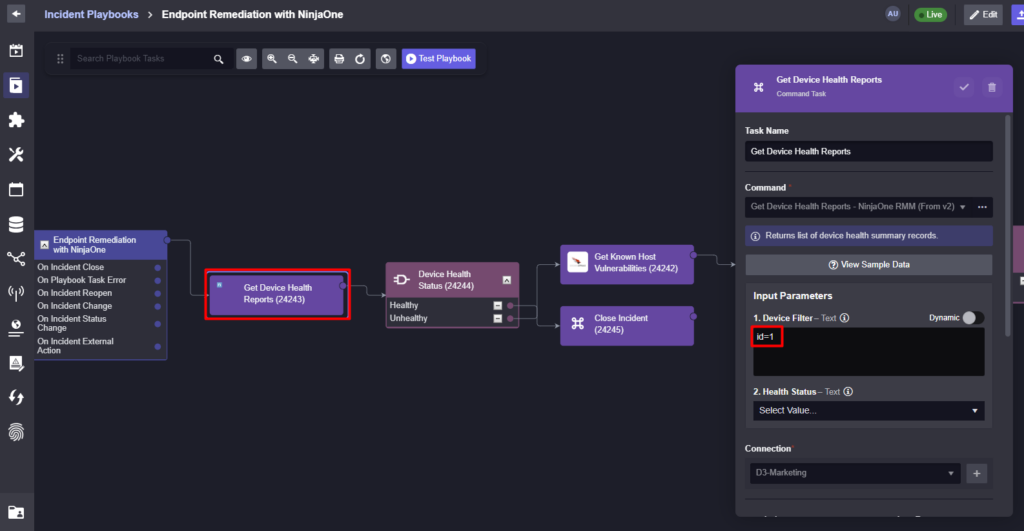
In this workflow, if the device is labeled as unhealthy, the workflow progresses to gather more information on the device from CrowdStrike and NinjaOne, such as the number of known vulnerabilities and the status of its latest OS update.
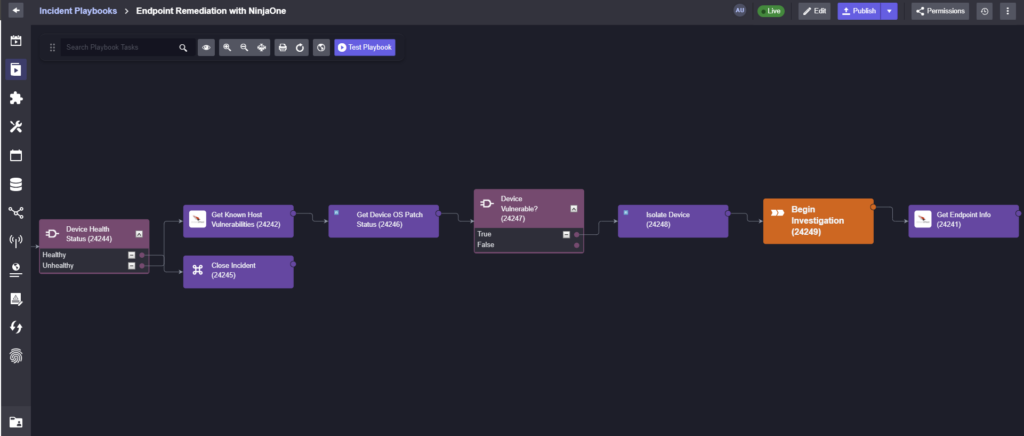
If the device is marked as vulnerable, the playbook leverages the NinjaOne API to isolate the device. Once the device is isolated, the security team can begin their investigation knowing that potential disruption has been minimized.
More on Integrations
SOAR tools will come with hundreds of out-of-the-box integrations, so as an MSP, you can be confident knowing that you will be able to work with a large variety of security and IT management tools that your customers may be using. For example, in Smart SOAR there are over 450 integrations that are pre-built and ready to use. These integrations are developed and managed by the D3 team, so you don’t have to worry about reading API documentation or writing code.
Final Thoughts
This workflow is one example of how MSPs can begin to offer security services using the tools that their clients already have deployed. By centralizing these services in a SOAR tool, they can be streamlined and delivered with little additional requirements on your team’s headcount. We understand that keeping operating costs low are key to building a successful managed service provider, so we designed Smart SOAR to support customers in that journey. For more information, reach out to us here and we can show you what your first security workflow may look like in D3 Smart SOAR.




