Isn’t it annoying when multiple alerts are clearly related, but you can’t easily consolidate them into a single incident? This is the issue faced by most SOCs. Either their detection platforms cannot group alerts from different data sources, or their SOAR tool does not have the ability to group multiple events within a single case.
In environments without automated alert grouping, security analysts are often overwhelmed by the sheer volume of alerts. Each alert must be individually reviewed and correlated manually, which is time-consuming and error-prone. Analysts have to sift through alerts from various sources, trying to identify patterns and connections that indicate a single incident. This manual process not only slows down the response time but also increases the likelihood of missing critical links between alerts, leading to potential security breaches.
With automated grouping, the scenario is vastly different. Central incident response systems can instantly correlate alerts from multiple data sources, identifying common indicators of compromise and consolidating them into a single incident. This capability allows analysts to see the bigger picture at a glance, ensuring that related alerts are not overlooked. Automated grouping reduces the noise by filtering out irrelevant alerts and focusing on significant threats, enabling a faster and more efficient response.
Three features in Smart SOAR that make this process possible—and even simple—are the:
- Event playbook,
- Incident workspace, and
- Playbook triggers.
Let’s walk through each feature and demonstrate how they make alert grouping a breeze.
Event Playbook
When alerts are first ingested into Smart SOAR, they are stored as events. If an event needs to be investigated, it’s escalated into an incident. This is a similar structure to many SIEMs, though is unique to Smart SOAR among SOAR platforms. The advantage of this two-tier alert structure in SOAR is that users can run correlation, triage, and deduplication playbooks on alerts before they escalate into an incident, creating many opportunities to reduce the total number of incidents analysts have to deal with.
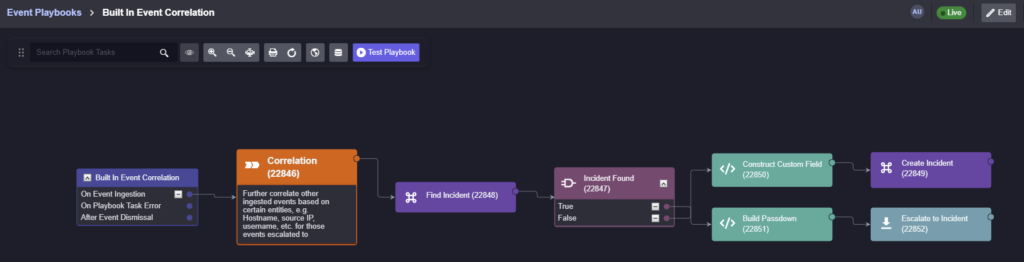
Above is an event playbook designed to search existing incidents for a related hostname within a 48-hour period. If an open incident is found that is related to the same endpoint, the incoming alert is attached to the existing incident, rather than escalated as a separate incident.
The correlation logic can be customized based on types of incidents, technologies, or incident response team structure that’s unique to your organization.
Incident Workspace
Smart SOAR has robust case management capabilities that are available out of the box, without any additional formatting needed. Included in the workspace are:
- Artifact and Data Management
- Correlation and Categorization
- Task Management
- Tracking and Auditing
- Reporting
- User Management and Collaboration
- Searchability and Data Storage
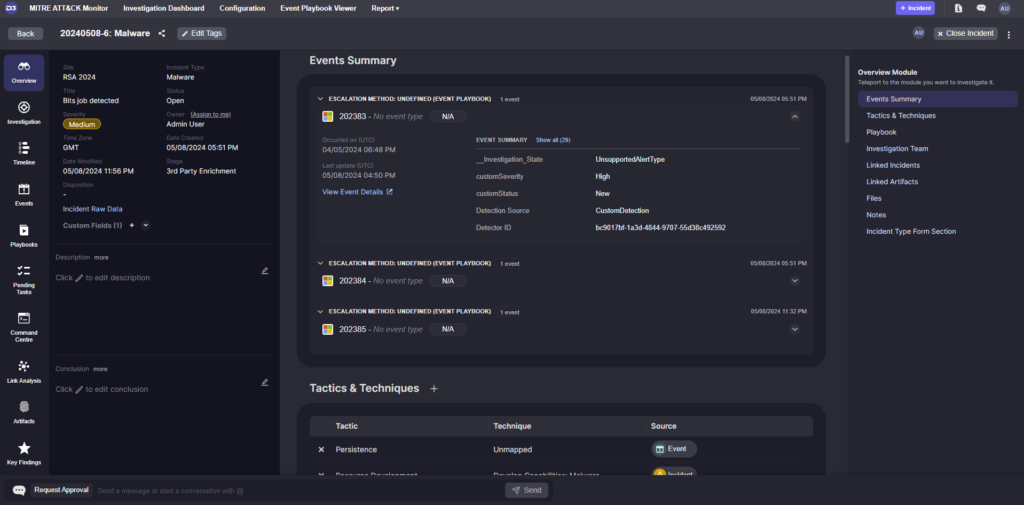
For alert grouping, Correlation and Categorization are most important. In the screenshot above, you can see an event summary taking up the majority of the incident workspace. Beneath it are two alerts, also from Microsoft Defender, that the event playbook categorized as related and attached to this incident. By navigating to the events tab, we can look into the underlying alert data, artifact behavior, and timeline.
