Carbon Black is a powerful endpoint protection platform, offering advanced threat hunting and incident response capabilities. When integrated with D3 Smart SOAR, it can further enhance your organization’s security posture by automating the incident response process, reducing the time it takes to address threats, and minimizing the impact on your business. In this blog post, we will explore how Carbon Black can be used within D3 Smart SOAR to streamline incident response workflows and provide comprehensive protection against cyber threats.
Typically, the Carbon Black integration is used alongside a SIEM, IAM, NDR, and OSINT tool to complement gaps that might be in the original alert and in Carbon Black’s database. The example below uses Carbon Black by itself to show the possibilities around automated incident response with D3 Smart SOAR.
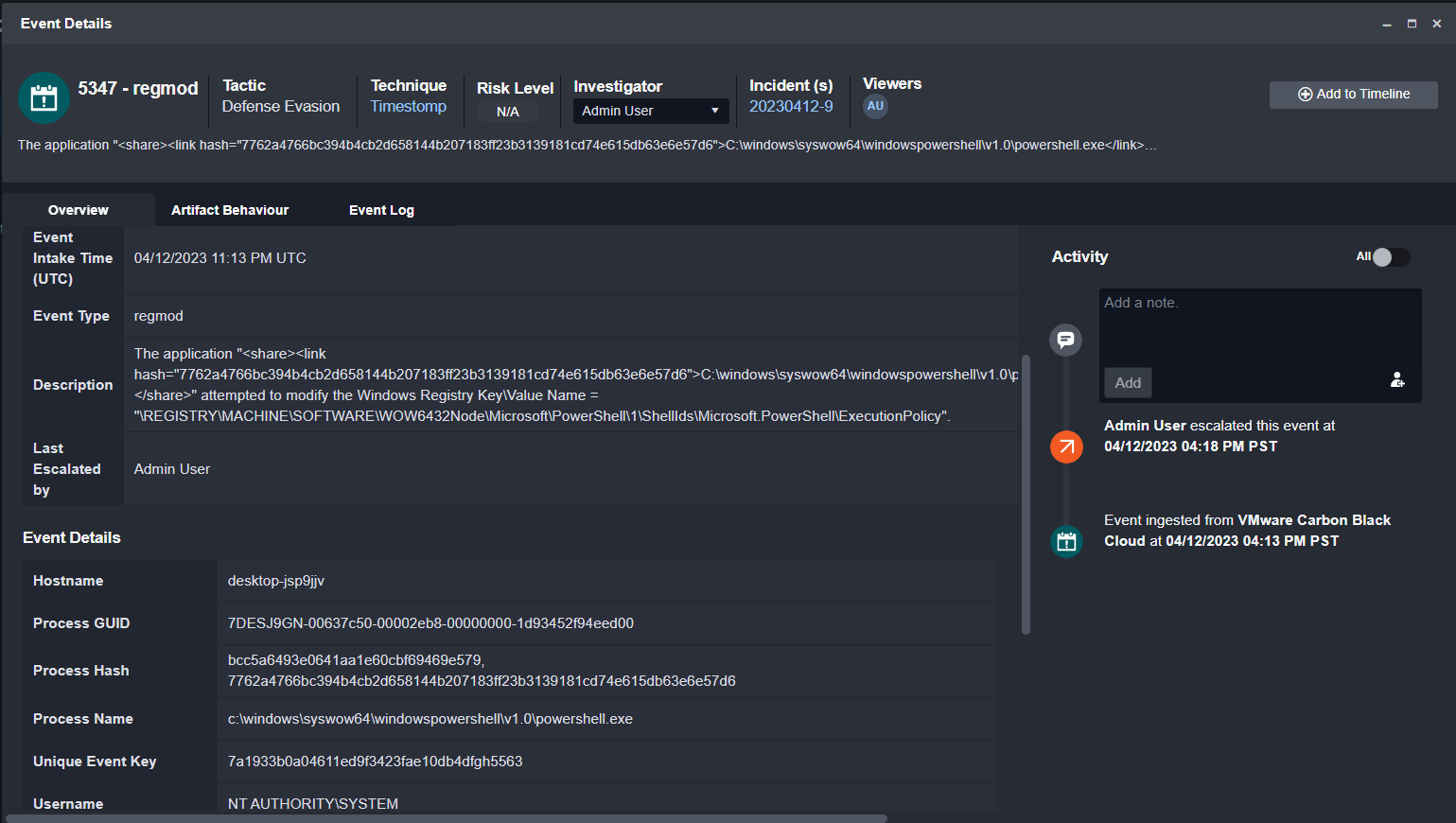
The Alert
This example uses a registry modification alert generated by Carbon Black. The event data contains the hostname, process GUID, process hash, process name, and the user. To investigate this further, we’ll need more information on the device and process.
The Playbook
This incident playbook has three main stages: correlation, enrichment, and remediation. The correlation stage searches Carbon Black’s database to pull in other alerts related to the device or process. Users can also search their SIEM or NDR for similar alerts if those tools are connected. Similarly, they can search Smart SOAR’s incident and event databases for related events that other tools may not have linked.
