There has always been some confusion around the distinctions between SIEM (security information and event management) and SOAR (security orchestration, automation, and response), which has been made worse in the past few years as some SIEM vendors have purchased SOAR companies in order to incorporate their features or sell SOAR as an add-on.
So, unless you’re an expert on the everchanging world of cybersecurity tools (and their corresponding acronyms), you might have wondered things like:
- What’s the difference between SOAR and SIEM?
- Why do I need SOAR if I have a SIEM?
- Can SOAR work without a SIEM?
In this article, we’ll try to answer all of those questions, because, SIEM and SOAR aren’t at all redundant, despite some superficial similarities. In fact, SOAR works excellently alongside a SIEM, expanding the SIEM’s powerful capabilities to effectively analyze, investigate, and respond to alerts. A SIEM is a great alert source, with its ability to aggregate and detect anomalous activity. The addition of a SOAR tool for escalation of notable alerts gives security teams with a SIEM the ability to add automation to their workflows and much more.
For more detail on this topic, including how D3’s Smart SOAR platform relates to SIEM, read SIEM & Smart SOAR: Everything You Need to Know.
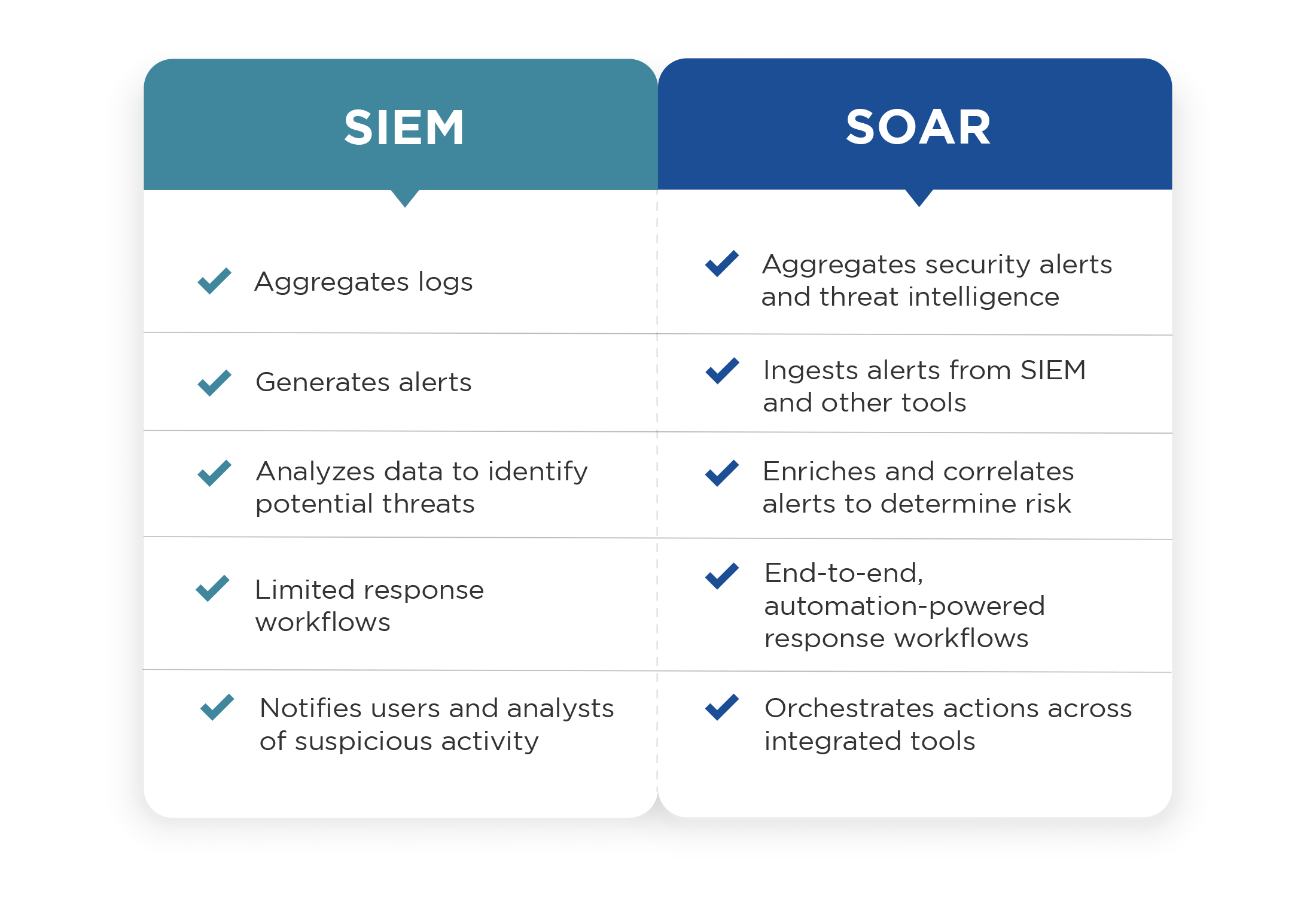
How Do SIEM and SOAR Work Together?
As long as SOAR has been around, it’s been seen as a perfect complement to a SIEM. For example, Gartner uses the combination of SIEM+SOAR as an example of a common approach to detection and response—contrasted with other approaches like XDR.
Even though other tools have come along that provide alternatives to the SIEM-centric SOC, a SIEM is still an ideal alert source, with its ability to aggregate and flag anomalous activity. Those alerts can be then escalated to an integrated SOAR platform, either manually or automatically based on SIEM rules.
The SOAR platform can then be used to analyze the alert, determine if it is a genuine incident, and orchestrate the necessary response across other integrated systems. High-quality integrations between SOAR and SIEM are also bidirectional, allowing the SOAR platform to query the SIEM for more information, and update it when the incident is resolved.
Read: How Smart SOAR Integrates with SIEMs
SIEM vs. SOAR: What Can SOAR Do That a SIEM Cannot?
An organization with a SIEM still needs SOAR. Despite the powerful capabilities of a SIEM, it doesn’t have the incident response, investigation, and case management tools and workflows needed to efficiently manage threats.
Adding SOAR extends SecOps functionality across the full incident lifecycle, with features including:
- Alert enrichment with threat intelligence, IOC correlations, and other data
- Incident-specific, automation-powered playbooks
- Orchestrated actions across the security environment, leveraging hundreds of integrations
- Comprehensive dashboards and reporting
Read: XDR vs. SIEM vs. SOAR: A Vendor-Agnostic Perspective
Can SOAR Work Without SIEM?
Many organizations that don’t have a SIEM still benefit greatly from SOAR. A SIEM is just one of the many alert sources that SOAR can integrate with. Even in organizations that have a SIEM, their SOAR tool will aggregate alerts from EDR, email protection, cloud security tools, and others—along with receiving incidents that are manually reported. SOAR can work perfectly well without a SIEM because many common use-cases begin from these other alert sources.
For example, if a potentially malicious file is detected on an endpoint by an EDR tool, the alert can be escalated to the SOAR tool, where the IOCs are extracted and checked against threat intelligence and past incidents. The SOAR playbook will also query additional information from the EDR and orchestrate actions such as scanning endpoints for correlated IOCs. Once the event has been properly investigated, the response playbook will orchestrate actions across the EDR—such as isolating affected machines—and other tools—such as blocking the sender’s domain in an email protection tool if the file came via email.
For more answers to questions about SIEM and SOAR, don’t forget to check out our downloadable resource SIEM & Smart SOAR: Everything You Need to Know.




