Threat hunting is a critical practice for catching sophisticated threats that may bypass the most advanced detection tools in a SOC. It helps organizations stay ahead of potential threats before they transform into significant issues. In threat hunting, analysts aim to identify signs of a potential cyberattack, while also working to understand the broader threat landscape and develop strategies to protect against future attacks.
In this blog, we’ll delve into how Smart SOAR helps security teams automate their response to cyber threats. By utilizing the mesh architecture that Smart SOAR enables, security teams can improve their response times, reduce the potential for human error and reallocate their time and resources to other critical areas, enhancing overall cybersecurity resilience.
How Threat Hunting Has Changed in the Past Decade
The cyber threat intelligence (CTI) market value is estimated at $11.6 billion, highlighting the significant investment organizations are willing to make to safeguard their digital assets and data. MITRE’s book ‘11 Strategies of a World-Class Cybersecurity Operations Center’ notes that many SOCs now consider threat hunting to be a foundational skill.
A decade ago, most cybersecurity strategies were reactive, responding to incidents after they occurred. Over time, the focus has shifted to proactive threat hunting, which involves understanding and anticipating the tactics, techniques, and procedures (TTPs) used by adversaries. Previously, threat hunting was a manual, time-consuming process. Now, tools such as Smart SOAR have made the threat hunting process more efficient through automation and orchestration of routine tasks, and by leveraging integrations with a wide range of security tools.
How Smart SOAR Helps Threat Hunters
Automated Alert and Incident Management
Throughout the incident response lifecycle, Smart SOAR excels in automating repetitive tasks, alleviating analyst burden, and reducing stress. At the initial alert stage, Smart SOAR playbooks enable SOC teams to automatically trigger triage and correlation actions. This automation expedites the dismissal or escalation of alerts to the incident level, while also assigning a risk score for prioritization.
Moving to the incident level, Smart SOAR playbooks can further enhance efficiency by automating the creation, updating, and management of incidents. Based on the playbook and investigation results, predefined response actions are executed. These actions may include isolating compromised systems or blocking malicious IP addresses. Notably, all actions taken from initial detection to final resolution are automatically documented in a comprehensive incident report.
Read: How to Reduce the Financial Impact of Security Incidents by 90% or More with Smart SOAR
Scheduled Automated Workflows
Smart SOAR provides the ability to schedule automated workflows. For example, SOC teams can schedule periodic data retrieval from threat intelligence platforms and subsequent actions such as parsing and normalizing the data, and searching for indicators of compromise (IOCs) through the organization’s log data or other security tools. If an IOC is found, an incident can be automatically created and response actions, such as blocking a URL or isolating a machine, can be automatically executed to limit the potential damage.
Indicators of Compromise (IOC) Search
Smart SOAR can search for IOCs such as file hashes, URLs, IP addresses, and domains from incoming incidents and use them to run searches across your entire environment. It can also expand your understanding of the incident by incorporating linked IOCs into the search. You can configure playbooks to automate remediation actions, like blocking an IP or triggering a password reset.
This IOC search workflow searches D3’s database for related events and incidents and pulls a list of affected hosts.

This IOC search workflow searches D3’s database for related events and incidents and pulls a list of affected hosts.
Ongoing Surveillance Tasks
The Ongoing Surveillance capability of Smart SOAR enables continuous monitoring of threats. You will be promptly notified when these threats are implicated in any incident.
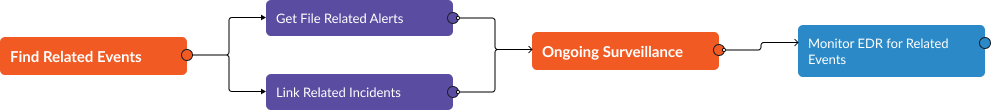
Imagine that your EDR has detected a suspicious file in the network. The ongoing surveillance capability of Smart SOAR can be used to search for related past events or incidents involving the file hash value. This can help establish if this file has been encountered before in your network and how it was dealt with, providing crucial context for the current incident. Simultaneously, Smart SOAR can monitor the EDR tool for any new alerts associated with the same file hash. If the EDR tool sends an alert about a new instance of the same file on a different endpoint, a Smart SOAR playbook can be configured to trigger a predefined response, such as isolating the affected endpoint, notifying the SOC team about the new incident, and even initiating a malware scan or removal process on the affected endpoint.
Smart SOAR: Ushering in a New Era of Enhanced Threat Hunting
Smart SOAR offers a transformative solution to the challenges faced by modern SOCs. By harnessing the capabilities of Event Pipeline-driven security hyperautomation, IOC surveillance, and scheduled workflows, SOC teams can significantly enhance their threat hunting capabilities. Embracing Smart SOAR enables analysts to focus on high-value tasks, improve incident response times, and bolster their overall cybersecurity posture. Schedule a demo to see it in action.




