As organizations seek to bolster their cyber defense strategies, the MITRE ATT&CK framework has emerged as a valuable resource for understanding and categorizing real-world threats. This globally-accessible knowledge base offers a comprehensive and structured approach to enumerating the tactics, techniques, and procedures (TTPs) used by adversaries. However, to truly harness the power of this framework, security teams must effectively operationalize it within their incident response workflows.
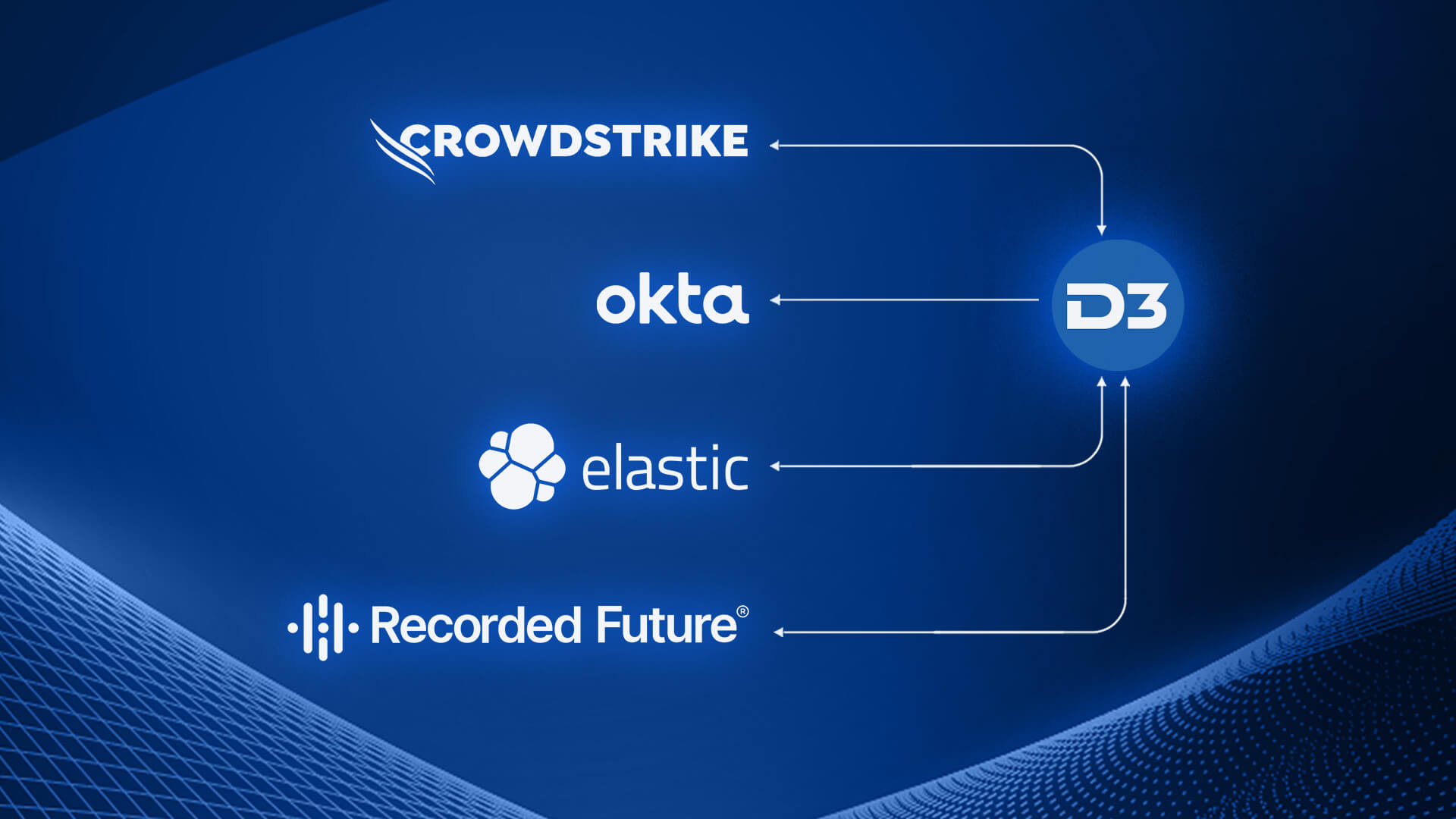
In this blog post, we’ll dive into how a D3 Smart SOAR playbook, tailored to the MITRE ATT&CK framework, can help organizations streamline their response to initial access attempts with valid accounts. We’ll discuss how this playbook integrates Elastic and Okta to classify incoming alerts and map them to their corresponding tactics, and uses CrowdStrike, Recorded Future and Okta to execute appropriate response actions. By leveraging the MITRE ATT&CK framework and powerful SOAR capabilities, security teams can proactively defend their environments and significantly enhance their incident response efforts.
