Scheduled task/job threats, which make up MITRE ATT&CK Technique T1053, can have severe implications for an organization’s security. MITRE also outlines how to address this technique in their D3FEND Matrix. However, until now, security teams haven’t had a consistent way of implementing D3FEND best practices.
This blog will explore how Security Orchestration, Automation, and Response (SOAR) can be utilized to implement MITRE D3FEND when addressing a Scheduled Task/Job threat. We will go through the various stages of MITRE D3FEND and demonstrate how Smart SOAR playbooks follow these stages to implement a consistent response to T1053.
MITRE ATT&CK Technique Overview
Scheduled task/job threats involve malicious activities executed through scheduled tasks, which can result in unauthorized access, data breaches, and disruptions to critical processes. In a study by MITRE Engenuity that took place between April 2019 and July 2021, Scheduled Task/Job was the most frequently observed technique, appearing in 24.1% of incidents. The scheduled job/task technique is also often used to enable other techniques, so shutting this threat down quickly prevents numerous other attacks.
The D3FEND Matrix
The MITRE D3FEND Matrix has six stages: model, harden, detect, isolate, deceive, and evict. Each has different tasks that can be completed to address T1053. In the examples below, I will show you how Smart SOAR playbooks can turn D3FEND’s recommendations into automated workflows.
Read: MITRE ATT&CK and D3FEND Explained
Stage One: Model
D3FEND Recommendation: Asset Vulnerability Enumeration. In stage one, MITRE recommends compiling a list of all vulnerabilities on the device that triggered the alert. In Smart SOAR, various endpoint detection and response tools can be used to run vulnerability scans on the affected device. For example, CrowdStrike users can:
- Initiate Ad-Hoc Scans: You can trigger a scan and pull the results into your playbook. The data from the scan includes malicious files and host metadata.
- Get Host Vulnerabilities: This command compiles a list of vulnerabilities associated with a specific host. The results include any affected applications, evaluation logic, remediation steps, and CVE IDs.
- Search Vulnerable Hosts by CVE: Using CVE IDs found in the previous task, you can then search for other affected hosts to uncover vulnerabilities that may be exploited for T1053.

Stage Two: Harden
D3FEND Recommendation: Local File Permissions. Once vulnerabilities and malicious files have been identified, identity and access management applications can be used to restrict a user’s access to specific files. For example, Active Directory is used in the following workflow to effectively manage access control by listing groups, retrieving user groups and group details, and adding devices and users to specific groups.
- List Groups: This command retrieves a list of all the groups present in Active Directory. It includes information such as their names, unique identifiers. It gives the response team an overview of the existing groups within their environment.
- Get User Groups: This command retrieves a list of groups that a specific user belongs to. This information is useful for understanding the user’s current access and privileges.
- Get Group Details: This command retrieves details about a specific group in Active Directory. It includes information such as the group type (e.g., security group or distribution group) and membership details. This helps users understand the purpose of any groups they are unclear about.
- Add Device to Group: Once the correct access management has been determined, device groups can be changed to apply updated access and control policies.
- Add User to Group: Similar to step four, user groups can be updated to apply necessary privileges to users whose accounts may have been compromised.
Implementing this workflow provides a centralized, consistent, and structured approach to managing user and device access across multiple files and directories.

Stage Three: Detect
In stage three, MITRE recommends various actions to verify T1053 threats. They include: Process Spawn Analysis, Scheduled Job Analysis, and File Analysis. Integration commands in Smart SOAR can easily be used to execute these various tasks. The workflow below uses Trellix (formerly McAfee), Okta, and Zscaler to compile all related information related to system tasks, user activity, and malicious files.
D3FEND Recommendation: Process Spawn Analysis. The command Get User Activity Logs from Okta provides insights into user actions, such as login attempts, application usage, and account modifications.
D3FEND Recommendation: Scheduled Job Analysis. Using two commands from Trellix, List all Server Tasks and Get Task Details, this playbook creates a comprehensive list of all server tasks or processes running within the system. It provides an overview of active tasks, their statuses, and resources. Then, specific tasks can be investigated further to understand their dependencies, execution details, and resource consumption.
