-

The Future of Defensible Security: From Reactive Playbooks to Attack-Pattern-Aware Autonomous Response
Why static automation isn’t enough—and what real-world adversary data tells us about how the next-gen SOC must evolve.
-

D3 Security Releases “In the Wild 2024” Report with Analysis and Incident Response Playbooks for the 10 Most Prevalent Cyber Attack Techniques
Vancouver, BC — April 10, 2024 — D3 Security, the leader in smart security orchestration, automation, and response (SOAR), today published In the Wild 2024,…
-

The 10 Most Common MITRE Tactics & Techniques of 2023
SOAR solutions create a centralized queue of all incidents going on in a security team’s environment. Endpoint, SIEM, email, behavior, and network alerts are all…
-

MITRE ATT&CK Technique-Driven Automation with Smart SOAR
MITRE ATT&CK is invaluable for SOC teams in understanding adversary behaviors and actions across a range of networks. This robust framework offers granular insight into…
-

What Are MITRE ATT&CK and MITRE D3FEND?
Ever wish you had a crystal ball for cyber threats? Meet MITRE ATT&CK and MITRE D3FEND, your digital fortune-tellers. In a fast-moving threat landscape, staying…
-

Implementing MITRE D3FEND for ATT&CK Technique T1053: Scheduled Task/Job
Scheduled task/job threats, which make up MITRE ATT&CK Technique T1053, can have severe implications for an organization’s security. MITRE also outlines how to address this…
-
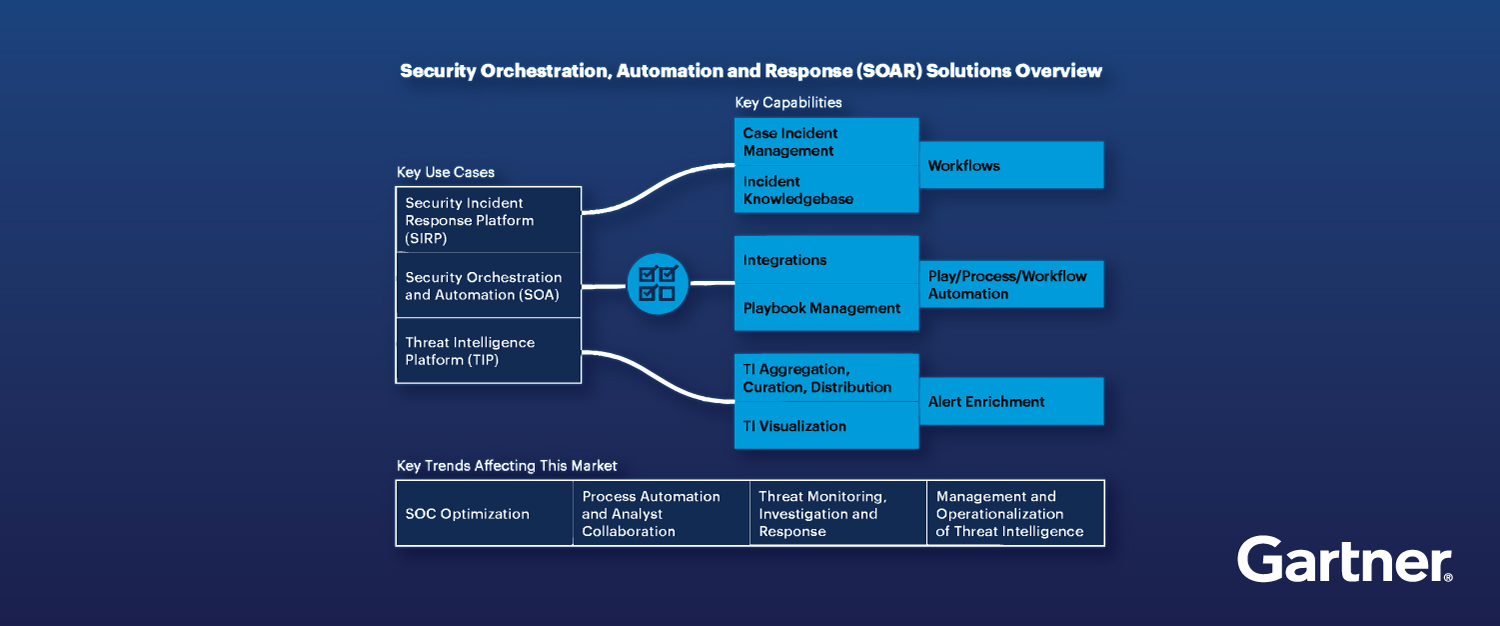
Top 5 Takeaways From Gartner’s 2023 Market Guide for SOAR
As an independent, vendor-agnostic SOAR provider, we‘re thrilled to announce that D3 Security has been recognized for the third consecutive time as a Representative Vendor…
-
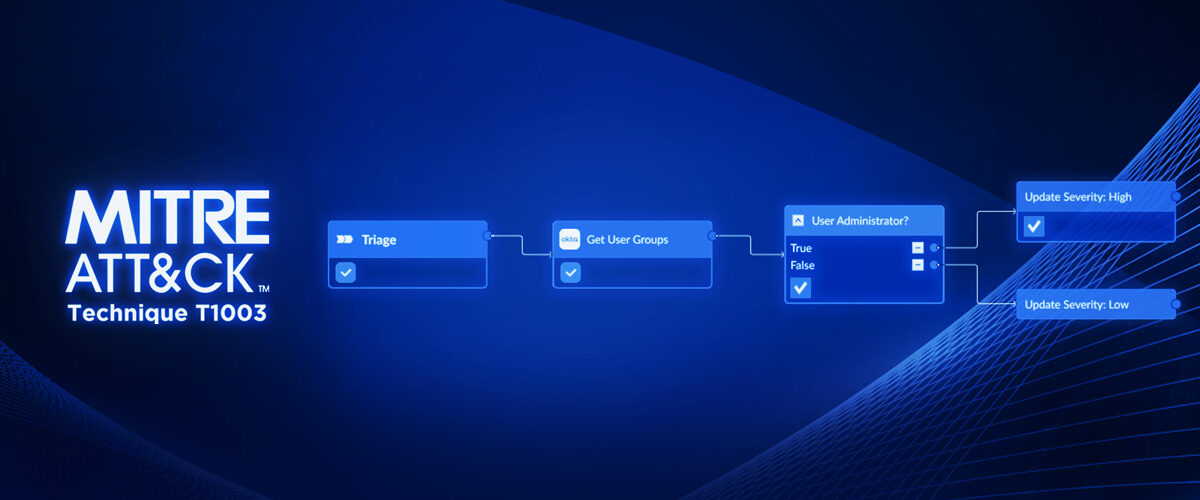
How to Automate Incident Response to MITRE ATT&CK Technique T1003: OS Credential Dumping
In this blog post, we will outline four incident response playbooks for MITRE ATT&CK Technique T1003: OS Credential Dumping. Credential Dumping is a technique that…
MITRE ATT&CK
Select a term…