The Alert: Failed Login Attempt
The event we’ll be looking at is a suspicious login attempt detected by Elasticsearch. The event data contains the source IP, source IP location, the IP and hostname of the target device, as well as the target username:
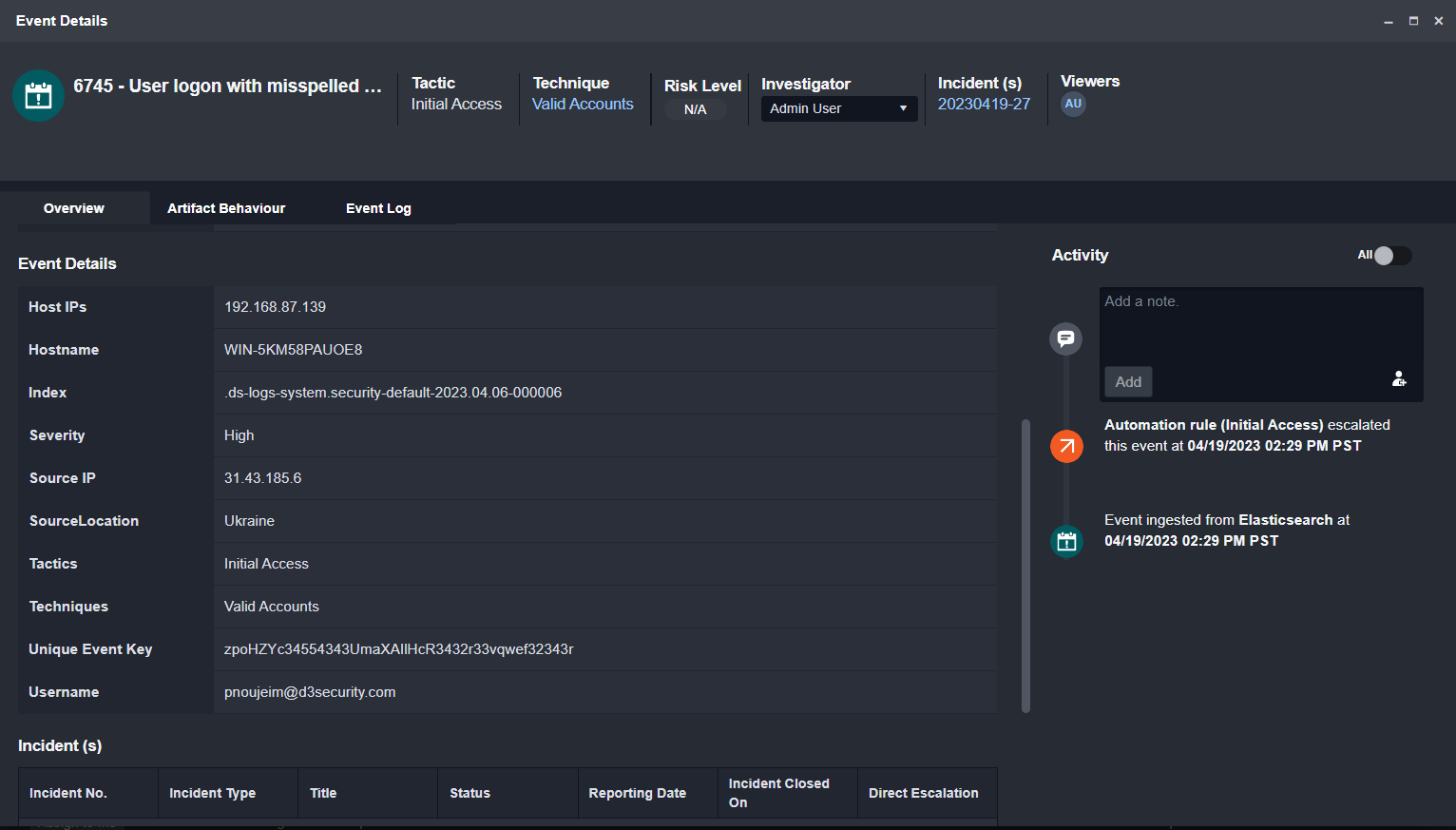
The event playbook below processed the event and tagged it as an Initial Access: Valid Account threat.
