The Threat Scenario
Consider a scenario where your file server, “D3Cyber-FileServer,” triggers an alert. The alert indicates an encryption attempt on “important_document.docx” by the command-line tool “cmd.exe.” This activity could signal a ransomware attack in progress, requiring immediate action.
An Automated Playbook for Suspicious File Activity
This playbook for suspicious file activity is designed to streamline incident response, ensuring rapid containment, thorough investigation, and effective threat eradication. Here’s how it works:
-
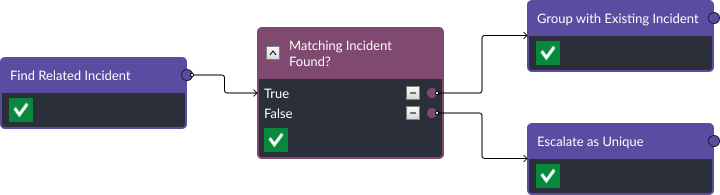
Alert Correlation and Prioritization
The playbook starts by correlating the alert with relevant indicators, such as computer name, user, file name, and process. This helps prioritize the alert based on its context and potential impact.
-
Enrichment for Informed Decisions
- Fetch Event Details: Using Splunk, the playbook gathers detailed event logs, offering a comprehensive view of the suspicious activity.
- Get File Hash: Through CrowdStrike, the playbook retrieves the file hash for deeper analysis.
- Query Indicators: The playbook checks CrowdStrike for any known malicious indicators associated with the source IP.
- Retrieve Network Logs: Through Checkpoint, the playbook pulls relevant network logs to trace suspicious traffic.

-
Classification and Severity Assessment
Enriched data allows for accurate incident classification. The use of “cmd.exe” for encryption and an internal IP address suggests a high-severity threat, indicating a possible ransomware attack.
-
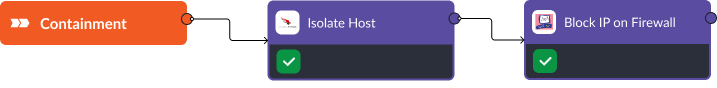
Immediate Containment Actions
- Isolate the Host: The playbook isolates the host using CrowdStrike, preventing further spread.
- Block IP on Firewall: The playbook adds a rule in Checkpoint to block outbound traffic from the suspicious IP, disrupting potential command and control communications.
-
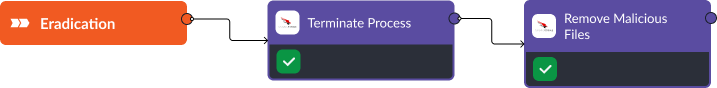
Eradication of the Threat
- Terminate Malicious Process: CrowdStrike is used to terminate the malicious “cmd.exe” process, stopping the encryption.
- Remove Malicious Files: Identified ransomware files are deleted, ensuring they cannot be executed again.
-
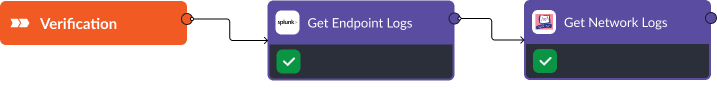
Verification
- Verify Process Termination: The playbook checks event logs in Splunk to confirm the termination of the malicious process.
- Ensure No Malicious Traffic: The playbook verifies through Checkpoint logs that no ongoing malicious traffic is present.
- Recovery
- Restore Network Connectivity: Once neutralized, the playbook lifts containment measures to restore normal operations.
- Validate System Integrity: A final validation is performed through Splunk, ensuring the system is clean and secure.

Why Choose Smart SOAR?
Our automated playbooks do more than react—they proactively defend, so you can take a mid-stage threat like suspicious file activity and root out any breach before it escalates. With D3 Smart SOAR, you benefit from:
- Speed and Efficiency: Automated responses reduce the time to contain and mitigate threats.
- Comprehensive Enrichment: Integration with leading tools ensures you have all the necessary data for informed decisions.
- Scalability and Customization: Our playbooks scale to handle any demanding workflows and the no-code/low-code editor is a flexible environment to accommodate unique use cases.
In the battle against ransomware, time is critical. D3’s Smart SOAR platform and its automated playbooks enable your security team to respond quickly and effectively, turning potential crises into manageable incidents.




