The collection and analysis of open-source threat intelligence (OSINT) are valuable stages in incident response. However, with large datasets and alert volumes, this process becomes cumbersome and teams cannot extract the full value from their threat intelligence feeds. Security Orchestration, Automation, and Response (SOAR) has gained popularity among mature security teams for its ability to automatically capitalize on relevant threat intelligence during incident response processes. With SOAR, organizations can automate collection, analysis, and implementation of OSINT data to improve the overall efficiency of their security operations. This article will discuss how SOAR is a force multiplier for threat intelligence and security teams.
What Is SOAR?
Before delving deeper into the role of SOAR in threat intelligence, it is necessary to define what SOAR is. SOAR is a cybersecurity software solution that integrates various security tools and platforms via APIs.
SOAR is an amalgamation of three fundamental concepts: security orchestration, automation, and response. Firstly, security orchestration involves integrating different security systems and applications to enable collaborative defense. Secondly, automation refers to the deployment of automated security tasks that previously required manual intervention, thereby accelerating threat detection and response times. Finally, response represents the ability to take immediate and effective action against detected threats.
SOAR is about unifying and enhancing an organization’s security operations. It eliminates silos between various security tools, automates repetitive tasks, and provides a platform for managing and responding to security threats in real-time. By leveraging SOAR, businesses can efficiently manage security alerts, minimize false positives, and reduce the time taken to respond to and neutralize threats.
OSINT and SOAR
The integration of OSINT and SOAR can significantly bolster an organization’s cybersecurity efforts. On one side, OSINT feeds valuable data into the SOAR platform about the evolving threat landscape, possible vulnerabilities, and the methods employed by cybercriminals. This information is critical to identify, investigate, and respond to threats in real-time.
On the flip side, SOAR can enhance the value derived from OSINT. By automating the collection, analysis, and response processes, SOAR can efficiently utilize the valuable OSINT inputs. It can sift through large volumes of data to pinpoint relevant threats, reducing the chances of missing critical indicators due to human error or resource constraints.
While OSINT provides the raw intelligence necessary to understand the potential threat landscape, SOAR is the engine that processes this data, automates actions, and orchestrates responses. Together, they create a comprehensive and proactive cybersecurity strategy capable of dealing with the complexities and demands of the modern digital environment.
OSINT Use Case 1: Automated Triage
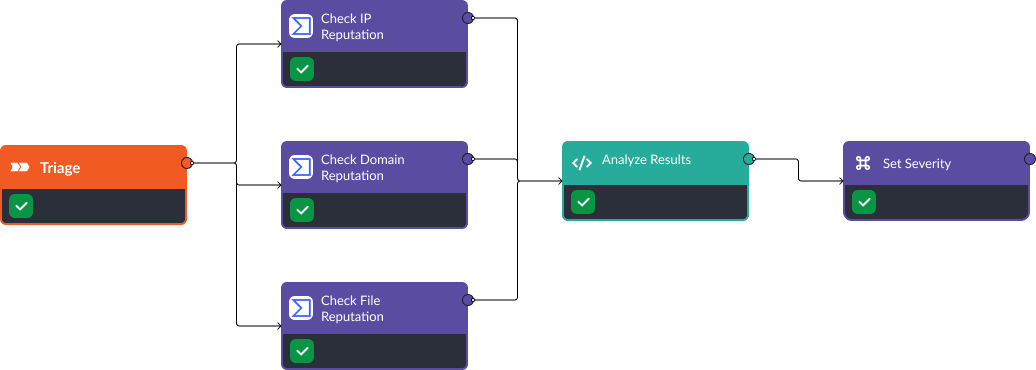
When alerts are ingested into SOAR tools, the relevant artifacts are extracted and sent to OSINT tools. OSINT tools often provide numerical scores for the artifact’s reputation. These scores can be consolidated and analyzed to produce a more accurate severity score for the incoming alert. Below is a workflow where VirusTotal is used to check the reputation of IP addresses, domains, and files included in an alert. Then, the results from VirusTotal are used to classify the alert as high, medium, or low severity. In Smart SOAR, this type of workflow runs automatically as soon as alerts are ingested.