Step 1: Determine Severity and Identify False Positives
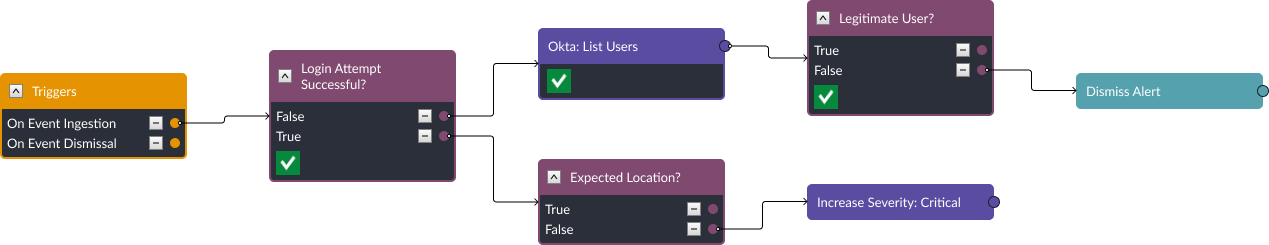
The first stage of the event playbook used for this alert checks three things:
- Was the authentication attempt successful?
- Is it a legitimate user?
- Is it coming from an expected location?
If the login attempt was successful and is coming from an unexpected location, the playbook increases the severity to critical. If the login attempt was unsuccessful, the playbook checks Okta to see if the target user is a legitimate user in the company. If they are not, the playbook tags the alert as a false positive and dismisses it.
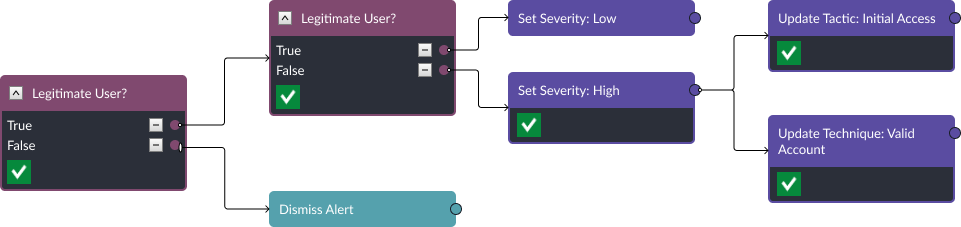
Step 2: Tag the Tactic and Technique
Once the legitimacy of the user is verified, the playbook checks if the location of the request is expected or not and then increases or decreases the severity depending on the result. If it is not expected, the playbook also tags the event as an Initial Access: Valid Account threat.