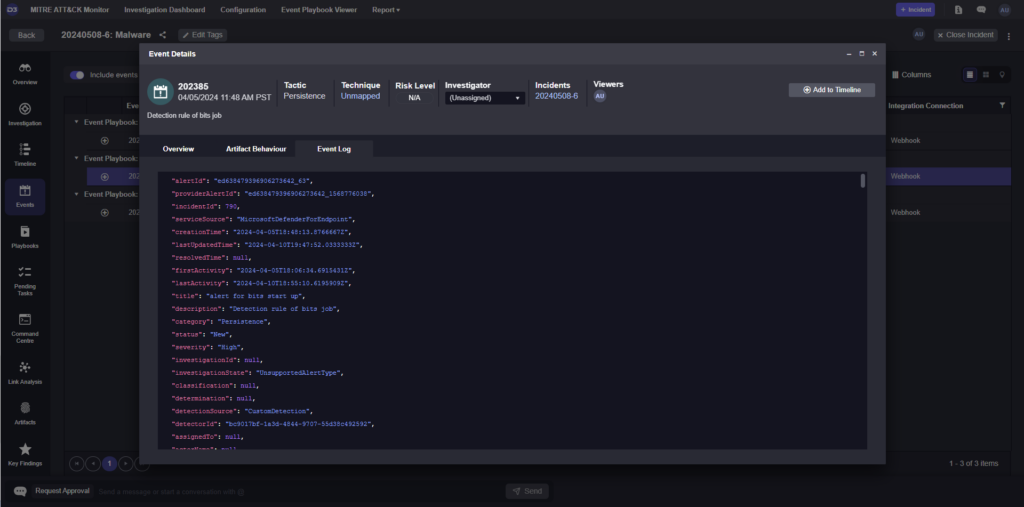
Playbook Triggers
The final piece of automated grouping is playbook triggers. After an alert is attached to an existing incident, a few things need to happen. The investigator needs to know about the new alert and the new alert needs to be incorporated into the incident response process. Playbook triggers are how Smart SOAR executes these actions.
In short, playbook triggers activate workflows when changes to an incident are made. One of the changes that can trigger a new workflow is new events being added.
The simplest workflow is to alert the incident owner. This can be done through Smart SOAR’s built-in messaging system, or through an external tool, like email or a messaging platform.
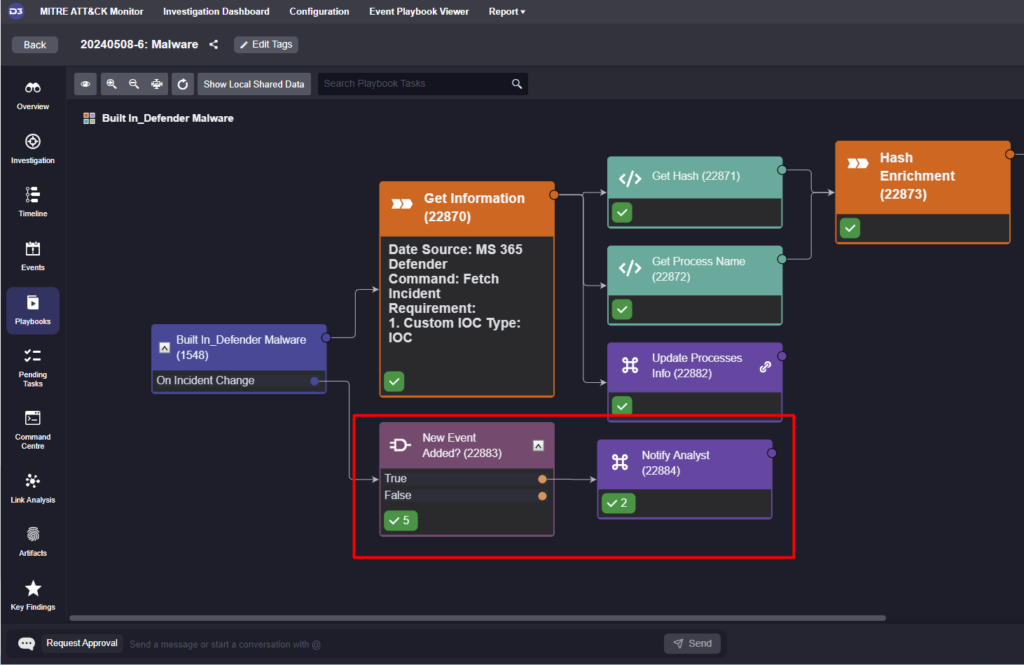
Above, you can see two tasks that trigger only on an incident change and check to see if a new event has been added. If true, the workflow notifies the analyst, who can then come and review the new event.
For a complete answer on what can be done with playbook triggers, read this article: Beyond One-Size-Fits-All: Advanced Playbook Triggers for Unique Use-Cases
Takeaway
The event playbook, incident workspace, and playbook triggers are three features that make grouping-related alerts simple and efficient in Smart SOAR. Unlike other SOAR platforms, which may require constructing custom cases or might not support case linking at all, Smart SOAR offers easy-to-activate capabilities for seamless alert correlation. These features streamline the incident response process by reducing the number of unique incidents to investigate and providing comprehensive information on each case, ultimately enhancing the overall effectiveness and ease of alert response.