OSINT Use Case 2: Automated Threat Intelligence Collection
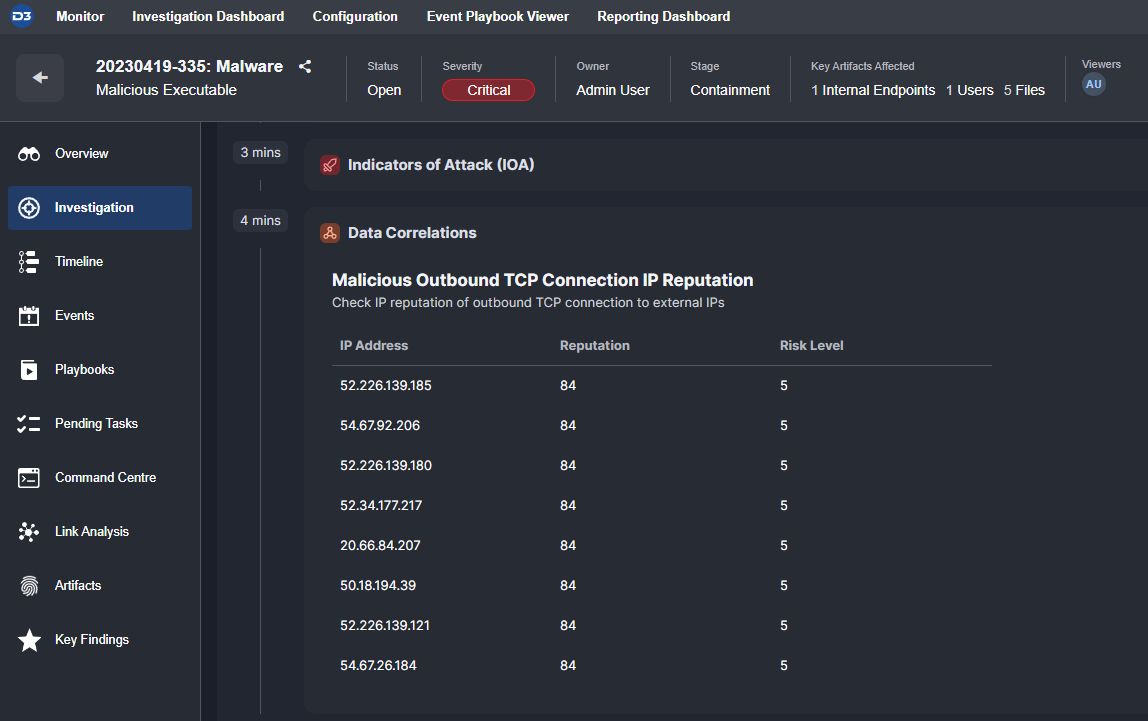
When incidents are created inside D3’s Smart SOAR, the artifacts are analyzed using API connections to our client’s OSINT tools. The results of these searches are collected and displayed for analysts to review. The automation of the data collection process minimizes data gaps, eliminates repetitive tasks, and ensures that the organization’s security operations have access to the most recent, complete, and up-to-date information about potential threats. Below, we can see the reputation scores for eight IP addresses associated with an attack:
OSINT Use Case 3: Correlation of Security Data
SOAR can correlate OSINT with data from various security technologies, including SIEM, endpoint detection and response (EDR), and identity and access management (IAM) tools. The integration of these tools means that all data relevant to an investigation is automatically gathered and kept in one place. In addition, SOAR playbooks can use this data to make decisions such as escalation and triage.
OSINT Use Case 4: Repeatable Processes
SOAR allows organizations to create and store automated workflows, thus providing a repeatable process for identifying, analyzing, and responding to threats. Automated workflows can be built for OSINT to be used to triage and investigate all alerts, tailored to the artifacts and incident type. This process reduces the risk of human error, standardizes response efforts, and ensures that threats are resolved in a timely and consistent manner.

OSINT Use Case 5: Cross-Tool Analysis
SOAR provides a centralized platform for analysis across each tool in a cybersecurity ecosystem. When an artifact is tagged as compromised by one system, SOAR can use OSINT to verify the vulnerability and reference it in future automated workflows. Security teams can know that their alerts are being analyzed with the most up-to-date and comprehensive information accessible.
Takeaway
SOAR plays a critical role in implementing threat intelligence to automate more accurate triage, eliminate repetitive tasks when collecting and parsing data, and standardize how OSINT is used during incident response. With the integration of SOAR and OSINT, mature security teams can benefit from increased efficiency and consistency in key processes.