Step 3: Enrichment
Once the event has been escalated into an incident, the enrichment stage is triggered:
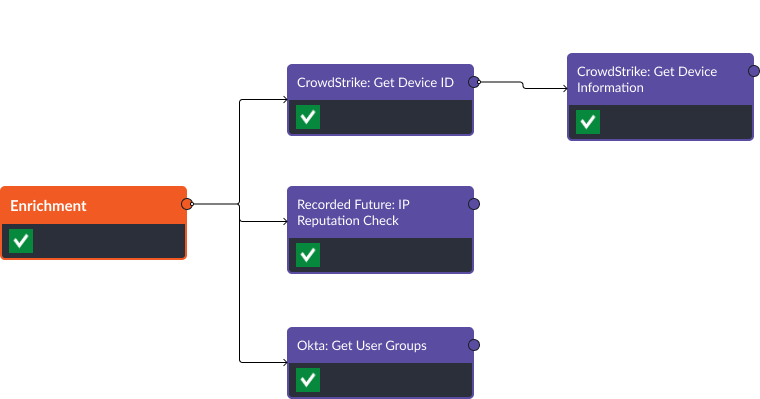
The enrichment stage of the incident playbook collects device information from CrowdStrike, IP reputation scores from Recorded Future, and the target user’s groups from Okta.
