Open-source threat intelligence (OSINT) is a valuable asset to pull from during incident investigations. However, doing this for every alert is monotonous and can be prone to human errors. When using SOAR security tools, you can build IoC enrichment directly into playbooks and automatically populate incident tickets with notable information from the community.
One popular OSINT database is AlienVault. Within Smart SOAR, there are two AlienVault integrations available out of the box:
- AlienVault OTX
- AlienVault USM Anywhere
In this article, I’ll outline how these two integrations can be used to ingest security alerts and automatically enrich them using the AlienVault integration.
Automated Enrichment with AlienVault OTX

The first step of this workflow is the event intake command Fetch Event. This pulls alerts in from AlienVault USM and stores them as events inside of Smart SOAR.
Then, AlienVault OTX is used to enrich the alert with the following commands:
- Check IP Reputation
- Get File Information, and
- Get URL Information
These commands are very versatile and appear in many playbooks for various incident types. Alerts from endpoint, network, or email security tools will often have IoCs that would benefit from being enriched using these AlienVault commands.
Once the results have been gathered by the playbook, they are displayed to users in the incident Investigation tab of the incident overview:
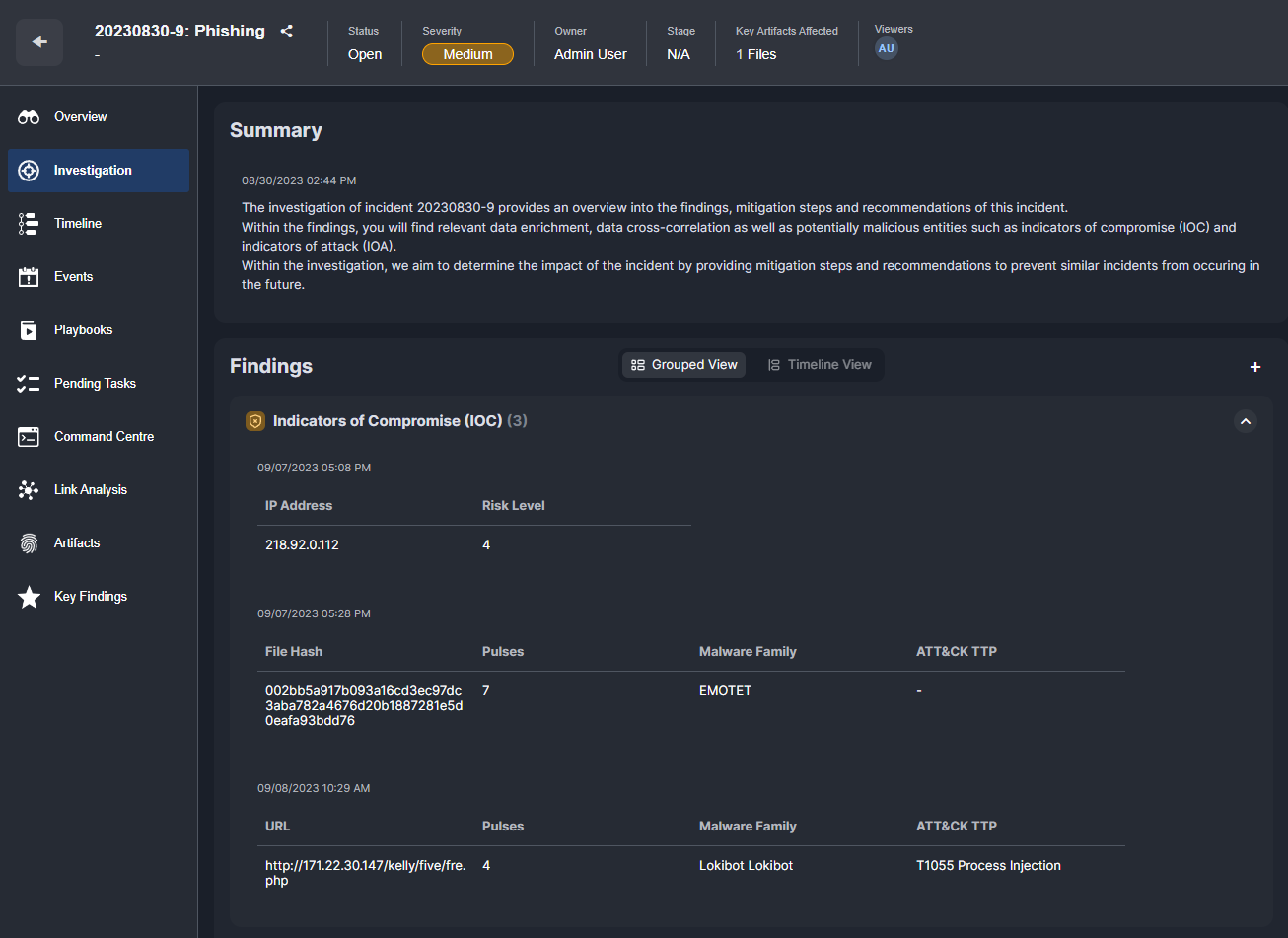
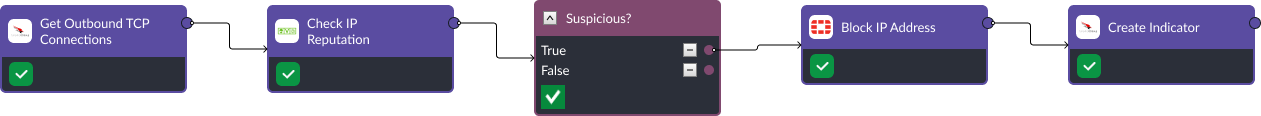
It’s common for AlienVault commands to be incorporated into workflows involving other security tools. For example, here is a workflow that retrieves all outbound connections made by a device, then runs the destination IP addresses through AlienVault OTX. For the ones that have been flagged by the community, the playbook blocks the IP addresses on the firewall and creates an indicator for it in an integrated EDR tool.
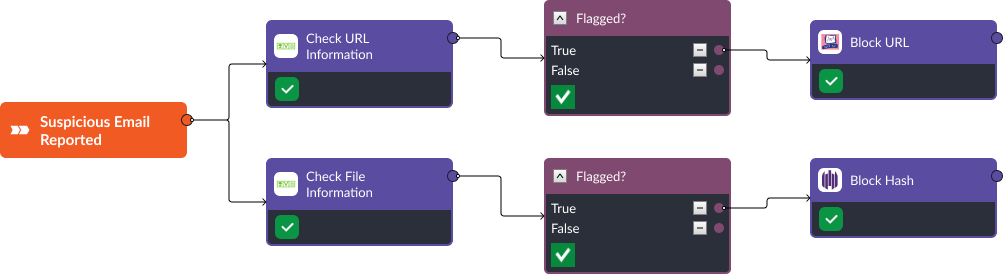
Similarly, suspicious links and files from phishing emails can be automatically analyzed and blocked across an internal network. The workflow below uses Checkpoint Firewall and SentinelOne to take action on results that have returned from AlienVault reputation checks.
Takeaway
OSINT databases can help security teams make more informed decisions, but collecting, parsing, and reviewing the data can be tiring. By incorporating OSINT into automated playbooks, SOAR users benefit from having all the relevant information on IoCs in one place: their incident ticket. Results from OSINT searches can be actioned from within SOAR to contain a threat or prevent flagged artifacts from being accessed within the network. For teams finding themselves performing repetitive tasks to retrieve valuable information, Smart SOAR is a tool that can help you streamline the process.