D3FEND Recommendation: File Analysis. Zscaler’s sandbox environment can be accessed directly through Smart SOAR to safely detonate suspicious files and retrieve the results for analysis. The sandbox reports provide detailed insights into the behavior, activities, and potential threats associated with the analyzed file.
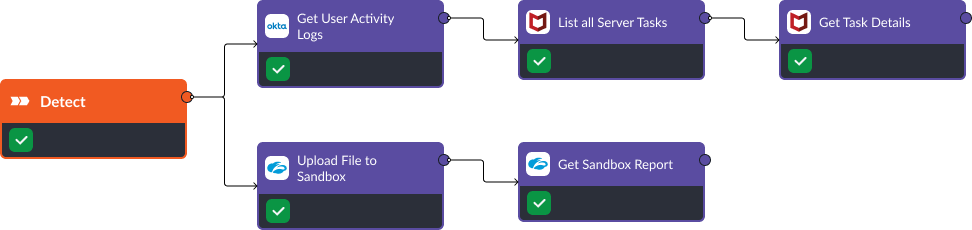
The combination of intelligence from endpoint, network, and identify tools can give users more context surrounding a suspicious scheduled task/job alert. This information is needed in order to make an informed decision when progressing to the isolation stage.
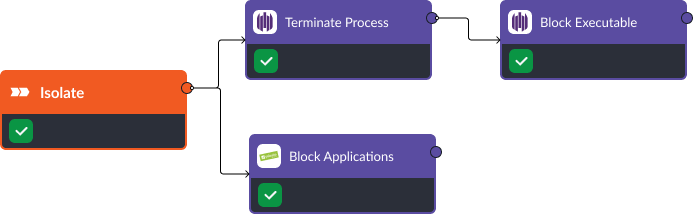
Stage Four: Isolate
When suspicious processes, files, and applications are identified, Smart SOAR can automatically block and isolate these IOCs.
D3FEND Recommendation: Hardware-based Process Isolation. Using scripts uploaded to SentinelOne, Smart SOAR can forcefully terminate a running process on endpoints. This allows users to stop a process that may be malicious or unauthorized.
D3FEND Recommendation: Executable Allow/Denylisting. With the Block Executable command, users can add a hash value associated with a file or software component to the blocklist in SentinelOne. This prevents the execution or access of files with matching hash values.
D3FEND Recommendation: System Call Filtering. This workflow uses Palo Alto Next-Generation Firewall to block specific applications to prevent unauthorized usage or launch across the network. This helps reduce the risks associated with potentially compromised software.
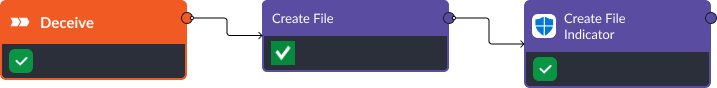
Stage Five: Deceive
D3FEND Recommendation: Decoy File. With two steps in a playbook, Smart SOAR can create a decoy file using user-generated input. Then, it takes the file hash and adds it to Microsoft Defender for Endpoints’ detection rules. Using this workflow, users can alert themselves when this file is accessed on a specific device.
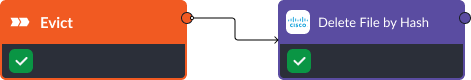
Stage Six: Evict
D3FEND Recommendation: File Removal. The final task is to remove malicious files or programs. Once the files have been analyzed and quarantined through stages three and four, they can be permanently removed. Commands like Delete File by Hash using Cisco Secure Endpoint accomplish this easily.
Conclusion
SOAR provides a unique opportunity for security teams to implement MITRE D3FEND best practices. By combining various commands and integrations, such as retrieving user activity logs, listing server tasks, blocking hashes and applications, and utilizing sandbox analysis, organizations can achieve a holistic approach to detect, isolate, and mitigate T1053. The workflows outlined above provide a centralized and structured approach to managing access control, analyzing system tasks, and taking proactive actions to protect against scheduled task/job-related security incidents.