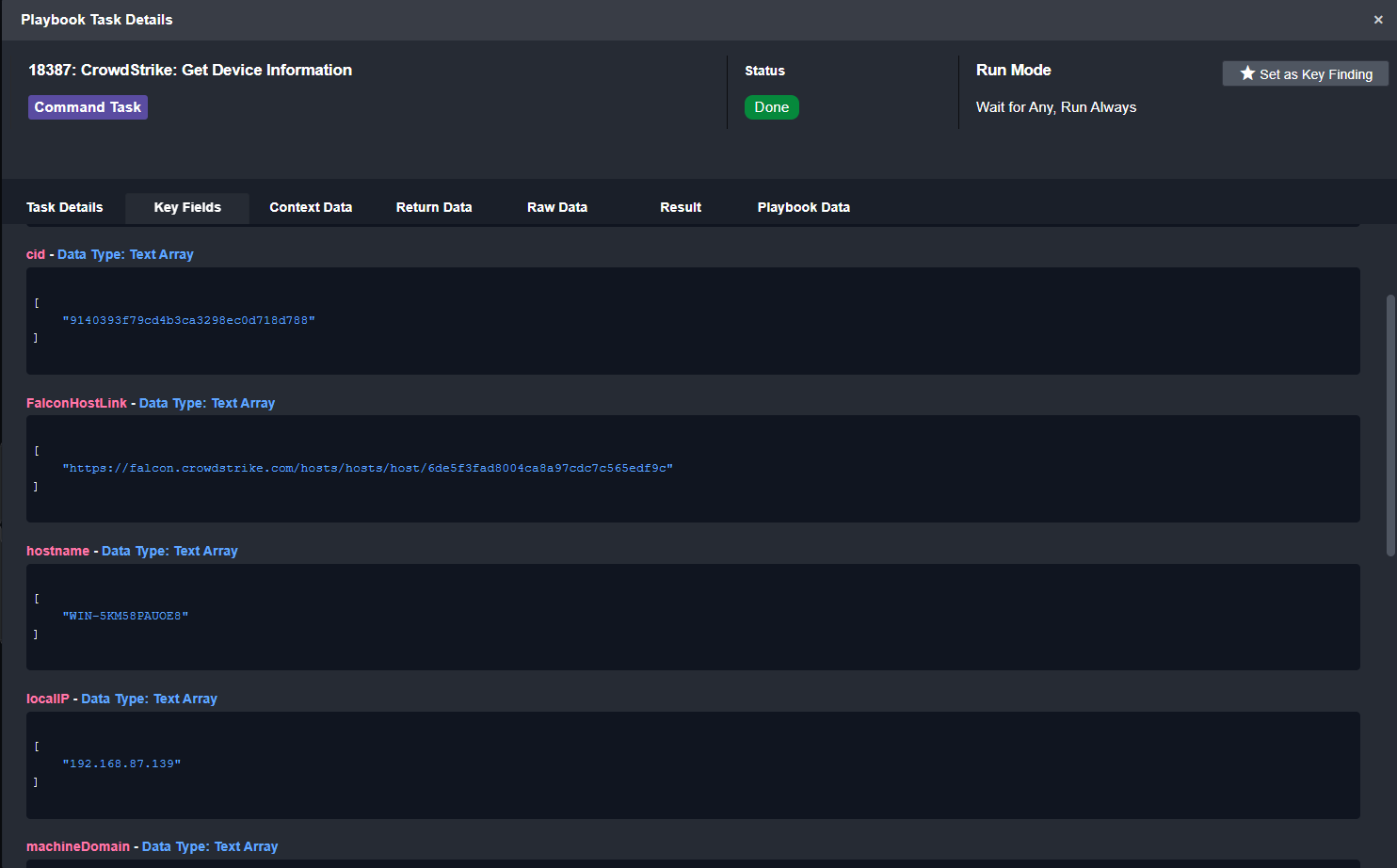
Device Information from CrowdStrike
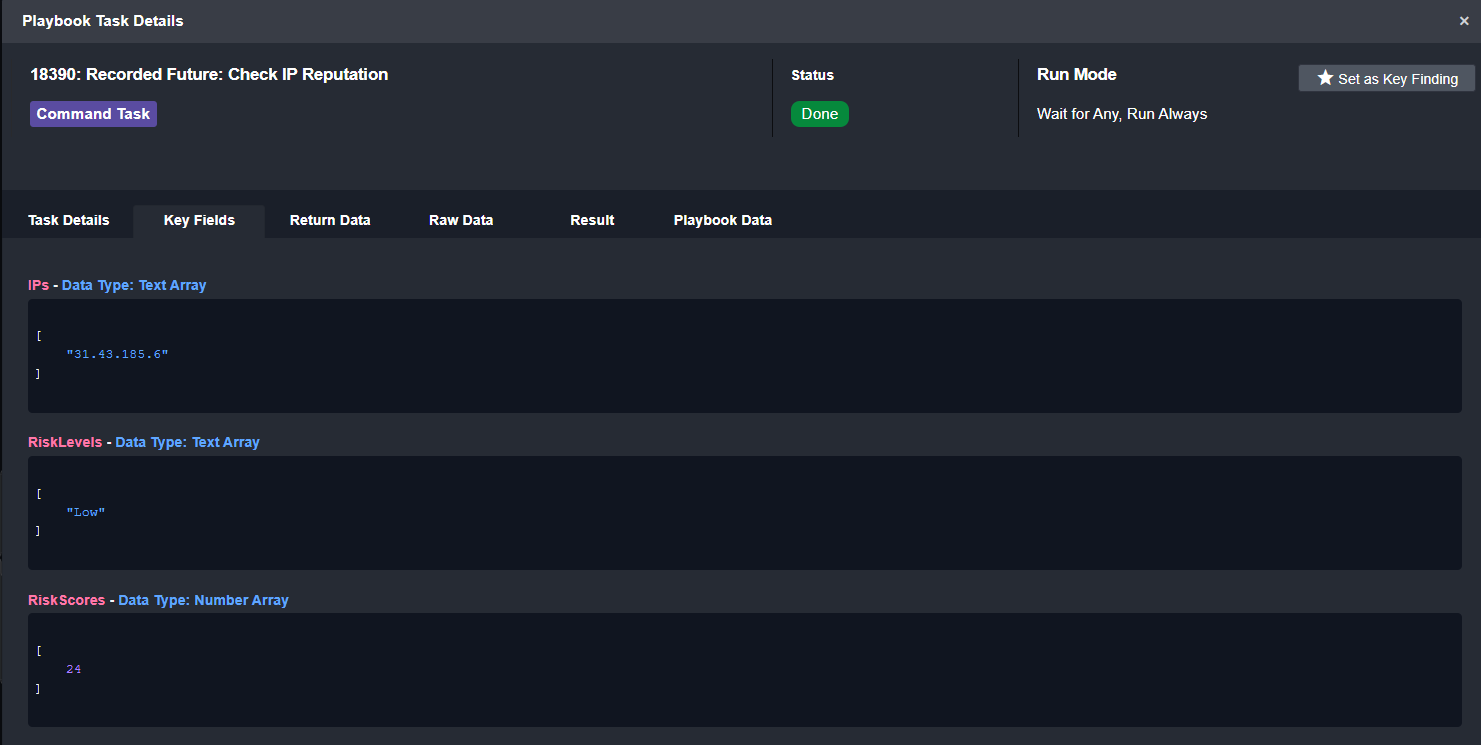
Recorded Future OSINT
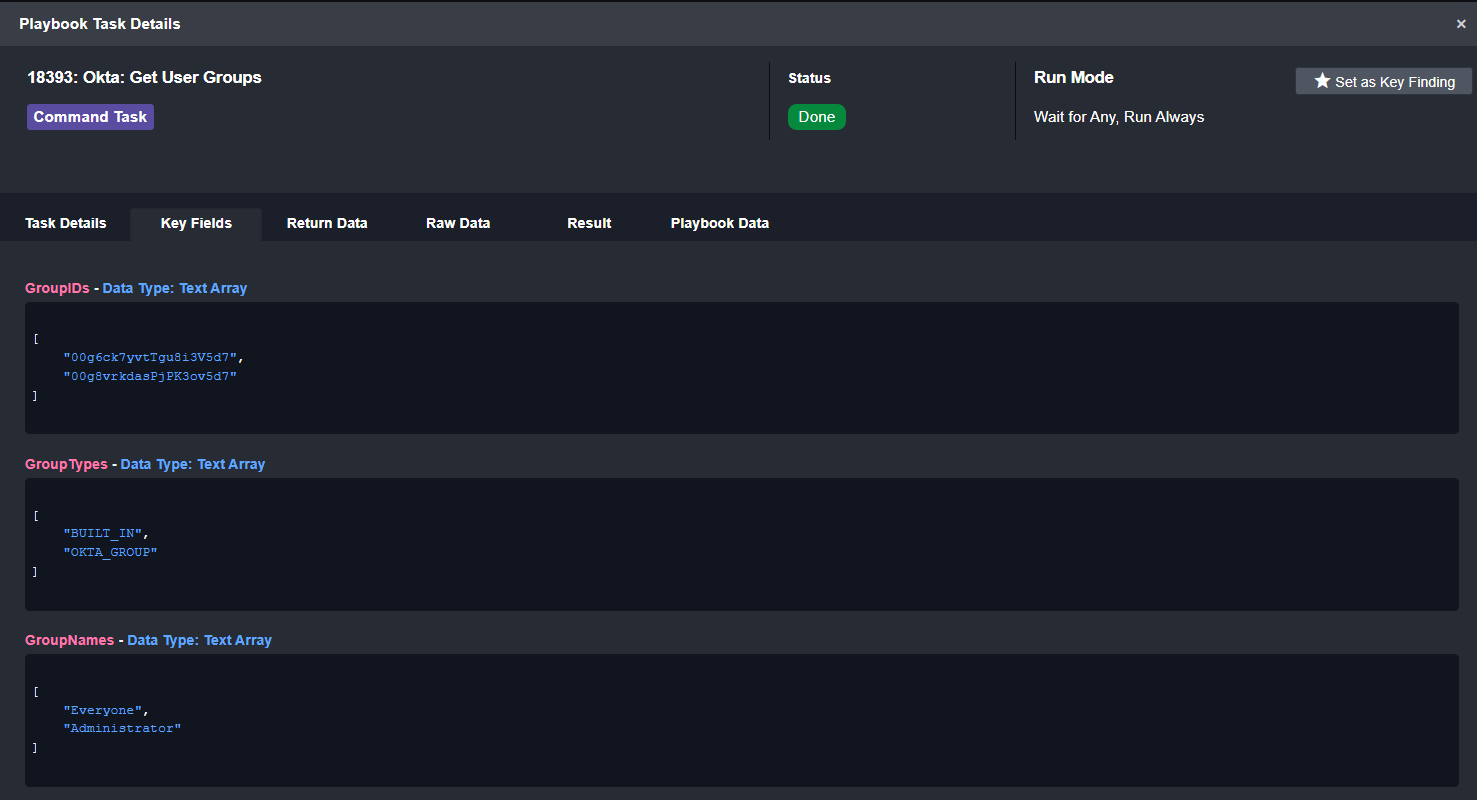
Okta User Groups
Step 4: Response
When enrichment is complete (this process takes 4-5 seconds from the point the incident is created), the playbook then checks to see if the target user is an administrator or not and checks the CrowdStrike IOC watchlist for the external IP. If the IP is not found, the playbook will add it to the watchlist. Also, if the user is not an administrator, it will close the incident.