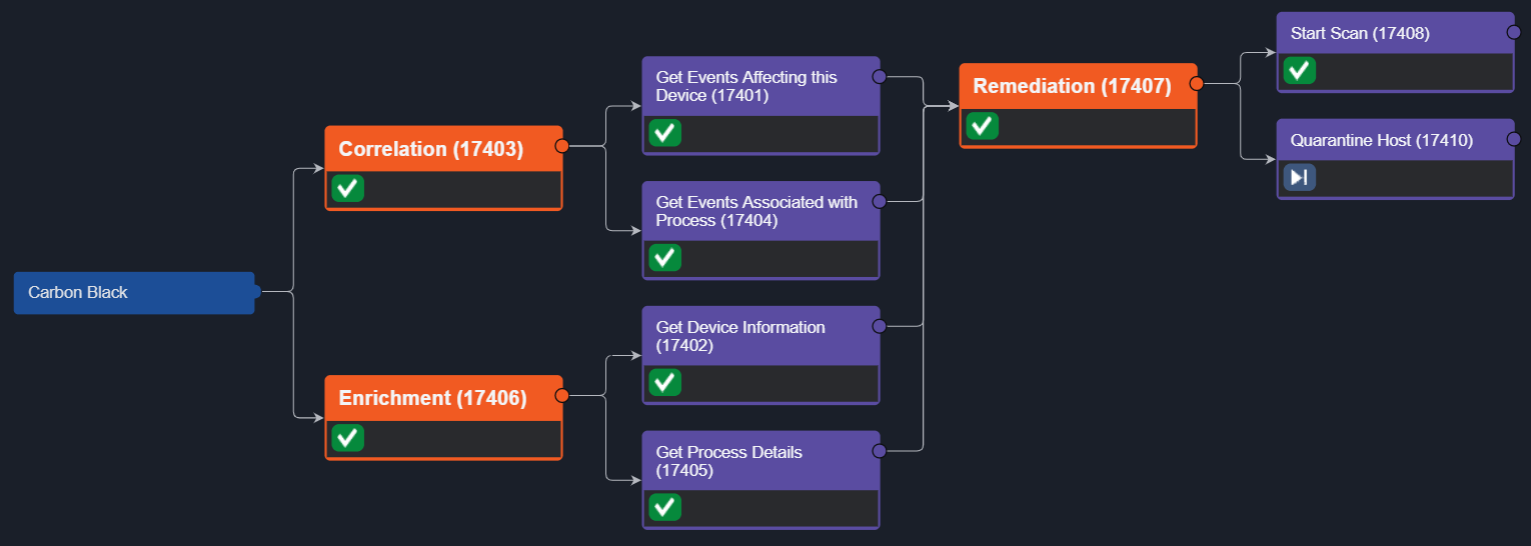
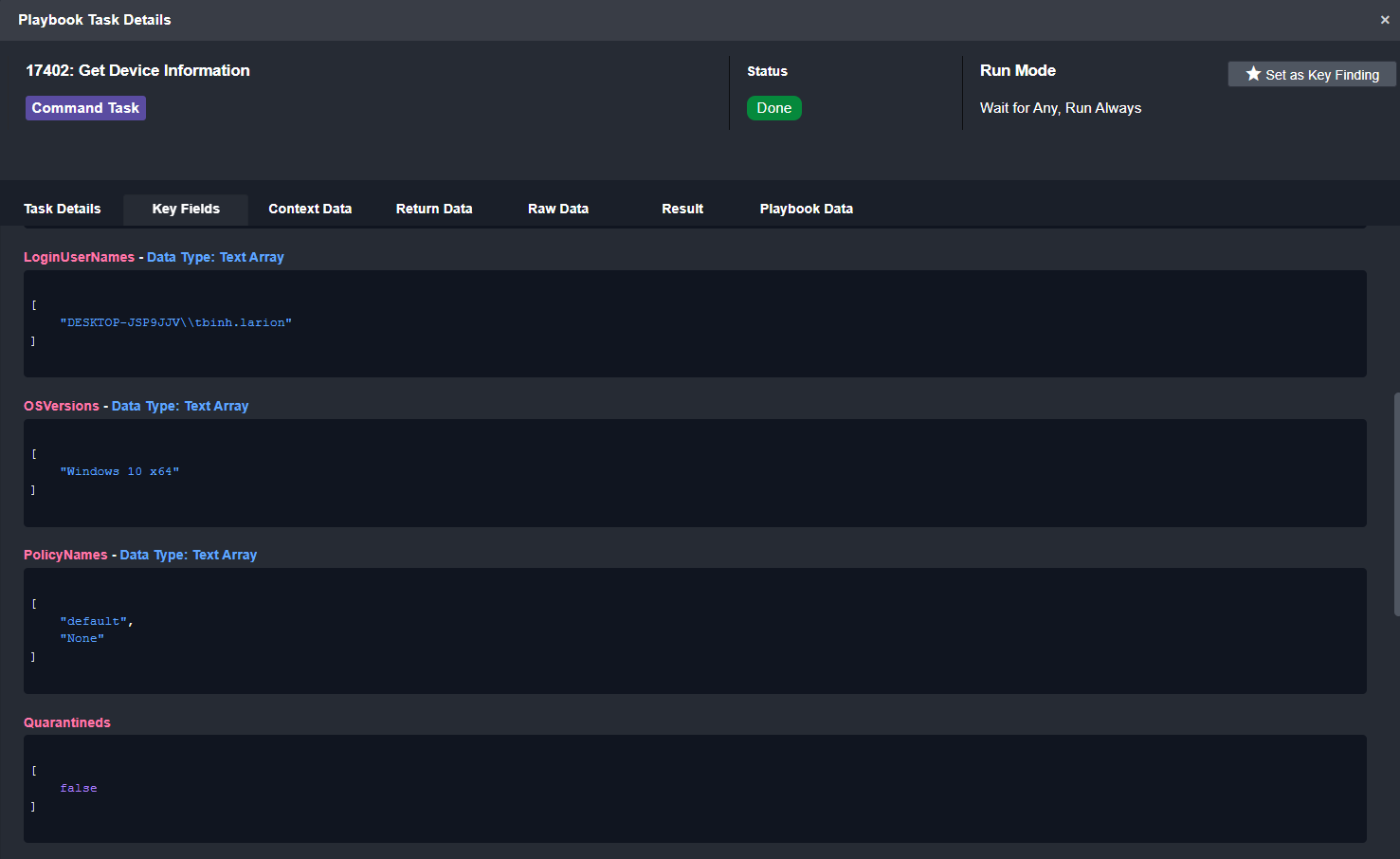
The enrichment stage pulls in additional information on the device and process. The Get Device Information command returns important information about the device, such as its vulnerability rating, registration status, and policies.
Get Device Info
Once the enrichment and correlation stages are complete, the playbook starts a scan on the affected device and gives the analyst the option to quarantine it. The total runtime for this playbook is 14 seconds.
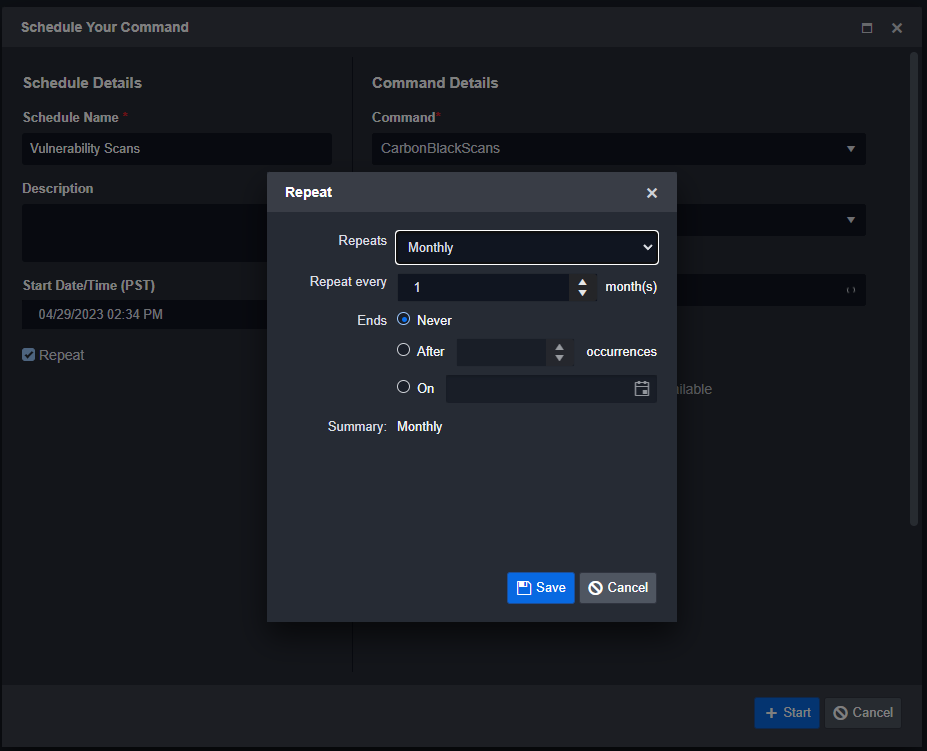
Vulnerability Scans
![]()
In Smart SOAR, users don’t have to wait for a security alert to trigger a playbook. They can use our scheduled automation feature to run playbooks in the background, independent of the events and alerts ingested into the platform. This capability enables users to automatically initiate background scans on target machines via Carbon Black’s API.
Conclusion
Integrating Carbon Black with D3 Smart SOAR offers organizations an efficient and powerful solution for automating incident response workflows. By leveraging the capabilities of Carbon Black and Smart SOAR, security teams can effectively correlate, enrich, and remediate incidents in a matter of seconds, significantly reducing the time to respond to threats. Moreover, the scheduled automation feature in Smart SOAR allows for proactive security measures, further enhancing an organization’s defense against cyberattacks.




