Security Orchestration, Automation, and Response (SOAR) platforms have transformed how organizations handle security alerts and incidents. However, many traditional SOAR solutions come with high ongoing maintenance requirements, demanding skilled engineers and constant vendor support. This complexity often stems from how these platforms handle data ingestion and normalization—or lack thereof. In this blog, we’ll explore the challenges posed by traditional SOAR tools and how D3’s dynamic data normalization simplifies maintenance, streamlines workflows, and reduces the burden on security teams.
The Challenges with Traditional SOAR Tools
High Maintenance Requirements
Most SOAR platforms require dedicated engineers and developers to maintain the system. Managing multiple alert types, complex playbooks, and broken workflows necessitates specialized skills and continuous oversight. Organizations often find themselves in constant communication with the vendor’s support team to troubleshoot issues and adapt to new threats.
Lack of Data Normalization
A significant issue with other SOAR vendors is their failure to normalize data upon ingestion. Instead, they:
- Process every alert as a standalone event: This approach treats each alert uniquely, ignoring the benefits of standardized processing.
- Require heavy Python coding to reformat data: Engineers must write extensive code to reformat alerts into a standard structure, adding to the maintenance burden.
Consequences of Poor Data Handling
- Complicated Playbooks
Each alert type demands its own playbook structure to address format differences. This results in playbooks with multiple paths—one for each alert structure—making them overly complex and difficult to manage. - Broken Workflows
If a playbook receives a new or unexpected alert structure, the workflow can break, halting automation entirely. This not only disrupts security operations but also increases the risk of missing critical threats. - Constant Monitoring and Oversight
Engineers must continuously monitor data ingestion, detection parameters, and playbook runs. This constant vigilance distracts them from strategic tasks and can lead to burnout.

Read our Whitepaper: The Hidden Costs of Legacy SOAR
D3’s Solution: Dynamic Data Normalization
Data Normalization on Ingestion
D3 tackles these challenges by normalizing data as it comes in. Every alert is reformatted into a single, standard structure upon ingestion. For a technical deep dive, read this article here, but at a high-level, the process is:
- Entirely configurable: Organizations can tailor the normalization process to fit their specific needs.
- Dynamic: The system adapts in real-time to different data formats.
- Comprehensive: Normalization happens across every ingestion point, ensuring consistency.
Benefits of D3’s Approach
- Simplified Playbooks
With data normalized, playbooks become significantly simpler. Security teams deal with one unified structure, eliminating the need for multiple paths and reducing the chance of errors. - Resilient Workflows
Dynamic mapping ensures workflows are robust and adaptable. Even if a new alert structure is introduced, the system adjusts without breaking the automation process. - Reduced Maintenance Overhead
Engineers only need to maintain a single workflow path. Any necessary oversight occurs at the ingestion level, freeing up resources and allowing teams to focus on higher-level security strategies.
Playbook without Normalization
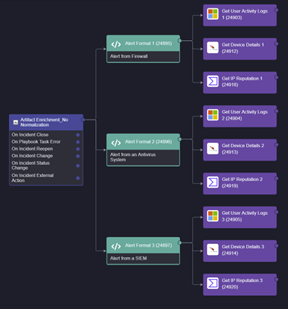
Playbook with Normalization
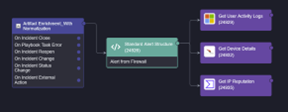
This is a 67% reduction in the number of tasks needed for this enrichment playbook. If you scale up the number of alert structures this number increases dramatically to 75, 80, 85, and then an over 90% playbook size reduction.
Key Takeaway
High maintenance requirements shouldn’t be the norm for SOAR platforms. D3 Smart SOAR’s dynamic data normalization streamlines security operations by simplifying playbooks, enhancing workflow resilience, and reducing the need for constant oversight. By addressing data normalization at the ingestion point, D3 enables organizations to fully leverage automation without overburdening their security teams.