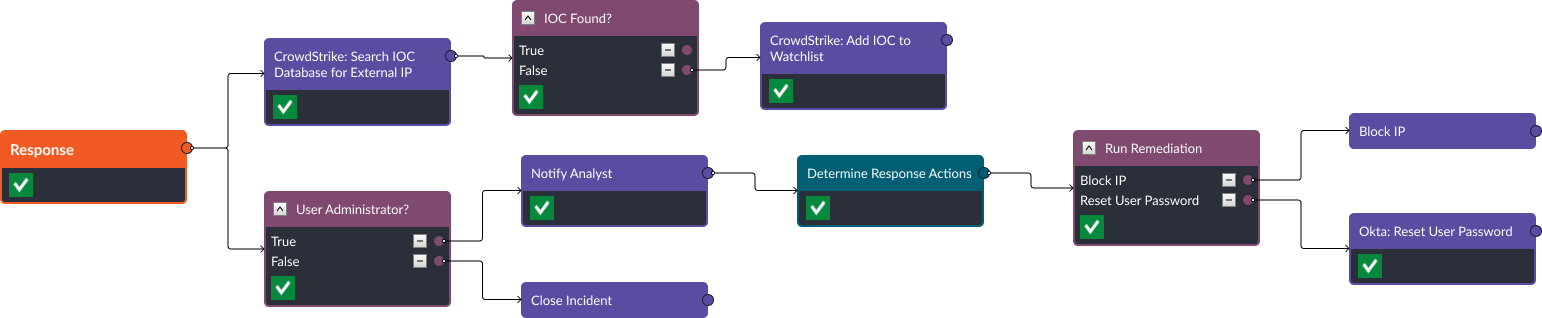
In this case, the user is an administrator, so we’ve notified the analyst assigned to the ticket that there are response actions they can take. The actions they can choose from between Okta and CrowdStrike are:
- Block IP
- Reset user password
- Deactivate user
- Isolate the host
In this case we’ve chosen just to reset the user password.
Step 5: Post-Incident Activities
Since remediation actions were taken, the playbook generates an incident report and sends it to the management team. The report contains event artifacts, actions taken, and steps completed by the analyst and playbook.
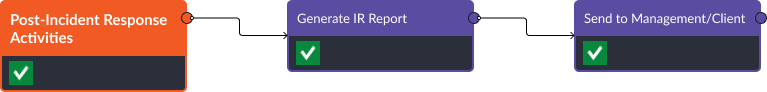

The total runtime for the event and incident playbook is 15 seconds, excluding the time spent waiting for the analyst to determine which response actions to take.
Conclusion
Organizations need to harness the power of the MITRE ATT&CK framework and SOAR capabilities to stay ahead of adversaries. The Smart SOAR playbook we’ve explored in this blog post demonstrates the potential to streamline incident response workflows by integrating Elastic, CrowdStrike, Okta, and Recorded Future. By rapidly processing and classifying alerts, enriching them with contextual information, and automating response actions, security teams can significantly reduce the time to detect and respond to threats.
The playbook’s ability to efficiently process initial access attempts with valid accounts showcases the importance of operationalizing the MITRE ATT&CK framework in incident response. By embracing this approach, organizations can enhance their overall cyber defense posture and be better prepared to face the challenges of modern cybersecurity threats.